- An Overview of AWS Machine Learning Tutorial
- Mapplet In Informatica | Purpose and Implementation of Mapplets | Expert’s Top Picks | Free Guide Tutorial
- Spring Cloud Tutorial
- Azure IoT Hub Integration Tutorial | For Beginners Learn in 1 Day FREE
- Cloud Native Microservices Tutorial | A Comprehensive Guide
- Azure Stream Analytics | Learn in 1 Day FREE Tutorial
- Azure Data Warehouse | Learn in 1 Day FREE Tutorial
- AWS Lambda Tutorial | A Guide to Creating Your First Function
- Azure Logic Apps Tutorial – A beginners Guide & its Complete Overview
- Azure Service Bus Tutorial | Complete Overview – Just An Hour for FREE
- Introduction to Azure Service Fabric Tutorial | Learn from Scratch
- Amazon CloudWatch Tutorial | Ultimate Guide to Learn [BEST & NEW]
- AWS Data Pipeline Documentation Tutorial | For Beginners Learn in 1 Day FREE
- What is Azure App Service? | A Complete Guide for Beginners
- AWS Key Management Service | All You Need to Know
- Apigee Tutorial | A Comprehensive Guide for Beginners
- Kubernetes Tutorial | Step by Step Guide to Basic
- AWS SQS – Simple Queue Service Tutorial | Quickstart – MUST READ
- AWS Glue Tutorial
- MuleSoft
- Cloud Computing Tutorial
- AWS CloudFormation tutorial
- AWS Amazon S3 Bucket Tutorial
- Kubernetes Cheat Sheet Tutorial
- AWS IAM Tutorial
- Cloud Concepts And Models Tutorial
- Cloud Network Security Tutorial
- Azure Active Directory Tutorial
- NetApp Tutorial
- OpenStack tutorial
- AWS Cheat Sheet Tutorial
- Informatica Transformations Tutorial
- AWS vs AZURE Who is The Right Cloud Platform?
- How to Host your Static Website with AWS Tutorial
- VMware Tutorial
- Edge Computing Tutorial
- Cognitive Cloud Computing Tutorial
- Serverless Computing Tutorial
- Sharepoint Tutorial
- AWS Tutorial
- Microsoft Azure Tutorial
- IOT Tutorial
- An Overview of AWS Machine Learning Tutorial
- Mapplet In Informatica | Purpose and Implementation of Mapplets | Expert’s Top Picks | Free Guide Tutorial
- Spring Cloud Tutorial
- Azure IoT Hub Integration Tutorial | For Beginners Learn in 1 Day FREE
- Cloud Native Microservices Tutorial | A Comprehensive Guide
- Azure Stream Analytics | Learn in 1 Day FREE Tutorial
- Azure Data Warehouse | Learn in 1 Day FREE Tutorial
- AWS Lambda Tutorial | A Guide to Creating Your First Function
- Azure Logic Apps Tutorial – A beginners Guide & its Complete Overview
- Azure Service Bus Tutorial | Complete Overview – Just An Hour for FREE
- Introduction to Azure Service Fabric Tutorial | Learn from Scratch
- Amazon CloudWatch Tutorial | Ultimate Guide to Learn [BEST & NEW]
- AWS Data Pipeline Documentation Tutorial | For Beginners Learn in 1 Day FREE
- What is Azure App Service? | A Complete Guide for Beginners
- AWS Key Management Service | All You Need to Know
- Apigee Tutorial | A Comprehensive Guide for Beginners
- Kubernetes Tutorial | Step by Step Guide to Basic
- AWS SQS – Simple Queue Service Tutorial | Quickstart – MUST READ
- AWS Glue Tutorial
- MuleSoft
- Cloud Computing Tutorial
- AWS CloudFormation tutorial
- AWS Amazon S3 Bucket Tutorial
- Kubernetes Cheat Sheet Tutorial
- AWS IAM Tutorial
- Cloud Concepts And Models Tutorial
- Cloud Network Security Tutorial
- Azure Active Directory Tutorial
- NetApp Tutorial
- OpenStack tutorial
- AWS Cheat Sheet Tutorial
- Informatica Transformations Tutorial
- AWS vs AZURE Who is The Right Cloud Platform?
- How to Host your Static Website with AWS Tutorial
- VMware Tutorial
- Edge Computing Tutorial
- Cognitive Cloud Computing Tutorial
- Serverless Computing Tutorial
- Sharepoint Tutorial
- AWS Tutorial
- Microsoft Azure Tutorial
- IOT Tutorial

AWS Key Management Service | All You Need to Know
Last updated on 10th Aug 2022, Blog, Cloud Computing, Tutorials
What is AWS KMS?
AWS Key Management Service (KMS) is an Amazon product that allows administrators to create, manage, and delete keys that encrypt data stored in AWS products and databases. AWS KMS can be accessed through AWS Identity and Access Management (IAM) by selecting the “Encryption Keys” section or by using the software. It gives the user centralized control over encryption keys used to define user data. The user will create, rotate, import, disable, outline, and delete usage policies for the secret writing keys and audit how to use them to encode the user information.
AWS KMS Functions :
AWS KMS functions include both management and cryptographic functions, which are listed below:
AWS KMS management functions include:
- Users can describe, create, and provide a list of master keys using AWS KMS.
- The master keys can be enabled or disabled.
- There is also the option of creating, accessing, and viewing grants for your master keys.
- Even in a master key, the automatic rotation of cryptographic materials can be easily enabled or disabled.
- There is also the option of importing cryptographic materials into AWS KMS master keys.
- Users can also tag the relevant master keys for easy identification, tracking, and categorization.
- Users can also create, delete, update, or list all aliases, which are typically associated with the respective master keys.
- Users can also delete master keys to receive notifications about the entire key lifecycle.
AWS KMS Cryptographic Functions:
- Data can be easily encrypted, re-encrypted, or decrypted in a variety of ways.
- Users can export various services to generate data encryption keys, whether the services are provided in plain text or encrypted form in the presence of a master key.
- Creating random numbers for use in various cryptographic functions
How does AWS KMS function?
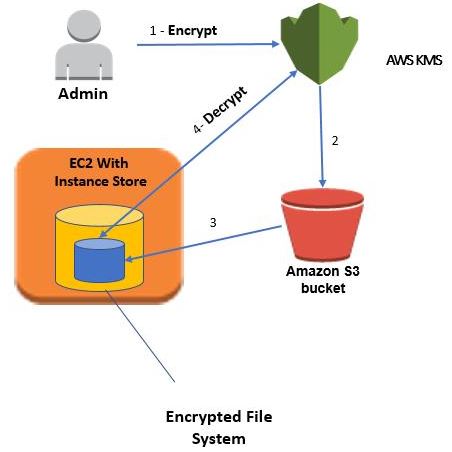
AWS Key Management Service is typically integrated with other AWS CloudTrail services in order to deliver encryption or provide various services using key usage logs to meet regulatory, auditing, and compliance requirements.AWS KMS enables you to securely store and manage your keys. The keys that are saved are known as CMKs (Customer Master Keys). The government-approved Hardware Security Modules (HSMs) will generate and protect these keys, allowing you to use them in the modules only in plaintext. You can use master keys to encrypt or decrypt data directly. You can define specific usage policies for them to determine who can use them to encrypt or decrypt data.
How to Begin with AWS KMS:
Let’s get started with KMS by looking at a code example that shows the core functions used in the AWS-KMS boilerplate repository. Let’s pretend we already have an AWS account.
Step 1: Create a Customer Master Key first (CMK)
The first step is to create a CMK, which can be skipped if you already have a setup in place. The following command will return a list of available master keys:
- $ aws kms list-keys
- {
- “Keys”:
- [{
- “KeyArn”: “arn:aws:kms:region:************:key/********-****-****-****-************”,
- “KeyId”: “********-****-****-****-************”
- }]
Step 2: Make a primary key (optional)
Generate a new data key that returns an encryption key to be used later in local data encryption using the generate-data-key command and the new CMK. Create a 256-bit long symmetrical encryption key using the key-spec parameter and the AES algorithm.
- $ aws kms create-primary
- –secondary-name ‘primary/kms-learnovita tutorial’
- –target-key-id ‘********-****-****-****-************’
Step 3: Develop a data key
Generate a data key that returns an encryption key to use later in local data encryption using the command generate-data-key and our new CMK. Create a 256-bit symmetric encryption key using the key-spec parameter and the AES algorithm.
- $ aws kms generate-data-key
- –key-id primary/kms-learnovita tutorial
- –key-spec ‘AES_256’ > ‘./.key/data_key.json’
It should be noted that the CiphertextBlob and Plaintext properties return base64 encoded data, and the KeyId must refer to the CMK rather than the generated data key.It should be noted that KMS does not keep the Data Key records on the servers. As a result, you must manage these keys on your own.
- {
- “Plaintext”: “4XY5FgHP1JyH7SkNYjY6C6gpZlWLbG0jkw06dVu0B4I=”,
- “KeyId”:”arn:aws:kms:region:
- ************:key/********-****-****-****-************”,
- “CiphertextBlob”: “AQIDAHiP2nl/OYfqakZzv1qo7ir0iHai3O1Utd4q71Louy78XgGOk8YwfNOJo77u6nxAye/RAAAAfjB8BgkqhkiG9w0BBwagbzBtAgEAMGgGCSqGSIb3DQEHATAeBglghkgBZQMEAS4wEQQMWfzIpfhT/iCHuZBdAgEQgDvFMB7ItgfGhdDdKZj6dMpzdiyYLuGKXNK2WpCrl1wi0S8uCZdtKpllJMNlhLaRVeX0ghxMqD+JK8gSfQ==”
- }
Step 4: Keep the CipherTextBlob
The next step is to extract CipherTextBlob from the base 64 decodes in data key.json and store it in your respiratory. The OpenSSL toolkit will provide a base64 implementation that we will use during decoding. The blob contains meta-data about which CMK was used when creating the data key. It allows you to retrieve the plaintext key after decryption.
- $ sed -nr ‘s/^.*”CiphertextBlob”:s*”(.*?)”.*$/1/p’ ‘./.key/data_key.json’
- | openssl base64 -d > ‘./.key/ciphertext_blob_decoded’
Step 5: Data encryption
Before proceeding to data encryption to extract the data, you must base64 decode the text key of data key.json, as we did in the previous step with the CipherTextBlob.
- $ sed -nr ‘s/^.*”Plaintext”:s*”(.*?)”.*$/1/p’ ‘./.key/data_key.json’
- | openssl base64 -d > ‘./.key/plaintext_key_decoded’
Because we’ve saved both the decoded cipher and the plaintext key in the.key/directory, we can now delete the data key.json files, which are no longer needed. To securely delete the key file, we use the shred command rather than the remove (rm) command.
- $ shred
- –iterations=100
- –remove=wipesync
- –zero ‘./.key/data_key.json’
Finally, we can start encrypting data using AES and OpenSSL. The following commands will help to do so.
- $ OpenSSL enc -e -aes256
- -kfile ‘./.key/plaintext_key_decoded’
- -in ‘.decrypted/database.json’
- -out ‘.encrypted/database.json’
Now we must delete the plaintext key and ensure that the base64 decode CipherTextBlob is correctly stored because the blob is the only way to recover and decrypt the data.
- $ shred
- –iterations=100
- –remove=wipesync
- –zero ‘./.key/plaintext_key_decoded’
Step 6: Decrypting the data
The most important aspect is data decryption. We have the deleted plaintext key after encryption; we must first restore it using the command AWS KMS decrypt.It is worth noting that the responses to the command “decrypt” return JSON objects containing the CMK Id. The query parameter allows us to return only the property in question, which is error-prone and quite messy.
- $ aws kms decrypt
- –ciphertext-blob ‘fileb://./.key/ciphertext_blob_decoded’
- –query ‘Plaintext’
- –output text | openssl base64 -d -out ‘./.key/plaintext_key_decoded’
Finally, pass the plaintext key to the OpenSSL toolkit, where we can decrypt our encrypted example data.
- $ openssl enc -d -aes256
- -kfile ‘./.key/plaintext_key_decoded’
- -in ‘.encrypted/database.json’
- -out ‘.decrypted/database.json’
Step 7: Record and audit CMK activity
AWS KMS is mostly integrated with other AWS CloudTrail services to deliver encryption or provide various services using key usage logs to meet regulatory, auditing, and compliance requirements. You can use CloudTrails to determine the IP address of the code that made the request, when it was made, who made the request, and so on.
AWS KMS Advantages:
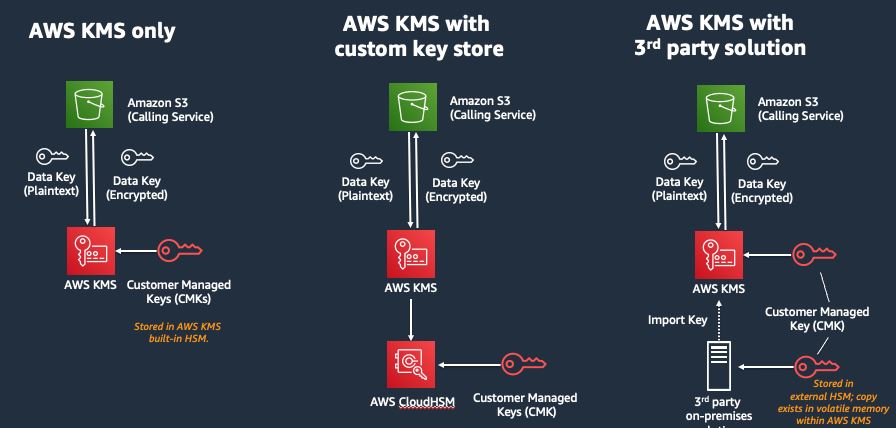
AWS KMS gives you centralized control over the encryption keys used to secure your data. It enables developers to easily add encryption functionality to their application code by encrypting and decrypting service APIs or integrating with the AWS Encryption SDK.
The following are the primary advantages of AWS KMS:
It is completely managed: This AWS Key Management Service is a fully managed service that focuses on the encryption needs of various applications in technology. It also contributes to the full-fledged delivery of physical security, availability, and maintenance of various hardware components.
Centralized Key Management: AWS KMS will grant you complete centralized control over the respective encryption keys. It will provide detailed information about the key usage in the organization to increase revenue. Users can also create, rotate, and import keys, as well as define how the policies should be used. Users can also audit their usage through the AWS Management Console, CLI, or AWS SDK.
AWS Service Integration: This AWS KMS is also integrated with various other AWS Services in order to ensure a smooth process for encrypting data that you store with the help of some services.
Encryption for all your applications: AWS KMS will assist you in effectively managing encryption keys and will also be used to store applications without revealing their storage details.
Built-in auditing: AWS Key Management Service will work with AWS CloudTrail to ensure API call logs are ready to be accessed or otherwise by KMS. With the help of these logs that meet compliance and regulatory requirements, users can also learn the details of the keys that are accessed or not, as well as the person who accessed them.
Low-cost: There will be no additional charges for the default keys in your account. The additional cost will only be paid for the master keys, which you will use for key usage or creation.
Security: Amazon Web Services KMS ensures that the encryption key is delivered or given to the most secure location. The key, such as FIPS 140-2, will be used by security modules to store the encrypted keys that you will use to save a large amount of data.
Compliance: The quality controls and security modules presented in KMS have been approved and certified, and they are completed with a compliance scheme.
Conclusion:
You now understand the fundamental theories underlying KMS as well as how to design encryption mechanisms for the project. Controlling the security breaches that occur all the time is crucial. KMS provides data scrambling, which means that only the owner of the key or password may read it. This ensures data confidentiality by preventing unauthorized users from viewing the data if they obtain access to the service or storage device. It also safeguards data integrity, preventing tampering without the owner’s knowledge. If you want to understand AWS and make a career in cloud computing, this is the place to be. Then look into our AWS Certification Training Course in your area.
