- How to learn Ethical Hacking?
- How to become a Ethical Hacker ? Know about the requirements to become one
- Introduction to Cyber Security | A Complete Guide
- Top Reasons to Learn Cyber Security | Everything You Need to Know to Become an Expert
- CyberSecurity Framework | How to Implement | A Definitive Guide with Best Practices [ OverView ]
- The Impact of AI and Machine Learning on Cybersecurity | Everything You Need to Know
- What is Certified Ethical Hacker (CEH) Certification and Why is it Important? [ OverView ]
- Benefits Of ECSA Certification | Everything You Need to Know | Expert’s Top Picks
- Top Most OSINT Tools – Open Source Intelligence | Expert’s Top Picks
- Cyber Security Salary in India : Everything You Need to Know
- What is Computer Security? Free Guide Tutorial & REAL-TIME Examples
- Ethical Hacker Salary and Job Description | Everything You Need to Know
- Hacking Tools and Software | All you need to know [ OverView ]
- What is DES? Free Guide Tutorial & REAL-TIME Examples
- How to Become an Ethical Hacker?
- Which are the Best Network Security Certifications?
- Cybersecurity Consultant Career Path
- The Most Effective Data Encryption Techniques
- Great CISSP Books and Study Guides for the CISSP Certification
- What Is Kerberos?
- Top CISSP Domains
- Cyber Security Career Path
- CISSP Certification Exam Guide 2020
- Top Cyber Security Trends for 2020
- CISSP Exam Online 2020
- Compare and Contrast Physical and Environmental Security Controls
- What is information security architect?
- Certified Information Systems Security Professional (CISSP) Certification
- Top Cyber Security Jobs
- What is CISA Certification?
- What is Threat Modeling?
- Certified Information Security Manager (CISM) Certification
- Information Security Management Principles
- Network Perimeter Security Design
- Things You Must Know About Cyber Security in the Cloud
- What is ECSA?
- Why is Cybersecurity Important?
- Tips to Clear Certified Ethical Hacker (CEH) Exam
- Average Annual Salary of a CISSP Certified Professional
- “How to Become a Cyber Security Engineer? “
- Who is an Ethical Hacker?
- What are the requirements to become Cissp certified?
- The Phases of Ethical Hacking
- What is Ethical Hacking?
- Top Ethical Hacking Certifications
- Hash in Python
- How to learn Ethical Hacking?
- How to become a Ethical Hacker ? Know about the requirements to become one
- Introduction to Cyber Security | A Complete Guide
- Top Reasons to Learn Cyber Security | Everything You Need to Know to Become an Expert
- CyberSecurity Framework | How to Implement | A Definitive Guide with Best Practices [ OverView ]
- The Impact of AI and Machine Learning on Cybersecurity | Everything You Need to Know
- What is Certified Ethical Hacker (CEH) Certification and Why is it Important? [ OverView ]
- Benefits Of ECSA Certification | Everything You Need to Know | Expert’s Top Picks
- Top Most OSINT Tools – Open Source Intelligence | Expert’s Top Picks
- Cyber Security Salary in India : Everything You Need to Know
- What is Computer Security? Free Guide Tutorial & REAL-TIME Examples
- Ethical Hacker Salary and Job Description | Everything You Need to Know
- Hacking Tools and Software | All you need to know [ OverView ]
- What is DES? Free Guide Tutorial & REAL-TIME Examples
- How to Become an Ethical Hacker?
- Which are the Best Network Security Certifications?
- Cybersecurity Consultant Career Path
- The Most Effective Data Encryption Techniques
- Great CISSP Books and Study Guides for the CISSP Certification
- What Is Kerberos?
- Top CISSP Domains
- Cyber Security Career Path
- CISSP Certification Exam Guide 2020
- Top Cyber Security Trends for 2020
- CISSP Exam Online 2020
- Compare and Contrast Physical and Environmental Security Controls
- What is information security architect?
- Certified Information Systems Security Professional (CISSP) Certification
- Top Cyber Security Jobs
- What is CISA Certification?
- What is Threat Modeling?
- Certified Information Security Manager (CISM) Certification
- Information Security Management Principles
- Network Perimeter Security Design
- Things You Must Know About Cyber Security in the Cloud
- What is ECSA?
- Why is Cybersecurity Important?
- Tips to Clear Certified Ethical Hacker (CEH) Exam
- Average Annual Salary of a CISSP Certified Professional
- “How to Become a Cyber Security Engineer? “
- Who is an Ethical Hacker?
- What are the requirements to become Cissp certified?
- The Phases of Ethical Hacking
- What is Ethical Hacking?
- Top Ethical Hacking Certifications
- Hash in Python

Top Reasons to Learn Cyber Security | Everything You Need to Know to Become an Expert
Last updated on 05th Nov 2022, Artciles, Blog, Cyber Security
- In this article you will get
- Preface
- Cybersecurity is a popular content, but do you know why it’s essential?
- Specialties in Cybersecurity
- Distributed Denial of Service
- Malware Attack
- Functions of Malware
- Sources of Malware
- Conclusion
Preface
In the current situation, Cyber Security is getting presumably the stylish choice to start your vocation with. The superb explanation is the developing interest of the specialists across the globe since the most recent couple of times. It’s one of the Information Technology spaces which are turning out to be decreasingly delicate. Due to the snappily expanding digital assaults across the globe, associations are searching for the specialists who can help them in handling commodity veritably analogous.
Another reality is network safety is a delicate space and needs a great deal of aptitude for the experts to take out assaults that are unapproved in nature. All effects considered, these aren’t by any means the only explanation why Cyber Security has allowed of fantastic extensions as of late. There are obviously a many different reasons as well. Then’s the rundown of top 10 apologies for why you ought to learn network protection this time.
1.High Demand for Cyber Security experts:
The application of the Internet has expanded impressively over the former decade. From requesting food to shopping, everything has come available on the web.While on one hand, this innovative metamorphosis has ended up being a help, also again, the web has come more helpless against digital assaults.This has for sure made a bottomless demand for Cyber Security to keep the web from online highway robbery and wrongdoing.
With mechanical advance in the web space, Cyber Security has come relatively conceivably the most satisfying vocation choices moment and the interest for Cyber Security professionals is expanding step by step.The interest for Cyber Security experts is really high that they’re getting signed at multiple times the rate than the remainder of the connected positions and thus you ought to learn Cyber Security.Adding to current realities, the worldwide interest for Cyber Security experts is reckoned upon to lift to 6 million before the finish of 2019 and a lack of1.5 million Cyber Security is reckoned upon to be seen.
2.Great salary packages:
Who does n’t need a decent compensation pack? Nearly everybody and getting a decent compensation does n’t do any detriment. With respects to erecting a profession in Cyber Security, experience and information are an irrefutable demand, nevertheless, beginning a vocation with a decent compensation pack is also a fantasy of numerous.Therefore, a introductory rule of interest and force has been applied then. The interest for Cyber Security experts is expanding step by step while the stock is significantly lower.
In this way, heads are prepared to pay further significant compensation to Cyber Security experts. This one further defense for why you should feel free to learn Cyber Security.As a coin has different sides, the world is loaded up with two feathers of individualities. One who utilizes the web immaculately and emphatically to make the world a superior spot as far as invention.
Also again, there are the individualities who need to hurt others by exploiting the web.Accordingly, to keep themselves from on the web and digital assaults, associations and houses are searching for specialists who can shield their fabrics from digital culprits and retain the stylish mortal asset, they will pay further.By being a talented Cyber Security complete with appeal, you can likewise arrange your pay with any business.An expanded Cyber Security request has ended up being productive for a ton of challengers who had or have an interest in the internet.Since the hole between the interest and force of Cyber Security experts is high, it has urged a more significant payment rate for Cyber Security experts.
3.Trip the world with cyber security:
Could it be said that you’re anticipating a task where you can go each over the earth? On the off chance that indeed, Cyber Security is the right vocation way for you.Network safety is a worldwide issue and is n’t simply confined to a specific geological region.Also, the ascent in expanding digital assaults has been being overall which have appreciatively outperformed the cache of Cyber Security experts refocused toward averting these digital assaults.Also, this expanded interest for Cyber Security experts has lately not passed at one specific spot yet has set out to open doors abroad too.Specialists in this specialty are also anticipated to make a trip abroad to take into account the musts of the associations that match their range of capacities.
4.Cyber security is an evergreen industry:
Gone were the days when Cyber Security wasn’t nothing to joke about. moment, in this always advancing invention time, the web has turned into a need for a larger part of individualities.Web assists them with dealing with their everyday requirements whether individual or expert.
Notwithstanding, programmers across the world are all the while exercising the web to satisfy their musts yet in a deceptive way.As digital assaults are getting more common currently, a harmonious demand for Cyber Security specialists is likewise expanding. Consequently, the work profile of a Cyber Security complete has come more steady than preliminarily.You may be believing that it’s hard to learn Cyber Security and acclimatize to the updates and patterns of Cyber Security.Yet, the fact is that there isn’t a lot that has changed in the Cyber Security space, latterly, you can really start your vocation as a Cyber Security complete.
5.Conditions are introductory:
Assuming you feel that erecting a profession in Cyber Security is inviting and worrisome, you’re potentially out- base. To turn into a Cyber Security complete, you completely do n’t need to go to some academy for a 4- time degree course or get a modest bunch time of involvement.You can move forward in the Cyber Security area as an expert with some information on IT space and an approved Cyber Security protestation.
Keep in mind, getting an protestation in Cyber Security is vital as it expands your capsule worth and gives a power of you being a Cyber Security complete.The qualification measure for getting a instrument in Cyber Security has been kept essential with an anticipation to connect the colossal hole between the interest and force of Cyber Security experts.Assuming you’re a fresher or indeed an undergrad, you can do with this profession without truly agonizing over anything.
6.Mathematics isn’t demanded:
Do you have arithmophobia? Is it true or not that you sweat the number? Indeed, all effects considered, you simply need to decompress.The data really confirm that calculation as a subject is veritably trying for a ton of understudies. A portion of the functioning experts are likewise scarified of calculation.The data confirm that not every person has an inclination for calculation and accordingly does n’t release them ahead with a profession of their decision as calculation is engaged with it.
To assemble a vocation in Cyber Security, you can clearly do with it without being vexed with respects to the calculation part. Digital protection is completely liberated from the donation of calculation and so on the off chance that you would rather avoid calculation, you really want not stress over getting a evidence in Cyber Security.Rather, you can invest your energy in dominating capacities like systems administration and programming to assemble a vocation in a specific range of capacities.
7.Unlimited career growth options:
Network protection is extending its standpoint through different enterprises. This ensures that’s an ideal stage for development as far as profession just as learning openings.Currently, digital assaults are getting further brilliant and hastily. This emerges the demand for Cyber Security experts to fox the programmers at a vastly quicker pace.
Associations and countries are subject to them for examining and limiting peril alongside fighting digital assaults and averting a wide range of sins.Handling the digital assaults are a result of ceaseless review, total examination and ideal prosecution.This demonstrates that when you learn Cyber Security, you’ll be constantly knowing new effects and acquiring rich experience which is an redundant to your range of capacities.
8.Openings to work with high profile agencies:
Maybe the stylish thing about being a Cyber Security complete is that your odds of working with presumably the topmost associations at numerous top situations on the earth increases.There’s no limitation on the volume of the association that you can work with.The interest for Cyber Security experts has significantly expanded across the globe. In this way, the geological block is naturally cleared.
It must be noticed that the eventuality does n’t end then, specialists in Cyber Security may likewise find the occasion to work with a portion of the first rate secret government and knowledge services like NSA, CBI and so forth alongside Central Intelligence Agency, Department of Defense and different banks.
9.A Plethora of diligence to choose from:
Assuming that you’re a Cyber Security complete, you aren’t simply confined to one specific assiduity. While previous the interest for Cyber Security experts was limited to specific businesses like riddle military associations, government services, banks, exigency conventions, IT associations and seminaries.
Be that as it may, as the motorized uneasiness has passed, there have been marches in the area of invention, information wisdom and advanced advertising.This has paved the way for Cyber Security experts to enter any assiduity that needs to be precisely secure. In addition, this is a remarkable defense for you to learn Cyber Security.
10.Learn “ White- Hat ” Hacking:
With the development of Digitalization, web showcasing has turned into the main inclination for nearly everybody.While on the positive side, it has set out productive open doors for promoters and advertisers while giving promising profession freedoms to numerous individualities.On the negative front, there has been an proliferation in the volume of digital violations and assaults. During the occupancy of your Cyber Security instrument, you’ll likewise get an occasion to learn “ white- cap ” hacking.This will make you the most demanded aspirant according to the business ’ perspective.
Cybersecurity is a popular content, but do you know why it’s essential?
We must understand that private information is much more vulnerable than ever ahead. We frequently hear about data breaches and cases of identity theft that affect millions of consumers.All companies and institutions are fighting to cover their data against hackers and cybercriminals, and you can also play a part in it. Cybersecurity isn’t involved only in associations, but indeed particular computers, mobile phones, and tablets.
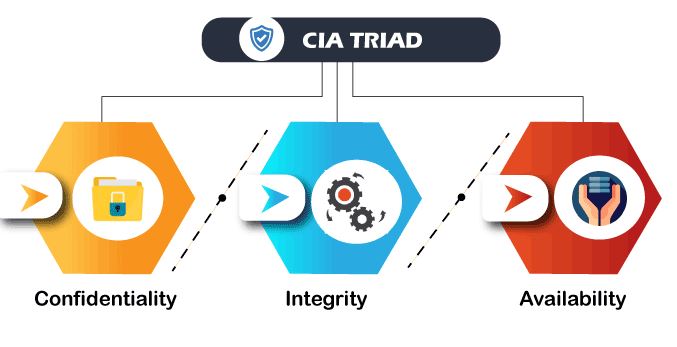
CIA Triad:
This is called the CIA, which has served as the assiduity standard for computer security since the time of first mainframes.Vacuity The principles of vacuity assert that systems, functions, and data must be available on- demand according to agreed- upon parameters grounded on situations of service.Let’s look at the areas in cybersecurity to understand the space more.
Specialties in Cybersecurity:
Access control systems and methodology This deals with guarding critical system coffers from unauthorized revision. Telecommunications and network security This focuses on dispatches, protocols, and network services, and the implicit vulnerabilities associated with each.
Security armature and models this focuses substantially on having security programs and procedures in place.:
Cryptography Designed to help you understand how and when to use encryption.Computer operations security This covers all those effects that be while your computers are running.Physical security This primarily addresses questions about physical access to your waiters and workstations.
These are some of the terms that you must be familiar with before learning anything about cybersecurity. These terms decide from networking generalities and will be useful to understand.
Network:
A network is a connection between two or further computers so that they can communicate with each other.
Internet:
The Internet is a means of connecting a computer to any other computer anywhere in the world via devoted routers and waiters.
Internet Protocols:
The data that’s transferred or entered can not follow any path. There are a set of rules that are followed to control the inflow of the internet. These rules are called internet protocol.
IP Address:
An Internet Protocol address( IP address) is an address assigned to all bias that connect to a computer network and uses the Internet Protocol for communication. An IP address looks like this168.192.10.3
MAC Address:
This is a unique identification number that every device has that connects to the internet. Traditional MAC addresses are 12- number hexadecimal figures. MAC address looks like this D8- FC-93-C5-A5-EO.
Sphere Name Garçon( DNS):
Consider DNS as the phonebook of the internet. All the IP addresses and the name of the links are saved in it. For illustration, you want to go togoogle.com. You class this on your web operation. also, this name goes to the DNS garçon, and the DNS garçon finds the IP address ofgoogle.com. also, the DNS garçon returns it to your computer with the IP address.
DHCP( Dynamic host configuration protocol):
Dynamic host configuration protocol is a protocol that assigns an IP address to any device that wants to connect to the internet.
The five main types of attacks are as follows:
- Distributed denial of service( DDoS)
- Man in the middle
- Dispatch attacks
- Word attacks
- Malware attack
Distributed Denial of Service
It’s an attack used to circumscribe a stoner from penetrating the coffers by submerging the business that’s used to pierce coffers. A botnet regulator controls all the bots that are under it. The bushwhacker sends a command to the botnet regulator that tells all bots to attack a garçon so that the garçon will be swamped. When a stoner wants to pierce a website, he’ll not be suitable to, as the business on the website will be at full capacity.
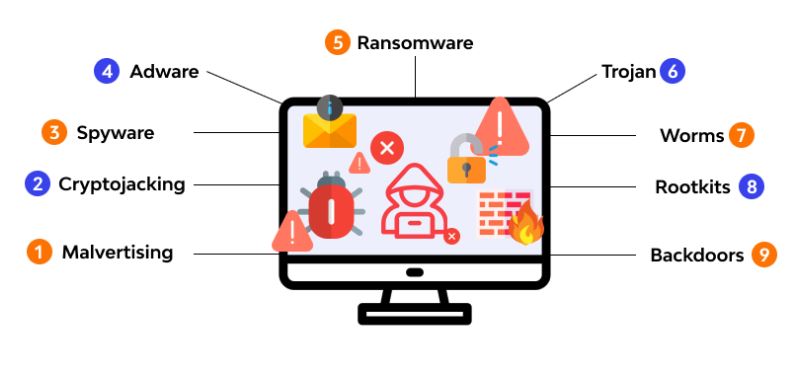
Malware Attack
Malware This is a vicious program or software that disrupts or damages the computer. There are three types of malware.The contagion requires someone to deliberately or intentionally spread the infection without the knowledge or authorization of a stoner or system director. An illustration of a contagion is the Melissa contagion.
Functions of Malware
Disabling security functions Some malware can disable antivirus software, as well as security updates. This malware tends to last longer because there’s no security to stop it. They tend to keep the system vulnerable to other malware.Creating botnets Hackers make botnets by purely rendering. A botmaster controls botnets, and they’re generally used to crash websites. Botmaster tells all botnets to flood tide the website by penetrating the website at the same time.
Sources of Malware
- Documents and executable lines Contagions can be hidden in document lines with the. exe extension. As soon as you open them, the contagion activates.
- Internet downloads Download lines only from trustedwebsites.However, there may be chances that those lines will contain contagions, and as soon as you open them, If you download from untrusted websites.
- Network connections Be sure that your service provider isgenuine.However, also it can be penetrated by anyone, If the network is relaxed.
- Dispatch attachments noway open dispatch attachments unless the sender can be trusted. These lines may contain contagions to produce backdoors.
- Vicious announcements noway click on advertisements that you do n’t trust. They’re created so that you can click on them, and hackers will admit details about you.
Conclusion
Inferable from the constantly expanding interest for Cyber Security experts, your work will ever be gotten in the event that you assemble a vocation in it.After you have gained the essential capacities, your worth in the business builds which infers that it’s productive 100 of the time to learn Cyber Security.In this manner, to catch your vocation in the Cyber Security space, also, at that point, you ought to without a mistrustfulness learn Cyber Security.