
DevOps Interview Questions and Answers
Last updated on 25th Sep 2020, Blog, Interview Question
DevOps is not just about tools alone but it is also a set of best practices that enable us to bridge the gap between the development and operations teams in the areas of continuous integration and deployment by using an integrated set of tools to automate the software delivery.
Let’s now take a look at some of the most frequently asked questions in the DevOps interview along with the possible responses that you can give. The responses may vary based on one’s own work and experiences.
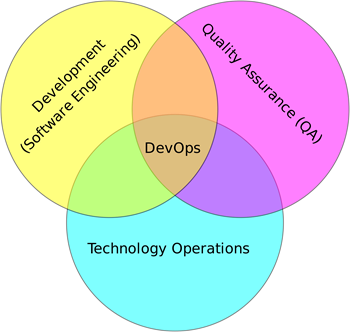
1. Explain what DevOps is?
Ans:
It is a newly emerging term in the IT field, which is nothing but a practice that emphasizes the collaboration and communication of both software developers and deployment(operations. team. It focuses on delivering software products faster and lowering the failure rate of releases.
2. Mention what the key aspects or principle behind DevOps are?
Ans:
The key aspects or principle behind DevOps is
- Infrastructure as code
- Continuous deployment
- Automation
- Monitoring
- Security
3. What are the core operations of DevOps with application development and with infrastructure?
Ans:
The core operations of DevOps are
Application development
- Code building
- Code coverage
- Unit testing
- Packaging
- Deployment
4. Explain how “Infrastructure code” is processed or executed in AWS?
Ans:
In AWS,
- The code for infrastructure will be in simple JSON format
- This JSON code will be organized into files called templates
- This templates can be deployed on AWS devops and then managed as stacks
- Later the CloudFormation service will do the Creating, deleting, updating, etc. operation in the stack
5. Explain which scripting language is most important for a DevOps engineer?
Ans:
A simpler scripting language will be better for a DevOps engineer. Python seems to be very popular.
6. Explain how DevOps is helpful to developers?
Ans:
DevOps can be helpful to developers to fix the bug and implement new features quickly. It also helps for clearer communication between the team members.
7. List out some popular tools for DevOps?
Ans:
Some of the popular tools for DevOps are
- Jenkins
- Nagios
- Monit
- ELK (Elasticsearch, Logstash, Kibana.
- Jenkins
- Docker
- Ansible
- Git
8. Mention at what instance have you used the SSH?
Ans:
I have used SSH to log into a remote machine and work on the command line. Beside this, I have also used it to tunnel into the system in order to facilitate secure encrypted communications between two untrusted hosts over an insecure network
.
9. Explain how you would handle revision (version. Control?
Ans:
My approach to handling revision control would be to post the code on SourceForge or GitHub so everyone can view it. Also, I will post the checklist from the last revision to make sure that any unsolved issues are resolved
.
10. What are the types of Http requests?
Ans:
The types of Http requests are
- GET
- HEAD
- PUT
- POST
- PATCH
- DELETE
- TRACE
- CONNECT
- OPTIONS
Subscribe For Free Demo
Error: Contact form not found.
11. Explain what you would check If a Linux-build-server suddenly starts getting slow?
Ans:
If a Linux-build-server suddenly starts getting slow, you will check for the following three things
| Application Level troubleshooting | RAM related issues, Disk I/O read-write issues, Disk Space related Issues, etc. |
|---|---|
| System Level troubleshooting | Check for Application log file OR application server log file, system performance issues, Web Server Log – check HTTP, tomcat lo, jboss, or WebLogic logs to see if the application server response/receive time is the issues for slowness, Memory Leak of any application |
| Dependent Services troubleshooting | Antivirus related issues, Firewall related issues, Network issues, SMTP server response time issues, etc. |
12.What are the key components of DevOps?
Ans:
The most important components of DevOps are:
- Continuous Integration
- Continuous Testing
- Continuous Delivery
- Continuous Monitoring
13. Name a few cloud platform which are used for DevOps Implementation
Ans:
Popular Cloud computing platform used for DevOps implementation are:
- 1.Google Cloud
- 2.Amazon Web Services
- 3.Microsoft Azure
14. Give some benefits of using Version Control system
Ans:
The version Control system allows team members to work freely on any file at any time.
- All the past versions and variants are closely packed up inside the VCS.
- A distributed VCS like helps you to store the complete history of the project so in case of a breakdown in the central server you can use your team member’s local Git repository.
- Allows you to see what exact changes are made in the file’s content
15. Explain Git Bisect
Ans:
Git bisect helps you to find the commit which introduced a bug using binary search
.
16. What is the build?
Ans:
A build is a method in which the source code is put together to check whether it works as a single unit. In the build creation process, the source code will undergo compilation, inspection, testing, and deployment.
17. What is Puppet?
Ans:
Puppet is a useful project management tool. It helps you to automate administration tasks.
18. Explain two-factor authentication
Ans:
Two-factor authentication is a security method in which the user provides two ways of identification from separate categories.
19. Explain the term ‘Canary Release’.
Ans:
A canary release is a pattern which reduces the risk of introducing a new version software into the production environment. It is done by making it available in a controlled manner to a subset of the user. Before making it available to the complete user set.
20. What types of testing is important to ensure that new service is ready for production?
Ans:
You need to conduct continuous testing to ensure that the new service is ready for production
21. What is Vagrant?
Ans:
A vagrant is a tool which can create and manage virtualized environments for testing and developing software.
22. What is the use of PTR in DNS?
Ans:
Pointer record which is also known as (PTR. is used for reverse DNS lookup.
23. What is Chef?
Ans:
It is a powerful automation platform which transforms infrastructure into code. In this tool, you can write scripts that are used to automate processes.
24. What are the prerequisites for the implementation of DevOps?\
Ans:
Following are the useful prerequisites for DevOps Implementation:
- At least one Version Control Software
- Proper communication between the team members
- Automated testing
- Automated deployment
25. Name some best practices which should be followed for DevOps success.
Ans:
Here, are essential best practices for DevOps implementation:
- The speed of delivery means time taken for any task to get them into the production environment.
- Track how many defects are found in the various
- It’s important to measure the actual or the average time that it takes to recover in case of a failure in the production environment.
- The number of bugs being reported by the customer also impact the quality of the application.
26. Explain SubGIt tool
Ans:
SubGit helps you to migrate SVN to Git. It also allows you to build a writable Git mirror of a local or remote Subversion repository.
27. Name some important network monitoring tools
Ans:
Some most prominent network monitoring tools are:
- Splunk
- Icinga 2
- Wireshark
- Nagios
- OpenNMS
28. Whether your video card can run Unity, how would you know?
Ans:
When you use a command
/usr/lib/Linux/unity_support_test-p
it will give detailed output about Unity’s requirements, and if they are met, then your video card can run unity.
29. Explain how to enable startup sound in Ubuntu?
Ans:
To enable startup sound
- Click control gear and then click on Startup Applications
- In the Startup Application Preferences window, click Add to add an entry
- Then fill the information in comment boxes like Name, Command, and Comment
/usr/bin/canberra-gtk-play—id= “desktop-login”—description= “play login sound”
- Logout and then login once you are done
You can also open it with the shortcut key Ctrl+Alt+T.
30. What is the quickest way to open an Ubuntu terminal in a particular directory?
Ans:
To open an Ubuntu terminal in a particular directory, you can use a custom keyboard shortcut.
To do that, in the command field of a new custom keyboard, type gnome – terminal – – working – directory = /path/to/dir.
31. Explain how you can get the current color of the current screen on the Ubuntu desktop?
Ans:
You can open the background image in The Gimp (image editor. and then use the eyedropper tool to select the color on a specific point. It gives you the RGB value of the color at that point.
32. Explain how you create launchers on a desktop in Ubuntu?
Ans:
To create launchers on a desktop in Ubuntu you can use
ALT+F2 then type ” gnome-desktop-item-edit –create-new~/desktop,” it will launch the old GUI dialog and create a launcher on your desktop
33. Explain what Memcached is?
Ans:
Memcached is a free and open source, high-performance, distributed memory object caching system. The primary objective of Memcached is to enhance the response time for data that can otherwise be recovered or constructed from some other source or database. It is used to avoid the need to operate SQL database or another source repetitively to fetch data for a concurrent request.
Memcached can be used for
- Social Networking->Profile Caching
- Content Aggregation-> HTML/ Page Caching
- Ad targeting-> Cookie/profile tracking
- Relationship->Session caching
- E-commerce -> Session and HTML caching
- Location-based services-> Database query scaling
- Gaming and entertainment->Session caching
Memcache helps in
- Speed up application processes
- It determines what to store and what not to
- Reduce the number of retrieval requests to the database
- Cuts down the I/O ( Input/Output. access (hard disk.
Drawback of Memcached is
- It is not a persistent data store
- Not a database
- It is not an application specific
- It cannot cache large object
34. Mention some important features of Memcached?
Ans:
Important features of Memcached includes
- CAS Tokens:A CAS token is attached to an object retrieved from a cache. You can use that token to save your updated object.
- Callbacks:It simplifies the code
- getDelayed: It reduces the delay time of your script which is waiting for results to come back from a server
- Binary protocol: You can use binary protocol instead of ASCII with the newer client
- Igbinary: Previously, a client always used to do serialization of the value with complex data, but with Memcached, you can use the igbinary option.\
35. Explain whether it is possible to share a single instance of a Memcache between multiple projects?
Ans:
Yes, it is possible to share a single instance of Memcached between multiple projects. Memcache is a memory store space, and you can run memcached on one or more servers. You can also configure your client to speak to a particular set of instances. So, you can run two different Memcache processes on the same host and yet they are completely independent. Unless, if you have partitioned your data, then it becomes necessary to know from which instance to get the data from or to put into.
36. You are having multiple Memcached servers, in which one of the memcache servers fails, and it has your data, will it ever try to get key data from that one failed server?
Ans:
The data in the failed server won’t get removed, but there is a provision for auto-failure, which you can configure for multiple nodes. Fail-over can be triggered during any socket or Memcached server level errors and not during standard client errors like adding an existing key, etc.
37. Explain how you can minimize the Memcached server outages?
Ans:
- When one instance fails, several of them go down, and this will put a larger load on the database server when lost data is reloaded as a client makes a request. To avoid this, if your code has been written to minimize cache stampedes then it will leave a minimal impact
- Another way is to bring up an instance of Memcached on a new machine using the lost machines IP address
- The code is another option to minimize server outages as it gives you the liberty to change the Memcached server list with minimal work
- Setting timeout value is another option that some Memcached clients implement for Memcached server outage. When your Memcached server goes down, the client will keep trying to send a request till the time-out limit is reached
38. Explain how you can update Memcached when data changes?
Ans:
When data changes you can update Memcached by
- Clearing the Cache proactively: Clearing the cache when an insert or update is made
- Resetting the Cache:It is similar to the first method but rather than just deleting the keys and waiting for the next request for the data to refresh the cache, reset the values after the insert or update.
39. Explain what Dogpile effect is? How can you prevent this effect?
Ans:
Dogpile effect is referred to the event when a cache expires, and websites are hit by the multiple requests made by the client at the same time. This effect can be prevented by using a semaphore lock. In this system when value expires, the first process acquires the lock and starts generating new value.
40. Explain how Memcached should not be used?
Ans:
- Memcached common misuse is to use it as a data store, and not as a cache
- Never use Memcached as the only source of the information you need to run your application. Data should always be available through another source as well
- Memcached is just a key or value store and cannot perform a query over the data or iterate over the contents to extract information
- Memcached does not offer any form of security either in encryption or authentication
When a server gets shut down does data stored in Memcached is still available?
Data stored in Memcached is not durable, so if a server is shut down or restarted, then all the data stored in Memcached is deleted.
42. Mention what the difference between Memcache and Memcached?
Ans:
- Memcache: It is an extension that allows you to work through handy object-oriented (OOPs. and procedural interfaces. It is designed to reduce database load in dynamic web applications.
- Memcached: It is an extension that uses the libmemcached library to provide API for communicating with Memcached servers. It is used to increase the dynamic web applications by alleviating database load. It is the latest API.
43. What are the different test types that Selenium supports?
Ans:
Functional – This is a type of black-box testing in which the test cases are based on the software specification.
Regression – This testing helps to find new errors, regressions, etc. in different functional and non-functional areas of code after the alteration.
Load Testing – This testing seeks to monitor the response of a device after putting a load on it. It is carried out to study the behavior of the system under certain conditions.
44. How can you access the text of a web element?
Ans:
Get command is used to retrieve the text of a specified web element. The command does not return any parameter but returns a string value.
Used for:
- Verification of messages
- Labels
- Errors displayed on the web page
Syntax:
- String Text=driver.findElement(By.id(“text”…getText(.;
45. How can you handle keyboard and mouse actions using Selenium?
Ans:
You can handle keyboard and mouse events with the advanced user interaction API. The advanced user interactions API contains actions and action classes.
| Method | Description |
|---|---|
| clickAndHold(. | Clicks without releasing the current mouse location |
| dragAndDrop(. | Performs click-and-hold at the location of the source element |
| keyDown(modifier_key. | Performs a modifier key press (ctrl, shift, Fn, etc.. |
| keyUp(modifier_key. | Performs a key release |
46. Which of these options is not a WebElement method?
Ans:
- 1.getText(.
- size(.
- 2.getTagName(.
- 3.sendKeys(.
The correct answer is B. size(.
47. When do we use findElement(. and findElements(.?
Ans:
A. findElement(.
It finds the first element in the current web page that matches the specified locator value.
Syntax:
WebElement element=driver.findElements(By.xpath(“//div[@id=‘example’]//ul//li”..;
B. findElements(.
It finds all the elements in the current web page that matches the specified locator value.
Syntax:
List elementList=driver.findElements(By.xpath(“//div[@id=‘example’]//ul//li”..;
48. What are driver.close(. and driver.quit(. in WebDriver?
Ans:
These are two different methods used to close the browser session in Selenium WebDriver:
- driver.close(. – This is used to close the current browser window on which the focus is set. In this case, there is only one browser open.
- driver.quit(. – It closes all the browser windows and ends the WebDriver session using the driver.dispose method.
49. How can you submit a form using Selenium?
Ans:
The following lines of code will let you submit a form using Selenium:
WebElement el = driver.findElement(By.id(“ElementID”..;
el.submit(.;
- 00 :
- HRS
- 50 :
- MIN
- 42
- SEC
50. Why are SSL certificates used in Chef?
Ans:
- SSL certificates are used between the Chef server and the client to ensure that each node has access to the right data.
- Every node has a private and public key pair. The public key is stored at the Chef server.
- When an SSL certificate is sent to the server, it will contain the private key of the node.
- The server compares this against the public key in order to identify the node and give the node access to the required data.
51. Which of the following commands would you use to stop or disable the ‘httpd’ service when the system boots?
Ans:
- 1.# system disable httpd.service
- 2.# system disable httpd
- 3.# systemctl disable httpd.service
The correct answer is A. # systemctl disable httpd.service
52. What is Test Kitchen in Chef?
Ans:
Test Kitchen is a command-line tool in Chef that spins up an instance and tests the cookbook on it before deploying it on the actual nodes.
Here are the most commonly used kitchen commands:
53. How does chef-apply differ from chef-client?
Ans:
- chef-apply is run on the client system.
chef-apply applies the recipe mentioned in the command on the client system.
$ chef-apply recipe_name.rb - chef-client is also run on the client system.
chef-client applies all the cookbooks in your server’s run list to the client system.
$ knife chef-client
54. What is the command to sign the requested certificates?
Ans:
For Puppet version 2.7:
#puppetca –sign hostname-of-agent
Example:
# puppetca –sign ChefAgent
# puppetca sign hostname-of-agent
Example:
# puppetca sign ChefAgent
For Puppet version 2.7:
# puppetca –sign hostname-of-agent
Example:
# puppetca –sign ChefAgent
# puppetca sign hostname-of-agent
Example:
# puppetca sign ChefAgent
55. Which open source or community tools do you use to make Puppet more powerful?
Ans:
- Changes in the configuration are tracked using Jira, and further maintenance is done through internal procedures.
- Version control takes the support of Git and Puppet’s code manager app.
- The changes are also passed through Jenkin’s continuous integration pipeline.
56. What are the resources in Puppet?
Ans:
- Resources are the basic units of any configuration management tool.
- These are the features of a node, like their software packages or services.
- A resource declaration, written in a catalog, describes the action to be performed on or with the resource.
- When the catalog is executed, it sets the node to the desired state.
57. What is a class in Puppet?
Ans:
Classes are named blocks in your manifest that configure various functionalities of the node, such as services, files, and packages.
The classes are added to a node’s catalog and are executed only when explicitly invoked.
- Class apache (String $version = ‘latest’. {
- package{
- ‘httpd’: ensure => $version,
- before => File[‘/etc/httpd.conf’],}
58. What is an Ansible role?
Ans:
An Ansible role is an independent block of tasks, variables, files, and templates embedded inside a playbook.
59. When should I use ‘{{ }}’?
Ans:
Always use {{}} for variables, unless you have a conditional statement, such as “when: …”. This is because conditional statements are run through Jinja, which resolves the expressions.
For example:
echo “This prints the value of {{foo}}”
when : foo is defined
Using brackets makes it simpler to distinguish between strings and undefined variables.
ystems, applications, and services?
Nagios enables server monitoring and the ability to check if they are sufficiently utilized or if any task failures need to be addressed.
- Verifies the status of the servers and services
- Inspects the health of your infrastructure
- Checks if applications are working correctly and web servers are reachable
60.What are the ways in which a build can be scheduled/run in Jenkins?
Ans:
- By source code management commits.
- After completion of other builds.
- Scheduled to run at a specified time.
- Manual build requests.
61. What do you mean by Nagios Remote Plugin Executor (NPRE. of Nagios?
Ans:
Nagios Remote Plugin Executor (NPRE. enables you to execute Nagios plugins on Linux/Unix machines. You can monitor remote machine metrics (disk usage, CPU load, etc..
- The check_npre plugin that resides on the local monitoring machine
- The NPRE daemon that runs on the remote Linux/Unix machine
62. What are the port numbers that Nagios uses for monitoring purposes?
Ans:
Usually, Nagios uses the following port numbers for monitoring:
63. What are active checks in Nagios?
Ans:
Active checks
- Active checks are initiated as a result of the Nagios process
- Active checks are regularly scheduled
64. What are passive checks in Nagios?
Ans:
Passive Checks:
- In passive checks, an external application checks the status of a host or service.
- It writes the results of the check to the external command file.
- Nagios reads the external command file and places the results of all passive checks into a queue for later processing.
- Nagios may send out notifications, log alerts, etc. depending on the check result information.
65. Explain the main configuration file and its location in Nagios.
Ans:
The main configuration file consists of several directives that affect how Nagios operates. The Nagios process and the CGIs read the config file.
A sample main configuration file will be placed into your settings directory:
/usr/local/Nagios/etc/resource.cfg
66. What is the Nagios Network Analyzer?
Ans:
- It provides an in-depth look at all network traffic sources and security threats.
- It provides a central view of your network traffic and bandwidth data.
- It allows system admins to gather high-level information on the health of the network.
- It enables you to be proactive in resolving outages, abnormal behavior, and threats before they affect critical business processes.
67. What are the benefits of HTTP and SSL certificate monitoring with Nagios?
Ans:
HTTP certificate monitoring
- Increased server, services, and application availability.
- Fast detection of network outages and protocol failures.
- Enables web transaction and web server performance monitoring.
SSL certificate monitoring
- Increased website availability.
- Frequent application availability.
- It provides increased security.
68. Explain virtualization with Nagios.
Ans:
Nagios can run on different virtualization platforms, like VMware, Microsoft Visual PC, Xen, Amazon EC2, etc.
- Provides the capabilities to monitor an assortment of metrics on different platforms
- Ensures quick detection of service and application failures
- Has the ability to monitor the following metrics:
- CPU Usage
- Memory
- Networking
- VM status
- Reduced administrative overhead
69. Name the three variables that affect recursion and inheritance in Nagios.
Ans:
name – Template name that can be referenced in other object definitions so it can inherit the object’s properties/variables.
use – Here, you specify the name of the template object that you
want to inherit properties/variables from.
register – This variable indicates whether or not the object definition
should be registered with Nagios.
- define some object type{
- object-specific variables ….
- name template_name
- use name_of_template
- register [0/1]
- }
70. Why is Nagios said to be object-oriented?
Ans:
Using the object configuration format, you can create object definitions that inherit properties from other object definitions. Hence, Nagios is known as object-oriented.
Types of Objects:
- Services
- Hosts
- Commands
- Time Periods
71. Explain what state stalking is in Nagios.
Ans:
- State stalking is used for logging purposes in Nagios.
- When stalking is enabled for a particular host or service, Nagios will watch that host or service very carefully.
- It will log any changes it sees in the output of check results.
- This helps in the analysis of log files.
72. What are the principles of DevOps?
Ans:
The principles behind DevOps are:
- Continuous deployment
- Infrastructure as code
- Automation
- Monitoring
- Security
73. Explain some popular tools of DevOps?
Ans:
Here are some popular tools of DevOps, such as:
- 1.Jenkins: Jenkins is a DevOps tool for monitoring the execution of repeated tasks. Jenkins is a software that allows continuous integration. And it will be installed on a server where the central build will take place.
- 2.Ansible: Ansible is a leading DevOps tool. Ansible is an open-source IT engine that automates application deployment, cloud provisioning, intra service orchestration, and other IT tools.
- 3.Nagios: Nagios is one of the more useful tools for DevOps. It can determine the errors and rectify them with the help of network, infrastructure, server, and log monitoring systems.
- 4.Docker: Docker is a high-end DevOps tool that allows building, shipping, and running distributed applications on multiple systems.
- 5.Git: Git is an open-source distributed version control system that is freely available for everyone. It is designed to handle minor to major projects with speed and efficiency.
74. What are the prerequisites for the DevOps implementation?
Ans:
Following are some useful prerequisites for DevOps implementation:
- Proper communication between the team members.
- At least one version control software.
- Automated testing.
- Automated deployment.
75.What are the core operations of DevOps with application development and infrastructure?
Ans:
The core operation of DevOps with application development and infrastructure are:
Application development
- Code building
- Code coverage
- Unit testing
- Packaging
- Deployment
Infrastructure
- Provisioning
- Configuration
- Orchestration
- Deployment
76. What are the technical and business benefits of DevOps work culture?
Ans:
Following are the technical and business benefits of DevOps work culture:
Technical benefits
- Less complex problems to fix.
- Continuous software delivery.
- Faster bugs resolution.
Business benefits
- Most stable operating environments.
- More time available to add product value.
- Faster delivery of features for customer satisfaction.
77. What is Scrum?
Ans:
Scrum is used to divide a sophisticated software and product development task into smaller chunks using iterations and increasing practices. Scrum consist of three roles, such as:
- Product owner
- Scrum master
- Team
78. What is version control?
Ans:
It is a system that records the changes to a file or set of files over time so you can recall specific versions.
The version control system consists of a central shared repository where teammates can commit the changes to a file or set of files. It allows:
- To revert the file to the previous state.
- To compare changes over time.
- To revert the entire project to a previous state.
- To see who modified something in the files.
79. Which scripting tools are used in DevOps?
Ans:
Both Python and Ruby scripting tools are used in the DevOps.
80.What is the role of AWS in DevOps?
Ans:
AWS is a cloud-based service provided by Amazon that ensures scalability through unlimited computing power and storage. It empowers IT enterprises to develop and deliver experienced products and deploy applications on the cloud.
81. Why do open source tools boost DevOps?
Ans:
Open source tools mainly used by any organization which is adapted by DevOps pipeline because DevOps came with the focus of automation in various aspects of organization build, release, change management, and infrastructure management areas.
82. What is the need for organization playbooks as the role?
Ans:
Organization playbooks as the role give more reliability and reusability to any plays while considering a task where MySQL installation should be done after the removal of Oracle DB. You need another requirement to install MySQL after java installation. In both cases, you need to install MySQL, but without roles, it needs to write playbooks separately for both use cases. Still, once using roles, the MySQL installation role is created can be utilized any number of times by invoking using logic in site.yaml.
Are you looking training with Right Jobs?
Contact Us- Jenkins Tutorial
- Docker Interview Questions and Answers
- Git Tutorial
- MS Project Interview Questions and Answers
- JIRA Interview Questions and Answers
Related Articles
Popular Courses
- Git Github Training
11025 Learners - Jenkins Training
12022 Learners - Docker Training Course Training
11141 Learners
- What is Dimension Reduction? | Know the techniques
- Difference between Data Lake vs Data Warehouse: A Complete Guide For Beginners with Best Practices
- What is Dimension Reduction? | Know the techniques
- What does the Yield keyword do and How to use Yield in python ? [ OverView ]
- Agile Sprint Planning | Everything You Need to Know


