- An Overview of AWS Machine Learning Tutorial
- Mapplet In Informatica | Purpose and Implementation of Mapplets | Expert’s Top Picks | Free Guide Tutorial
- Spring Cloud Tutorial
- Azure IoT Hub Integration Tutorial | For Beginners Learn in 1 Day FREE
- Cloud Native Microservices Tutorial | A Comprehensive Guide
- Azure Stream Analytics | Learn in 1 Day FREE Tutorial
- Azure Data Warehouse | Learn in 1 Day FREE Tutorial
- AWS Lambda Tutorial | A Guide to Creating Your First Function
- Azure Logic Apps Tutorial – A beginners Guide & its Complete Overview
- Azure Service Bus Tutorial | Complete Overview – Just An Hour for FREE
- Introduction to Azure Service Fabric Tutorial | Learn from Scratch
- Amazon CloudWatch Tutorial | Ultimate Guide to Learn [BEST & NEW]
- AWS Data Pipeline Documentation Tutorial | For Beginners Learn in 1 Day FREE
- What is Azure App Service? | A Complete Guide for Beginners
- AWS Key Management Service | All You Need to Know
- Apigee Tutorial | A Comprehensive Guide for Beginners
- Kubernetes Tutorial | Step by Step Guide to Basic
- AWS SQS – Simple Queue Service Tutorial | Quickstart – MUST READ
- AWS Glue Tutorial
- MuleSoft
- Cloud Computing Tutorial
- AWS CloudFormation tutorial
- AWS Amazon S3 Bucket Tutorial
- Kubernetes Cheat Sheet Tutorial
- AWS IAM Tutorial
- Cloud Concepts And Models Tutorial
- Cloud Network Security Tutorial
- Azure Active Directory Tutorial
- NetApp Tutorial
- OpenStack tutorial
- AWS Cheat Sheet Tutorial
- Informatica Transformations Tutorial
- AWS vs AZURE Who is The Right Cloud Platform?
- How to Host your Static Website with AWS Tutorial
- VMware Tutorial
- Edge Computing Tutorial
- Cognitive Cloud Computing Tutorial
- Serverless Computing Tutorial
- Sharepoint Tutorial
- AWS Tutorial
- Microsoft Azure Tutorial
- IOT Tutorial
- An Overview of AWS Machine Learning Tutorial
- Mapplet In Informatica | Purpose and Implementation of Mapplets | Expert’s Top Picks | Free Guide Tutorial
- Spring Cloud Tutorial
- Azure IoT Hub Integration Tutorial | For Beginners Learn in 1 Day FREE
- Cloud Native Microservices Tutorial | A Comprehensive Guide
- Azure Stream Analytics | Learn in 1 Day FREE Tutorial
- Azure Data Warehouse | Learn in 1 Day FREE Tutorial
- AWS Lambda Tutorial | A Guide to Creating Your First Function
- Azure Logic Apps Tutorial – A beginners Guide & its Complete Overview
- Azure Service Bus Tutorial | Complete Overview – Just An Hour for FREE
- Introduction to Azure Service Fabric Tutorial | Learn from Scratch
- Amazon CloudWatch Tutorial | Ultimate Guide to Learn [BEST & NEW]
- AWS Data Pipeline Documentation Tutorial | For Beginners Learn in 1 Day FREE
- What is Azure App Service? | A Complete Guide for Beginners
- AWS Key Management Service | All You Need to Know
- Apigee Tutorial | A Comprehensive Guide for Beginners
- Kubernetes Tutorial | Step by Step Guide to Basic
- AWS SQS – Simple Queue Service Tutorial | Quickstart – MUST READ
- AWS Glue Tutorial
- MuleSoft
- Cloud Computing Tutorial
- AWS CloudFormation tutorial
- AWS Amazon S3 Bucket Tutorial
- Kubernetes Cheat Sheet Tutorial
- AWS IAM Tutorial
- Cloud Concepts And Models Tutorial
- Cloud Network Security Tutorial
- Azure Active Directory Tutorial
- NetApp Tutorial
- OpenStack tutorial
- AWS Cheat Sheet Tutorial
- Informatica Transformations Tutorial
- AWS vs AZURE Who is The Right Cloud Platform?
- How to Host your Static Website with AWS Tutorial
- VMware Tutorial
- Edge Computing Tutorial
- Cognitive Cloud Computing Tutorial
- Serverless Computing Tutorial
- Sharepoint Tutorial
- AWS Tutorial
- Microsoft Azure Tutorial
- IOT Tutorial
Cloud Concepts And Models Tutorial
Last updated on 29th Sep 2020, Blog, Cloud Computing, Tutorials
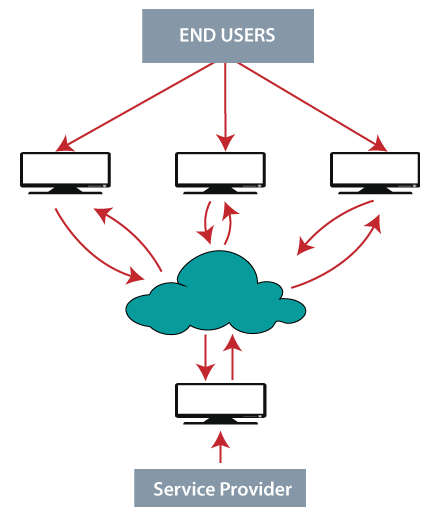
What is Cloud Computing?
Cloud computing is a service, which offers customers to work over the internet. It simply states that cloud computing means storing and accessing the data and programs over the internet rather than the computer’s hard disk. The data can be anything such as music, files, images, documents, and many more.
The user can access the data from anywhere just with the help of an internet connection. To access cloud computing, the user should register and provide with ID and password for security reasons. The speed of transfer depends on various factors such as internet speed, the capacity of the server, and many more.
The management of Cloud Computing is done by the host itself as they come up with new modifications, which continuously improves the service. The host has an ample amount of storage and fast processing servers, through which the data gets accessed very quickly. Cloud Computing’s major advantage is that the user can only concentrate on the job while leaving the problems behind.
Why Cloud Computing
For providing the small, as well as extensive IT infrastructure, IT companies follow the traditional method. That means for any type of IT Company we need a server room that is the basic need of any IT companies.
In that server room, we need so many things like a mail server, database server, networking, firewalls, routers, switches, modems, QPS (query per second), configuration system, high need speed, and the maintenance engineers.
To establish such a type of IT infrastructure, we need lots of money and resources. So, to overcome all these problems and to reduce the IT infrastructure cost, the concept of cloud computing comes into existence.
Why named Cloud
The reason behind the term “cloud” came from the design of a network that was used by the network engineers to express or represent the location of different network devices and their interconnection. The structure of this network design was similar to a cloud.
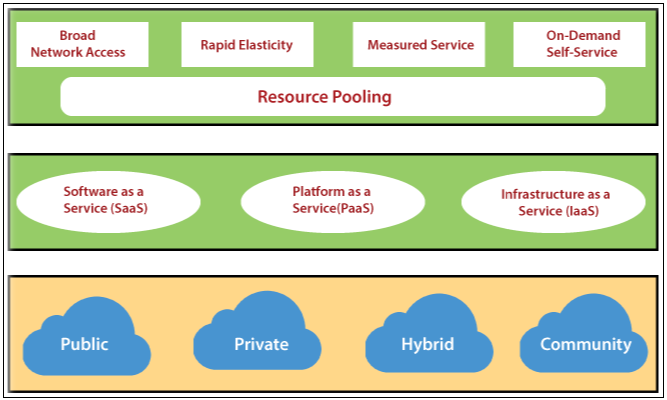
Features of Cloud Computing
- On-demand self-services: Cloud computing permits users to use web services and resources as on-demand. Any-one can login to a website at any time and use it.
- Broad network access: Cloud computing is web-based, and it can be accessed from anywhere at any time.
- Resource pooling: In cloud computing, resource pooling means allowing multiple customers to share a pool of resources.
- Rapid Elasticity: In cloud computing, scaling of the resources is very easy, no matter whether it is horizontal or vertical. Scaling of resources means the capacity of resources to deal with increasing or decreasing demand.
- Multi-sharing: In cloud computing, multi-users and applications can work more in a well defined and competent way within less cost by sharing a common infrastructure.
- Maintenance: Maintenance of cloud computing application is simple because of no need of installation on each user’s computer, and it can be accessed from various places.
Subscribe For Free Demo
Error: Contact form not found.
Architecture of Cloud Computing
The architecture of cloud computing is broadly divided into two parts :
- Front end
- Back end
Both ends are connected via a network, normally an Internet connection. The diagram below illustrates the cloud computing architecture’s visual view:
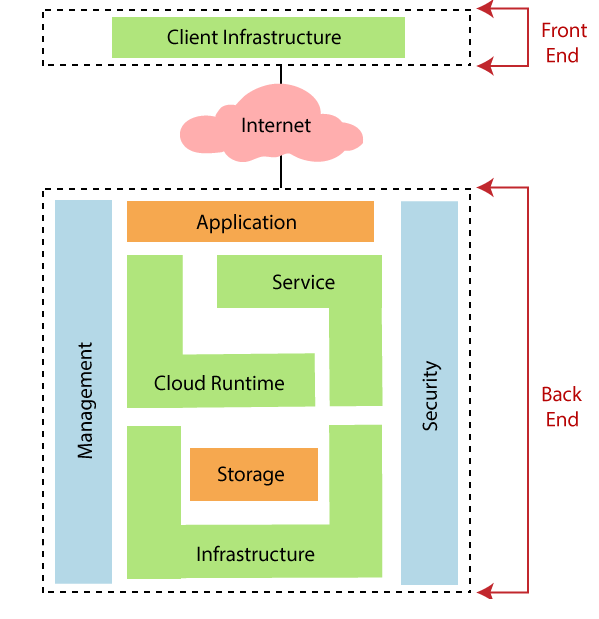
Let’s discuss both parts of cloud computing architecture in detail.
- Front end: Front end is the view that is visible to the client or a user. It is the client part of the cloud computing system. Front-end contains the user interfaces, applications, and networks that are used for accessing the cloud system. Example: a web browser.
- Back end: The back end is the cloud itself. It contains all the resources that are required to provide a cloud computing service. This end is composed of huge data storage, virtual machines, security mechanism, services, development model, etc.
Cloud service models
aaS: Cloud Service Models
There are various types of cloud service model
- Software as a service (SaaS)
- Infrastructure as a service (IaaS)
- Platform as a service (PaaS)
- Identity as a service (IDaaS)
- Network as a service (NaaS)
Let’s discuss each service model in detail.
- Software-as-a-service (SaaS): SaaS is also called “on-demand-software.” In SaaS, the consumer uses an application, but does not control the operating system, hardware, or network infrastructure on which it is running. In SaaS software and related data are centrally hosted on the cloud server. SaaS can be accessed by users using a thin client through a web browser.
Example
- Cordys
- Zynga
- Dropbox
- Animoto

Advantages of SaaS
- SaaS is easy to buy: The cost of SaaS is based on the monthly or annual fee. SaaS permits the organization to access business functionality at a low price, which is less than the licensed application.
- No need for more hardware for SaaS: For SaaS, there is no need for more hardware because the software is hosted remotely, so no need to invest in additional hardware.
- Low maintenance required for SaaS: SaaS requires low maintenance because it removes the necessity of installation, set-up, and general daily upkeep and maintenance for the organization. The cost of the initial set-up is slightly less than the enterprise software.
- No special software or hardware version required: The significant advantage of SaaS is that all users have the same version of the software and can access it via the web browser.
Disadvantages of SaaS
- Security:-Security is the main issue in SaaS. It does not provide security of the data.
- Total dependency:-SaaS is dependent on the internet. Without the internet it cannot be accessed.
- Switching between SaaS vendors is difficult:- Switching is difficult in SaaS, and due to this, the task of transferring the huge data files over the internet is slow.
Infrastructure as a Service
Infrastructure as a Service (IaaS) provides the facility of essential resources like physical machines, virtual machines, virtual storage, etc.
Infrastructure as a service (IaaS) is a form of cloud computing that offers virtualized computing resources.
Example: Amazon Web Services
It also offers other resources such as:
- Virtual Machine disk storage
- Virtual local area network
- Load balances
- IP addresses
- Software bundles
It is all about virtual servers, extended network, and remote storage. For this, no more large hardware investments, maintenance, or infrastructure are needed.
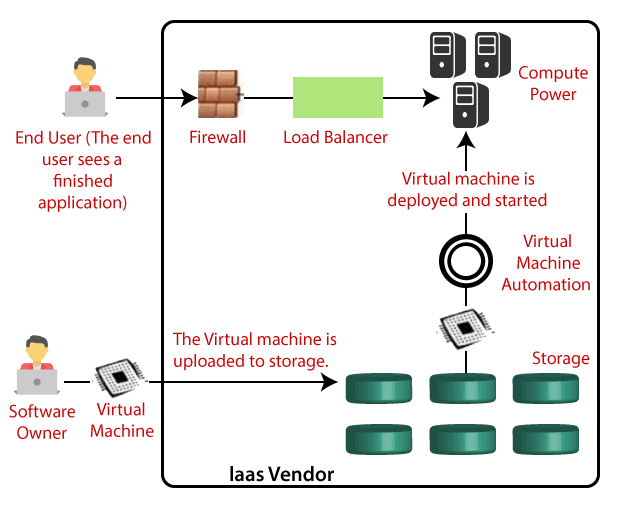
Advantages of IaaS
- We can dynamically select a CPU, memory, and storage configuration as per your requirements.
- We can easily access the broad computing power available on the IaaS cloud computing platform.
- We can easily remove the need for investment in rarely used IT hardware.
- IT infrastructure is handled by the IaaS cloud computing platform vendors.
Disadvantages of IaaS
- The IaaS cloud computing platform model totally depends on the internet.
- IaaS is also dependent on the availability of virtualization services.
- Require training to learn how to manage new infrastructure.
- Having issues regarding data security due to multitenant architecture.
Platform as a Service
Platform as a Service (PaaS)
Platform as a service (PaaS) is a programming platform for developers which is created for the programmer to develop, test, run and manage the applications.
In PaaS developers can efficiently write the application and deploy it directly into the PaaS layer. It also provides the run time environment for application development. The client uses a hosting environment for their application. The client controls the applications that run in the environment but does not control the software, hardware or network infrastructure on which they are running.

Example of PaaS
- Google apps engine (GAE)
- Windows Azure
- Sales force.com
PaaS consist of:
- Physical infrastructure:-It contains data centers, servers, storage, and network equipment.
- Intermediate layer software:–It contains operating systems, libraries, language frameworks, tools for building applications.
- User interface:– It includes a graphical user interface (GUI), a command line interface or both: the interface displays the architecture and logic of the deployment machinery.
Advantages of PaaS
- The cost of PaaS is low because the development through PaaS requires a computer and a good internet connection so less investment is required for hardware and software.
- Simple and easy to use
- PaaS is highly scalable because application development can scale from one to thousands of users without any change to the applications.
- Possibility of lower risk because there is no requirement of up-front investment in hardware and software developers only needs a PC and an internet to start building applications.
Disadvantages of PaaS
- Movement or transfer from one pass vendor’s application to another PaaS vendor will create some problems.
- Privacy of data can get hamper if it is not held within the limit of the company or organization.
Identity as a Service (IDaaS)
Identity as a service provides management of employee, client, or user’s identification-related information as a digital entity. It reduces the problem of remembering every different username and password combination when an employee leaves the company or organization.
IDaaS may contain:
- Directory services
- Registration information
- Authentication services
- Risk and monitoring
- Event monitoring
- Profile management
Employees in an organization need to login to the system to perform various jobs. These systems may be a local server or cloud base. There are various problems that an employee may be facing like:
- Remembering a different username and password sequence for accessing various services.
- If any employee leaves the organization, it is needed to ensure that each account of that user is disabled. This increases the workload on the staff of IT.
To solve this kind of problem, a new technique emerged, which is called Identity-as-a-Service (IDaaS).
Functions of Identity as a Service (IDaaS)
- Cloud-based and multi-tenant architecture:- A multi-tenant architecture offers enormous benefits such as the vendor can issue updates, security fixtures, and improve performance. It also customizes the competence or capabilities to manage access provision and governance efficiency.
- Security:–The important need of IDaaS is identity and access management. IDaaS in cloud computing offers characteristics such as multi-factor authentication, digital access cards, and biometrics. These characteristics help to quickly retrieve the information in a secure manner.
- Single sign-on federation:- It augments the experience of the end-user while maintaining security and availability of the network to use as intended. The client or user uses the secure password combination without working though to remember that it is used to access service on a regular basis.
- Analytics and intelligence:– Analytics and intelligence capabilities are used to report the users of access privileges in the context of multifaceted associations. This association is between users, their roles and responsibilities, job function, and data usage.
- Governance, risk, and compliance:-The governance, risk and compliance are supported by augmenting the automation and intelligence capabilities of an identity as a service system. This function supports an organization to define and automate the application- specific processes, which will get familiar with the access and usage pattern.
Network as a service
Network as a Service (NaaS)
Network as a service (NaaS) offers networking infrastructure to the user who doesn’t want to build their application. In this, the third party provides the network infrastructure.
NaaS consists of services such as wide-area networking connectivity, data center connectivity, bandwidth on demand, and other applications. In NaaS, products can be purchased for multiple clients for a particular period.
It contains the optimization of resource allocations by making network and computing resources as a consolidated whole.
Features of Network as a Service (NaaS)
- NaaS permits the customers to access the internet directly and securely. Also, it allows users to run custom routing protocols.
- With the help of a virtualized network, the Naas offers network service to the client. This feature benefits the customer as they don’t have to manage and worry about the infrastructure and can concentrate on developing the business.
- It helps the client by providing them with a virtual environment, which saves their substantial costs like the cost of the hardware and their maintenance.
- It also has a feature of remote access via which a customer can access the data from anywhere and at any time with the help of an internet connection.
Advantages of Network as a Service (NaaS)
The advantages of NaaS are:
- A network as a Service reduces the time taken by the staff to maintain and commit, and due to this, the business grows.
- NaaS also has a guaranteed uptime to a location. This benefits the user and is one of the primary business concerns.
- SD-WAN technologies are available at NaaS, which offers an easy to use multiple network links that support connectivity.
- SD-Wan technology also supports solving the issues regarding traffic engineering for applications such as VoIP.
loud providers are responsible for managing resources and their quality. Management of resources consists of several aspects of cloud computing such as load balancing performance, backups, deployment, capacity, etc. the management is vital to access the full functionality of resources in the cloud.
Cloud Management Task
The cloud providers perform a number of tasks to ensure the effective use of cloud resources. Discuss some of them.
1.Audit system backup is needed to audit the backups timely to assure the restoring of randomly selected files of various users. Backup can be taken in the following ways:
- The company’s backup of data, from on-site computers to cloud-based disks.
- The cloud provider’s backup of data.
2.If the cloud provider has secured the information, and the backup is taken at different locations, the client should know the details of those locations.
- Data flow of the system: – It is the duty of the managers to create a diagram that illustrates an overall system flow. The system flow defines the movement throughout the cloud solution of information belonging to an entity.
- Vender-locks in awareness and solutions: – The managers need to understand how to leave specific cloud providers services.
- Knowing the provider’s security procedures: – It is must that the manager must know the security plans of the providers for the following services.
- Multi Tenant use
- E-commerce processing
- Employee screening
- Encryption policy.
- Monitoring capacity planning and scaling capabilities: – The managers should know the capacity planning in order to assure that whether the cloud provider is fullfill the future capacity requirement for their business or not. Managers need to control the scaling capability to ensure that services can be scaled up or down as required by the customer.
- Monitor Audit log use: – To detect process failures, administrators need to review reports periodically.
- Solution testing and validation: – When the cloud provider provides the solution, it is important to test it in order to ensure that it gives the accurate result, and it is free from error. This is required for a system to be robust and reliable.
Cloud Computing Operations
Cloud computing operation is referred to as superior cloud services. Today, cloud computing operations have become very popular and widely used by many organizations just because it enables all business operations to be carried out over the Internet. Using a web application or mobile application, these operations can be carried out. There are various types of cloud operations. Some of the operations are:
- Email-marketing
- Content management
- System-wide reporting
- Online marketplace
- Accounting services
- Human resource management and recruitment systems.
Managing Cloud Operations
There are various ways to manage day-to-day cloud operations.
- Always employ the right tools and resources to perform some tasks in the cloud.
- Everything ought to be achieved at the right time and cost.
- It is necessary to pick a suitable asset for project management.
- It is necessary that the process is standardized and automated to manage repetitive tasks.
- Using an effective process will reduce the waste of effort and redundancy.
- One should maintain the quality of service to avoid re-work later.
A cloud provider is a company that provides the resources of cloud computing, such as infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS) to other businesses or individuals. The different types of cloud computing platforms are:
- Salesforce.com
- Appistry
- Appscale
- AT and T
- Engine yard
- Enomaly
- Flexiscale
- Gcloud3
- Gizmox
- Amazon web services (AWS)
- Microsoft Azure
- IBM cloud services
- Adobe creative cloud
- Rackspace
- Alibaba cloud
Salesforce.com:- Salesforce.com is a force.com development platform. This offers a user-friendly interface and lets users login, build an app, and push it in the cloud. It is a cloud computing service as a software company which is specialized in customer relationship management (CRM). It permits businesses to use cloud technology to better connect with customers, partners, and potential customers.
Features of Rackspace
- Fast drifting to the cloud.
- Supports you to formulate your business in the worst-case scenario.
- Supports you to use a combination of solid-state drives and hard drives to deliver high performance.
- Alibaba cloud:-Alibaba is the biggest Chinese cloud computing company. It is the latest platform which created a global footprint with over 1500 CDN nodes worldwide of 19 regions and 56 availability zones across more than 200 countries.
Features of Alibaba Cloud
- It supports you to achieve results faster.
- It provides the facility of backup and protection of data
- Highly stable application and reliable data storage.
Cloud Computing Security
It is an encrypted form in the cloud. Proxy and brokerage tools should be used to limit client access to shared data directly.
Security Planning
Before using a specific resource to cloud, one should need to evaluate various conditions of the resource such as:
- Choose a resource that requires moving to the cloud and evaluating its sensitivity to risk.
- Understand the data storage process of the cloud service provider and its transition to and from the cloud.
- Consider models of cloud services like IaaS, PaaS, and SaaS. Such models demand that customers should be responsible for protection at various service levels.
- Consider the type of cloud to use, such as public, private, community, or hybrid.
Understanding Security of Cloud
A specific service model describes the boundary between the customer and the responsibilities of service providers. The cloud security alliances (CSA) stack model is a model which helps to explain the limits between each service model and also shows how various functional units relate to each other.
The following figure shows the CSA stack model:
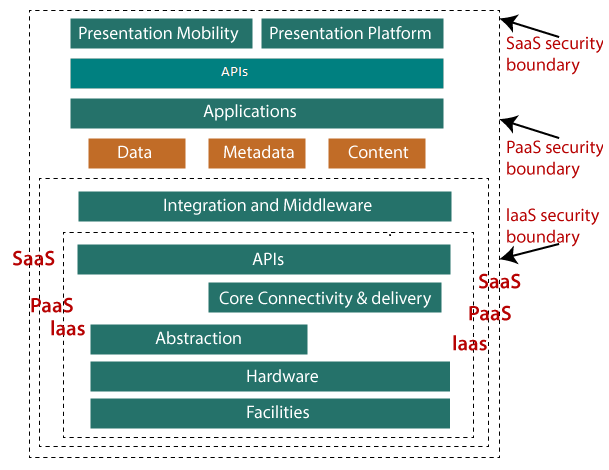
Understanding Data Security
Because all the data is transferred via the internet; data security is the main concern in the cloud. There are various key mechanisms for protecting data.
- Access control
- Auditing
- Authentication
- Authorization
Isolated Access to Data
Because the information stored in the cloud can be accessed from anywhere, we need a mechanism for isolating and shielding data from direct access by the user.
- Brokered cloud storage access is a strategy to cloud storage isolation. Two programs are being developed in this approach.
- A broker with complete processing access but no customer access.
- A proxy with no storage access, but access to both the broker and the client
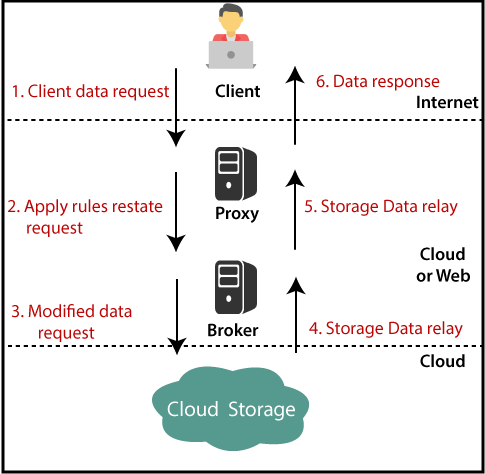
Working of Brokered Cloud Storage Access System
When the client sends a request to access data:
- The request of the client goes to the external service interface of the proxy.
- The proxy sends the request to the broker.
- The broker asks for cloud storage data.
- The proxy must give the information to the server at last.
The following figure shows the entire above steps
Cloud Computing Storage
Cloud Storage is a service that permits to store data on the offsite storage system, and it is managed by third-party and is made accessible by a web service API.
Storage Device
Storage devices are of two types:
- Block storage device
- File storage device
Block storage device: – The block storage devices permit raw storage to the clients. These raw storages are divided to create volumes.
- File storage device: – The file storage devices provide storage to the clients in the form of files, maintaining its file system. This is achieved as a network attached storage (NAS).
Cloud Storage Classes
Cloud storage can be classified into two categories
- Managed cloud storage
- Unmanaged cloud storage
Managed cloud storage: – Managedcloud storage provides online-space-storage. The cloud-managed storage system tends to be a blank disk for the user to be able to partition and format.
Unmanaged cloud storage: – Unmanaged cloud storage ensures that the customer’s data is preconfigured. The consumer cannot format, install their own file system, or alter the properties of the ride.
Creating cloud storage system: – The cloud storage system holds various copies of data on multiple servers at multiple locations. If one system fails, then it is necessary only to change the pointer to the location, where the object is stored.
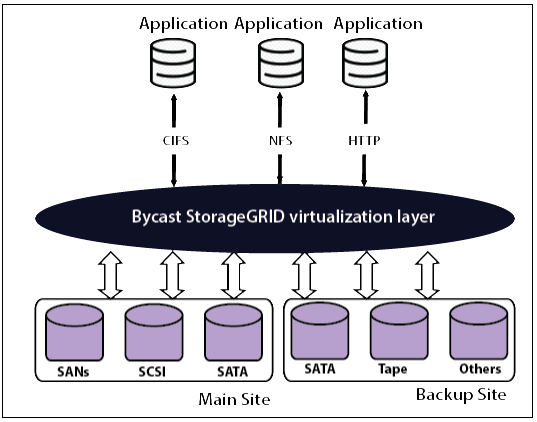
The cloud providers can use data virtualization software such as Storage-GRID to integrate storage resources into cloud storage systems. It designs a virtualization layer that fetches storage from various storage devices into a single management system. It can also handle information over the network from CIFS and NFS file systems. The following figure shows the storage-GRID virtualizing the storage into the storage cloud.
Virtual Storage Containers
The virtual storage container provides high-performance cloud storage systems. The machine, files, and other objects ‘ logical unit number (LUN) are generated in virtual storage containers.
The figure below shows a virtual storage container that defines a domain for cloud storage.
Challenges
Storing the data in the cloud is not an easy task. Apart from its flexibility and convenience, it also has various challenges faced by the customers. The customer must be able to:
- Provide supplementary storage on demand.
- Know and limit the stored data’s physical location.
- Check how data is erased.
- Have access to a recorded data storage hardware disposal system.
- Have administration access control over data.
Cloud Computing Strategy
Strategic Planning
Before investing the money for cloud computing and developing cloud applications, the user must necessarily consider the needs, strategically plan them for business needs.
Users must consider the following issues.
- Budget requirement
- Privacy and data security
- Need for training
- Data export requirement
- Data backup requirement
- Client accessing facility
Now, in order to meet all these requirements and to make fruitful use of them, it must form a mindset with strategies. So let’s talk about the different cloud planning phases that an organization has to follow before getting their hands dirty, by choosing the cloud technology.
The three main phases are:
- Strategy Phase
- Planning Phase
- Deployment Phase
Strategy phase: – In this phase, we discuss the problems that are faced by the customers.
There are two steps to check this phase:-
- The Value proposition of cloud technology: – It may contain various activities such as IT management simplification, maintaining cost reduction, low-cost outsourcing, high QoS (quality of service) outsourcing, and innovation in the business model.
- Strategy planning of cloud technology: – In this, based on the analysis of value proposition, the strategies are established, and the documentations of strategy are made according to the problems that customers might face when using cloud technology.
Planning Phase:- In the planning phase, the problem analysis and risk analysis for switching to cloud technology is examined to assure whether the customer is agreed or satisfied in meeting their business goals or not.
The steps for planning are:
- Development of business architecture.
- Development of IT architecture
- QoS development requirement.
- Development of transformation plan.
Deployment phase: – The deployment stage rotates its plans based on the above two planning phases and includes the following steps:
Step1: Selecting appropriate providers of the cloud: – The selection is based on SLA (service level agreement), which defines the level of service that cloud provider will offer.
Step2: Maintaining the technical service:-The provider must assure the appropriate maintenance of services by offering the best Quality of Service to their users.
Points to be considered before Investing in Cloud
Many IT firms and companies want to remodel their infrastructure & technology; Cloud computing has become profitable for them. It is evident that cloud technology altered the modern scenario of technology, still, it is also a truth that there are certain issues (such as security, fast internet connection, etc.) that shows its limitations. So, the users who will invest their money in cloud technology, they have to look at every aspect thoroughly.
The points are:
- Availability: – As soon as all of your business-critical data is stored in the cloud storage, it becomes essential to check whether or not the data is available, whether the data is secured, or whether there are loopholes that could become the cause of a company’s downfall. Therefore, you should stay focused as a user before signing the deal and check this aspect with the service provider.
- Compliance: – Still, it looks that all data gets stored in the cloud storage, but data is located on various servers; these servers are located in various nations of the globe. Although it has an advantage in terms of data accessibility, the user needs to be concerned about the issue of legality; the problem in the sense-users needs to test whether there will be any bias or limitation in storing a specific type of data outside national boundaries.
- Compatibility: – Before investing money in the cloud, the user must check the compatibility of the IT infrastructure of the organization.
While cloud technology provides optimal benefits for users, as vendor users also need to harvest and extract maximum cloud usage. In addition, it has to bear in mind that the organization’s employees have to cope with the cloud technology infrastructure.
- Monitoring: When you put the data on cloud storage, the cloud service provider takes the responsibility and control of your data. Due to this reason, monitoring becomes a problem. Since complete monitoring of data is possible, so users should make sure that appropriate monitoring of data is allowed by the providers based on user requirements.
Strategy Life Cycle
The cloud technology implementation approach includes the following:
- Planning for utilizing cloud technology.
- Capabilities of an enterprise.
- Target architecture required
- Gap analysis and transition planning
- Planning to implement cloud
- Governance and significance of SOA (service-oriented architecture).
Mobile Cloud Computing
Mobile Cloud Computing is a system where you can use your mobile phone to access the cloud remotely. Both mobile phones and internet connections are required. In mobile cloud computing, the customer can access the data from anywhere at any time very easily. It provides the mobile network operator with many business opportunities along with cloud providers. The objective of Mobile Cloud Computing is to permit the access of cloud from the mobile phone by offering an excellent experience to the customers and to promote it. Mobile cloud computing is cost-effective and also saves time. It is economical because as you go theory, the sites are focused on compensation.
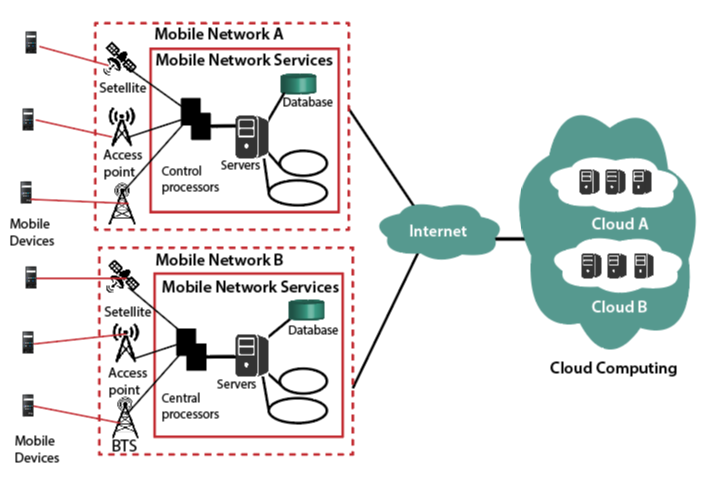
Architecture of Mobile Cloud Computing
Mobile Cloud Computing works on the computational augmentation approach, which is executed remotely rather than executing on the device. With the help of computational augmentation, the mobile device can use the computational resources of varied cloud-based resources Mobile cloud computing consists of four types of remote mobile cloud network resources, nearby mobile computing, local mobile computing and hybrid cloud. Big companies like Amazon are in mobile communities at a distance, while small-scale organizations are part of local immobile computing bodies.
The following figure shows the architecture of mobile cloud computing:
Why Choosing Mobile Cloud Computing
The reasons why we choose mobile cloud computing are:
- Rapid development:-cloud companies are creating mobile apps that help consumers on a daily basis. This application comes up with refinement which continuously enhances the performance of the applications. As companies are improving or developing their applications regularly, this leads to the fact that there is a speedy development in mobile cloud computing.
- Flexible: – Flexibility is another issue to choose from mobile cloud computing. The built-in technologies are more comprehensive and versatile. There are different types of approaches and devices that help in mobile computing. In MCC, the customer can select the service which needs for their business, which makes it more flexible.
- Secure: – mobile cloud computing is robust and keeps all the data secure in the cloud. That backed up can safely fetch at any time. These applications are protected by a password, so if in case the mobile is lost, the cloud does not face any risk. The method is very simple from one device to another, and no information is lost.
How to support Mobile Cloud Computing
- Functionality outsourcing: – Tasks such as video indexing and offshore speech recognition to the less demanding role of the cloud to be done on the device itself.
- Web analytics: – In web analytics, the company collects information and analyses it for the product improvement and application upgrades. To make products better and make the mobile application capture, save and render information about the interface of the user, the company continuously puts lots of effort.
- Hosting services: – Mobile cloud computing customers can exploit a certain amount of control in the operating system to guarantee less configuration problems. It is one of the best ways to advantage the cloud.
- Hardware augmentation: – A clone of mobile software is developed to expand further high-level application support that was not previously possible due to its processing ability.
Advantages of Cloud Computing
- Flexible: – Mobile cloud computing is flexible because it permits accessing data from anywhere at any time. The customer only needs an internet connection and a device through which they can get the cloud data easily.
- Multiple platform availability: – The cloud computing application introduces by the company, used in various platforms like Android, IOS, and many more. Regardless of the system, the cloud can easily access and change.
- Economical: – Mobile cloud computing removes the cost of hardware and it is one of the most cost-effective methods use and maintain. Mobile cloud computing costs the user only has to pay for what they used.
- Backup and recovery:- In mobile cloud computing, the data backup can take easily, and data retrieving is also easy when needed.
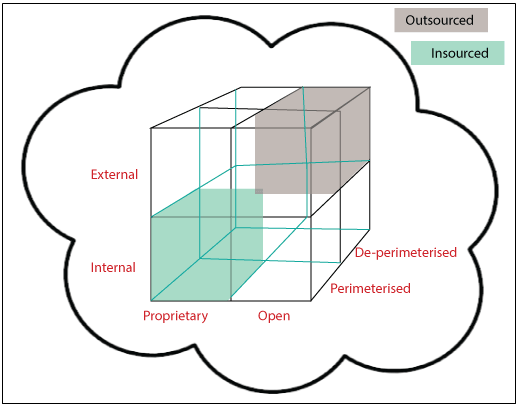
Cloud Cube Model
The Cloud computing model is developed by the Jericho forum. It helps to classify the network of cloud-based systems on the four-dimensional factor: Internal/External, proprietary/open, de-parameterized/ parameterized, and insourced/ outsourced.
Introduction to Cloud Cube
The Cloud cube model helps to categorize the network of cloud-based on the four-dimensional factor. The main motive of the cloud model is to secure and protect the cloud network. The cloud model supports choosing cloud creation for the security association. It also helps IT managers, organizations, and business leaders by offering a safe and protected network.
Security is an essential aspect for cloud users, and most of the cloud providers understand it. The customer should also take care of that; the selected cloud formation fulfills the regulatory and location needs. They also need one thing in their mind that if cloud providers stop offering the services, where else they can move.
There are three service models which consists of:
- SaaS
- PaaS
- IaaS
There are four deployment models also.
- Public cloud
- Private cloud
- Community cloud
- Hybrid cloud
The models are flexible, user-friendly, and offer many benefits to cloud users.
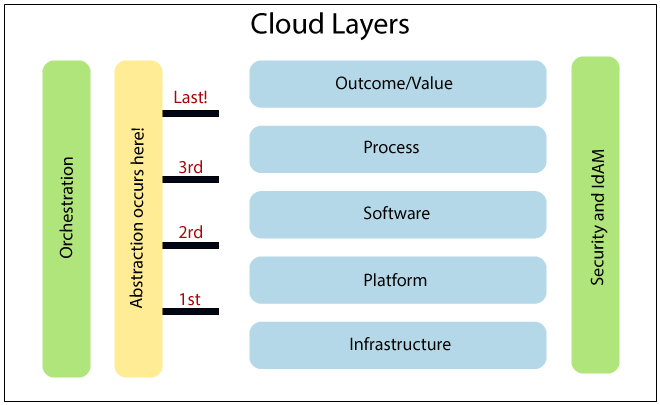
The following figure shows the cloud layers when the clouds operates.
How is Data Secured in the Cloud Cube Model?
There are various steps and points you should keep in your mind while securing your data in a cloud cube model.
- The categorization of the data, the user must know what rules must be applied to secure and protect it.
- It should make sure that the data exist only in particular trust levels.
- It should examine what regulatory compliance and constraints are applicable. For example: – The data is kept in a specific limit and whether it has to stay in the secure harbor or not.
When the data is categorized and can put in the needed zone, the assigned person is in a position to decide the following aspects-
- The processes and data, which are to be shifted in the cloud.
- At what level the customer wants to operate in the cloud. Maybe it is infrastructure, platform, and software.
- The cloud formations fulfill the requirements.
- In a cloud, the level of operation can be different as per the requirement.
The following figure shows the cloud layers, where the cloud operates:
Dimensions of Cloud Cube Model
There are following four dimensions in the Cloud cube model.
- Internal/External
- Proprietary/open
- De-parameterized/parameterized
- Insourced/outsourced dimension
Internal/External: – Internal/External is the most common form of the cloud. It describes the physical location of the data. It agrees whether the data exists inside or outside of your organization’s limit. In this, the data that is stored by the help of private cloud deployment will be referred to as internal, and the data outside the cloud will be referred to as external.
Proprietary/Open: – The second dimension of cloud formation is proprietary/open. It defines the state of ownership of the cloud technology and interfaces. It also defines the level of incomparability while enabling data transportability between the system and forms of cloud.
The meaning of proprietary dimension means that the organization is offering the service in a secure and protected manner under their ownership.
The open dimension using such type of technology in which more suppliers are allowed. In addition to that, the user is not constrained in being able to share the data and cooperate with selected partners using open technology.
De-parameterized/Parameterized: – To reach a de-parameterized/parameterized form, the user requires Jericho forum and collaboration oriented architecture commandments. It defines whether you are working inside your traditional mindset or outside it.
The meaning Parameterized dimension is continuing to work within the traditional boundary, orphan signaled by network firewalls. With the support of VPN and the operation of the virtual server in your IP domain, the customer can expand the organization’s boundary into the external cloud computing domain.
De-parameterized is the system which is designed on the principles outlined in the Jericho forum’s commandments. In this, data is encapsulated with metadata and structure, which will again support to secure the data and control the inappropriate usage.
Insourced/Outsourced: – Insourced/outsourced is the fourth dimension of the cloud cube model. In the outsourced dimension, services are offered by the third party, and in the insourced dimension, the services are offered by the own staff.
In some organizations with traditional bandwidth software or hardware, providers will run smoothly when they become cloud service providers.
Organizations exploring to process cloud services should have the capability to set a legally binding collaboration agreement. In this, an organization must ensure that the data is removed from the service provider’s infrastructure.
Conclusion
Cloud monitoring is the major focus as companies are generating lots of data which is to store for further analysis. The companies are coming up with fast servers so that the service should be fast and quick access. With the help of Cloud Computing, the user can focus on different aspects of the company and help to provide growth to the company.
