
Best Ethical Hacking Tools & Software for Hackers Tutorial | Ultimate Guide to Learn [UPDATED]
Last updated on 11th Aug 2022, Blog, Tutorials
What is Nmap?
Nmap is a tool that ethical hackers frequently utilize. Its popularity stems from its ease of use and simple installation, as well as its robust scanning features. This nmap tutorial provides a thorough overview of the software and teaches you how to do advanced scans on your own.
Nmap is mostly used by network administrators to scan for:
- Open ports and services
- Discover services along with the versions
- Guess the operating system running on the target machine
- Get correct packet routes till the target machine
- Monitoring the hosts
- Nmap is a free and open source utility for network discovery and security auditing.
- Many systems and network administrators also found it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.
- Nmap uses raw IP packets in novel ways to find what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics.
- It was designed to fastly scan large networks, but works fine against single hosts.
Nmap Use Cases
- For example, can use Nmap to:
- Identify the live hosts on network
- Identify the open ports on network
- Identify the operating system of services on network
- Address vulnerabilities in the network infrastructure
Nmap Scan Types:
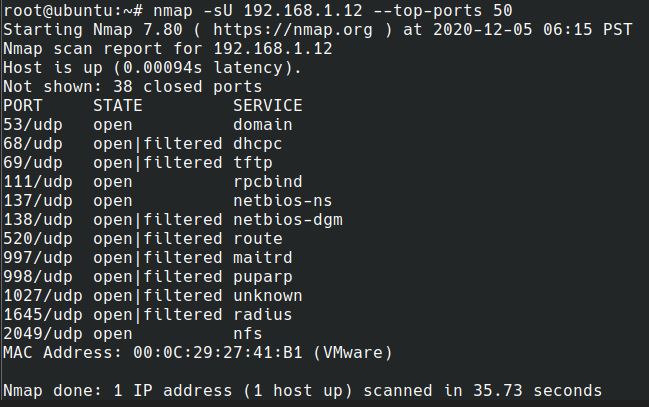
A variety of scans can be performed using Nmap. are:
TCP SCAN: It is generally used to check and finish a three-way handshake between you and a chosen target system.It is generally very noisy and can be detected with almost small to no effort. It is “noisy” because the services can log the sender IP address and might trigger Intrusion Detection Systems.
UDP SCAN: UDP scans are used to check if there is any UDP port up and listen for incoming requests on the target machine.Unlike TCP, UDP has no mechanism to respond with a positive acknowledgment, there is always a chance for a false positive in the scan results.It is used to reveal Trojan horses that might be running on UDP ports or even reveal hidden RPC services.This type of scan tends to be quite slow because machines tend to slow down their responses to this type of traffic as a precautionary measure.
SYN SCAN: This is another form of TCP scan.The difference is that, unlike a typical TCP scan, nmap creates a syn packet—the initial packet sent to establish a TCP connection.That the connection is never formed, rather the responses to these specially crafted packets are analyzed by Nmap to produce scan results.
ACK SCAN: ACK scans are used to find whether a particular port is filtered or not.This proved to be extremely helpful when trying to probe for firewalls and the existing set of rules.Simple packet filtering will permit established connections (packets with the ACK bit set), whereas a much more sophisticated stateful firewall might not.
FIN SCAN: Also a stealthy scan, like the SYN scan, but sends the TCP FIN packet instead.Most but not all computers will send an RST packet (reset packet) back if they get this input, so the FIN scan shows false positives and negatives, but it may get under the radar of some IDS programs and the other countermeasures.
NULL SCAN: It is an extremely stealthy scan and what do is as the name suggests — they set all the header fields to null.This is not a valid packet and a few targets will not know how to deal with such packets.Such targets are commonly some version of windows and scanning them with NULL packets may end up producing unreliable results.On the other side, when a system is not running windows this can be used as an efficient way to get through.
XMAS SCAN: These are sneaky in nature, just as null scans.Due to the implementation of their TCP stack, computers running Windows will not respond to Xmas scanning.The set of flags that are enabled in this packet that is sent out for the scanning gave the process its name.XMAS scans are used to create the PSH, URG and FIN flags that can be found in the TCP header.
RPC SCAN: It is used to discover machines that respond to Remote Procedure Call services (RPC).It provides commands to be run on a certain machine remotely, under a certain set of connections.RPC service can run on an array of various ports, hence, it becomes hard to infer from a normal scan whether RPC services are running or not.It is commonly a good idea to run an RPC scan from time to time to find out where these services are running.
IDLE SCAN: It is the stealthiest of all scans, as the packets are bounced off an external host.Control over the host is commonly not necessary, but the host needs to meet a particular set of conditions.It is one of the more controversial options in Nmap , it only has a use for malicious attacks.
How Does N-Map Work?
Scanning networks is a 3-step process, with Nmap carrying out the first two and leaving the ethical hacker for the third
Sending Requests: Nmap sends raw IP packets to discover the accessible hosts on a network system. According to network configurations, these packets require a response from the destination computer.
Receiving Replies: Since these requests warrant a reply, the host sends back responses highlighting the ports that can communicate with the other machines.Open ports will send some response, while the closed ones can be filtered out since they will have no response.
Analyzing Responses: Once the hackers have some data from the target’s side, they must go through vulnerable services and open ports. After this level, one can move on to the third phase in ethical hacking, gaining access to the victim machine.
features of Nmap include:
- Ability to rapidly recognize all the devices including servers, routers, switches, mobile devices, etc on one or multiple networks.
- Helps identity services running on a system including web servers, DNS servers, and the other common applications.
- Nmap can also detect the application versions with reasonable accuracy to help detect existing vulnerabilities.
- Nmap can find information about the operating system running on devices.
- It can provide detailed information like OS versions, making it simpler to plan additional approaches during penetration testing.
- During security auditing and vulnerability scanning can use Nmap to attack systems using existing scripts from the Nmap Scripting Engine.
- Nmap has a graphical user interface called Zenmap.
- It helps to develop visual mappings of a network for better usability and reporting.
Nmap Scripting Engine:
Need to use the Nmap Scripting Engine (NSE).A number of various script categories can be created with the NSE. These are:
auth – scripts that work with or bypass secure credentials on a target system .
broadcast – scripts typically used to discover hosts by broadcasting on a local network
brute – scripts that used brute force to gain access to a remote server
default – scripts set by default on Nmap based on speed, usefulness, verbosity, reliability, intrusiveness, and security
discovery – scripts that finding public registries, directory services, and SNMP-enabled devices
dos – scripts which cause denial of service. Can be used to test or attack services.
exploit – scripts designed to exploit the network vulnerabilities
external – scripts that sent data to external databases like whois-ip
fuzzer – scripts that send randomized fields within the packets
intrusive – scripts that risk crashing the targeted system and interpreted as malicious by the other administrators
malware – scripts used to test a system have been infected by malware.
safe – scripts that are not considered intrusive, designed to exploit loopholes, or crash services
version – used under the version detection feature but cannot be selected the explicitly
vuln – scripts designed to check for vulnerabilities and report them to user
Advantages of Nmap:
Nmap has advantages that make it different from other network scanning tools.Nmap is a free and open-source program.
- Some other advantages are below.
- It is used for auditing network systems as it can find new servers.
- It search for subdomain and Domain Name System
- The target host can be interacted with using the Nmap Scripting Engine (NSE).
- It finds the nature of the service in the host and performs whether the host is a mail service or a web server.
What is the Nmap aggressive mode?
IT is activated by the -A option on the command.This activates a bundle of options are:
- OS detection (-O),
- version detection (-vS),
- script scanning (-sC),
- traceroute (-traceroute).
- If you want to use those four functions, it’s a lot quicker to just type -A.
Best alternatives to Nmap:
Zenmap EDITOR’S CHOICE : Produced by developers of the Nmap.This is official GUI version of network discovery tool.,provide a respectable mapping service for free.Runs on the Windows, Linux, macOS, and Unix.
Paessler PRTG: A network monitoring package that contains SNMP for discovery and also creates a network inventory.This tool has amazing network maps.Runs on the Windows Server.
Datadog Network Device Monitoring : This module from a SaaS platform contains device discovery and ongoing status checks with the SNMP.
Site24x7 Network Monitoring: This section of a cloud platform of screening systems provides both device status checks and traffic analysis based on a network discovery routine.
Progress WhatsUp Gold: This network performance monitor used SNMP to discover all devices connected to a network, create a network inventory and topology map, and then perform the continuous monitoring.Available for the Windows Server
Conclusion:
Nmap is undoubtedly the networking “Swiss Army Knife,” quickly scanning and discovering vital information about the network, hosts, ports, firewalls, and operating systems.Nmap includes a plethora of parameters, flags, and preferences that allow system administrators to thoroughly study a network.
Are you looking training with Right Jobs?
Contact Us- Windows Azure Interview Questions and Answers
- Salesforce Architecture Tutorial
- Wrapper Class in Salesforce Tutorial
- salesforce lightning
Related Articles
Popular Courses
- VM Ware Training
11025 Learners - Microsoft Dynamics Training
12022 Learners - Siebel Training
11141 Learners
- What is Dimension Reduction? | Know the techniques
- Difference between Data Lake vs Data Warehouse: A Complete Guide For Beginners with Best Practices
- What is Dimension Reduction? | Know the techniques
- What does the Yield keyword do and How to use Yield in python ? [ OverView ]
- Agile Sprint Planning | Everything You Need to Know
