- How to learn Ethical Hacking?
- How to become a Ethical Hacker ? Know about the requirements to become one
- Introduction to Cyber Security | A Complete Guide
- Top Reasons to Learn Cyber Security | Everything You Need to Know to Become an Expert
- CyberSecurity Framework | How to Implement | A Definitive Guide with Best Practices [ OverView ]
- The Impact of AI and Machine Learning on Cybersecurity | Everything You Need to Know
- What is Certified Ethical Hacker (CEH) Certification and Why is it Important? [ OverView ]
- Benefits Of ECSA Certification | Everything You Need to Know | Expert’s Top Picks
- Top Most OSINT Tools – Open Source Intelligence | Expert’s Top Picks
- Cyber Security Salary in India : Everything You Need to Know
- What is Computer Security? Free Guide Tutorial & REAL-TIME Examples
- Ethical Hacker Salary and Job Description | Everything You Need to Know
- Hacking Tools and Software | All you need to know [ OverView ]
- What is DES? Free Guide Tutorial & REAL-TIME Examples
- How to Become an Ethical Hacker?
- Which are the Best Network Security Certifications?
- Cybersecurity Consultant Career Path
- The Most Effective Data Encryption Techniques
- Great CISSP Books and Study Guides for the CISSP Certification
- What Is Kerberos?
- Top CISSP Domains
- Cyber Security Career Path
- CISSP Certification Exam Guide 2020
- Top Cyber Security Trends for 2020
- CISSP Exam Online 2020
- Compare and Contrast Physical and Environmental Security Controls
- What is information security architect?
- Certified Information Systems Security Professional (CISSP) Certification
- Top Cyber Security Jobs
- What is CISA Certification?
- What is Threat Modeling?
- Certified Information Security Manager (CISM) Certification
- Information Security Management Principles
- Network Perimeter Security Design
- Things You Must Know About Cyber Security in the Cloud
- What is ECSA?
- Why is Cybersecurity Important?
- Tips to Clear Certified Ethical Hacker (CEH) Exam
- Average Annual Salary of a CISSP Certified Professional
- “How to Become a Cyber Security Engineer? “
- Who is an Ethical Hacker?
- What are the requirements to become Cissp certified?
- The Phases of Ethical Hacking
- What is Ethical Hacking?
- Top Ethical Hacking Certifications
- Hash in Python
- How to learn Ethical Hacking?
- How to become a Ethical Hacker ? Know about the requirements to become one
- Introduction to Cyber Security | A Complete Guide
- Top Reasons to Learn Cyber Security | Everything You Need to Know to Become an Expert
- CyberSecurity Framework | How to Implement | A Definitive Guide with Best Practices [ OverView ]
- The Impact of AI and Machine Learning on Cybersecurity | Everything You Need to Know
- What is Certified Ethical Hacker (CEH) Certification and Why is it Important? [ OverView ]
- Benefits Of ECSA Certification | Everything You Need to Know | Expert’s Top Picks
- Top Most OSINT Tools – Open Source Intelligence | Expert’s Top Picks
- Cyber Security Salary in India : Everything You Need to Know
- What is Computer Security? Free Guide Tutorial & REAL-TIME Examples
- Ethical Hacker Salary and Job Description | Everything You Need to Know
- Hacking Tools and Software | All you need to know [ OverView ]
- What is DES? Free Guide Tutorial & REAL-TIME Examples
- How to Become an Ethical Hacker?
- Which are the Best Network Security Certifications?
- Cybersecurity Consultant Career Path
- The Most Effective Data Encryption Techniques
- Great CISSP Books and Study Guides for the CISSP Certification
- What Is Kerberos?
- Top CISSP Domains
- Cyber Security Career Path
- CISSP Certification Exam Guide 2020
- Top Cyber Security Trends for 2020
- CISSP Exam Online 2020
- Compare and Contrast Physical and Environmental Security Controls
- What is information security architect?
- Certified Information Systems Security Professional (CISSP) Certification
- Top Cyber Security Jobs
- What is CISA Certification?
- What is Threat Modeling?
- Certified Information Security Manager (CISM) Certification
- Information Security Management Principles
- Network Perimeter Security Design
- Things You Must Know About Cyber Security in the Cloud
- What is ECSA?
- Why is Cybersecurity Important?
- Tips to Clear Certified Ethical Hacker (CEH) Exam
- Average Annual Salary of a CISSP Certified Professional
- “How to Become a Cyber Security Engineer? “
- Who is an Ethical Hacker?
- What are the requirements to become Cissp certified?
- The Phases of Ethical Hacking
- What is Ethical Hacking?
- Top Ethical Hacking Certifications
- Hash in Python

CyberSecurity Framework | How to Implement | A Definitive Guide with Best Practices [ OverView ]
Last updated on 05th Nov 2022, Artciles, Blog, Cyber Security
- In this article you will get
- Preface to CyberSecurity Framework
- What’s a cyber security frame?
- NIST Cyber Security Framework
- 5 Functions of the Cybersecurity Framework
- 6 way for enforcing the NIST Cybersecurity Framework
- Who is impacted by the NIST Framework?
- Conclusion
Preface to CyberSecurity Framework
Cyber security is more important than ever. In thepost-COVID-19 world, cyber pitfalls are more current than ever and guarding unauthorized access to data centers and other motorized systems is commodity a business can not do without. For numerous businesses, an ad- hoc approach to cyber security is ineffective. With no clear plan in place, it’s delicate to cover and manage all implicit cyber pitfalls to your business.A cyber security frame is a great way for any business to have a clear plan to manage and alleviate cybercrime pitfalls. Another way to deal with cybercrime is to produce an incident response plan and you can read further about this in our former post.
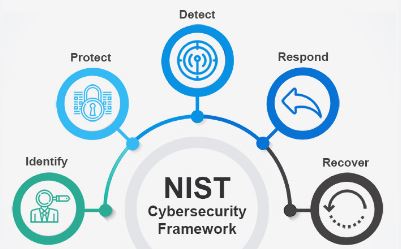
What’s a cyber security frame?
Similar fabrics reduce the company’s exposure to vulnerabilities. When duly enforced, a cyber security frame enables IT security leaders to more intelligently manage their companies ’ cyber pitfalls. An association can acclimatize being cyber security structure to meet its requirements or develop internally.
NIST Cyber Security Framework
- The National Institute of norms( NIST) first developed the Cyber Security Framework in 2014 to give guidance for associations that wish to strengthen their cyber security protections.
- The NIST Cybersecurity Framework( CSF) has lately been streamlined to interpretation1.1.
- It was created at the decree of President Barack Obama by cybersecurity professionals from government, academia and colorful diligence and was latterly erected into civil government policy by the new administration.
- NIST is the standard for CSF cyber security frame and can be acclimatized to meet the requirements of any association.
Acclimatizing the NIST CyberSecurity Framework for your business:
The content of the NIST CSF is freely available and there are numerous useful coffers available to IT directors to help them understand the content of the CSF. Creating a frame for your own business requirements is easier said than done, still in this post, we’ve taken five crucial way to make your own cyber security frame using NIST CSF. Structure.
Step 1:Set your thing pretensions
Like utmost plans, the key to success is understanding what you want to achieve by establishing this frame. That way, you can more understand and measure what success looks like.For utmost businesses, the crucial decision to make when setting pretensions is the position of threat forbearance that’s respectable to both the C- suite and your IT department.
Generally, it’ll be the responsibility of the IT operation platoon to bring together a definitive agreement that makes it clear what position of threat is respectable to your association.Setting a clear budget is also an important step and is essential when setting pretensions. Work within the limits of your own business when setting pretensions and include the fiscal constraints to achieve those pretensions.
It may make sense to run a test within the same department to find out what works and what does n’t. Once the whole business is outlined, feedback at this stage can save you precious coffers and help you streamline your pretensions to make them more precise and attainable.
Step 2:Produce a detailed profile
The coming step is to go more in- depth and outline your specific business requirements. NIST’s Framework perpetration league will help you understand your current situation and where you need to be. They’re divided into three areas:
- Threat operation process.
- Integrated risk management program.
- External participation.
Step 3:Assess your current situation
Once you have set your pretensions and created a detailed profile, it’s time to assess your current situation.The starting point for this is a detailed threat assessment to establish your current situation. You can use open source or marketable software tools able of scoring your target areas or connect with a cyber security expert to conduct an independent assessment of your current situation.
Once all areas are scored, you’ll be suitable to present findings to your crucial stakeholders, showing the security pitfalls to organizational operations, means and individualities. Vulnerabilities and pitfalls should be easily linked at this stage of the process.
Step 4:Gap Analysis and Action Plan
With a deep understanding of the pitfalls and implicit business impacts, you can move on to gap analysis.In this step of the process, you can compare your factual score with your target score. You may want to produce a heat chart to represent the results in an accessible and digestible way. Any significant differences incontinently punctuate the areas you would like to concentrate on.Work on what you need to do to ground the gap between your current score and your target score.Identify a range of conduct you can take to ameliorate your score and prioritize them through conversations with all crucial stakeholders. Specific design conditions, popular considerations and staffing situations can all affect your planning.
Step 5:Apply your action plan
With a clear picture of the current health of your deliverance, a set of organizationally aligned target pretensions, a comprehensive gap analysis and a set of remedial conduct, you’re now ready to apply NIST CSF.RMF is a process-based framework that is applied practically using several more direct specialized publications from NIST and SP 800-30 is one of them.
5 Functions of the Cybersecurity Framework
Astronomically speaking, this is to insure that your data is secure. still, more specifically, the NIST Cybersecurity Framework has five distinct functions that all work together to keep data secure. Then are five tasks and their places in maintaining cyber security.
1.Identify:
The first task, Identify, focuses on how you estimate and identify threat in your business and IT systems. This requires taking a detailed look at your current data practices. The following conduct come under identity.
- Asset Management
- Business climate
- Governance
- Threat assessment
- Threat operation strategy
- Force chain threat operation
2.Cover:
How can you cover your association from cyber security breaches? To maintain control over who’s penetrating your data, you must apply the following authorizations that are covered by the cover function.
- Identity management and access control
- Awareness and Training
- Data security
- Information protection procedures and procedures
- Conservation
- Defensive technology
3.Detect:
To insure that data protection incidents are kept to a minimum, you need ways to descry incidents when they do do. The descry function includes the following way.
- Anomalies and incidents
- Security nonstop monitoring
- Discovery process
4.Reply:
When there’s a data breach, every alternate counts. With every end nanosecond, innumerous precious lines can be compromised. As similar, you need to reply snappily to any sign of a violation by taking the following conduct.
- Response plan
- Dispatches
- Analysis
- Mitigation
- Enhancement
5.Recover:
Eventually, the final way you take in the cyber security frame are concentrated on how to recover lost or compromised data. To insure that your data is fluently recovered and safe in the future, use these way.
- Recovery plan
- Enhancement
- Dispatches
6 way for enforcing the NIST Cybersecurity Framework
1.Set your pretensions:
The first thing you should do before enforcing the NIST Framework is to set your own organizational pretensions regarding your data security. What position of threat are you comfortable with? Which areas of your business need security the most? Setting pretensions allows you to organize your conduct, establish a compass for your safety sweats, and prioritize which way are most important and should be taken first. Plus, it allows everyone in your association to be on the same runner.
2.Produce a detailed profile:
Not every business has the same cyber security conditions. Although the NIST frame is billed as a voluntary set of guidelines applicable to numerous diligence, its operation to your business may look different from your peers. The Framework perpetration categories help you identify where your business needs enhancement and what way should be taken to make those advancements a reality. The situations are listed below:
Tier 1:
Partial:This means that your cyber security practices are generally responsive to any cyber security incident.
Tier 2:
Threat- Informed:This position describes companies that may be apprehensive of certain pitfalls and are regularly planning how to respond to that threat.
Tier 3:
Unremarkable:The unremarkable league applies to companies that have easily outlined and regularly unremarkable cyber security procedures.
Tier 4:
Adaptive:Adaptive companies are visionary in terms of cyber security measures, responding to incidents rather than precluding them.
It isn’t necessary that you move from Tier 1 to Tier 4 as soon as possible. Again, progress through the situations should be when it’s the smartest decision for your company from a cost and safety viewpoint.
3.Set your current position:
Conduct an independent threat assessment so that you can determine your current data protection status. A threat assessment of your current sweats shows what’s working and what steps you need to take to get your other security sweats up to NIST norms.
One way to determine your current status is to use a software tool able of scoring your security sweats. Train staff members on how to use these tools or mate with a third party seller to perform the evaluation. Make sure the assessing parties have no previous knowledge of your target score, precluding any bias in scoring.
4.Dissect any gaps and identify necessary conduct:
Once scores are collected, they can be presented to crucial stakeholders in your business. With this knowledge, you’re equipped to identify areas of threat and produce a strategy that can close the cyber security gap.
Using these scores also makes it easier to prioritize where you need to concentrate your sweats. Addressing areas where there’s a large difference between your factual score and your target score should be your first precedence. With this essential knowledge, you can produce a strategic plan for enforcing the NIST Framework. this knowledge, you are equipped to identify areas of risk and create a strategy that can close the cyber security gap.
5.Apply your plan:
Once you have a plan, now is the time to apply it. Using the knowledge you have about the current state of your cyber security sweats, you can begin to ameliorate at threat areas. It’s also important to flash back that your cyber security plan is n’t just a box to check and forget. rather, you need to see it as an ongoing trouble that needs to be streamlined and reconsidered as your business and security features change.
As you apply your plan, you should also use this occasion to validate all processes associated with your cyber security sweats and produce training accoutrements grounded on those processes.
6.Influence NIST coffers:
Eventually, be sure to check out all the coffers NIST has to offer. These attendants will help you navigate the frame perpetration process, and determine the stylish course of action for your business. coffers, divided by function, are especially helpful for understanding the precise operation of these security sweats in your business.
Using the NIST Cybersecurity Framework is a smart way to reduce the threat of a data breach. One way to fluently align with NIST cyber security norms is by espousing secure train participating results. With erected- in security measures, you can save time by espousing a single result with multiple security functionalities. With the right strategy and a secure train sharing result enforced in your association, you’ll know that your data is sufficiently secure.
Who is impacted by the NIST Framework?
It’s easy to suppose that NIST compliance and data security only apply to IT departments. In fact, everyone in your association who owns or has access to your computer plays a part in maintaining cyber security norms. Since the frame is a voluntary cyber security measure, it’s easy for workers to feel that this isn’t their problem. clearly not so.
For illustration, an dispatch transferred over a public Wi- Fi connection at a coffee shop can have dire consequences. thus, you need everyone on board with your security sweats. While it’s imperative that your IT platoon is familiar with and laboriously aligned with the NIST frame, it’s wise for everyone in your association to be apprehensive of it and the part individualities play in maintaining norms.
The NIST Cybersecurity Framework is a set of stylish practices that associations can use to keep their data secure. Created by the National Institute of norms and Technology, the frame was designed to make cost-effective data security possible for associations of any size. While perpetration of the frame is voluntary, it’s wise for your association to apply these processes and work towards ongoing alignment. Doing so reduces the threat of cyber security breaches.
Conclusion
A cyber security frame is an essential element in dealing with the trouble of cybercrime for your business. Without clear pretensions and an understanding of the position of threat forbearance, it becomes extremely delicate to measure the success of your cyber security sweats.
By following these five clear way and acclimatizing NIST CSF to your business, you’re furnishing your business with the stylish possible path to successfully combating cybercrime, helping to cover unauthorized access to data centers and other motorized systems. are doing.Still, talk to one of our brigades moment, If you ’d like to talk to us about your cyber security requirements and learn further about erecting a cyber security structure for your business.
