- Cryptography Tutorial: What is Cryptanalysis, RC4, and CrypTool [OverView]
- Best Ethical Hacking Tools & Software for Hackers Tutorial | Ultimate Guide to Learn [UPDATED]
- Splunk Enterprise Security Tutorial | Get all the Reviews, Ratings, and Features
- CyberArk Tutorial | For Beginners [ STEP-IN ]
- Types of Wireless Attacks Tutorial
- CISSP – Asset Security Tutorial
- Information Security Governance Tutorial
- Encryption Techniques Tutorial
- IT Threats And Attacks Tutorial
- CISSP
- CISA – Protection of Information Assets Tutorial
- Security Implications Tutorial
- Information Security Management Tutorial
- WebGoat Tutorial
- Steganography Tutorial
- Actimize Tutorial
- Advanced Ethical Hacking – Burpsuite Tutorial
- Cybersecurity Tutorial
- BIOMETRICS Tutorial
- Ethical Hacking Tutorial
- Cryptography Tutorial: What is Cryptanalysis, RC4, and CrypTool [OverView]
- Best Ethical Hacking Tools & Software for Hackers Tutorial | Ultimate Guide to Learn [UPDATED]
- Splunk Enterprise Security Tutorial | Get all the Reviews, Ratings, and Features
- CyberArk Tutorial | For Beginners [ STEP-IN ]
- Types of Wireless Attacks Tutorial
- CISSP – Asset Security Tutorial
- Information Security Governance Tutorial
- Encryption Techniques Tutorial
- IT Threats And Attacks Tutorial
- CISSP
- CISA – Protection of Information Assets Tutorial
- Security Implications Tutorial
- Information Security Management Tutorial
- WebGoat Tutorial
- Steganography Tutorial
- Actimize Tutorial
- Advanced Ethical Hacking – Burpsuite Tutorial
- Cybersecurity Tutorial
- BIOMETRICS Tutorial
- Ethical Hacking Tutorial

Cybersecurity Tutorial
Last updated on 25th Sep 2020, Blog, Cyber Security, Tutorials
Cyber security refers to a body of technologies, processes and practices designed to prevent an attack, damage or unauthorized access to networks, devices, programs and data. It also can be referred to as security of information technology. Users must understand and follow the basic principles of data security, such as email attachments carefulness, strong passwords, and data backup. It is especially challenging today to enforce successful cybersecurity initiatives because more devices than people are accessible and more creative attackers.
What is Cyber Security?
Let’s understand what Cyber means. Cyber could be defined as something related to the group of computers or the internet. While security means the mechanism of protecting anything. So both the terms Cyber and security took together define the way of protecting user data from the malicious attacks that could lead to the security breach.
It is the term that has been used for a decade back after the internet started evolving like anything. By the virtue of Cyber security, any organization or any user can secure their crucial data from the hackers. Though it is concerned with hacking at some point, it actually used ethical hacking to implement Cyber security in any system.
Definition of Cyber Security
It may be defined as the process to mitigate the security threats in order to protect reputation loss, business loss or monetary loss of any organization.
The term Cyber security clearly sought that it’s a kind of security that we offer to the system that numerous users can access using the internet or intranet. There are several tools and techniques that are used to implement it. The most important fact about securing data is that it’s not a one time process but a continuous process. The system administrator has to keep things updated in order to keep the risk low.
The necessity to learn Cyber Security
A huge amount of data is collected, processed and stored on computers in government, corporate, military, financial, medical organizations and it is important to protect such data, hence cybersecurity is important. The major portion of such data is sensitive information which is to be protected from unauthorized access, if not protected the consequences could be negative. The sensitive data is transmitted across networks and other devices while carrying on business and protection of such information and the system used to process and store such information is done by cybersecurity. With the increase in the growth, volume and sophistication of cyber-attacks, those companies, and organizations protecting the data related to national security, health, financial records and other sensitive information, must take measures to protect their sensitive data and information.
Types of Cyber Security
Types of Cyber Security are nothing but the techniques used to prevent the stolen or assaulted data. It needs knowledge of possible threats to data, such as viruses and other malicious code. We all have been using computers and all types of handheld devices daily. All of these devices provide us with a lot of ease in using online services. These online services are made available to make the life of the end-users or people like us a lot easier.
Some of these services which are made available to us are:
- 1. Internet Banking
- 2. Online Shopping
- 3. Ticket Booking, etc.
Types of Cyber Attacks
Below are the different types of cyber attacks:
- 1. Denial of Service Attack (DoS)
- 2. Hacking
- 3. Malware
- 4. Phishing
- 5. Spoofing
- 6. Ransomware
- 7. Spamming
Types of Cyber Security
Some of the best Cyber Security Tools made available today are:
1. IBMQRadarAdvisor and Watson
This is by far the best security tool in use by any of the organizations. Watson, using artificial intelligence (AI), is a self-learning and self-evolving system. What it does is, before even the threat is detected it eliminates the section. The working goes as such: IBM QRadar tracks the section. It gathers information and links online, offline and within the system with that code. It formulates a strategy to encompass it and then when an incident is raised, it kills the threat. This is one of the best online incidents – kill security tools being used.
2. Wireshark
It is one of the most widely used network analyzer protocols. It assesses the vulnerable sections on the network upon which the user is working. Wireshark can gather or see the minutes of the detail and activities which are going on a network. The incoming and outgoing packets of data and the protocol which is being used in the transmission can be easily viewed. What it does is captures the live data and creates an offline analysis sheet, which helps in tracking.
3. Cryptostopper
It is one of the best tools available online right now to stop the ransomware or malware attacks on a system. What crypto stopper does is that it finds the bots which are encrypting the files and deletes them. It creates a pattern or a deception formula for the threat to latch it on by itself onto the formula, once it latches itself; crypto stopper detects and deletes that code. Cryptostopper makers tend to make a promise of a 9-second threat detection and elimination challenge. It isolates the workstation and the affected areas of the system so that the ransomware cannot manage to affect more and more areas.
4. N MAP
It is one of the many primary and open source utilities made available for network securities. NMAP is not only good with small but large networks as well. It recognizes the hosts and the receiver on a network. Along with it, it also runs on all the distributions of operating systems. It can scan hundreds and thousands of machines on a network at a single moment.
Subscribe For Free Demo
Error: Contact form not found.
5. Burp Suite
It is another web scanning algorithm security tool, which helps to scan web-based applications. The main purpose of this tool is to check and penetrate the compromised system. It checks all the surfaces which might be affected along with the sender and destination’s requests and responses for the threat. If any threat is found, it can either be quarantined or can be eliminated.
6. OpenVAS
A utility of Nessus, but very different from Nessus and Metasploit though they work the same, yet different. It is considered as one of the most stable, less loophole and use of web security tools available online at the moment.
There are two major components of OpenVAS.
- Scanner: It scans the vulnerable sections and sends a compiled report of all of it to its manager.
- Manager: It compiles all the requests which are received from the scanner and then it makes a report of all such incidences.
7. Nessus
Nessus is yet another tool that checks for malicious hackers. It scans the computers on the network for unauthorized hackers who try to access the data from the internet. On average it is considered that Nessus scans for unauthorized access for 1200 times. Apart from others, it doesn’t make assumptions that certain ports are only set for web servers like Port 80 is set for Web Server only. And it is an open-source tool, which also provides a vulnerable patching assistance facility, which further helps in providing possible solutions for the affected areas.
8. Metasploit Framework
Created by Rapid7 in Boston, Massachusetts. It is considered the best open-source framework which is in use for checking vulnerabilities. It has a command shell as it runs in Unix, so users can run their manual as well as auto commands to check and run the scripts. Metasploit Framework has some inbuilt as well as some third-party interfaces, which can be used to exploit the affected areas.
9. SolarWinds Mail Assure
It is a multi-functional tool that addresses most of the email security concerns. It has data from almost 2 million domains, which comes from 85 countries. It is also offered as Software As A Service (SAAS). It helps in the protection of the user’s devices from spams, viruses, phishing, and malware.
There are a lot many other online security tools available that can help in eliminating the risk along with the above-mentioned list. They are as follows:
- 1. Aircrack-ng
- 2. Touch Manager
- 3. MailControl
Principles of Cyber Security
Let us see, what are those 10 steps set of principles:
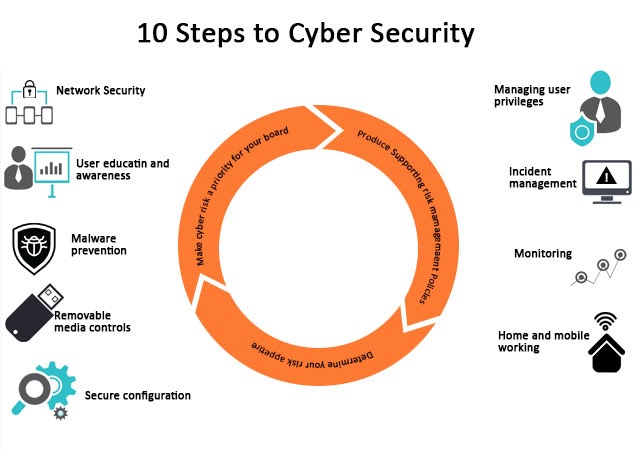
1. Risk Management Regime
A risk management regime should be set up which mainly consists of applicable policies and practices that must be established, streamlined and should effectively be communicated to all the employees, contractors and suppliers to assure that everyone is aware of the approach, e.g., how decisions are made, about risk boundaries, etc.
The risk management regime should be supported by a governance structure which should be strong enough and should constitute a board of members and senior members with expertise in a given area.
2. Secure Configuration
Establish policies that would secure the organization’s security perimeter, a secure baseline and processes should be developed for ensuring configuration management. One must also disable or remove unnecessary functionality from the system which always lies at the high end of security breaching. All the software and systems should be regularly patched to fix loopholes that lead to a security breach. Failing to any of the mentioned strategies might lead to an increased risk of compromise of systems and information.
3. Network Security
connecting to an unsecured network, for an instance – HTTP, over the internet, poses a big risk of getting your systems to be attacked or infected by bugs that lie at the other end. So policies and appropriate architectural and technical responses must be established which will serve as a baseline for networking. It will ensure the inbound and outbound networking rules that must be implemented to secure your network perimeter.
4. Managing User Privileges
All the users should be provided with reasonable (and minimal) access privileges that would allow them to just go fine with their work. If users are granted more access than they need, it will be misuse and a much bigger risk to information security. Also, the granting of highly elevated privileges should be very carefully controlled and managed.
5. User Education and Awareness
End users and organization’s people play a vital role in keeping an organization safe and secure. If end-users are not aware of the policies, risk management regime that has been set and defined by the organization, these policies will fail its purpose. End-users must be provided with security awareness training and regular training should be conducted to ensure the users are aware of the organization’s policies and threats that may lead to security breaches. On the other hand, the cybersecurity professionals of the organization should be highly trained and should be ready to combat mode at any point in time if any breaches happen.
6. Incident Management
A SIEM solution will always create security-related incidents to you. An organization should establish effective incident management policies to support the business and ensure security throughout the organization and at all the endpoints, endpoints at rest (Like desktop) as well as endpoints in motion (Like laptops, Mobile Phones, etc.).
7. Malware Prevention
It requires the establishment of policies that directly address the business processes that are at the forefront of getting infected by malware such as email, web, personal devices, USB.
8. Monitoring
A monitoring strategy and solution should be created in order with the help of which an organization will have complete visibility of the security posture. It can also be used to create another layer of security when security breaches are passed by our detection and prevention system but the monitoring solution detects it and creates a security incident.
9. Removable Media Controls
Every organization must define its removable media policies and should restrict the use of removable media as much as possible. If there are cases where their use is unavoidable, the policy should limit the types of media that can be used and the types of information that can be shared.
10. Home and Mobile Networking
When users are at home or mobile, they are no longer connecting to the company’s LAN or WAN. This poses a network risk where organizations do not have control over the internet. So risk-based policies that support mobile and home working should be established. The company can also choose to manage the user’s profile on mobile and have control of their data that is stored on mobile or Home computer.
Cyber Security Standards
There are several cybersecurity standards out there that are supposed to protect the system and its users in various ways. Based on what kind of data has to be protected, there are different standards.
Below are some of the common and important standards:
1. ISO 27001
This is one of the common standards that adhere to the organization to implement an Information security management system. It consists of the set of procedures that states the rules and requirements which have to be satisfied in order to get the organization certified with this standard. As per this standard, the organization is supposed to keep all the technology up to date, the servers should exist without vulnerabilities and the organization has to be audited after the specified interval to remain compiled to this standard. It is an international standard and every organization that serves other organizations that complies with this standard is supposed to comply with ISMS policy that is covered under ISO 27001 practice.
2. PCI DSS
PCI DSS stands for Payment Card Industry Data Security Standard. This can be considered as the standard that has to be opted by the organization that accepts payment through their gateway. The businesses that store user data like their name and card related information must have to adopt this standard in their organization. As per this compliance, the technologies used by the organization should be up-to-date and their system should continuously undergo the security assessment to ensure that it is not having any severe vulnerability. This standard was developed by the cluster of card brands(American Express, Visa, MasterCard, JCB, and Discover).
3. HIPAA
HIPAA stands for Health Insurance Portability and Accountability Act. It is the standard that the hospitals are supposed to follow to ensure that their patient’s data are fully protected and cannot be leaked anyway. In order to comply with this standard, the hospital must have a strong network security team who takes care of all the security incidents, their quarterly security reports should be healthy, all the transaction has to be done in encrypted mode and so on. This standard ensures that the critical health-related information of the patient will remain secure so that the patient can feel safe about their health.
4. FINRA
FINRA stands for Financial Industry Regulatory Authority. This standard is all about making things secure for the financial bodies that handle the funds or are aggressively engaged in financial transactions. In this standard, the system is supposed to be highly secure and to comply with this standard, various measures have to be considered in terms of data security and the user’s data protection. It is one of the most essential standards that all the organizations based on finance are supposed to comply with.
5. GDPR
GDPR stands for General Data Protection Regulation. It is a standard defined by the European government which is concerned about the data protection of all the users. In this standard, the body that has to manage the compliance has to make sure that the user’s data is secure and cannot be accessed without proper authorization. As the name states, this standard mainly focuses on the safety of the user’s data so that they can feel safe while sharing it with any of the organizations that are complying with the General Data Protection Regulation.
Cybersecurity Framework
- It may be defined as the set of policies that the organization or any eligible body must have to follow in order to comply with that particular framework or standard.
- The policies are defined by the certifying body that checks the audit report in order to finalize if the organization is actually complying with the specific framework. Based on the requirement of the organization, it depends on what kind of framework suits them or they should opt in order to ensure the business continuity in a secure manner. There will be some cases where the organization will need to comply with more than one framework to make sure that they are covering all the security aspects for their business.
- In other terms, the cybersecurity framework can also be explained as the rules that an enterprise must comply for the safety of their operations. It is not an optional thing for the organization but something mandatory where the government plays a vital role.
- For different purposes, there are different frameworks. For instance, if any organization is willing to accept the online payment, in that case, they need to comply with PCI DSS compliance before they implement the online payment mechanism in their system. For the hospitals that process the patient data has to comply with HIPAA compliance and the same way, there are several frameworks out in the market that the organization has to comply with in order to run their operations.
Types of Cybersecurity Framework
Below are some of the most important frameworks that are used very frequently all across the world.
1. NIST Framework
NIST is one of the most important frameworks that is used for improving Critical Infrastructure Security. Infrastructure security is a very crucial part of any organization and the NIST framework makes sure that there should be some strict policies existing that can lead to safeguarding the infrastructure.
2. PCI DSS
PCI DSS stands for Payment Card Industry Data Security Standard. This may be defined as the standard that an organization has to follow who is willing to accept or process online payment. This standard is concerned about protecting users from online fraud. To comply with this standard, the organization has to make sure that they are handling the user’s sensitive details very carefully, the user’s card details shouldn’t be stored unless needed, the transaction has to be done in the secure mode and so on things like this. This standards-compliance makes the users feel trust in the organization as their critical data remains safe.
3. ISO 270001
ISO 270001 is one of the main standards that falls under the domain of cybersecurity. There are some of the basic rules that have to be followed by the organization in order to comply with this standard. While applying for compliance with this standard, the organization’s system must have to be free from vulnerabilities, the organization should produce a healthy report very often, there should be a SOC setup who takes care of the network to prevent the user’s data and so on similar things.
Some of the Cybersecurity Fundamentals are given below:
1. Network Security
Network security can be defined as protecting the internal network from being attacked by malicious users. The organizations use the internal servers that have to stay protected in order to protect the system and business operations. The server has to be configured with the security aspects so that it has the capability to oppose the attack. The network security is also about protecting all the devices connected in the network like computers, printers, routers, switches and so on. The server should have a strong mechanism implemented to detect malicious activity so that it could be stopped before it harms the network. The main purpose of this network security is to ensure that the network is secure so that the entire system could stay protected.
Below are some of the technologies and tools used in network security.
- IPS & IDS – These are the tools that are used to detect malicious activity and stop it from being executed. IPS stands for intrusion prevention system and IDS stands for the intrusion detection system.
- Firewall – Firewall works are the checking point for all of the requests that hit the ports of the server to get inside the network. It ensures that the ports not in use should be closed or filtered based on the business need.
2. Security Compliances
Compliances are the policies that have to be implemented in the organization to protect their system. The compliances are a set of rules which define the security measures which the organization must have to take care of in order to stay protected. All the policies that restrict the users or the employees of the organization from performing particular activities are the outcome of security compliances. ISO 27001 is one of the most popular forms of compliance that is usually practiced by large, mid and some of the small organizations.
Below are some of the compliance that vary industry-wise.
- PCI DSS: The compliance is applicable for all of the organizations that accept online payment. It stands for Payment Card Industry Data Security Standard. It is mandatory for all of the organizations to adopt this compliance before they can bring the functionality of accepting online payment into their system.
- HIPAA: It stands for Health Insurance Portability and Accountability Act. This is the compliance that has to be followed by all of the organization that works with patients data. The purpose of this complaint is to ensure that the sensitive data of the patients are protected.
3. Web Application Security
Web Application Security may be defined as the term that defines the protection of the web application that is used by the users of that system in order to interact with them. The web application must be developed by keeping the security in mind as the vulnerability can be leveraged by attackers in order to breach the system. Compromising any vulnerability can also make a path for the attacker to attack the organization’s network. To make sure that the application is protected from vulnerabilities, there is a mechanism to perform manual and automated checks. There are several tools available that allow the cybersecurity analysts to run the scan and check if the web application is vulnerable to any attack. The OWASP Top 10 is the list of vulnerabilities that are commonly found in any application and are very severe in nature.
Below are some of the common web application vulnerabilities that are usually found in the application.
- SQL Injection: The SQL injection is the vulnerability that lets the attacker inject SQL queries in the application in order to access the data from the database without authorization.
- Cross-site scripting: This vulnerability allows an attacker to execute the Javascript at the client-side so that they can get the information stored in the client-side and also to force the client to perform a particular activity.
- Broken authentication: The is the second vulnerability mentioned in the list of OWASP top 10. Any application that allows the authentication bypass is vulnerable to this attack.
- XML External Entity: Any application that parses the XML entity from the external data is vulnerable to this attack. The hacker can gain access to sensitive files stored in the server using this weakness of the application.
Components
The cybersecurity consists of the components that are used to work with this. Those components play a crucial role in order to get leveraged by any organization.
Below are the components.
- Core: It is the first among the three components of the cybersecurity framework. As the name states, it is something that is concerned with the initial phase of the cybersecurity framework.
- Implementation Tiers: The Implementation Tiers part is the next important component of the cybersecurity framework. It is concerned with the implementation of the framework in any organization. While actually implementing the particular framework, the security professional has to be careful about the Implementation Tiers.
- Profiles: Profiles are the last component of the cybersecurity framework and concerned about the users who are supposed to be the part of the system that will be complying with the standard or the framework.
.
Applications of Cyber Security
The applications of Cyber Security are:
- Provides protection against malware, ransomware, phishing and social engineering in business.
- Cybersecurity protects the data and networks.
- The digital assets are protected by preventing unauthorized users from accessing it.
- The recovery time after a breach is improved.
- Cyber Security provides protection for end-users and their personal information.
- Confidence is improved in the organization because of cybersecurity.
Conclusion
Cyber security is a very emerging field that plays a vital role in ensuring the organization’s process continuity. It is not a single thing but comprises several approaches or techniques. Any business must have to adopt Cyber security in order to protect their user’s information and keep the business moving forward in an efficient way.

