
FortiWeb Interview Questions and Answers [FREQUENTLY ASK]
Last updated on 26th Sep 2022, Blog, Interview Question
1. What’s FortiWeb?
Ans:
FortiWeb may be a Firewall service high-powered by net|the online|the net} application (WAF) that provides safety to any applications hosted on the net from threats that concentrate on these web servers. mistreatment multi-layered and correlate detection techniques; FortiWeb secures applications from far-famed vulnerabilities. FortiWeb hardware and virtual machine platforms are obtainable for small & medium scale, massive enterprises, additionally as service suppliers.
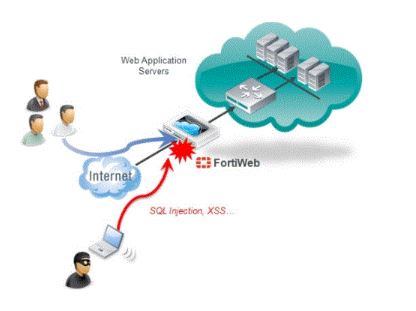
2. However FortiWeb protects the server from threats?
Ans:
FortiWeb’s protocol firewall and denial-of-service (DoS) attack hindrance technologies secure our net applications from attack. It uses advanced methodologies to supply duplex security against difficult risks like SQL injection, across the location scripting (XSS) attacks; FortiWeb additionally defends against threats like fraud, money fraud, and company undercover work. FortiWeb offers the tools required to observe and enforce rules, business best practices, and internal security policies, as well as firewalling and fixture needs.
3.Where FortiWeb fits within the design layout?
Ans:
FortiWeb is deployed as a one-arm to suit apologies however is normally positioned in line to intercept all incoming shopper connections and spread them to servers. FortiWeb has communications protocol and HTTP-specific firewalling capabilities. Since FortiWeb isn’t designed to produce security to non HTTP/HTTPS net applications, it is deployed behind a firewall like FortiGate that focuses on safety for alternative protocols, as well as FTP and SSH. Once FortiWeb is employed, it will assemble from an online browser or terminal individual on the central laptop.
4. What’s HPKP in FortiWeb?
Ans:
Enabling protocol Public Key Promise (HPKP), FortiWeb inserts a header into the server’s response header field once handling shopper requests. The inserted header specifies associate degree exclusive science public key, with that the shopper accesses the server. Specifying a public key for accessing the net server lessens the possibilities of the MITM risks with pretend certificates and compromised CAs.
5. What’s OCSP Stapling?
Ans:
FortiWeb supports OCSP (Online Certificate standing Protocol) stapling, an alternate methodology to OCSP during which the certificate holder often requests the revocation standing of certificates of servers from OCSP servers and attaches the time-stamped response to the initial SSL/TLS handclasp between purchasers and servers. This relocates the resource load of checking the revocation standing of certificates from the shopper to the presenter of the certificate and reduces the entire variety of queries to OCSP servers.
6. Will FortiWeb defend against written document Stuffing?
Ans:
FortiWeb currently protects against written document stuffing attacks. sanctioned written document Stuffing Defense, username, and countersign credentials in an exceedingly net server login try are processed within the information to verify whether or not it’s a spilled username/password combination or not. mistreatment of this feature needs FortiGuard.
7. What’s Active-Active High Availability?
Ans:
Up to eight Forty Webs are deployed as associate degree Active-Active hour angle clusters in Reverse Proxy or True clear Proxy modes. The master unit within the cluster distributes all incoming traffic to alternative cluster members, as well as itself in line with the desired load-balancing algorithm: packet supply informatics, least variety of process connections, or round-robin.
8. What are the protocol Protocol Constraints?
Ans:
Seventeen new protocol protocol constraints are further within the updated versions of FortiWeb. Eight of them ar further to control the precise HTTP/2 header fields, they are:
- Illegal association Preface
- Illegal Frame kind
- Illegal Frame Flags
- Initial Window Size
- Header Compression Table Size
- Header List Size
- Frame Size
- Number of coinciding Streams
The others ar as following:
- Redundant protocol Headers
- Maximum computer address Parameter Name Length
- Maximum computer address Parameter price Length
- Illegal Character in Parameter Name
- Unlawful Character in Parameter price
- NULL Character in computer address
- Unlawful Character in computer address
- Malformed computer address
- illicit Size Chunk
9. What are the protocol Constraint Exceptions?
Ans:
Constraint exceptions ar, further correspondingly for the 5 new protocol constraints:
- Redundant protocol Headers
- Maximum computer address Parameter Name Length
- Maximum computer address Parameter price Length
- Illegal Character in Parameter Name
- Unlawful Character in Parameter price
- HTTP constraint exceptions are applied to the packets with specific supply informatics addresses.
10. What’s FortiWeb architecture?
Ans:
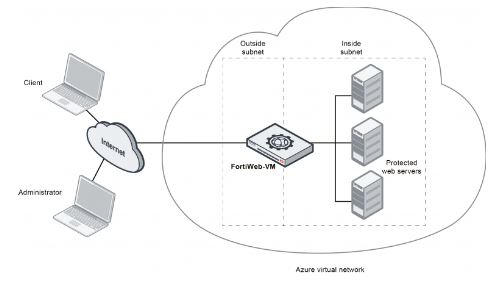
11. What’s website Publishing?
Ans:
Site business enterprise permits golem purchasers to access Microsoft Exchange servers through Exchange ActiveSync. whereas a site-publishing rule is, organized for Exchange ActiveSync, single sign-on, authentication cookie & Kerberos authentication don’t seem to be obtainable, protocol Basic Authentication is that the solely methodology to certify the purchasers.
12. What’s GEO IP?
Ans:
Geo informatics information may be a dedicated information, further to reinforce FortiWeb’s GEO informatics for distinguishing actual locations of IPv6 addresses. it’s not needed to sporadically transfer the GEO informatics information. FortiWeb mechanically updates the information from the FortiGuard Distribution Servers. The interface of manually uploading the information is unbroken for those deployments that don’t have a web association.
13. What’s cookie poisoning?
Ans:
The cookie poisoning settings are currently a section of the new cookie security policy that permits directors to assemble further ways to stop cookie-based attacks. For instance, we will write the cookies issued by a backend server or add security attributes to them.
14. What’s user tracking?
Ans:
The new Americana-tracking feature permits us to trace sessions by a user, capture a username to reference in traffic, and attack log messages. We will use this feature to stop a session fixation attack and set a fundamental quantity throughout that FortiWeb blocks requests with a session ID from a timed-out session.
15. What’s the distinction between True clear proxy mode and clear examination mode?
Ans:
| True clear | Transparent examination |
|---|---|
| True clear – clear proxies within the traffic reaching on any network port happiness to a Layer two bridge, relates to the primary applicable policy, and permits the traffic to pass. FortiWeb logs impede, or maybe modify the violations as per the policy for its safety profile. This mode permits user authentication through protocol rather than HTTPS. | clear examination – Any FortiWeb device asynchronously monitors the traffic reaching its network port, that belongs to the Second Layer Bridge, and applies the device’s initial policy, & permits the safe passage of the traffic. FortiWeb obstructs the traffic about the matching policy and safety profile, however ne’er modifies it. |
16. What are Advanced SSL settings for garçon pool members?
Ans:
When the operation mode is in reverse proxy, {we can|we will|We are able to} choose the versions of SSL and TLS and that cipher suites are supported for connections between FortiWeb and a private server pool member. For true clear proxy and WCCP modes, these apply to connections between FortiWeb and therefore the server pool member also as SSL/TLS offloading.
17. What’s threat scoring?
Ans:
The threat-scoring feature permits the United States of America to put together the policies of signature in any organization to require punitory measures supported varied signature violations on any shopper, rather than one signature violation. Once any shopper violates a signature within the threat-scoring class, it contributes to a combined threat score. Once the combined threat score exceeds the utmost worth that’s nominative, FortiWeb takes action. we will specify the combined threat scores; the calculation is predicated, on protocol transactions or sessions, or communications protocol sessions.
18. What are the standing and Policy standing dashboards?
Ans:
The System Resources gismo on the dashboard displays the count of current connections and connections per second for all the policies. Policy Sessions gismo and Policy standing dashboard show the count of current connections and connections per second by policy On the standing dashboard, graphs within the time period Monitor gismo show total counts for protocol outturn, attack events, and protocol hits, additionally to counts for individual policies.
19. What’s the amount of blocks?
Ans:
When the operation mode is clear within the examination or offline protection and amount Block is that the action, FortiWeb takes action against traffic that violates a policy. FortiWeb tries to dam a shopper that has profaned the policy for the length of your time, nominative by the Block amount.
20. What’s network topology?
Ans:
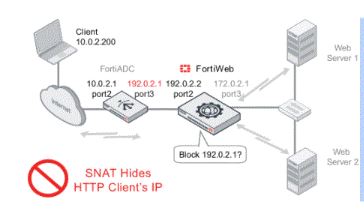
21. What’s DoS?
Ans:
Service Denial (DoS) attack or distributed denial-of-service attack (DDoS attack) is an effort to overpower an online server, creating the resources unobtainable to its supposed users. DoS assaults involve a colossal range of sessions at varied OSI layers and keeping them open as long as possible to overpower the server by overwhelming its accessible sockets. Most DoS attacks use machine-driven tools rather than any browsers to form the harmful and massive range of requests sent to an online server.
22. What’s Botnet?
Ans:
A botnet may be a threat that utilizes zombies, that were antecedently infected, distributed globally, to overpower the server directed by the command on management servers. Examples ar LOIC, HOIC, and Zeus.
23. What’s the reverse proxy mode?
Ans:
When the FortiWeb operates a Reverse Proxy manner, it offers start-to-end HTTP/2 security that desires each the shoppers & HTTP/2 servers running at the back-end. Moreover, once the online servers at the rear finish don’t support HTTP/2, FortiWeb offers the HTTP/2 defense with information amendment protocols between the HTTP/2 shoppers & the HTTP/1.1 servers at the back-end. This allows the user to relish HTTP/2 advantages while not having to upgrade their back net servers.
24. However will HA select the active appliance?
Ans:
An HA try may not resume their active and standby roles once the failing appliance resumes responsiveness to the heartbeat. Since the presently active device is having a bigger uploading time than a failing & active device, that has come back on-line, assumes every has the matching range of the accessible ports, the device that is presently active sometimes holds its standing because the active device, unless it’s been enabled to override. If it’s enabled, and therefore the appliance setting of the returning device that’s higher, are chosen because the presently active device within the cluster.
25. What’s the Topology for offline protection mode?
Ans:
“Out-of-band” may be an appropriate description for this model. stripped-down changes are needed, because it doesn’t introduce any latency. FortiWeb monitors traffic received on the info capture port’s network interface and applies the primary policy. as a result of it not being in line with the destination, it doesn’t permit the allowable traffic. FortiWeb logs in and blocks violations in step with the matching policy and its protection profile. If FortiWeb detects a malicious request, it sends a communications protocol RST packet through the block port to the online server and shopper in an effort to terminate the affiliation. It doesn’t modify traffic.
26. Will we tend to delete the admin account?
Ans:
Admin is the default administrator account and has no word ab initio. The admin administrator account exists by default and can’t be deleted. The admin administrator account is analogous to any root administrator account. This administrator account continuously has all the permission to envision and modify the choices for configuration in FortiWeb devices, as well as the viewing and modifying of all alternative admin accounts. Usernames and permissions aren’t doable to be changed.
27. What’s the Active – passive style?
Ans:
FortiWeb is thought for active-passive vogue, i.e., if one device is selected because the active device, wherever the policies are being applied for all the connections, the other becomes the passive standby, that initiates the role of a vigorous device and starts process the appointed tasks provided that the active device fails. Each active and standby device senses breakdown by communication by the heartbeat link, that connects the 2 devices in hour angle try. Failures are detected once active devices stop responding to a heartbeat from standby devices for a selected time, organized as Heartbeat timeout = Interval in Detection x Threshold in Heartbeat Loss.
28. Will we have a tendency to replicate the external hour angle configuration with none FortiWeb HA?
Ans:
Configuration synchronization offers the flexibility to copy the FortiWeb’s configuration from another device while not requiring high accessibility (HA). The arrangement may be a unilateral push and not a bilateral arrangement. It adds missing things, overwrites objects whose names match however ne’er removes distinctive objects on FortiWeb, nor pulls the things from the target to initiate the FortiWeb device.
29. A way to adapt auto-learning to dynamic URLs & uncommon parameters?
Ans:
Protection settings may be organized with the help of auto-learning. Auto-learning teaches lots of the threats net assets face. It conjointly helps to grasp the net applications’ structures and the way end-users use them. Most significantly, though, auto-learning helps tailor FortiWeb’s configuration to suit net applications. Auto-learning detects the URLs with the opposite behaviors of hypertext transfer protocolS or HTTP sessions by observing the traffic passing to the servers. to find out whether or not the request is legitimate or a possible attack try, it performs the subsequent tasks:
- Evaluate the request to attack signatures.
- Monitors inputs like cookies and uniform resource locator parameters.
- Tracks net servers’ response to every request, like 401 Unauthorized or five hundred Internal Server Error.
- Captures the speed of requests for files by scientific discipline address and content kind.
- By learning from traffic, the FortiWeb appliance suggests acceptable configurations and quickly generates profiles expressly designed for distinctive traffic.
30. What’s a personal internet cloud platform?
Ans:
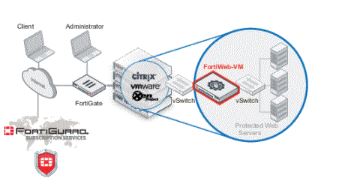
31. The way to put together computer address interpreters?
Ans:
While mistreatment auto-learning, we have a tendency to should outline the way to intercept the dynamic URLs that embrace multiple factors in non-standardized ways in which, like separators (; or #, ) or the issue that is embedded at intervals in the URL’s structure. In any internet programme, these interceptor plug-ins are higher known “URL replacers.”
32. However, will FortiWeb acknowledge knowledge types?
Ans:
FortiWeb acknowledges the info sorts of parameters by matching them with regular expressions. Regular expressions are categorized as: Predefined — Regular expressions set enclosed at intervals in the code. These match common knowledge sorts and can’t be changed except via FortiGuard, however will be traced and used because the basis for a custom knowledge kind. It will be employed by each auto-learning profile and input rules. Custom — Regular expression, that has been designed to find any knowledge patterns that can not be recognized by the predefined set. It will be changed and employed by input rules, however can not be employed by auto-learning profiles.
33. What are Predefined knowledge types?
Ans:
After installation, FortiWeb already has some knowledge-kind regular expressions that are predefined like default signatures for common knowledge sorts in order that we have a tendency to don’t ought to write them once more. Initial ones are enclosed at intervals in the FortiWeb code. If FortiWeb is connected to FortiGuard Military Intelligence Section 5 updates, it will often transfer updates to its predefined knowledge sorts. This provides new and increased knowledge sorts with no effort. solely we should always use the distinctive signatures in elements of the configuration wherever they’re used in step with the organization.
34. What’s your opinion of Fortinet’s FortiGate Firewall?
Ans:
- The rising tendency towards all-in-one merchandise feels like an honest selling plan, however once it involves performance, there’s an enormous gap.
- With one dead box, utterly synchronic with one another operating synergistically, the merchandise is guaranteed to be appreciated. FortiOS discharged by Fortinet with its variety of appliances offers smart routing and cryptography options by enhancing support for RIP I & II and OSPF.
35. What’s UTM?
Ans:
Unified threat management (UTM) may be a move toward security management that permits a network administrator to watch and manage a good kind of security-related applications and infrastructure elements through one management console. UTM appliances not solely mix firewall, entranceway antivirus, and intrusion detection and bar capabilities into one platform however additionally works at intervals themselves interdependently rather like a chunk of material.
36. What’s Security fabric?
Ans:
Security material uses FortiTelemetry to attach completely different security detectors and tools along to gather, coordinate, and answer vicious geste anyplace it happens on the network in a time period. The core of a security material is AN upstream FortiGate set at the sting of the network, with numerous FortiGates performing as net Segmentation Firewalls( ISFWs). A security material is employed to coordinate with the geste of different Fortinet wares within the network, together with FortiAnalyzer, FortiManager, FortiClient, FortiClient EMS, FortiWeb, FortiSwitch, and FortiAP.
37. What is trouble operation?
Ans:
Integrated trouble operation may be a complete approach to network security problems that address multiple feathers of malware, also as diluted pitfalls and spam, and protects from irruption not solely at the hallway still also at the end point situations.
38. What is a Coming- Generation Firewall?
Ans:
- Coming- Generation Firewall( NGFW) is a element of the third generation in firewall technology, combining a conventional firewall with different network device filtering functionalities, like AN operation firewall mistreatment AN in- line.
- different ways may also use, like TLS/ SSL translated business examination, web point filtering, QoS/ bandwidth operation, antivirus scrutiny, and third- party identity operation integration( i.e. LDAP, Compass, Active Directory).
39. What is the distinction between a Next- Generation Firewallvs. ancient Firewall?
Ans:
NGFWs include typical functions of ancient firewalls like packet filtering, network and harborage address restatement( NAT), stateful observance, with virtualnon-public network( VPN) support. The end of coming- generation firewalls is to incorporate a lot of layers of the OSI model, up the filtering of network business that is smitten by the packet contents.
40. What is Fortinet FortiWeb armature?
Ans:
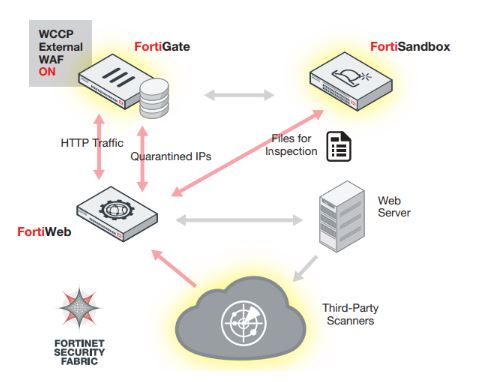
41. Does one realize Fortinet as AN Organization?
Ans:
Fortinet is AN yank MNC with its headquarters in Sunnyvale, California. It develops and markets cybersecurity packages, appliances, and services, like firewalls,anti-virus, intrusion bar, and endpoint security, among others.
42. Tell North American nation one thing regarding Fortinet’s history?
Ans:
Fortinet raised roughly$ 93 million in backing by 2004 and introduced 10 FortiGate appliances. That veritably same time was the launch of a revenant patent disagreement between Fortinet and Trend small. The pot went public in 2009, raising$ 156 million through AN original public immolation.
43. When examining and delivering dispatch dispatches, what will a FortiMail unit liquidate in a clear mode?
Ans:
First, examine contagions, also examine the content of the communication cargo, also examine for spam, followed by playacting a routing operation to determine consecutive hop in MTA.
44. What style of firewall is FortiGate?
Ans:
Fortinet FortiGate Firewalls are Secure SD- WAN-ready security platforms designed to shield home services, SMBs,mid-sized, distributed enterprises, and branches.
45. What are the advantages of the ascendable point in Fortinet Fabric?
Ans:
Fortinet Security material protects any association from IoT to the Cloud. an entire security strategy wants each in- depth performance and deep review alongside the breadth i.e. end to end. Security not solely must gauge to fulfill volume and performance demands, still it also must gauge itself up indirectly, seamlessly pursuit and securing knowledge from IoT and endpoints.
46. What will Aware mean in Fortinet Security fabric?
Ans:
Security material behaves as one reality from a Policy and work perspective, enabling end- to- end segmentation so as to reduce the peril from advanced pitfalls. We’ve a tendency to not solely go to see knowledge that flows into and out of the network; still, that knowledge passes through the network once it’s within the border. Fortinet Security material permits end- to- end network segmentation for deep visibility and scrutiny of business traveling the network, and controls WHO and what gets to travel wherever thereby minimizing the peril from advanced pitfalls.
47. What is the strategy FortiGate unit uses to work out the provision of an internet cache exploitation wccp?( web cache communication protocol)?
Ans:
The web cache sends AN “ I see you ” communication, being brought by the FortiGate unit.
48. WAN enhancement is designed in active or unresistant mode, formerly can the remote peer settle for an bid to initiate a lair?
Ans:
The pass is going to be accepted formerly there is an identical WAN enhancement unresistant rule.
49. Still will FortiMail Administrator recoup Dispatch Account data from AN LDAP garçon rather than configuring this knowledge manually on the unit?
Ans:
The set up of the LDAP profile sections “ stoner question options ” and “ Authentication ” also associates the profile to the sphere that’s regionally designed.
50. What is the administration companion?
Ans:
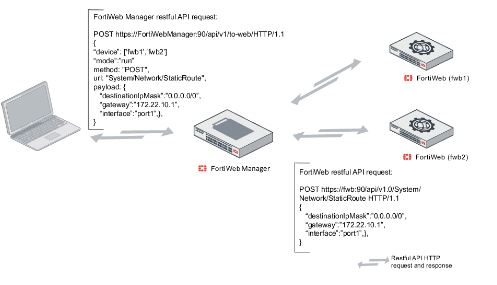
51. Once employing a sender name on a FortiMail unit, is that action taken against a supply informatics address generating spam or invalid E-mail messages?
Ans:
- FortiMail Delays the e-mail messages from that supply informatics address with a short lived failure.
- FortiMail Rejects the e-mail messages from that supply informatics address with a permanent failure.
- FortiMail Quarantines all the e-mail messages from that supply informatics address.
52. What will the safety feature of Fortinet Security material profit us?
Ans:
- Global and native risk intelligence and change data is shared across individual merchandise to decrease time to shield. Not solely will security have to embody powerful security tools for the assorted places and functions within the network, however true visibility ANd management want these distinct components to figure along as an integrated security system.
- Fortinet’s Security material behaves as one cooperative entity from a policy and work perspective, permitting individual product components to share international and native risk intelligence and risk mitigation data.
53. What can we mean by unjust in Fortinet Security Fabric?
Ans:
Big knowledge cloud systems correlate risk data and network knowledge to deliver unjust Threat Intelligence in period. it’s not enough to sense unhealthy traffic or block malware exploitation distinct security devices. Network directors want a standard set of risk intelligence and centralized orchestration that enables the safety to dynamically adapt as a risk is disclosed anyplace, not simply in our network, however conjointly anyplace within the world. Fortinet’s huge knowledge cloud systems change and correlate risk data and network knowledge and supply unjust threat intelligence to every and each single security device within the network’s security material in period.
54.What can we perceive concerning Open arthropod genus in Fortinet Security Fabric?
Ans:
Well-defined, open arthropod genus permits leading technology partners to become a part of the material. Of course, real security material lets North American nations maximize our existing investment in security technologies. That’s why Fortinet has developed a series of well-defined, open arthropod genus that permit technology partners to become a section of the Fortinet Security material. Combined, the Fortinet Security material is in a position to quickly adapt to the evolving specification further as dynamic the threat landscape.
55. Why is that the plan of a security material therefore necessary to network security during this current environment?
Ans:
In this futurist era, corporations need to upset a growing list of problems that place unimaginable strain on their security capabilities, together with the net of Things, virtualization, SDN, aThey even have professionals WHO expect to be ready to access work applications and knowledge from anyplace, at any time, and on a similar device, they use to manage their skilled lives.
56. What distinguishes Fortinet’s security material approach from different vendors’ {attempts|makes AN attempt|tries} at an integrated platform?
Ans:
Fortinet distinguishes itself from different vendors with purposely designed integration starting with a unified OS, extremely optimized hardware and package process with unmatched zero-day discovery, and a detection approach that mixes behavioral detection, machine learning, and hardware virtualization.This allows the Fortinet Security material to travel on the far side what’s potential with a standard signature-based approach to risk protection, or with siloed security technologies that vendors have begun to sew along exploitation AN overlay “platform” technique.
57. However, will Fortinet’s Security material profit Fortinet’s international partner network of distributors and answer providers?
Ans:
Because of its important and complicated character, security continues to be one in all the most important opportunities for the channel. Partners which will arrange, design, deploy ANd optimize an integrated security system square measure finding a growing demand for his or her skills. By combining the standard security devices ANd rising technologies along into an integrated security material, associates will facilitate their customers collect and reply to intelligence that’s a lot of unjust, synchronize risk responses, and change the creation, distribution, and orchestration of their security management and additional investigation.
58. However, is Fortinet’s Fabric-Ready Partner program completely different from the partner programs we have a tendency to see different vendors promoting?
Ans:
Unlike different approaches, Fortinet’s approach truly permits the partners to deliver pre-integrated, end-to-end security offerings prepared for preparation in any organization.
59. AN e-mail message, received by the FortiMail unit is subject to the bounce verification, opposed Spam check, beneath those circumstances?
Ans:
The tagged email address will receive a bounce notice if the email server for the recipient email domain is unable to deliver the email. The bounce address tag will be checked using the private keys by the FortiMail device when the bounce message gets there.
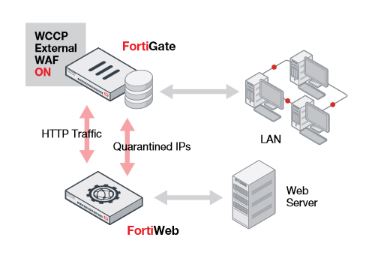
60. What’s Fortinet FortiWeb 1000D architecture?
Ans:
61. Network Administrator of a FortiMail Unit operative in server mode has been given the need to put together disk quotas for all the users of a selected domain. however will the administrator bring home the bacon to this requirement?
Ans:
The network administrator must outline a disk quota price in a very resource profile?
62. That operational mode permits the FortiMail unit to control as a full-featured email server instead of simply a mail relay agent?
Ans:
By sharing IoCs over a seamless Security Fabric, FortiMail is connected with Fortinet products as well as third-party components to let you adopt a proactive approach to security. Through API-level connection, it also provides Microsoft 365 Exchange with sophisticated and additional email security protection.
63. Describe the one reason for deploying a FortiMail unit in clear mode?
Ans:
If the network administrator deploys the FortiMail unit in clear mode then DNS records don’t essentially need to be changed.
64.Which SMTP Sessions is outlined as incoming?
Ans:
SMTP sessions for the protected domain square measure outlined as incoming.
65. That back-end servers wont to offer recipient verification?
Ans:
LDAP servers, and SMTP servers.
66. A supervisor is bothered By the number Of disc space getting used To Store Quarantine Email Messages For Non-existent Accounts. What Techniques are Used On A FortiMail Unit to Stop Email Messages From Being Isolated For Non-existent Accounts?
Ans:
Recipient Address Verification ought to be adopted to stop Email messages from being isolated for non-existent accounts.
67. Within the native Storage Structure Of The Fortimail Unit, What will The non-volatile storage Contain?
Ans:
The contents of non-volatile storage in a very native structure of the Fortimail unit are– microcode pictures with certificates and system configuration.
68. Offer Pine Tree State any 3 variations between ancient and next-generation firewalls?
Ans:
| Traditional | Next generation |
|---|---|
| It works solely from layer a pair of to layer four. | It works on layer a pair of to layer seven. |
| Application-level awareness isn’t supported within the ancient firewall. | Application-level awareness is supported within the ancient firewall. |
| Traditional firewalls don’t support name and identity services. | Next-generation firewalls support name and identity services. |
69. Tell Pine Tree State World Health Organization started Fortinet and when?
Ans:
Ken Xie and Micheal Xie square measure brothers World Health Organization supported Fortinet in 2000. Fortinet is an associate degree yank transnational company that develops cybersecurity solutions.
70. However, installation and reading guide?
Ans:
71. Tell Pine Tree State one thing concerning Fortinet’s FortiGate?
Ans:
FortiGate was the primary and first product of Fortinet. It’s a physical firewall that has protection against machine-driven visibility and malware to eliminate attacks. FortiGate includes net filtering, machine-driven threat protection, Secure Socket Layer(SSL) examination, and IPS(Intrusion bar System). It additionally contains computer science to observe threats proactively.
72. Is Fortinet FortiGate an honest firewall?
Ans:
Whenever somebody needs to shop for a firewall, he checks whether or not the firewall provides smart security or not. He will check if the firewall is at an inexpensive value or not, because the Fortinet FortiGate firewall offers sturdy security and comes at an inexpensive price(starting from thirty seven,987).
73. Tell one thing about an ancient firewall?
Ans:
A traditional firewall may be a network security device that statefully examines the network traffic coming into and existing points among the network supported state, port, and protocol. ancient firewalls will solely track traffic on 2-4 layers; this makes ancient firewalls less effective to supply the protection required to handle all the advanced cyber threats happening during this digital era.
74. What does one understand about a next-generation firewall?
Ans:
A next-generation firewall isn’t solely a network security device that statefully examines the network traffic coming into an existing purpose among the network supported state, port, and protocol. It additionally includes several further options like:
- Integrated intrusion bar.
- Application management and awareness.
- Sandbox integration.
- Web filtering.
- Antispam, Antivirus, Anti-malware.
- Advanced threat protection.
- Deep Packet beginning.
- All these options create the next-generation firewall far better compared to the standard firewall.
75. What does one understand about Fortinet security fabric?
Ans:
Fortinet Security material controls the complete digital attack surface of a company to scale back the chance. It additionally provides broad visibility to deal with several security challenges and eliminates the complexness of supporting multiple purpose products.
76.List many security challenges that Fortinet Security material addresses?
Ans:
Fortinet Security material addresses the below security challenges:
- Expanding attack surface.
- Advanced threat landscape.
- Grater scheme complexness.
- Increasing regulatory demands.
77. Why do we need to use Fortinet UTM?
Ans:
Many firewalls and router-based hardware square measure lacked the power to visualize the applications that square measure crossing the network and creating choices supported this information. however Fortinet UTM provides the provision to visualize the applications that square measure traversing the network. Thanks to this data, the administrator will create choices on whether or not to deny or enable the traffic.
78. What’s integrated threat management?
Ans:
Integrated threat management may be a security approach that consolidates numerous security parts among one application or platform for associate degree IT enterprise design.ITM emerged as a response to progressively difficult and protracted malicious attacks by hackers et al intent upon damaging systems.
79. What square measures the assorted encoding mechanisms obtainable in Fortigate Firewall?
Ans:
Two completely different encoding mechanisms square measure obtainable within the Fortigate firewall they are:
- Advanced encoding normal.
- Data Encryption normal.
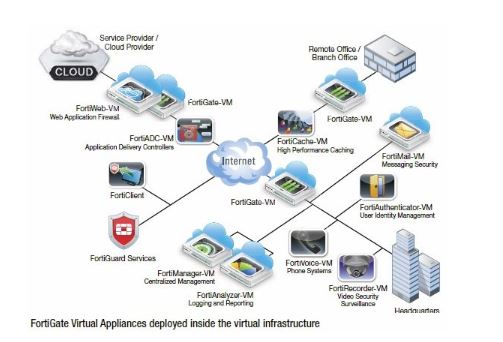
80. What’s FortiWeb VirtualEnvironment?
Ans:
81. What does one fathom FortiCloud?
Ans:
FortiCloud may be a platform of Fortinet that delivers security and management services. With FortiCloud, customers will simply connect, defend and deliver their applications and information on-premise and inside the cloud.
82. List the advantages of FortiCloud?
Ans:
Three primary edges of victimization FortiCloud are:
- FortiCloud saves U.S.A. time and resources.
- Offers clear visibility.
- Extended material security.
83. What’s FortiOS?
Ans:
FortiOS may be a purposeful, security-hardened software that controls all the networking and security capabilities inside FortiGates across your whole network with one inherent software.
84. What’s the software employed by FortiOS?
Ans:
FortiOS uses the UNIX software kernel and numerous different free software package products authorized beneath antelope GPL.
85. Why is FortiAI designed?
Ans:
FortiAI is specifically designed for security operations groups for work threats. FortiAI uses Artificial neural networks and AI to observe and analyze threats primarily based upon continuous learning algorithms.
86. What’s the newest version of FortiS?
Ans:
The latest version of FortiAI is FortiAI V1.5, discharged on March thirty, 2021.
87. What area unit the key options of FortiGate?
Ans:
The top 5 Fortinet FortiGate key options are:
Security ratings: with the assistance of security ratings, we are able to affirm security measures.
Threat Protection: protects antivirus, internet filtering, and malware.
Anomaly-based detection: anomaly-based detection can investigate the traffic and alerts if it finds any attack behavior.
Threat Intelligence: threat intelligence protects our network from cloaked and best-known threats.
Automated risk assessment: machine-controlled risk assessment examines our network mechanically and creates reports.
88. What’s the purpose of FortiMail in an exceedingly convenient mode of transport?
Ans:
When delivering Email messages, the aim of the Fortimail in an exceedingly transport mode is to visualize for any virus, it later checks the content of the message payload, then it inspects for spam. Finally, it performs a routing operation to work out the succeeding hop inside MTA.
89. Rather than manually configuring the e-mail information, will the FortiMail administrator get the e-mail information from the LDAP server?
Ans:
Yes, it’s doable within the LDAP profile section, attend “User question options” and “authentication”, then connect the profile to the domain that’s designed regionally.
90. What’s defacement?
Ans:
91. List the actions taken against a supply information processing address that makes invalid or spam E-mail messages once utilizing the sender name upon a FortiMail Unit?
Ans:
With a brief failure, Fortimail delays the messages sent by that information processing address. With a permanent failure, Fortimail rejects the messages sent by that information processing address. Fortimail restrains all the messages sent by that information processing address.
92. That session of SMTP is outlined as incoming?
Ans:
Protected domains of SMTP area unit outlined as incoming.
93. What’s the utilization of VPN?
Ans:
VPN is abbreviated as Virtual non-public Network wont to mask your IP(Internet Protocol) address. It connects a personal affiliation from a public wi-fi affiliation. A VPA may be an important tool for obscurity and privacy once you are a unit victimizing the general public web.
Are you looking training with Right Jobs?
Contact Us- Hadoop Interview Questions and Answers
- Apache Spark Tutorial
- Hadoop Mapreduce tutorial
- Apache Storm Tutorial
- Apache Spark & Scala Tutorial
Related Articles
Popular Courses
- Hadoop Developer Training
11025 Learners - Apache Spark With Scala Training
12022 Learners - Apache Storm Training
11141 Learners
- What is Dimension Reduction? | Know the techniques
- Difference between Data Lake vs Data Warehouse: A Complete Guide For Beginners with Best Practices
- What is Dimension Reduction? | Know the techniques
- What does the Yield keyword do and How to use Yield in python ? [ OverView ]
- Agile Sprint Planning | Everything You Need to Know
