- Top 70+ Informatica Cloud Interview Questions and Answers
- 40+ [REAL-TIME] Terraform Interview Questions and Answers
- 40+ [REAL-TIME] AWS SysOps Interview Questions and Answers
- [50+] Best WebMethods Interview Questions and Answers
- Get [LATEST] Dell Boomi Interview Questions and Answers
- Browse [LATEST] Snowflake Interview Questions and Answers
- Best Application Packaging and Virtualization Interview Questions
- EMC Interview Questions and Answers
- Chef Interview Questions and Answers
- Amazon Redshift Interview Questions and Answers
- MCSA Interview Questions and Answers
- JSP Interview Questions and Answers
- AWS Architect Interview Questions and Answers
- AWS Lambda Interview Questions and Answers
- CA SiteMinder Interview Questions and Answers
- CommVault Interview Questions and Answers
- Citrix Netscaler Interview Questions and Answers
- Apigee Interview Questions and Answers
- Kernel RTOS Development Interview Questions and Answers
- Azure Data Factory Interview Questions and Answers
- Cloud Computing Interview Questions and Answers
- OpenStack Interview Questions and Answers
- Google Cloud Interview Questions and Answers
- Kubernetes Interview Questions and Answers
- NetApp Interview Questions and Answers
- AWS Interview Questions and Answers
- VMWare Interview Questions and Answers
- Docker Interview Questions and Answers
- Top 70+ Informatica Cloud Interview Questions and Answers
- 40+ [REAL-TIME] Terraform Interview Questions and Answers
- 40+ [REAL-TIME] AWS SysOps Interview Questions and Answers
- [50+] Best WebMethods Interview Questions and Answers
- Get [LATEST] Dell Boomi Interview Questions and Answers
- Browse [LATEST] Snowflake Interview Questions and Answers
- Best Application Packaging and Virtualization Interview Questions
- EMC Interview Questions and Answers
- Chef Interview Questions and Answers
- Amazon Redshift Interview Questions and Answers
- MCSA Interview Questions and Answers
- JSP Interview Questions and Answers
- AWS Architect Interview Questions and Answers
- AWS Lambda Interview Questions and Answers
- CA SiteMinder Interview Questions and Answers
- CommVault Interview Questions and Answers
- Citrix Netscaler Interview Questions and Answers
- Apigee Interview Questions and Answers
- Kernel RTOS Development Interview Questions and Answers
- Azure Data Factory Interview Questions and Answers
- Cloud Computing Interview Questions and Answers
- OpenStack Interview Questions and Answers
- Google Cloud Interview Questions and Answers
- Kubernetes Interview Questions and Answers
- NetApp Interview Questions and Answers
- AWS Interview Questions and Answers
- VMWare Interview Questions and Answers
- Docker Interview Questions and Answers

CA SiteMinder Interview Questions and Answers
Last updated on 16th Oct 2020, Blog, Cloud Computing, Interview Question
These CA Siteminder Interview questions have been designed specially to get you acquainted with the nature of questions you may encounter during your interview for the subject of CA Siteminder . As per my experience good interviewers hardly plan to ask any particular question during your interview, normally questions start with some basic concept of the subject and later they continue based on further discussion and what you answer.we are going to cover top 100 CA Siteminder Interview questions along with their detailed answers. We will be covering CA Siteminder scenario based interview questions, CA Siteminder interview questions for freshers as well as CA Siteminder interview questions and answers for experienced.
1.What are the LDAP logs?
Ans:
- Access logs (search, modify, delete–0,1,2 success,49 -unsuccess)
- error logs (replication errors and all unindexed searches).audit logs (updates)
2. What are the config files in LDAP?
Ans:
- 99user.ldif (schema information regarding objects and attributes) and
- dse.ldif (all suffix, ports, index, replication, aci, performance, plug in-information & log location).
3. What is ACI? Explain?
Ans:
ACI means access control instructions that determine what permissions are granted to users, who access a particular branch for a list of attributes in the directory.
4. What is changelog DB and retro change log?
Ans:
Updates in directory server, Master checks its updates from changelog DB. The information present in changelogDB is in binary form. To convert this binary we use retrochnagelogdb plug-in.
5. What is replication? What types do you use? What is the replication id range?
Ans:
Replication is Sinking data from one server to another server or sync data.
It contains
- master – Read&Write
- consumer – only Read
- hub – no Read & Write
The replication id range is 1 to 65534
6. What is referral?
Ans:
Transferring requests from consumer to master is also called referral. Or It reads the changelogDB and it transfers updates to master.
7. What is Schema?
Ans:
Schemas are the set of rules that describe what kind of data is stored. It helps to maintain consistency and quality of data and reduces duplication of data. Object class attribute determines schema rules the entry must follow.
8. What is SSO?
Ans:
Single Sign On is a property of access control of multiple related, but independent software systems. With this property a user logs in with a single user login to gain access to connected systems without being prompted for different usernames or passwords or in some configurations seamlessly sign on to all systems.
9. What is Siteminder or Policy Server?
Ans:
Siteminder (Policy Server) is an access management tool which provides authentication, authorization & Single Sign-On for applications which are integrated with siteminder.
10.What are authorization events?
Ans:
- OnAccesAccept
- Access Reject
11.What Are The Basic Steps That You Will Take To Stop Unauthorized Access?
Ans:
- Well, there are certain things that can be done for this. The very first thing is to secure important files with passwords. The data backup must also be protected through the same approach. It is necessary to enable the firewall as it is very helpful in this matter.
- All the accounts on a company server that are no longer in use should immediately be suspended. It is also necessary to restrict the access of data to only those who work in a similar department or those who are authorized representatives in an organization.
12.What are Authentication events?
Ans:
- OnAuthAccept
- OnAuthAttempt
- OnAuthChallenge
- OnAuthReject
- OnAuthUserNotFound
13.How is the authentication scheme context available to web servers from Siteminder?
Ans:
By SiteMinder default HTTP headers
Subscribe For Free Demo
Error: Contact form not found.
14.Types in agent keys in SiteMinder?
Ans:
- Dynamic Key
- Static Key
15.In what format policy store key is stored in SiteMinder?
Ans:
The policy store key is stored in the key stash file using a proprietary encryption technique. The policy store key is used directly or indirectly to encrypt all other keys. Policy Store key is the Policy Server’s most critical key
16.Can You Name Some Parameters That Define Ssl Session Connection?
Ans:
- Client writes Mac Secret
- Server write Mac secret
- Sequence numbers
- Client writes keys
- Server and client Random
- Initialization vectors.
17.What are the ways to End sessions in CA Siteminder?
Ans:
- User Logout of the system
- Session Times out, asking user to re-enter credentials
- User is disabled by system Manager
18.What Do You Mean By Host Intrusion Detection System? Name The Three Classes Of Intruders?
Ans:
It is basically a snapshot-based mechanism. It takes snapshots of systems and compares them with the previous snapshots. The aim is to detect whether the files have changed or if they are missing. If a problem is there, it immediately sends an alert to the administrator. The three classes of intruders are clandestine users, Misfeasor and Masquerader.
19.How do you integrate a new application?
Ans:
The new application can be integrated by Onboarding the application.
20.What According To You Are The Major Challenges In The Current Scenario For Web Access Management Systems?
Ans:
- Key issues in understanding the HTTP
- Frequent change in SSL approaches
- Centralized Remote access to machines
- System alerting approaches and mechanisms
- Updating policies
21.Named expressions enable you to?
Ans:
Expressions enable you to define reusable expressions.
22.Which feature applies to application roles?
Ans:
Application Roles define a set of users who have access to an application resource or a group of application resources.
23.What Do You Think Can Cause Vulnerabilities In Web Access Management Security?
Ans:
- Password sharing with those who are not authorized to access information
- Designs errors
- Human errors
- Complex software and applications
24.How You Will Protect A Password File?
Ans:
Password files access control and second is Hashed passwords. This is because they are not simple to crack and they cannot be judged simply.
25. What are the versions that support the upgrade of CA Identity Manager 12.6.5?
Ans:
Basically, all the r12 versions can be upgraded to 12.6.5 version. It includes the following versions,
- CA Identity Manager version r12
- CA Identity Manager version r12.6 or 12.6 SPx
- CA Identity Manager version r12.5 or 12.5 SPx
26. Describe account templates?
Ans:
- Account templates can be found in each provisioning role of role planning activity. Accounts present in managed end points and the procedure to map the user attributes to accounts will be defined by account templates.
- For each endpoint type multiple endpoints can be chosen and the assigned user of the role will receive an account in the end point.
27. What is Synchronization?
Ans:
- The Synchronization process in CA Identity Manager is used to ensure that the provisioning directory and CA Identity Manager User Store have data in common (matching data).
- There are two types of synchronization such as inbound synchronization and outbound Synchronization. These can be used to handle changes from the user store or either directory.
28.List down the types of Synchronization Tasks ?
Ans:
Synchronization tasks can be classified into two types,
- User synchronization and
- Account synchronization
29. Mention the different password management features of CA identity Manager?
Ans:
CA Identity Manager has several password management features as listed below,
- Password managers
- Password policies
- Self-service password management.
The Self-service password management has the following sub-features
- Change my password
- Self-registration
- Unlock account or Reset password
- Forgotten User ID
- Forgotten password
- Password synchronization on Endpoint accounts
30. What are the different tasks that allow administrators to manage CA Identity Manager Environment?
Ans:
- Bulk Loader tasks
- View submitted tasks
- Bulk task
- Logical Attribute Handler tasks
- Select Box Data tasks
- Email tasks
31.What Do You Know About Penetration Testing?
Ans:
It is basically a method to detect several vulnerabilities in a system. It can be done manually or through automated approaches and it aims to evaluate the system security. Just like other approaches, the prime objective of this is to ensure the system stays protected against the attacks. In this approach, if a vulnerability is found, the same is used to find others after understanding its behavior and cause.
32.What Exactly Do You Understand By Intrusion Detection?
Ans:
It is basically an approach that is useful in detecting the possible attacks by hackers and intruders and dealing with the same. It includes collecting the information and finding the possible ways to stop the hacker’s attacks. Sometimes auditing the system data can also be a part of this approach.
33.What Is Security Testing?
Ans:
It is basically an approach to check if there is any glitch in the security mechanisms of any data. It plays a vital role in securing an application simply. Security analysts can keep themselves up to date with all the major challenges that can affect their work and can detect and remove bugs immediately.
34.Name A Few Basic Methods For Effective Identity And Authenticity Management?
Ans:
Using a user name and a password approach is one of the common and in fact, the best way to manage them. In addition to this, securing a user’s personal information is also helpful in this manner. Finger touch sensors are other methods that are quite common in the present scenario.
35.What Benefits Access Management And Identity Management Can Derive?
Ans:
- Well, there are certain benefits that can simply help the organization to keep up the pace. The first, and in fact, the biggest benefit is cost saving. An organization can save a huge sum of money simply by considering this approach.
- Next big thing that can be assured is operational efficiency. In addition to this, business growth for e-commerce is another leading benefit due to which this technology is widely preferred in the current scenario.
36.What Do You Know About The Url Manipulation?
Ans:
It is an attack basically that hackers consider for manipulating the URL of a website. This is done to get access to the critical information. However, it is possible to stop them from performing this task.
37.If Web Server Is Made To Run On Default Settings, Can It Cause A Security Issue?
Ans:
Yes, there are certain chances for that. Actually web servers on default settings are vulnerable to hackers and attackers. It can even fail-secure access management and can create issues such as data loss and leakage in no time. The server settings must be customized based on software and applications that are used in an organization for the purpose of protecting the data.
38.Do You Know About Phishing On A Network? How It Can Be Harmful For An Organization?
Ans:
- It is basically an approach that hackers and other people use to get information about an organization. Basically, they create fake web pages which appear similar to that of the actual ones. They try to put them on the user’s screen and wait for them to enter their username and passwords.
- To avoid this issue, one must make sure that the web address of the URL is the same as that of the organization name. Phishing can lead to hacking accounts and unauthorized access to the information that no organization wants to share with anyone who is not an employee of them.
39. What is the Purpose and Audience of a siteminder?
Ans:
This guide outlines the important architectural and configuration decisions an organization can consider when implementing SiteMinder. This document is intended to assist with the planning the following:
- A new SiteMinder implementation
- A significant modification to an existing implementation
This guide is intended for IT personnel who are familiar with the enterprise network and access management concepts and technologies.
This guide assumes familiarity with the following:
- Application servers
- Directory servers
- Databases
- Web Servers
40. What is SiteMinder Documentation ?
Ans:
- Use a single console to view all documents published for SiteMinder.
- Use a single alphabetical index to find a topic in any document.
- Execute a full–text search of the entire documentation set.
41. What do you mean by the term protocols? Is it possible to change them once defined?
Ans:
Protocols are generally a set of rules that are applicable to a process. When it comes to security and authenticity, it is necessary for users to obey all of them and make sure that the tasks or activities they are engaged in don’t violate them. With protocols, it is almost impossible to ensure network as well as identity management. Yes, it is possible to change the protocols anytime in case the need for the same is felt.
42.what are SiteMinder Components ?
Ans:
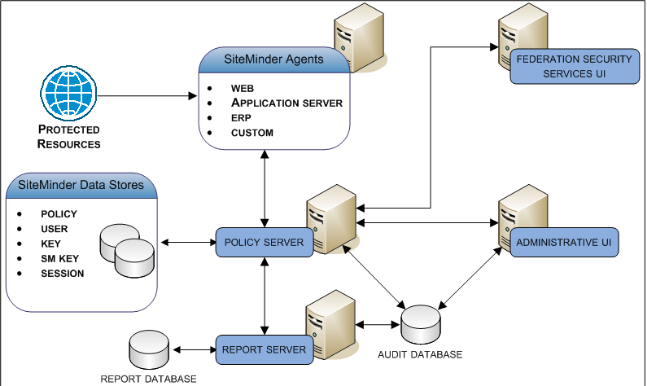
- A SiteMinder environment includes multiple components. Some components are required to secure resources, while others are optional, or only required to implement specific features. These components work with the resources, applications, directories, and databases in your organization to provide secure access to resources in your enterprise network. All SiteMinder components are supported on a number of operating environments.
- Your SiteMinder implementation is highly dependent on the environment to which you are deploying it. Your implementation does not have to reflect the following diagram. Rather, the purpose of the following diagram is to illustrate the major components in a SiteMinder environment and their general relationships with each other.
43. What is the policy server in siteminder?
Ans:
A Policy Server provides the following:
- Policy-based user management
- Authentication services
- Authorization services
- Password services
- Session management
- Auditing services
The Policy Server interacts with all other major components to perform these tasks.
44. Who are SiteMinder Agents ?
Ans:
A SiteMinder Agent can reside on a web server, a J2EE application server, an Enterprise Resource Planning (ERP) system, or custom application. An Agent acts as the Policy Enforcement Point (PEP), intercepting user requests for resources and communicating with a Policy Server to determine if the resource is protected.
If the resource is not protected, the Agent allows access. If the resource is protected, the Agent continues to communicate with the Policy Server to authenticate and authorize users. A successful authorization prompts the Agent to let the resource request proceed to the server. Agents also:
- Provide information to web applications to enable content personalization
- Cache information about authenticated users and protected resources to allow user access to resources
- Enable single sign–on (SSO)
45. Explain CA Business Intelligence ?
Ans:
- CA Business Intelligence is a set of reporting and analytic software that various CA products use for the purposes of presenting information and supporting business decisions. CA products use CA Business Intelligence to integrate, analyze, and then present, through various reporting options, information required for effective enterprise IT management.
- Included in CA Business Intelligence is BusinessObjects Enterprise XI 3.1 SP3, a complete suite of information management, reporting, and query and analysis tools. CA Business Intelligence installs BusinessObjects Enterprise XI 3.1 SP3 as a stand–alone component. In this guide, this stand–alone component is referred to as the Report Server. Installing the Report Server is a separate step within the overall SiteMinder installation process.
- Installing the Report Server separately from SiteMinder–specific components lets other CA products share the same Business Intelligence Services.
The Report Server compiles reports to help you analyze your SiteMinder environment. The purpose of this component it to create the following types of reports:
- Audit
- Policy analysis
The Report Server communicates with the following components to compile reports:
- The Central Management Server (CMS) database (report database)
- An Administrative UI
- A Policy Server
- A SiteMinder audit database
46. What are Data Stores in siteminder?
Ans:
A SiteMinder implementation contains multiple data stores. Some stores are required, while others are optional, or only required to implement specific features.
The following descriptions detail:
- If the store is required or optional
- The purpose of the store
47. How will you define an identity? Why is it necessary in an organization?
Ans:
It is basically a set of information and data that is used to identify a user or a group. With having identity, it is not possible to ensure a secure environment in an organization. In addition to this, there are certain conflicts that can be created and machines often fail to perform their task.
48. What exactly do you know about Access management and identity management?
Ans:
Access management assures web access management such as authorizing users to accomplish a task, authentication, avoiding fraud and handling other similar tasks. On the other side identity management helps clients to simply manage the identity lifecycle of those who work in an organization.
49. Name some attributes of security testing?
Ans:
These are:
- Non-repudiation
- Authentication
- Confidentiality
- Resilience
- Availability
- Authorization
- Integrity
50. If the web servers are down, Will you prefer to share the communication or personal information through your personal email account?
Ans:
Well, if the information is too sensitive, I wouldn’t go for it. However, if the same need to be conveyed on an urgent basis, I will seek the information of top management or security analysts and will proceed after getting the permissions only.
51.What are SiteMinder Audit Databases?
Ans:
By default, the Policy Server writes audit events to a text file, which is known as the Policy Server log. The purpose of audit logs is to track information about all user activity, including:
- All successful authentications
- All failed authentications
- All successful authorization attempts
- All failed authorization attempts
- All administrative login attempts
- All administrative actions, such as changes to administrator passwords, the creation of policy store objects, and changes to policy store objects
52. What are SiteMinder Key Databases?
Ans:
- Some SiteMinder features and some SiteMinder product integrations require keys for signing, verifying, encrypting, and decrypting information. The purpose of the SiteMinder key database (smokey database) is to make the private keys and the certificate authority (CA) certificates available to the environment.
- The smokey database is a separate component from a SiteMinder key store, and is a local, embedded database that does not require an external store.
- For example, use of the SiteMinder Microsoft InfoCard authentication scheme and integrating SiteMinder with Federation Security Services are both examples of an implementation that requires a smokey database.
53. Describe SiteMinder Administrative UI?
Ans:
The SiteMinder Administrative UI (Administrative UI) is a web-based administration console that is installed independent of the Policy Server. The Administrative UI functions as the primary UI in a SiteMinder implementation and is intended for managing all tasks related to access control, such as:
- Authentication and authorization policies
- Enterprise Policy Management (EPM)
- Reporting and policy analysis
The Administrative UI is intended for viewing, modifying, and deleting all Policy Server objects, except objects related to Federation Security Services (FSS). All federation-related configuration tasks are managed using the FSS Administrative UI.
54. What do you mean by Federation Security Services Administrative UI ?
Ans:
- The SiteMinder Federation Security Services Administrative UI (FSS Administrative UI) is an applet–based application that is optionally installed with the Policy Server. Federation Security Services components consist of the affiliates (consumers, service providers, resource partners) and SAML authentication schemes that you configure to support federated communication between two partners.
- The FSS Administrative UI is intended for only managing tasks related to SiteMinder Federation Security Services.
55.list some of the Web Server Vendors ?
Ans:
Some web server vendor are as follows:
- Apache HTTP Server
- Apache Tomcat
- Hewlett–Packard Company (HP) Apache
- IBM HTTP Server
- IBM Lotus Domino
- Microsoft IIS
- OracleHTTP Server
- Red Hat Apache
- Sun Java System
56. Name some domains that fall under the Identity Management?
Ans:
There are several domains and a few of them are:
- Directory management
- Access Management
- Identity Management directory
- OVD
- OID
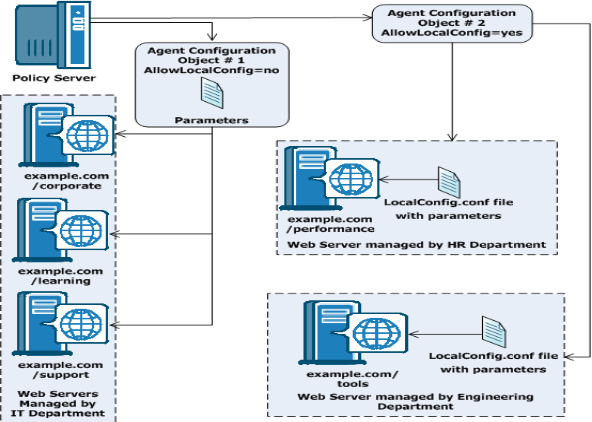
57.Central and Local Configurations Together
Ans:
You can also use a combination of central and local configuration to meet your needs. For example, you can manage three similar web servers with central configuration, while managing the other two servers with local configuration. See the following illustration for an example:
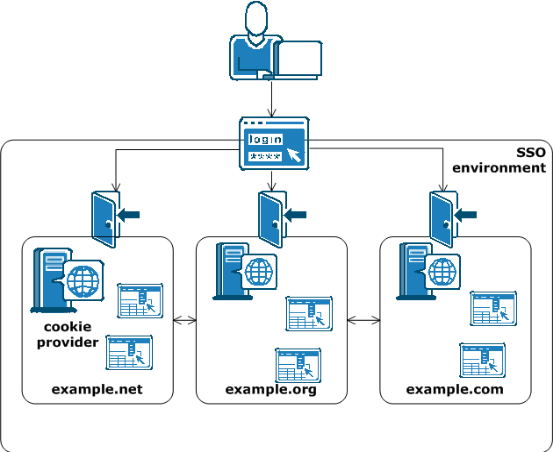
58.Will the single-sign on environment in your enterprise extend across multiple cookie domains?
Ans:
The following illustration shows an example of an SSO environment using multiple cookie domains:
- SiteMinder implements single sign-on across multiple cookie domains using a SiteMinder Web Agent configured as a cookie provider.
- The cookie domain where the cookie provider Web Agent resides is named the cookie provider domain. All the other Web Agents from the other cookie domains within the single sign-on environment, point to one cookie provider.
59.What exactly do you know about authorization? Is it different from Authentication?
Ans:
- It decides whether a user is allowed to explore some data or information is not. It is possible for them to make requests to the network administrators or departments’ heads to gain access. It is basically performed through the user’s access point as well as its URL.
- There are certain policies that restrict the access of data. Both authorization and authentication are different approaches. The common thing in both of them is they contribute together to enhance the security of the information in a business
60. How will you authenticate a person or a user?
Ans:
The first and in fact, the most common approach is passwords that they have. These are basically the secret piece of information that no one else except the authorization users have. Next approach is biometrics which is becoming more and more common in the present scenario. In addition to this, access cards can be offered to the users for allowing them to enter the restricted areas such as server rooms.
61. What is remote administration? Can it cause risk to the business data and information?
Ans:
- Remote access is a common approach. It is basically a method which enables a user to control a PC without his/her physical presence at the site.
- The device can be controlled through a remote connection which is based on the internet. Remote access is generally given to the internal resources. In case an unauthorized person outside the organization is given such access, there are certain chances of data and information leakage.
62. Is it easy to use load-balancing?
Ans:
yes in an SSO environment must refer to a single cookie provider domain. Add a load-balancer between the web servers in your cookie provider domain and the other cookie domains in your SSO environment. The following illustration shows an example: The Web Agent in the example.org cookie domain points and the Web Agent in the example.com cookie domain both point to the same cookie provider domain of example.net. A load-balancer distributes the traffic evenly between all the web servers in the example.net cookie provider domain.
63.Write detailed notes on the steps to upgrade to 12.6.5?
Ans:
- In case of pre-r12 versions, you cannot upgrade to 12.6.5 directly. Instead, you have to upgrade to r12.5, r12 or r12.5 SP1 to SP6. Even the imsconfig versions of pre-12 should be upgraded to these versions prior upgrading to 12.6.5
In order to upgrade to CA Identity Manager 12.6.5, perform the following steps,
- The upgrade prerequisites of your system should be met for the verification
- You need to upgrade provisioning components
- The CA Identity Manager on the node or cluster should be upgraded
- Perform the up gradation of report server
- Finally, carry out post-upgrade configuration
64. If you want to enter authentication information on a login page which appeared in a pop up window, would you proceed or will not enter the information? Why or why not?
Ans:
No, I will not enter the authentication information. This is because it can be a virus, a web page or which is against the security policies. Anyone must avoid entering confidential or useful information on such pop-up pages.
65. Name the two methods by which Penetrating tests can be considered?
Ans:
Black Box Testing and White Box Testing are the two methods. It can also be done through another approach which is known as Grey Box.
66. What is always a restriction on one department to access the data of another department in an organization?
Ans:
Well, obviously, for the security reasons. Let a user name Mr. X is working in the purchase department and a user Mr. Y is working in the Information Technology department. Both of them don’t need data from each other department. If they show any such intention, maybe it’s because they want to share it with anyone. Thus to avoid such a risk, organizations impose such restrictions. It helps them enhance their security up to a great extent.
67.A SiteMinder environment can operate on what FIPS modes of operation?
Ans:
- FIPS–compatibility
- FIPS–migration
- FIPS–only
68. how an environment can contain multiple blocks to address architectural consideration?
Ans:
- Redundancy
- Failover
- Capacity and scale
- Multiple cookie domains
69.The simplest SiteMinder deployment requires one ————of components?
Ans:
Block
70.what is a block component in siteminder?
Ans:
block of components is a logical combination of dependent components that include:
- A Web Agent
- A Policy Server
- A user store
- A policy store An Administrative UI
71. Do you think ISO 17799 has any benefit?
Ans:
Yes, there are certain benefits. It unveils the best practices that can be taken for information security management. All organizations irrespective of their size can go for this approach as there are a lot of useful guidelines that can simply be followed. Also, it provides useful information on securing web access management with some simple policies that can be trusted in the long run.
72. Can we open a browser using the windows adapter?
Ans:
This is a tricky question often asked by the interviewer to check your ability to identify the basic situation. Yes, like any other application browser is also a windows application. In order to open a browser from windows adapter we have to put the full path of the browser with extension. However windows adapter is not capable of interrogating the controls from the browser for that WebAdapter is required.
73. What is the benefit of using a Global web page?
Ans:
In the process of interrogating a particular web page, there is an interrogator popup which has different interrogation options. Within this option, you can see a checkbox for “Create a Global page”. So using this option you will be able to assign interrogated objects to the newly created global page.
74. What are the tasks in which identity management and authenticity management matters the most?
Ans:
There are certain tasks in an organization that are not unveiled to all the employees. They need to be kept secret. However, sometimes employees need to be engaged in them. When they are allowed broader access to the information, it’s necessary to manage the same. There are certain chances while dealing on a special project that information may leak and businesses have to bear huge loss.
75. What do you mean by the term authentication? Why is it necessary?
Ans:
It is basically a process that seems simple but in actual it is very complex. Any user has to prove his/her identity and has to provide a lot of credentials before access is allowed to the information or data. All such credentials are considered as authentic. It is necessary to make sure that no unauthorized person will gain access to confidential information or any data that can put a business on risk.
76.How do I get CA Siteminder tutorials for free?
Ans:
There are many places where you can easily get CA Siteminder Tutorials and videos for beginners, free of charge. Although, you have to make sure you are doing the Labs while reading, otherwise, it’s worthless.
77.What are the Roles and responsibilities of an CA Siteminder resource?
Ans:
There are many roles in CA Siteminder such as,
- Senior Developer (70% Job Openings).
- Manager (10% Job Openings).
- Technical Architect (20% job Openings).
78.Where can I get CA Siteminder Training?
Ans:
There are many vendors but make sure you get Lab access before and after the sessions.
79.Where can I get CA Siteminder Interview questions and Answers and how difficult are they?
Ans:
Most of the questions are quite easy, some are of advanced levels.
80.How much time does it take to learn CA Siteminder Tool?
Ans:
Well, that depends upon the quality of training, but with free tutorials, you can learn the basics in 15 hours.
81.How Can I download the software for CA Siteminder? If yes, how can I get it?
Ans:
That depends. If you are a partner with CA Siteminder then you can get a Training License for practice etc. CA Siteminder Partner for the license.
82.What about Jobs in CA Siteminder? Do we have good scope?
Ans:
CA Siteminder has been implemented in these locations: San Jose, Los Angeles, Detroit, Denver, Chicago, San Francisco, London, Toronto, Houston, Austin, Dallas, Orlando, Seattle, Washington, New York, India (Bangalore, Hyderabad, Pune, Chennai, Mumbai, Noida, Delhi, Gurgaon) Singapore, Melbourne, Dubai.
83.How can I get access to CA Siteminder Portal?
Ans:
- Normal Access.
- Partner Access
84. Name any two strategies that are useful in making web access management more secure?
Ans:
Installation of anti-spyware software and having latest security updates can help a lot in this matter.
85. What is the abbreviation for CA Siteminder?
Ans:
COMPUTER ASSOCIATES SITEMINDER.
86.What is a referral?
Ans:
Transferring requests from consumer to master is also called a referral. Or It reads the changelogDB and it transfers updates to master.


