What You'll Learn
Learn to manage privileged accounts and enforce security policies effectively in the CyberArk Online Training.
CyberArk Online Course Understand the core components of CyberArk and how to configure them for use.
Gain expertise in secure password management and automating access controls.
Learn to implement CyberArk solutions for improved security in enterprise environments.
Develop skills in auditing, reporting, and compliance within the CyberArk platform.
Master best practices for managing identities and protecting critical assets with CyberArk.
CyberArk Course Objectives
- Increased Demand for CyberArk Experts
- Expansion into Cloud Security
- Growing Regulatory Compliance Requirements
- Advancements in Privileged Account Management Technology
- Career Growth in Cybersecurity Roles
- Introduction to CyberArk
- Privileged Account Security
- Managing Password Vaults
- Risk Mitigation with CyberArk
- Advanced Security Features
- Banking and Finance
- Healthcare and Pharmaceuticals
- Information Technology
- Government and Defense
- Energy and Utilities
- Enhanced Career Opportunities
- Demonstrated Expertise in Cybersecurity
- Increased Job Market Competitiveness
- Higher Earning Potential
- Credibility with Employers
Request more informations
WhatsApp (For Call & Chat):
+91 76691 00251
CyberArk Course Benefits
CyberArk Certification Course offers in depth knowledge of privileged access management, enhancing security protocols It equips you with the skills needed to protect sensitive data, manage accounts and prevent cyber threats The course provides hands on experience, boosting employability and preparing you for high demand roles in cybersecurity.Earn CyberArk Certification to unlock career growth opportunities in the field.
- Designation
-
Annual SalaryHiring Companies
About Your CyberArk Certification Training
Our CyberArk Online Training offers an affordable path to mastering privileged access management, security protocols and compliance measures. With 500+ hiring partners we provide excellent career opportunities and placement support Gain practical experience through hands on projects ensuring you acquire real world skills necessary to excel in the cybersecurity industry Join today and enhance your career in CyberArk security!
Top Skills You Will Gain
- Privileged Access
- Identity Management
- Security Protocols
- Risk Mitigation
- Session Monitoring
- Audit Logging
12+ CyberArk Tools
Online Classroom Batches Preferred
No Interest Financing start at ₹ 5000 / month
Corporate Training
- Customized Learning
- Enterprise Grade Learning Management System (LMS)
- 24x7 Support
- Enterprise Grade Reporting
Why CyberArk Course From Learnovita ? 100% Money Back Guarantee
CyberArk Course Curriculum
Trainers Profile
Our CyberArk Online Training instructors are committed to delivering the latest curriculum with innovative insights. With globally recognized, certified CyberArk trainers, students gain access to a wealth of knowledge & practical expertise. They ensure learners acquire up to date skills and information, keeping pace with industry demands. Through our CyberArk Internship students can apply theoretical learning in real world environments ensuring career readiness.
Syllabus for CyberArk Course Download syllabus
- CyberArk Solutions
- Security Fundamentals
- PAM Architecture
- Privileged Access
- CyberArk Tools
- Pre-Installation Setup
- System Requirements
- Installation Guide
- Server Configuration
- Network Configuration
- Vault Overview
- Vault Configuration
- Storage Management
- Vault Access Control
- Vault Security
- Password Management
- Password Vault
- Access Control
- Rotation Policies
- Security Audits
- Access Control
- Policy Management
- User Privileges
- Session Management
- Permission Configuration
- Session Recording
- Session Logging
- Audit Trails
- Monitoring Techniques
- Alerting Systems
- Threat Prevention
- Response Mechanisms
- Risk Identification
- Real-time Monitoring
- Attack Detection
- Integration Overview
- API Usage
- Automation Scripts
- External Integrations
- Third-Party Tools
- Reporting Dashboard
- Event Logs
- Report Generation
- Audit Trails
- Security Metrics
- Compliance Standards
- Regulatory Requirements
- Compliance Audits
- Security Frameworks
- Risk Assessment
Request more informations
WhatsApp (For Call & Chat):
+91 76691 00251
Industry Projects
Career Support
Not Just Studying
We’re Doing Much More!
Empowering Learning Through Real Experiences and Innovation










Exam & CyberArk Certification
- Basic understanding of IT security concepts
- Familiarity with network security and security protocols
- Experience with other cybersecurity tools is beneficial
- Completion of the CyberArk Training program
- At least a fundamental knowledge of PAM concepts and practices
- CyberArk Administrator
- Cybersecurity Analyst
- Privileged Access Manager
- IT Security Specialist
- PAM Consultant

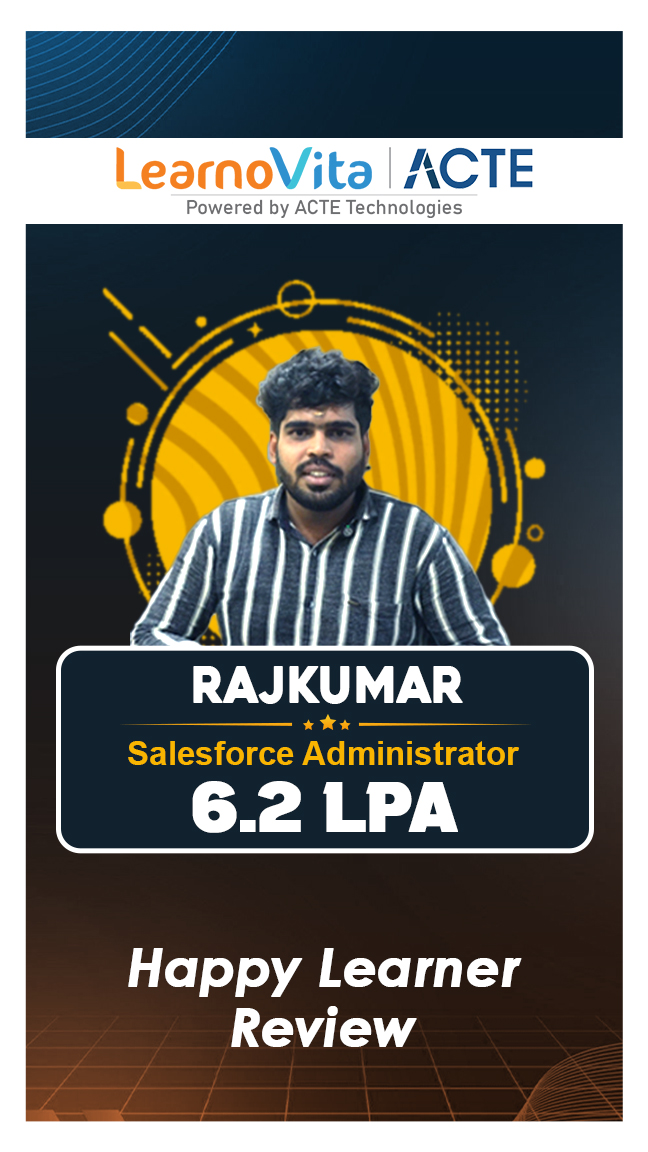
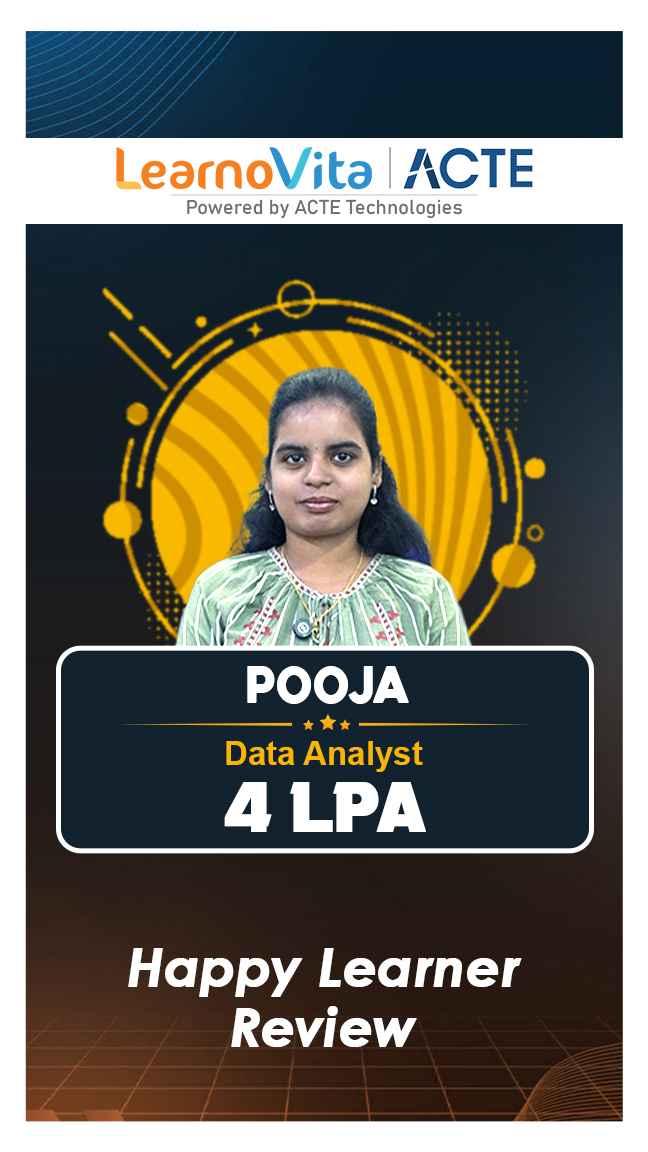
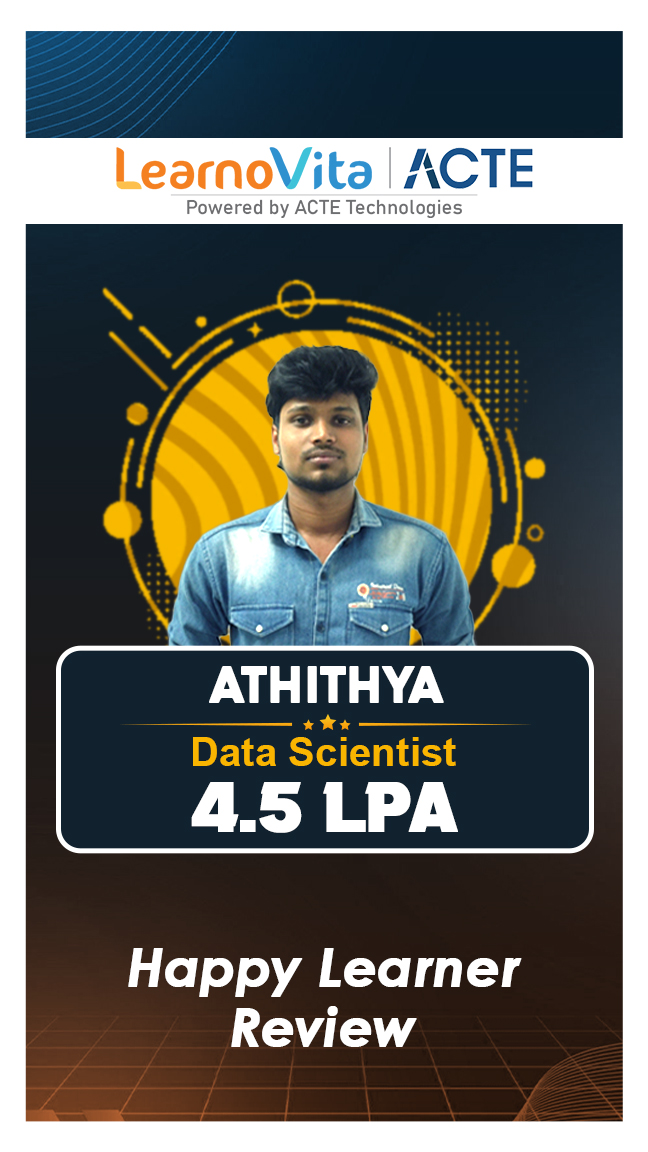
Our learners
transformed their careers

A majority of our alumni
fast-tracked into managerial careers.
Get inspired by their progress in the Career Growth Report.
Our Student Successful Story
How are the CyberArk Course with LearnoVita Different?
Feature
LearnoVita
Other Institutes
Affordable Fees
Competitive Pricing With Flexible Payment Options.
Higher CyberArk Fees With Limited Payment Options.
Live Class From ( Industry Expert)
Well Experienced Trainer From a Relevant Field With Practical CyberArk Training
Theoretical Class With Limited Practical
Updated Syllabus
Updated and Industry-relevant CyberArk Course Curriculum With Hands-on Learning.
Outdated Curriculum With Limited Practical Training.
Hands-on projects
Real-world CyberArk Project With Live Case Studies and Collaboration With Companies.
Basic Projects With Limited Real-world Application.
Certification
Industry-recognized CyberArk Certifications With Global Validity.
Basic CyberArk Certifications With Limited Recognition.
Placement Support
Strong Placement Support With Tie-ups With Top Companies and Mock Interviews.
Basic Placement Support
Industry Partnerships
Strong Ties With Top Tech Companies for Internships and Placements
No Partnerships, Limited Opportunities
Batch Size
Small Batch Sizes for Personalized Attention.
Large Batch Sizes With Limited Individual Focus.
Additional Features
Lifetime Access to CyberArk Course Materials, Alumni Network, and Hackathons.
No Additional Features or Perks.
Training Support
Dedicated Mentors, 24/7 Doubt Resolution, and Personalized Guidance.
Limited Mentor Support and No After-hours Assistance.
CyberArk Course FAQ's
- LearnoVita is dedicated to assisting job seekers in seeking, connecting, and achieving success, while also ensuring employers are delighted with the ideal candidates.
- Upon successful completion of a career course with LearnoVita, you may qualify for job placement assistance. We offer 100% placement assistance and maintain strong relationships with over 650 top MNCs.
- Our Placement Cell aids students in securing interviews with major companies such as Oracle, HP, Wipro, Accenture, Google, IBM, Tech Mahindra, Amazon, CTS, TCS, Sports One , Infosys, MindTree, and MPhasis, among others.
- LearnoVita has a legendary reputation for placing students, as evidenced by our Placed Students' List on our website. Last year alone, over 5400 students were placed in India and globally.
- We conduct development sessions, including mock interviews and presentation skills training, to prepare students for challenging interview situations with confidence. With an 85% placement record, our Placement Cell continues to support you until you secure a position with a better MNC.
- Please visit your student's portal for free access to job openings, study materials, videos, recorded sections, and top MNC interview questions.

- Build a Powerful Resume for Career Success
- Get Trainer Tips to Clear Interviews
- Practice with Experts: Mock Interviews for Success
- Crack Interviews & Land Your Dream Job



 Fees Starts From
Fees Starts From



















 Regular 1:1 Mentorship From Industry Experts
Regular 1:1 Mentorship From Industry Experts




