DBMS Interview Questions and Answers [ TO GET HIRED ]
Last updated on 26th Sep 2022, Blog, Interview Question
1. What’s DBMS?
Ans:
DBMS may be an assortment of programs that facilitate users to form and maintain information. In alternative words, software package provides United States associate degree interface or tool for performing arts completely different operations like the creation of a info, inserting information into it, deleting information from it, change the info, etc. software package may be a code within which information is hold on in an exceedingly safer manner as compared to the file-based system.
2. What’s a database?
Ans:
An info may be a logical, consistent and arranged assortment of information that may simply be accessed, managed and updated. Databases, conjointly referred to as electronic databases square measure structured to produce the power of creation, insertion, change of the info expeditiously and square measure hold on within the variety of a file or set of files, on the disk, tapes and alternative kind of secondary devices. info largely consists of the objects (tables. , and tables embrace the records and fields. Fields square measure the essential units of information storage, that contain the knowledge of a couple of specific sides or attributes of the entity delineated by the info. a software package is employed for extraction of information from the info within the variety of the queries.
3. What’s an info system?
Ans:
The collection of info and software package code alone is thought of as an info system. Through the info system, we are able to perform several activities such as- the info will be held on within the info with ease, and there aren’t any problems with information redundancy and information inconsistency.
The data are going to be extracted from the info victimization software package code whenever needed. So, the mix of info and software package code allows one to store, retrieve and access information with tactful accuracy and security.
4. What square measures the benefits of DBMS?
Ans:
- Redundancy management.
- Restriction for unauthorized access.
- Provides multiple user interfaces.
- Provides backup and recovery.
- Enforces integrity constraints.
- Ensure information consistency.
- Easy accessibility.
- Easy information extraction and processing thanks to the utilization of queries.
5. What’s a stop in DBMS?
Ans:
The stop may be a kind of mechanism wherever all the previous logs square measure faraway from the system and for good hold on within the storage disk.
There square measure 2 ways in which which may facilitate the software package in ill and maintaining the ACID properties, and that they are- maintaining the log of every group action and maintaining shadow pages. So, once it involves log primarily based recovery systems, checkpoints inherit existence. Checkpoints square measure those purposes to that the info engine will recover when a crash as a such lowest point from that the group action log record will be wont to recover all the committed information up to the purpose of the crash.
6. Once will a stop occur in DBMS?
Ans:
A stop is sort of an exposure of the software package state. victimization checkpoints, the software package will scale back the number of labor to be done throughout a restart within the event of ensuant crashes. Checkpoints square measure used for the recovery of the info when the system crashes. Checkpoints square measure employed in the log-based recovery system. Once thanks to a system crash we’d like to restart the system, then at that time we tend to use checkpoints. So that, we tend to don’t ought to perform the transactions from the terribly beginning.
7. What does one mean by clear DBMS?
Ans:
The clear software package may be a kind of software package that keeps its natural object hidden from users. natural object or physical storage structure implies to the memory manager of the software package, and it describes however the info is held on disk.
8. What square measures the single operations in relative Algebra?
Ans:
PROJECTION and choice square measure the single operations in relative pure mathematics. single operations square measure those operations that use single operands. single operations square measure choice, PROJECTION, and RENAME.
As in choice relative operators square measure used for instance – =,=, etc.
9. What’s RDBMS?
Ans:
RDBMS stands for electronic database Management Systems.RDBMS is that the variety of software packages that uses the structure to spot and access information regarding the opposite piece of information within the info. RDBMS is the system that allows you to perform completely different operations such as- update, insert, delete, manipulate and administer an electronic database with lowest difficulties. Most of the time RDBMS uses SQL language as a result of it’s simply comprehendible and is employed typically.
10. What number kinds of info languages square measure there?
Ans:
- There square measure four kinds of info languages :of these commands square measure is used to change the info that?s why they’re referred to as information Definition Language.
- Data Manipulation Language (DML. e.g., SELECT, UPDATE, INSERT, DELETE, etc. These commands square measure used for the manipulation of already updated information that’s why they’re a part of information Manipulation Language.
- DATA management Language (DCL. e.g., GRANT and REVOKE. These commands square measure used for giving and removing the user access to the info. So, they’re a part of the info management Language.
- Transaction Management Language (TCL. e.g., COMMIT, ROLLBACK, and SAVEPOINT.
11. What does one perceive regarding the info Model?
Ans:
The Data model is such as a set of abstract tools for describing information, information relationships, information linguistics and constraints. These models square measure wont to describe the link between the entities and their attributes.
There is the amount of information models :
- Hierarchical information model.
- Network model.
- Relational model.
- Entity-Relationship model and so on.
12. Outline a Relation Schema and a Relation.
Ans:
A Relation Schema is specific as a group of attributes. It’s additionally called table schema.Relation schema is thought of because the blueprint with the assistance of that we will justify however the info is organized into tables. This blueprint contains no information.
A relation is specific as a group of tuples. A relation is that the set of connected attributes with characteristic key attributes
See this instance :
And,every tuple is an associated ordered list of n-values t=(v1,v2, …., vn).
13. What’s a degree of Relation?
Ans:
The degree of relation may be a variety of attributes of its relation schema. A degree of relation is additionally called Cardinality; it’s outlined because of the variety of occurrences of 1 entity that is connected to the amount of occurrences of another entity. There is a unit 3 degrees of relation; they’re one-to-one(1:1. , one-to-many(1:M. , and many-to-one(M:M) .
14. What’s a Relationship?
Ans:
The Relationship is outlined as an associate association among 2 or a lot of entities. There area unit 3 style of relationships in package
One-To-One : Here one record of any object is often associated with one record of another object.
One-To-Many (many-to-one) : Here one record of any object is often associated with several records of alternative objects and the other way around.
Many-to-many : Here quite one record of an associate object is often associated with a variety of records of another object.
15. What area unit the disadvantages of file process systems?
Ans:
- Inconsistent
- Not secure
- Data redundancy
- Difficult in accessing information
- Data isolation
- Data integrity
- Concurrent access isn’t potential
- Limited information sharing
- Atomicity downside
16. What’s information abstraction in DBMS?
Ans:
Data abstraction in a package may be a method of concealing moot details from users. As a result of information systems area units manufactured from advanced information structures, it makes the user move with the information.
For example: we all know that the majority of the users like those systems that have a straightforward GUI which means no advanced process. So, to stay the user tuned and to create access to the info straightforwardly, it’s necessary to try to do information abstraction. In addition to that, information abstraction divides the system in several layers to create the work specific and well outlined.
17. What area unit the 3 levels of knowledge abstraction?
Ans:
Following area unit 3 levels of knowledge abstraction :
Physical level: It’s a very cheap level of abstraction. It describes however information is held on.
Logical level: It’s succeeding at a higher level of abstraction. It describes what information is held within the information and what the link among those information is.
View level: It’s the very best level of knowledge abstraction. It describes solely a part of the complete information.
For example- User interacts with the system exploiting the GUI and fills the desired details, however the user doesn’t have any plan however the info is being employed. So, the abstraction level is entirely high visible LEVEL.
Then, succeeding level is for PROGRAMMERS as during this level the fields and records area unit visible and also the programmers have the data of this layer. So, the extent of abstraction here may be a very little low visible LEVEL.
And lastly, the physical level within which storage blocks are delineated.
18. What’s DDL (Data Definition Language. ?
Ans:
Data Definition Language (DDL. may be a custom for commands that define the various structures during an information. Most ordinarily DDL statements are unit-products, ALTER, and DROP. These commands are a unit used to change information into information.
19. What’s DML (Data Manipulation Language. ?
Ans:
Data Manipulation Language (DML) may be a language that allows the user to access or manipulate information as organized by the suitable information model. For example- choose, UPDATE, INSERT, DELETE.
There is 2 style of DML :
Procedural DML or Low level DML : It needs a user to specify what information area unit required and the way to induce that information.
Non-Procedural DML or High level DML : It needs a user to specify what information area unit required while not specifying a way to get that information.
20. Justify the practicality of DML Compiler.
Ans:
The DML Compiler interprets DML statements during a search language that the question analysis engine will perceive. A DML Compiler is needed as a result of the DML is that the family of syntax parts is incredibly like the opposite programming language which needs compilation. So, it’s essential to compile the code within the language that the question analysis engine will perceive then work on those queries with correct output.
21. What’s relative Algebra?
Ans:
Relational pure mathematics may be a Procedural search language that contains a group of operations that take one or 2 relations as input and turn out a brand new relationship. relative pure mathematics is the basic set of operations for the relative model. The decisive purpose of relative pure mathematics is that it’s like pure mathematics that operates on the amount.
There area unit few elementary operations of relative pure mathematics :
- Select
- Project
- Set distinction
- Union
- Rename,etc.
22. What’s Calculus?
Ans:
Relational Calculus may be a Non-procedural search language that uses mathematical mathematical logic rather than pure mathematics. Relative calculus doesn’t work on arithmetic fundamentals like pure mathematics, differential, integration, etc. That’s why it’s additionally called mathematical logic.
There is 2 style of relative calculus :
- Tuple relational calculus.
- Domain relative calculus.
23. What does one perceive by question optimization?
Ans:
The term question optimisation specifies AN economical execution arrange for evaluating a question that has the smallest amount calculable price. The construct of question optimisation came into the frame once there were a variety of ways, and algorithms existed for identical tasks then the question arose that one is additional economical and therefore the method of determinant the economical approach is understood as question optimisation.
There are several advantages of question optimisation :
- It reduces the time and house complexity.
- More queries are often performed as because of optimisation each question relatively takes less time.
- User satisfaction because it can offer output quick
24. What does one mean by sturdiness in DBMS?
Ans:
Once the software package informs the user that a group action has completed with success, its impact ought to persist albeit the system crashes before all its changes are mirrored on disk. This property is termed sturdiness. Sturdiness ensures that after the group action is committed into the info, it’ll be kept within the non-volatile memory and at the moment system failure cannot have an effect on that knowledge any longer.
25. What’s normalization?
Ans:
Analyzing the given relation schemas in step with their purposeful dependencies. it’s wont to minimize redundancy and conjointly wont to minimize insertion, deletion and update distractions. standardization is taken into account as a necessary method because it is employed to avoid knowledge redundancy, insertion anomaly, updation anomaly, deletion anomaly.
There most ordinarily used traditional forms are :
- First traditional Form(1NF).
- Second traditional Form(2NF).
- Third traditional Form(3NF).
- Boyce & Codd traditional Form(BCNF).
26. What’s Denormalization?
Ans:
Denormalization is the method of boosting up info performance and adding of redundant knowledge that helps to induce obviate advanced knowledge. Denormalization may be a part of info optimization technique. This method is employed to avoid the employment of advanced and expensive joins. Denormalization doesn’t see the thought of not normalizing instead denormalization takes place when standardization.
27. What’s purposeful Dependency?
Ans:
Functional Dependency is the start line of standardization. It exists once a relation between 2 attributes permits you to work out the corresponding attribute’s price unambiguously. The purposeful dependency is additionally referred to as info dependency and defines because the relationship that happens once one attribute in an exceedingly relation unambiguously determines another attribute. it’s written as A->B which suggests B is functionally enthusiastic about A.
28. What’s the E-R model?
Ans:
This model relies on the important world.Here the first objects are the entity, attribute of that entity, relationship set, AN attribute of that relationship set are often mapped within the kind of E-R diagram.
In the E-R diagram, entities are pictured by rectangles, relationships are pictured by diamonds, attributes are the characteristics of entities and pictured by ellipses, and knowledge flow is pictured through a line.
29. What’s AN entity?
Ans:
The Entity may be a set of attributes in an exceedingly info. AN entity is often a real-world object that physically exists during this world. All the entities have their attributes that within the globe are thought of because of the characteristics of the item.
For example : within the worker info of an organization, the worker, department, and therefore the designation are often thought of because of the entities.
30. What’s AN Entity type?
Ans:
An entity sort is such that as a group of entities, having identical attributes. Entity sort usually corresponds to at least one or many connected tables within the info. A characteristic or attribute that defines or unambiguously identifies the entity is termed entity sort.
31. What’s AN Entity set?
Ans:
The entity set specifies the gathering of all entities of a specific entity sort within the info. AN entity set is understood because of the set of all the entities that share identical properties.
For example, a collection of individuals, a collection of scholars, a collection of firms, etc..
32. What’s AN Extension of entity type?
Ans:
An extension of AN entity sort is such that as a group of entities of a specific entity sort that are sorted into AN entity set.
33. What’s a Weak Entity set?
Ans:
An entity set that doesn’t have decent attributes to create a primary secret is said to be a weak entity set. The member of a weak entity set is understood as a subordinate entity. Weak entity set doesn’t have a primary key, however we want a method to differentiate among all those entries within the entity set that rely upon one explicit robust entity set.
34. What’s AN attribute?
Ans:
An attribute refers to an info element. it’s wont to describe the property of AN entity. AN attributes are often outlined because of the characteristics of the entity. Entities are often unambiguously known victimizing the attributes. Attributes represent the instances within the row of the info.
For example : If a student is AN entity within the table then age is the attribute of that student.
35. What are the integrity rules in DBMS?
Ans:
Data integrity is one important facet whereas maintaining the info. So, knowledge integrity is enforced within the info system by imposing a series of rules. That set of integrity is understood because the integrity rules.
36. What does one mean by extension and intension?
Ans:
Extension : The Extension is that the range of tuples is given during a table at any instance. It changes because the tuples area unit is created, updated and destroyed. the particular information within the information changes quite oftentimes. So, the info within the information at a selected moment in time is thought as extension or information state or photo. It’s time dependent.
Intension : Connotation is additionally referred to as information Schema and outlined because the description of the information, that is specified throughout information style and is anticipated to stay unchanged. The Intention could be a constant worth that offers the name, structure of tables and also the constraints ordered thereon.
37. What’s System R? what percentage of its 2 major subsystems?
Ans:
System R was designed and developed from 1974 to 1979 at IBM San Jose analysis Centre. System R is the 1st implementation of SQL, that is, the commonplace relative information search language, and it absolutely was additionally the primary to demonstrate that RDBMS may offer higher group action process performance. It’s an example that is created to point out that it’s potential to create a relative System that may be employed in a real-life atmosphere to resolve real-life issues.
Following area unit 2 major subsystems of System R :
- Research Storage.
- System relative system.
38. What’s information Independence?
Ans:
Data independence specifies that “the application is free of the storage structure and access strategy of information.” It causes you to be able to modify the schema definition at one level while not fixing the schema definition within the next higher level.
There area unit 2 sorts of information Independence :
Physical information Independence: Physical information is that the information holds on within the information. it’s within the bit-format. Modification at the physical level shouldn’t have an effect on the logical level.
For example : If we would like to govern the info within any table that ought to not modify the format of the table.
Logical information Independence: Logical information within the information regarding the information. It essentially defines the structure. like tables hold on within the information. Modification at the logical level shouldn’t have an effect on the read level.
39. What area unit the challenges of managing massive data?
Ans:
Those who affect analytics could also be excited by the promise of insight and business intelligence that comes from massive information, however people who manage information based face the challenges that return alongside managing overall growth ANd data varieties from an increasing range of information platforms.
40. What’s Join?
Ans:
The be a part of operation is one amongst the foremost helpful activities in relative pure mathematics. it’s most ordinarily used thanks to mix info from 2 or a lot of relations. A be a part of is usually performed on the idea of an equivalent or connected column. Most advanced queries of SQL involve being a part of a command.
There area unit following sorts of be a part of :
Inner be a part ofs: Inner join is of three classes. They are :
- Theta join
- Natural be a part of
- Equi join
Outer joins : Outer joins have 3 varieties. They are :
- Left outer be a part of
- Right outer be a part of
- Full outer be a part of
41. What’s 1NF?
Ans:
1NF is the 1st traditional kind. it’s the only sort of standardization that you just will implement during an information. the first objectives of 1NF area unit to :
- Every column should have an atomic (single worth).
- Create separate tables every cluster of connected information and establish each row with a novel column.
42. What’s 2NF?
Ans:
2NF is the Second traditional kind. A table is alleged to be 2NF if it follows the subsequent conditions :
The table is in 1NF, i.e., first it’s necessary that the table ought to follow the principles of 1NF. Every non-prime attribute is absolutely functionally smitten by the first key, i.e., each non-key attribute ought to be smitten by the first key in such a way that if any key component is deleted, then even the non_key component can still be saved within the information.
43. What’s 3NF?
Ans:
3NF stands for the Third traditional kind. A information is termed in 3NF if it satisfies the subsequent conditions :
- It is in its second traditional kind.
- There is no transitive useful dependency.
- For example : X->Z
- Where :
- X->Y
- Y doesn’t -> X
- Y->Z so, X->Z
44. What’s BCNF?
Ans:
BCMF stands for Boyce-Codd traditional kind. it’s a sophisticated version of 3NF, thus it’s additionally spoken as three.5NF. BCNF is stricter than 3NF.It is in 3NF.For every useful dependency X->Y, X ought to be the super key of the table. It just means X can not be a non-prime attribute if Y could be a prime attribute.
45. Justify ACID properties
Ans:
ACID properties unit some basic rules, that got to be glad by each group action to preserve the integrity. These properties and rules area unit :
ATOMICITY : Atomicity is usually referred to as the ‘all or nothing rule.’ which means all area units are a united unit, and that they either run to completion or are not dead in the least.
CONSISTENCY : This property refers to the uniformity of the info. Consistency implies that the information is consistent before and once the group action.
ISOLATION : This property states that the quantity of the group action will be dead at the same time while not resulting in the inconsistency of the information state.
DURABILITY : This property ensures that after the group action is committed it’ll be held on within the non-volatile memory and system crash also can not have an effect on it any longer.
46. What’s the hold on procedure?
Ans:
A hold on procedure could be a cluster of SQL statements that are created and hold on within the info. The hold on procedure will increase the reusability as here the code or the procedure is held on into the system and used once more and once more that creates the work simple, takes less time in process and reduces the quality of the system. So, if you’ve got a code that you would like to use once more and once more then save that code and decide on that code whenever it’s needed.
47. What’s the distinction between a DELETE command and TRUNCATE command?
Ans:
| DELETE command | TRUNCATE command |
|---|---|
| DELETE command is employed to delete rows from a table supporting the condition that we offer during a wherever clause. | TRUNCATE command is employed to get rid of all rows (complete data) from a table. it’s kind of like the DELETE command with no wherever clause. |
| DELETE command delete solely those rows that are unit nominative with the wherever clause. | The TRUNCATE command can not be rolled back. |
| The DELETE command will be rolled back. | The TRUNCATE command doesn’t maintain a log. That’s why it’s quick. |
| The DELETE command maintains a log, that’s why it’s slow. | TRUNCATE uses table log whereas TRUNCATE performs. |
48. What’s 2-Tier architecture?
Ans:
The 2-Tier design is the same as basic client-server. within the two-tier design, applications on the consumer finish will directly communicate with the info at the server facet.
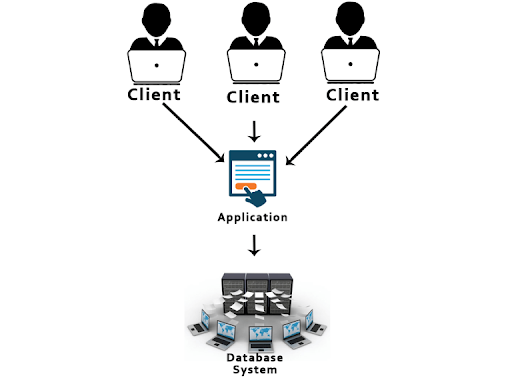
49. What’s the 3-Tier architecture?
Ans:
The 3-Tier design contains another layer between the consumer and server. Introduction of 3-tier design is for the benefit of the users because it provides the graphical user interface that makes the system secure and far additional accessible. During this design, the application on the client-end interacts with an associate degree application on the server that communicates with the info system.
50. However, does one communicate with an associate degree RDBMS?
Ans:
You have to use Structured source language (SQL) to speak with the RDBMS. victimization queries of SQL, we {will|We are able to} offer the input to the info so when processing the queries the info will offer the U.S. the desired output.
51. What’s the distinction between a shared lock and exclusive lock?
Ans:
Shared lock : Shared lock is needed for reading an information item. within the shared lock, several transactions might hold a lock on an equivalent knowledge item. Once over one deal is allowed to browse the info things then that’s called the shared lock.
Exclusive lock : Once any dealings is close to perform the write operation, then the lock on the info item is associate degree exclusive lock. Because, if we tend to enable over one dealings then that may result in the inconsistency within the info.
52. Describe the categories of keys?
Ans:
There area unit following styles of keys :
Primary key : The first key’s associate degree attribute during a table which will unambiguously determine every record during a table. It’s mandatory for each table.
Candidate key : The Candidate key’s associate degree attribute or set of associate degree attribute which might unambiguously determine a tuple. The first key will be selected from these attributes.
Super key : The Super key’s a collection of attributes which might unambiguously determine a tuple. Super key’s a superset of the candidate key.
Foreign key : The Foreign key’s a primary key from one table, that incorporates a relationship with another table. It acts as a cross-index between tables.
53. What area unit the variations between a package and RDBMS?
Ans:
| DBMS | RDBMS |
|---|---|
| Provides associate degree organized method of managing, retrieving, and storing from a set of logically connected information. | Provides an equivalent as that of package, however it provides relative integrity. |
54. What does one perceive regarding aggregation and atomicity?
Ans:
| Aggregation | Atomicity |
|---|---|
| This is a feature of the E-R model that permits a relationship set to participate in another relationship set. | This property states that an info modification should either follow all the foundations or nothing in the least. So, if one part of the dealings fails, then the complete dealings fail. |
55.What does one perceive by signification and extension?
Ans:
Intension: Signification or most typically called info schema defines the outline of the info. This is often nominative throughout the info style and largely remains unchanged.
Extension: Extension is the variety of tuples offered within the info at any instance of your time. This value keeps dynamical as and once the tuples area unit is created, updated and destroyed. So, the info gift within the info at a selected instance of your time is understood because the extension of the info or most typically called the shot of the info.
56. What’s concurrency control?
Ans:
This is a method of managing coincidental operations during an info session in order that info integrity isn’t compromised. the subsequent area unit the 2 approaches concerned in concurrency management :
Optimistic approach : Involves versioning
Pessimistic approach : Involves protection
57. What area unit the various styles of normalization?
Ans:
The following area unit the primary 3 traditional forms. except for these, you’ve got higher traditional forms like BCNF :
First traditional kind (1NF) : No continuance teams at intervals rows.
Second traditional kind (2NF) : Each non-key (supporting) column worth depends on the complete primary key.
Third traditional kind (3NF) : Dependent exclusively on the first key and no different non-key (supporting column value).
58. What does one perceive by correlated subqueries in DBMS?
Ans:
A correlated subquery is additionally a kind of subquery dependent on another question. So, once subqueries are unit dead for every of the rows of outer queries, then they’re termed as correlated subqueries. every subquery is dead one time for each row of the outer question.59. Justify information partitioning and its importance.
Ans:
Data partitioning is the method of dividing logical information into freelance units for the betterment of accessibility, performance, and tractableness.60. What does one perceive regarding purposeful dependency and transitive dependency in DBMS?
Ans:
Functional Dependency: A purposeful dependency may be a constraint that’s employed in describing the link among totally different attributes in a very relation.
Example : take into account a relation “A1” having attributes X and Y. The purposeful dependency among these 2 attributes are going to be X -> Y, this suggests that Y is functionally enthusiastic about X.
Transitive Dependency: A transitive dependency may be a constraint which will solely occur in a very relation of 3 or a lot of attributes.
Example : take into account a relation “A1” having attributes X, Y and Z. Now, X->Z is claimed to carry transitive dependency, as long as the subsequent purposeful dependencies holds true :
X -> Y
Y doesn’t ->X
Y -> Z
61. What’s the distinction between 2 and three-tier architectures?
Ans:
| Two-tier design | Three-tier design |
|---|---|
| This is kind of like the client-server design. | This design contains an additional layer between the consumer and therefore the server. |
| Clients directly communicate with the information at the server-side shoppers communicate with an associate degree application(GUI. on the server-side, that produces the system safer and accessible. | This application thenceforth communicates with the information system. |
62. Once was the primary direction system created?
Ans:
History of direction systems the primary package was developed within the early Nineteen Sixties once Charles Bachman created a steering package called the Integrated information Store (IDS. . Shortly after, IBM developed the Info Management System (IMS. , a graded package designed for IBM mainframes that’s still employed by several giant organizations nowadays.
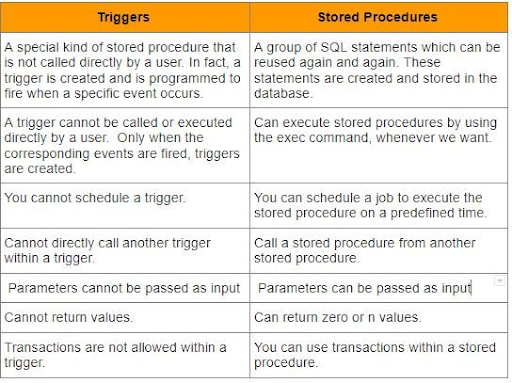
63. Mention the variations between Trigger and keep Procedures
Ans:
64. What are the variations between Hash be part of, Merge be part of and Nested loops?
Ans:
| Hash join | Merge join | Nested loops |
|---|---|---|
| The hash be part of is employed once you need to be part of giant tables. | Merge be part of is employed once projections of the be part of tables are sorted on the join columns. | The nested loop consists of an associate degree outer loop and an inner loop. |
65. What does one perceive regarding Proactive, Retroactive and co occurring Update?
Ans:
Proactive Update : These updates are applied to the information before it becomes effective within the real-world setting.
Retroactive Update : These retroactive updates are applied to information when it becomes effective within the real-world setting.
Simultaneous Update :These updates are applied to the information at an equivalent instance of your time because it becomes effective in a very real-world setting.
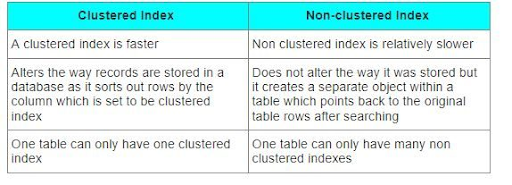
66. What are indexes?
Ans:
Indexes are information structures answerable for up the speed of knowledge retrieval operations on a table. This system uses a lot of cupboard space to take care of additional copies of knowledge by mistreatment further writes. So, indexes are chiefly used for looking out algorithms, wherever you would like to retrieve information in a very fast manner.
67. What does one perceive by pointer? Mention the various varieties of cursor?
Ans:
A pointer may be an information object that helps in manipulating information, row by row and represents a result set.
The types of pointer ar as follows :
Implicit pointer: This kind of cursor is asserted mechanically as shortly because the execution of SQL takes place. Here, the user isn’t indicated regarding the declaration of the pointer.
Explicit pointer: This kind of cursor is outlined by the PL/ SQL, because it handles a question in addition to one row.
68. Justify the terms specialization and generalization
Ans:
Specialization : Specialization may be a method of shaping a group of subclasses of the entity kind. Here, every taxon can contain all the attributes and relationships of the parent entity. aside from this, the subclasses might contain further attributes and relationships specific to itself.
Generalization : Generalization may be a method of finding relations, common attributes for a selected set of entities; and at last shaping a typical taxon for them.
69. What does one perceive regarding information Independence?
Ans:
When you say an associate degree application has information independence, it implies that the appliance is free of the storage structure and information access methods of knowledge.
70. What are the various integrity rules gifts within the DBMS?
Ans:
The different integrity rules gift in package ar as follows :
Entity Integrity: This rule states that the worth of the first key will ne’er be NULL. So, all the tuples within the column are known because the primary key ought to have a price.
Referential Integrity: This rule states that either the worth of the foreign secret’s NULL or it ought to be the first key of the other relation.
71. What will the Fill issue thought mean with relation to indexes?
Ans:
Fill issue is employed to say the proportion of area left on each leaf-level page, that is jam-choked with information. Usually, the default price is a hundred.
72. What’s Index looking and the way will it facilitate up question performance?
Ans:
The process of boosting a set of indexes is understood as Index looking. This is often done as indexes improve the question performance and therefore the speed at which they’re processed.
It helps in up question performance within the following manner :
- The best queries are recommended mistreatment of the question optimizer.
- Index, question distribution and their performance are used as metrics to visualize the result.
- Databases are tuned into a little assortment of drawback queries.
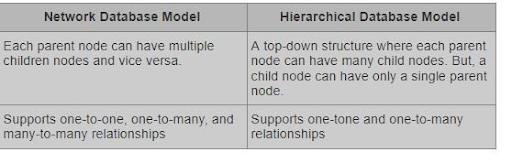
73. What are the variations between network and graded information models?
Ans:
74. Make a case for what’s a stalemate and mention however it may be resolved?
Ans:
Deadlock could be a state of affairs that happens once 2 dealings attend a resource that is secured or different transaction holds. Deadlocks may be prevented by creating all the transactions and acquiring all the locks at identical instances of your time. So, once a stalemate happens, the sole thanks to cure it’s to abort one amongst the transactions and take away the completed work.
75. What area unit the variations between Associate in Nursing exclusive lock and a shared lock?
Ans:
Exclusive Lock : Associate in Nursing exclusive lock could be a lock on an information item once a deal is on the brink of performing the write operation.
Shared Lock : A shared lock permits quiet one dealings to scan the information.
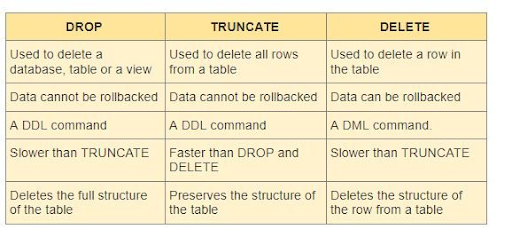
76. What area unit the variations between DROP, TRUNCATE and DELETE commands?
Ans:
77. What area unit the various varieties of DBMS’s?
Ans:
The data held within the information may be retrieved, deleted and changed to support the client’s demand. the various varieties of package area units as follows: relative package (RDBMS. : this sort of package uses a structure that permits the users to access information in respect to another piece of knowledge in a very information.
78. What will DML signify in a very package interview?
Ans:
DML: DML stands for information manipulation language; it’s been used for manipulating information out there in one single information by exploiting some key SQL queries INSERT or DELETE. different sets of SQL queries may be thought of as DML like choose, DELETE, INSERT or UPDATE.
79. What is the commonest kind of DBMS?
Ans:
The most widely used kind of package these days is the computer database Management Systems (RDBMS. . Some direct Systems may be accessed directly by exploiting artificial languages like COBOL whereas others give their own programming language for interacting with the information.
80. Once was the direction system ( package . initial used?
Ans:
The term package has been around since the Sixties once IBM developed the primary package model referred to as data Management System, during which information was held on a very pc in a very class-conscious tree structure. Individual items of knowledge were connected solely between parent and kid records.
81. Mention the variations between distinctive Key and first Key
Ans:
| Unique Key | Primary Key |
|---|---|
| Unique Key will have a NULL price.The first key cannot have a NULL price. | Each table will have quite one distinctive key every table will have just one primary key. |
82. What does one ought to comprehend DBMS’s?
Ans:
History of packages. Introduction. A package (Database management system. is employed to make and maintain the structure of an information, and so to enter, manipulate and retrieve the information it stores. Making Associate in Nursing economical information style is the key to effectively employing information to support Associate in Nursing organization’s business operations.
83. What is the best example of a direction system?
Ans:
A direction system (DBMS) could be a trojan horse designed to manage an outsized quantity of structured information, and run operations on the required information requested by the users. The simplest example of a package is Banking.
84. Was the UN agency the primary person to make a DBMS?
Ans:
Here area unit the necessary landmarks from history: 1960 – Charles Bachman designed initial package system 1976- Peter Chen coined and outlined the Entity-relationship model additionally called the ER model 1985- Object-oriented package developed. 1990s- Incorporation of object-orientation in relative packages.
85. What area unit some samples of direction systems?
Ans:
Some samples of direction system software packages are Oracle, Microsoft SQL Server, PostgreSQL, and MySQL. they’re all samples of computer database management systems. There also are non-relational direction systems Associate in Nursing MongoDB is an example of 1 of these.
86. What area unit some samples of information management systems?
Ans:
The package manages incoming information, organizes it, and provides ways for the information to be changed or extracted by users or different programs. Some package examples embody MySQL, PostgreSQL, Microsoft Access, SQL Server, FileMaker, Oracle, RDBMS, dBASE, Clipper, and FoxPro.
87. What’s the simplest direction software?
Ans:
Oracle information is the most generally used object-relational direction software package. The newest version of this tool is 12c wherever c means cloud computing. It supports multiple Windows, UNIX , and UNIX versions.
88. What’s the primary information system?
Ans:
A database, as a set of knowledge, may be organized thus a direction System will access and pull specific data. In 1960, Charles W. Bachman designed the Integrated information System, the “first” package. IBM, not needing to be unseen, created an information system of their own, called IMS.
89. Once was the primary computer database system created?
Ans:
Two major computer database system prototypes were created between the years 1974 and 1977, and they were the painter, which was developed at UBC, and System R, created at IBM San Jose. painter used a question language called QUEL, and it led to the creation of systems like painter firm., MS SQL Server, Sybase, Wang’s PACE, and Britton-Lee.
90. Once did databases become dominant in PC Science?
Ans:
Often the term “database” is additionally accustomed to loosely visit any of the package, the information system or Associate in Nursing application related to the information. pc scientists could classify information-management systems consistent with the database models that they support. relative databases became dominant within the Nineteen Eighties.
91. What was the evolution of the information system?
Ans:
The Evolution of information. From pre-stage flat-file systems, to relative and object-relational systems, information technology has competed with many generations and its history is over forty years currently. The Evolution : 1968 File-Based: forerunner of information, knowledge was maintained during a file.
92. However long has the evolution of databases lasted?
Ans:
From pre-stage flat-file systems, to relative and object-relational systems, information technology has competed with many generations and its history is over forty years currently. The Evolution : 1968 File-Based: forerunner of information, knowledge was maintained during a file.
93. What was the forerunner of the relative database?
Ans:
From pre-stage flat-file systems, to relative and object-relational systems, information technology has competed with many generations and its history is over forty years currently. 1968 File-Based: forerunner of information, knowledge was maintained during a file.
94. What was the primary class-conscious information within the world?
Ans:
[1968-1980] Era of class-conscious Database: outstanding class-conscious information model was IBM’s 1st software known as IMS ( info Management System . . class-conscious knowledge Model:
95. However square measure Records organized during a class-conscious database?
Ans:
Hierarchical information Model, because the name suggests, could be an information model during which the info is organized during a class-conscious tree structure. Because it is organized and supports the hierarchy, each record of the info tree ought to have a minimum of one parent, apart from the kid records within the last level, and every parent ought to have one or additional kid records.
96. What’s the distinction between class-conscious and network databases?
Ans:
This model permits relationships, and it’s a “schema” (a represented illustration of the relationships. The biggest distinction between the class-conscious model and also the network model is that the network model permits every record to own over one parent and kid record.
97. However, will a class-conscious information model add RDBMS?
Ans:
Hierarchical information Model. information RDBMS engineering. A class-conscious model represents the info during a tree-like structure during which there’s one parent for every record. To take care of order there’s a form field that keeps relation nodes into a recorded manner.
98. Once was the class-conscious information model created by IBM?
Ans:
In order to retrieve knowledge from a class-conscious information the full tree has to be traversed ranging from the foundation node. This model is recognized as the 1st information model created by IBM within the Nineteen Sixties. The class-conscious knowledge Model could be an approach of organizing information with multiple one to several relationships.
99. Why square measure RDBMS employed in non relative databases?
Ans:
Technologically, RDBMS square measure is thought-about primeval. However, the robust theoretical foundation of computer database technology has unbroken it pertinent during a volatile business. This is often why even non-relational databases embody RDBMS-like options, like the SQL interface in Hadoop.
100. What square measures the challenges in DBMS?
Ans:
Challenges of information security in software Last Updated : twenty Aug, 2019 Seeing the immense increase in volume and speed of threats to databases and lots of info assets, analysis efforts got to be thought-about to the subsequent problems like knowledge quality, belongings rights, and information survivability.
Are you looking training with Right Jobs?
Contact Us- Hadoop Interview Questions and Answers
- Apache Spark Tutorial
- Hadoop Mapreduce tutorial
- Apache Storm Tutorial
- Apache Spark & Scala Tutorial
Related Articles
Popular Courses
- Hadoop Developer Training
11025 Learners - Apache Spark With Scala Training
12022 Learners - Apache Storm Training
11141 Learners
- What is Dimension Reduction? | Know the techniques
- Difference between Data Lake vs Data Warehouse: A Complete Guide For Beginners with Best Practices
- What is Dimension Reduction? | Know the techniques
- What does the Yield keyword do and How to use Yield in python ? [ OverView ]
- Agile Sprint Planning | Everything You Need to Know
