- An Overview of AWS Machine Learning Tutorial
- Mapplet In Informatica | Purpose and Implementation of Mapplets | Expert’s Top Picks | Free Guide Tutorial
- Spring Cloud Tutorial
- Azure IoT Hub Integration Tutorial | For Beginners Learn in 1 Day FREE
- Cloud Native Microservices Tutorial | A Comprehensive Guide
- Azure Stream Analytics | Learn in 1 Day FREE Tutorial
- Azure Data Warehouse | Learn in 1 Day FREE Tutorial
- AWS Lambda Tutorial | A Guide to Creating Your First Function
- Azure Logic Apps Tutorial – A beginners Guide & its Complete Overview
- Azure Service Bus Tutorial | Complete Overview – Just An Hour for FREE
- Introduction to Azure Service Fabric Tutorial | Learn from Scratch
- Amazon CloudWatch Tutorial | Ultimate Guide to Learn [BEST & NEW]
- AWS Data Pipeline Documentation Tutorial | For Beginners Learn in 1 Day FREE
- What is Azure App Service? | A Complete Guide for Beginners
- AWS Key Management Service | All You Need to Know
- Apigee Tutorial | A Comprehensive Guide for Beginners
- Kubernetes Tutorial | Step by Step Guide to Basic
- AWS SQS – Simple Queue Service Tutorial | Quickstart – MUST READ
- AWS Glue Tutorial
- MuleSoft
- Cloud Computing Tutorial
- AWS CloudFormation tutorial
- AWS Amazon S3 Bucket Tutorial
- Kubernetes Cheat Sheet Tutorial
- AWS IAM Tutorial
- Cloud Concepts And Models Tutorial
- Cloud Network Security Tutorial
- Azure Active Directory Tutorial
- NetApp Tutorial
- OpenStack tutorial
- AWS Cheat Sheet Tutorial
- Informatica Transformations Tutorial
- AWS vs AZURE Who is The Right Cloud Platform?
- How to Host your Static Website with AWS Tutorial
- VMware Tutorial
- Edge Computing Tutorial
- Cognitive Cloud Computing Tutorial
- Serverless Computing Tutorial
- Sharepoint Tutorial
- AWS Tutorial
- Microsoft Azure Tutorial
- IOT Tutorial
- An Overview of AWS Machine Learning Tutorial
- Mapplet In Informatica | Purpose and Implementation of Mapplets | Expert’s Top Picks | Free Guide Tutorial
- Spring Cloud Tutorial
- Azure IoT Hub Integration Tutorial | For Beginners Learn in 1 Day FREE
- Cloud Native Microservices Tutorial | A Comprehensive Guide
- Azure Stream Analytics | Learn in 1 Day FREE Tutorial
- Azure Data Warehouse | Learn in 1 Day FREE Tutorial
- AWS Lambda Tutorial | A Guide to Creating Your First Function
- Azure Logic Apps Tutorial – A beginners Guide & its Complete Overview
- Azure Service Bus Tutorial | Complete Overview – Just An Hour for FREE
- Introduction to Azure Service Fabric Tutorial | Learn from Scratch
- Amazon CloudWatch Tutorial | Ultimate Guide to Learn [BEST & NEW]
- AWS Data Pipeline Documentation Tutorial | For Beginners Learn in 1 Day FREE
- What is Azure App Service? | A Complete Guide for Beginners
- AWS Key Management Service | All You Need to Know
- Apigee Tutorial | A Comprehensive Guide for Beginners
- Kubernetes Tutorial | Step by Step Guide to Basic
- AWS SQS – Simple Queue Service Tutorial | Quickstart – MUST READ
- AWS Glue Tutorial
- MuleSoft
- Cloud Computing Tutorial
- AWS CloudFormation tutorial
- AWS Amazon S3 Bucket Tutorial
- Kubernetes Cheat Sheet Tutorial
- AWS IAM Tutorial
- Cloud Concepts And Models Tutorial
- Cloud Network Security Tutorial
- Azure Active Directory Tutorial
- NetApp Tutorial
- OpenStack tutorial
- AWS Cheat Sheet Tutorial
- Informatica Transformations Tutorial
- AWS vs AZURE Who is The Right Cloud Platform?
- How to Host your Static Website with AWS Tutorial
- VMware Tutorial
- Edge Computing Tutorial
- Cognitive Cloud Computing Tutorial
- Serverless Computing Tutorial
- Sharepoint Tutorial
- AWS Tutorial
- Microsoft Azure Tutorial
- IOT Tutorial

AWS IAM Tutorial
Last updated on 29th Sep 2020, Blog, Cloud Computing, Tutorials
Amazon Web Services (AWS) provides a cloud platform to a small-scale industry such as Quora as well as to large-scale industry such as D-link. Myriads of people are now using Amazon Web Services cloud
Best AWS Features
Amazon Web Services has various features which make it reliable among different firms. Some of the features of AWS are:-
a. Mobile Friendly Access
Mobile friendly access includes two ways:-
i. AWS Mobile Hub
This Amazon Web Services feature is for both Android and IOS. AWS Mobile Hub supports and guides you towards the suitable and compatible feature for your app. It includes a console that helps you to access AWS services which include development, testing, and monitoring of the mobile application. It includes lucid ways to select and configure mobile app features like content delivery and push notifications.
ii. AWS Mobile SDK
By this AWS feature, your app can directly access Amazon Web Services such as dynamo DB, S3, and Lambda. The Mobile SDK supports IOS, Android, Web, React Native, Unity and many more.

b. Serverless Cloud Functions
Amazon API and Amazon Gateway help users by running their code and scaling it. The only thing a user has to do is to upload the code with the help of a mobile phone. Users should not take care of the servers as the whole process is then managed by AWS. Apps which are made should deliver a great experience to the users. We want many tasks to be performed at once and for that, we need back-end code that runs and responds to the code. Managing the infrastructure to host back-end codes requires size, provision and lots of servers. AWS Server less cloud function helps the user in such a way that they should focus only on building the application. Server management is done by AWS along with it, it performs scaling, patching and administration of the infrastructure.
Subscribe For Free Demo
Error: Contact form not found.
c. Databases
Amazon provides a database as per your requirement and the database provided by them is completely managed by them. Some of the databases and their uses are:
- Relational Database – Transactional Purposes.
- Non-Relational Database –Internet Scale Applications.
- Data Warehouse – Analytics.
- In-memory data Store – Caching & Real-time workloads.
- Graph Database – Application with highly connected data.
d. Storage
It is one of the AWS features, provided by Amazon is economical, flexible and easy to use. The storage provided by AWS can be used independently as well as in combination to meet your requirement. Following are the types of storage provided by AWS.
- Amazon glacier – It is used for long-term storage.
- Amazon Simple Storage Service – It provides scalable object storage for archival, analytics and data backup.
- The Amazon EBS – It provides block level storage volumes for persistent data storage for use with EC-2 instances.

e. Security and Compliance
As most of the companies rely on AWS so Amazon provides maximum security to the data provided by them. AWS features, allows the customer to scale and innovate. Customers here pay only for the service they use. Moreover, there are no upfront expenses.
The security groups of AWS associate with EC2 instances. They provide security at the protocol and port access level. In AWS there are security rules that filter traffic coming into and out of an EC2 instance. Rules comprise four fields which are:-
- Type
- Protocol
- Port Range
- Source

f. AWS Marketplace
AWS Marketplace is an online store where a customer can immediately search for the suitable software or can buy it for their business. They can use Marketplace’s one-click deployment and launch the required software by paying only for what they will use.
It was launched in 2012 to accelerate the growth of AWS from Third party providers. AWS provides commercial as well as free software and services to support the customers business.
products to build applications as the products built with AWS are reliable, flexible and scalable.
Before you create users, you should understand how IAM works. IAM provides the infrastructure necessary to control authentication and authorization for your account. The IAM infrastructure includes the following elements:
Terms
Learn more about IAM terms.
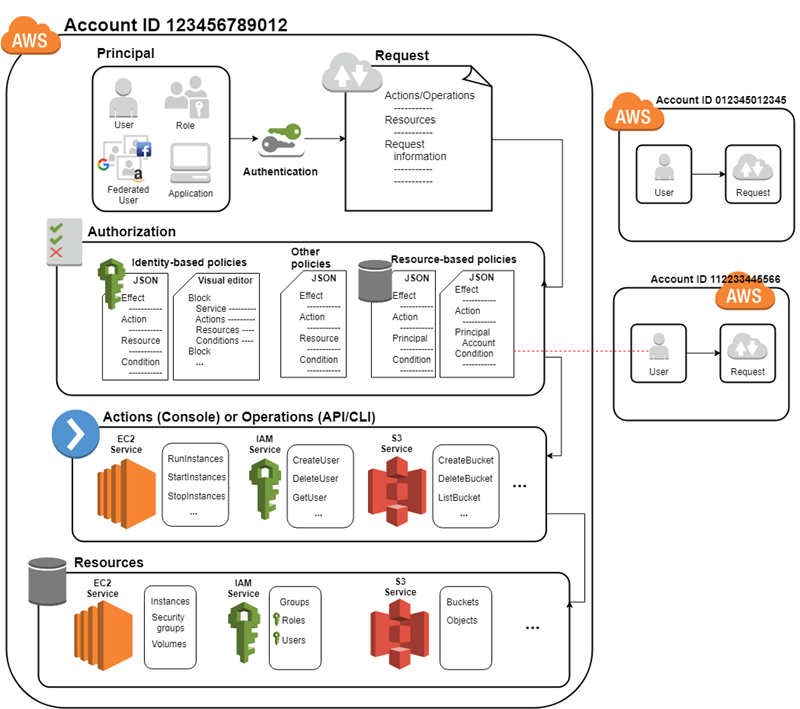
Resources
The user, group, role, policy, and identity provider objects that are stored in IAM. As with other AWS services, you can add, edit, and remove resources from IAM.
Identities
The IAM resource objects that are used to identify and group. You can attach a policy to an IAM identity. These include users, groups, and roles.
Entities
The IAM resource objects that AWS uses for authentication. These include IAM users, federated users, and assumed IAM roles.
Principals
A person or application that uses the AWS account root user, an IAM user, or an IAM role to sign in and make requests to AWS.
Principal
A principal is a person or application that can make a request for an action or operation on an AWS resource. The principal is authenticated as the AWS account root user or an IAM entity to make requests to AWS. As a best practice, do not use your root user credentials for your daily work. Instead, create IAM entities (users and roles). You can also support federated users or programmatic access to allow an application to access your AWS account.
Request
When a principal tries to use the AWS Management Console, the AWS API, or the AWS CLI, that principal sends a request to AWS. The request includes the following information:
- Actions or operations – The actions or operations that the principal wants to perform. This can be an action in the AWS Management Console, or an operation in the AWS CLI or AWS API.
- Resources – The AWS resource object upon which the actions or operations are performed.
- Principal – The person or application that used an entity (user or role) to send the request. Information about the principal includes the policies that are associated with the entity that the principal used to sign in.
- Environment data – Information about the IP address, user agent, SSL enabled status, or the time of day.
- Resource data – Data related to the resource that is being requested. This can include information such as a DynamoDB table name or a tag on an Amazon EC2 instance.
AWS gathers the request information into a request context, which is used to evaluate and authorize the request.
Authentication
A principal must be authenticated (signed in to AWS) using their credentials to send a request to AWS. Some services, such as Amazon S3 and AWS STS, allow a few requests from anonymous users. However, they are the exception to the rule.
To authenticate from the console as a root user, you must sign in with your email address and password. As an IAM user, provide your account ID or alias, and then your user name and password. To authenticate from the API or AWS CLI, you must provide your access key and secret key. You might also be required to provide additional security information. For example, AWS recommends that you use multi-factor authentication (MFA) to increase the security of your account. To learn more about the IAM entities that AWS can authenticate
Authorization
You must also be authorized (allowed) to complete your request. During authorization, AWS uses values from the request context to check for policies that apply to the request. It then uses the policies to determine whether to allow or deny the request. Most policies are stored in AWS as JSON documents and specify the permissions for principal entities. There are several types of policies that can affect whether a request is authorized. To provide your users with permissions to access the AWS resources in their own account, you need only identity-based policies. Resource-based policies are popular for granting cross-account access. The other policy types are advanced features and should be used carefully.
AWS checks each policy that applies to the context of your request. If a single permissions policy includes a denied action, AWS denies the entire request and stops evaluating. This is called an explicit deny. Because requests are denied by default, AWS authorizes your request only if every part of your request is allowed by the applicable permissions policies. The evaluation logic for a request within a single account follows these general rules:
- By default, all requests are denied. (In general, requests made using the AWS account root user credentials for resources in the account are always allowed.)
- An explicit allow in any permissions policy (identity-based or resource-based) overrides this default.
- The existence of an Organization’s SCP, IAM permissions boundary, or a session policy overrides the allow. If one or more of these policy types exists, they must all allow the request. Otherwise, it is implicitly denied.
- An explicit deny in any policy overrides any allows.
To learn more about how all types of policies are evaluated, see Policy evaluation logic. If you need to make a request in a different account, a policy in the other account must allow you to access the resource and the IAM entity that you use to make the request must have an identity-based policy that allows the request.
Actions or operations
After your request has been authenticated and authorized, AWS approves the actions or operations in your request. Operations are defined by a service, and include things that you can do to a resource, such as viewing, creating, editing, and deleting that resource. For example, IAM supports approximately 40 actions for a user resource, including the following actions
- CreateUser
- DeleteUser
- GetUser
- UpdateUser
To allow a principal to perform an operation, you must include the necessary actions in a policy that applies to the principal or the affected resource. To see a list of actions, resource types, and condition keys supported by each service, see Actions, Resources, and Condition Keys for AWS Services.
Resources
After AWS approves the operations in your request, they can be performed on the related resources within your account. A resource is an object that exists within a service. Examples include an Amazon EC2 instance, an IAM user, and an Amazon S3 bucket. The service defines a set of actions that can be performed on each resource. If you create a request to perform an unrelated action on a resource, that request is denied. For example, if you request to delete an IAM role but provide an IAM group resource, the request fails. To see AWS service tables that identify which resources are affected by an action, see Actions, Resources, and Condition Keys for AWS Services.
Policies
The access management portion of AWS Identity and Access Management (IAM) helps you define what a principal entity is allowed to do in an account. A principal entity is a person or application that is authenticated using an IAM entity (user or role). Access management is often referred to as authorization. You manage access in AWS by creating policies and attaching them to IAM identities (users, groups of users, or roles) or AWS resources. A policy is an object in AWS that, when associated with an identity or resource, defines their permissions. AWS evaluates these policies when a principal uses an IAM entity (user or role) to make a request. Permissions in the policies determine whether the request is allowed or denied. Most policies are stored in AWS as JSON documents. For more information about policy types and uses, see Policies and permissions in IAM.
Policies and accounts
If you manage a single account in AWS, then you define the permissions within that account using policies. If you manage permissions across multiple accounts, it is more difficult to manage permissions for your users. You can use IAM roles, resource-based policies, or access control lists (ACLs) for cross-account permissions. However, if you own multiple accounts, we instead recommend using the AWS Organizations service to help you manage those permissions.
Policies and users
IAM users are identities in the service. When you create an IAM user, they can’t access anything in your account until you give them permission. You give permissions to a user by creating an identity-based policy, which is a policy that is attached to the user or a group to which the user belongs. The following example shows a JSON policy that allows the user to perform all Amazon DynamoDB actions (dynamodb:*) on the Books table in the 123456789012 account within the us-east-2 Region.
- “Version”: “2012-10-17”,
- “Statement”:
- “Effect”: “Allow”,
- “Action”: “dynamodb:”
After you attach this policy to your IAM user, the user only has those DynamoDB permissions. Most users have multiple policies that together represent the permissions for that user.
Actions or resources that are not explicitly allowed are denied by default. For example, if the preceding policy is the only policy that is attached to a user, then that user is allowed to only perform DynamoDB actions on the Books table. Actions on all other tables are prohibited. Similarly, the user is not allowed to perform any actions in Amazon EC2, Amazon S3, or in any other AWS service. The reason is that permissions to work with those services are not included in the policy.
The IAM console includes policy summary tables that describe the access level, resources, and conditions that are allowed or denied for each service in a policy. Policies are summarized in three tables: the policy summary, the service summary, and the action summary. The policy summary table includes a list of services. Choose a service there to see the service summary. This summary table includes a list of the actions and associated permissions for the chosen service. You can choose an action from that table to view the action summary. This table includes a list of resources and conditions for the chosen action.
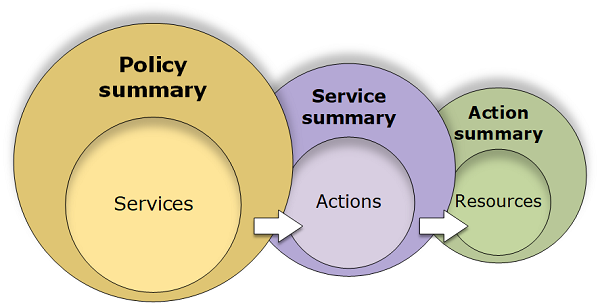
You can view policy summaries on the Users page for all policies (managed and inline) that are attached to that user. View summaries on the Policies page for all managed policies.
For example, the previous policy is summarized in the AWS Management Console as follows:
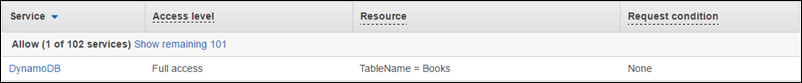
You can also view the JSON document for the policy. For information about viewing the summary or JSON document
Policies and groups
You can organize IAM users into IAM groups and attach a policy to a group. In that case, individual users still have their own credentials, but all the users in a group have the permissions that are attached to the group. Use groups for easier permissions ,
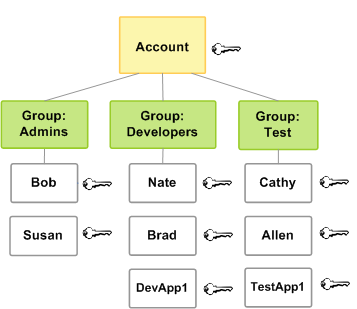
Users or groups can have multiple policies attached to them that grant different permissions. In that case, the users’ permissions are calculated based on the combination of policies. But the basic principle still applies: If the user has not been granted an explicit permission for an action and a resource, the user does not have those permissions.
Federated users and roles
Federated users don’t have permanent identities in your AWS account the way that IAM users do. To assign permissions to federated users, you can create an entity referred to as a role and define permissions for the role. When a federated user signs in to AWS, the user is associated with the role and is granted the permissions that are defined in the role. For more information, see Creating a role for a third-party Identity Provider (federation).
Identity-based and resource-based policies
Identity-based policies are permissions policies that you attach to an IAM identity, such as an IAM user, group, or role. Resource-based policies are permissions policies that you attach to a resource such as an Amazon S3 bucket or an IAM role trust policy.
Identity-based policies control what actions the identity can perform, on which resources, and under what conditions. Identity-based policies can be further categorized:
1.Managed policies – Standalone identity-based policies that you can attach to multiple users, groups, and roles in your AWS account. You can use two types of managed policies:
- AWS managed policies – Managed policies that are created and managed by AWS. If you are new to using policies, we recommend that you start by using AWS managed policies.
- Customer managed policies – Managed policies that you create and manage in your AWS account. Customer managed policies provide more precise control over your policies than AWS managed policies. You can create and edit an IAM policy in the visual editor or by creating the JSON policy document directly. For more information, see Creating IAM policies and Editing IAM policies.
2.Inline policies – Policies that you create and manage and that are embedded directly into a single user, group, or role. In most cases, we don’t recommend using inline policies.
Resource-based policies control what actions a specified principal can perform on that resource and under what conditions. Resource-based policies are inline policies, and there are no managed resource-based policies. To enable cross-account access, you can specify an entire account or IAM entities in another account as the principal in a resource-based policy.
The IAM service supports only one type of resource-based policy called a role trust policy, which is attached to an IAM role. Because an IAM role is both an identity and a resource that supports resource-based policies, you must attach both a trust policy and an identity-based policy to an IAM role. Trust policies define which principal entities (accounts, users, roles, and federated users) can assume the role. To learn how IAM roles are different from other resource-based policies.
What is AWS IAM????
Amazon Web Services (AWS) Identity and Access Management (IAM) is a service that assists us to control access securely to AWS resources.
We can use IAM to decide who is to be authenticated and authorized to use the resources.
AWS IAM – Objective
Here, in this AWS IAM Tutorial, we will discuss what is Amazon IAM (Identity and Access Management). Moreover, we will study the functions and uses of AWS IAM.
What is Amazon IAM?
AWS (Amazon Identity and access management) can help a user to manage to compute, store, manage, and application services in the AWS cloud. It uses access control techniques through which a user is familiar with which includes users, groups, and permission. With the help of this, the user can specify the user and allow it to use specific services. This depends on the kind of action they perform with the help of the available resources. Amazon Cloudtrail helps to analyze and monitor the activities under process in Amazon IAM. Microsoft directory can also be added using the federal based technology. This benefits IT, workers and managers, to monitor the services in a better way.
With the help of a single AWS IAM, the user can manage the customer and their needs. It provides Amazon AWS building blocks which help the user to build the applications for the security purpose. AWS Identity and access management help the user to focus on the features and functionality which includes the security on the other side of the things. AWS IAM can also rotate access keys on the virtual machine instances. This makes sure that only the trusted user can access the AWS at any given time. Amazon IAM is economical and there are no additional charges for it. One can start using IAM very easily.
What are Amazon Identity and access management?
Functions of AWS IAM
Following are important Amazon IAM Functions, let’s discuss them one by one:
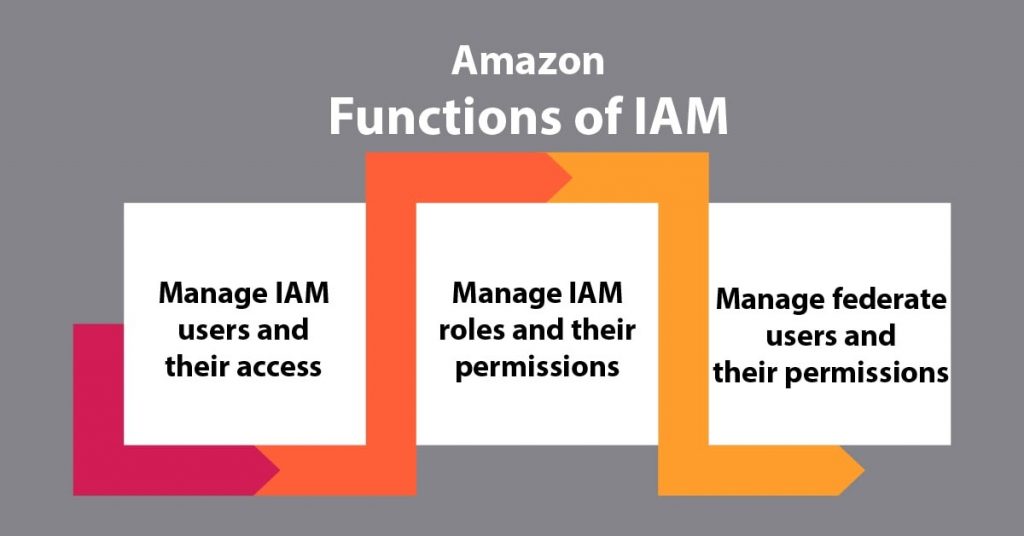
Amazon Identity and Access Management – Functions
a. To Manage AWS IAM users and their access
The user will be able to produce users in Amazon IAM, assign them individual security. The user can also demand the temporary security credentials to produce users access to AWS services and resources. Here, users will be able to manage permissions so as to manage those operations a user can perform.
b. To Manage Amazon IAM roles and their permissions
The user will be able to produce roles in AWS Identity and access management and manage permissions to manage that operations are performed by the entity, or AWS service, that assumes the role. The user will be able to conjointly outline the entity is allowed to assume the role. Additionally, the user will be able to use service-linked roles to delegate permissions to AWS services that make and manage AWS resources on The user’s behalf.
c. To Manage to federate users and their permissions
The user will be able to alter identity federation to permit existing identities (users, groups, and roles) in The user are an enterprise to access the AWS Management Console, decide AWS APIs, and access resources, while not the necessity to make an IAM user for every identity. Use any identity management resolution that supports SAML 2.0, or use one in all our federation samples (AWS Console SSO or API federation).
4. Amazon IAM Uses
Here, we will clear the Applications of AWS IAM in detail:
Amazon Identity and Access Management – Uses
a. Directory integration image
AWS IAM is accustomed to grant the user staff and applications united access to the AWS Management Console and AWS service APIs, using the user existing identity systems like Microsoft Active Directory. The user will use any identity management answer that supports SAML 2.0, or be at liberty to use one in every of our federation samples (AWS Console SSO or API federation).
b. Fine-grained access management to AWS resources
Amazon IAM permits the users to regulate access to AWS service Apis and to specific resources. IAM also permits The user to feature specific conditions like time of day to regulate however a user will use AWS, their originating science address, whether or not they are using SSL, or whether or not they have genuine with a multi-factor authentication device.
c. MFA Image
Multi-factor authentication is extremely valuable as it protects The user’s AWS surroundings by using AWS MFA, a security feature out there at no further value that augments username and countersigns credentials. Amazon MFA needs users to prove physical possession of a hardware MFA token or MFA-enabled mobile device by providing a legitimate MFA code.
d. Managed access to the mobile image
Manage access control for mobile applications with net Identity suppliers. The user can modify the mobile and browser-based applications to firmly access AWS resources by requesting temporary security credentials that grant access solely to specific AWS resources for a configurable amount of the user’s time.
5. Conclusion
Hence, we saw AWS helps the user to make their business better by providing the techniques. With the help of Amazon IAM, the user can create and manage AWS groups and users. It is also preferred as it provides the security benefit and the user can allow and deny them access to AWS resources. Amazon Identity and Access Management does not include any upfront cost and is economical too. Furthermore, if we miss something or you want to share some information with us, feel free to ask in the comment section.
