- How to learn Ethical Hacking?
- How to become a Ethical Hacker ? Know about the requirements to become one
- Introduction to Cyber Security | A Complete Guide
- Top Reasons to Learn Cyber Security | Everything You Need to Know to Become an Expert
- CyberSecurity Framework | How to Implement | A Definitive Guide with Best Practices [ OverView ]
- The Impact of AI and Machine Learning on Cybersecurity | Everything You Need to Know
- What is Certified Ethical Hacker (CEH) Certification and Why is it Important? [ OverView ]
- Benefits Of ECSA Certification | Everything You Need to Know | Expert’s Top Picks
- Top Most OSINT Tools – Open Source Intelligence | Expert’s Top Picks
- Cyber Security Salary in India : Everything You Need to Know
- What is Computer Security? Free Guide Tutorial & REAL-TIME Examples
- Ethical Hacker Salary and Job Description | Everything You Need to Know
- Hacking Tools and Software | All you need to know [ OverView ]
- What is DES? Free Guide Tutorial & REAL-TIME Examples
- How to Become an Ethical Hacker?
- Which are the Best Network Security Certifications?
- Cybersecurity Consultant Career Path
- The Most Effective Data Encryption Techniques
- Great CISSP Books and Study Guides for the CISSP Certification
- What Is Kerberos?
- Top CISSP Domains
- Cyber Security Career Path
- CISSP Certification Exam Guide 2020
- Top Cyber Security Trends for 2020
- CISSP Exam Online 2020
- Compare and Contrast Physical and Environmental Security Controls
- What is information security architect?
- Certified Information Systems Security Professional (CISSP) Certification
- Top Cyber Security Jobs
- What is CISA Certification?
- What is Threat Modeling?
- Certified Information Security Manager (CISM) Certification
- Information Security Management Principles
- Network Perimeter Security Design
- Things You Must Know About Cyber Security in the Cloud
- What is ECSA?
- Why is Cybersecurity Important?
- Tips to Clear Certified Ethical Hacker (CEH) Exam
- Average Annual Salary of a CISSP Certified Professional
- “How to Become a Cyber Security Engineer? “
- Who is an Ethical Hacker?
- What are the requirements to become Cissp certified?
- The Phases of Ethical Hacking
- What is Ethical Hacking?
- Top Ethical Hacking Certifications
- Hash in Python
- How to learn Ethical Hacking?
- How to become a Ethical Hacker ? Know about the requirements to become one
- Introduction to Cyber Security | A Complete Guide
- Top Reasons to Learn Cyber Security | Everything You Need to Know to Become an Expert
- CyberSecurity Framework | How to Implement | A Definitive Guide with Best Practices [ OverView ]
- The Impact of AI and Machine Learning on Cybersecurity | Everything You Need to Know
- What is Certified Ethical Hacker (CEH) Certification and Why is it Important? [ OverView ]
- Benefits Of ECSA Certification | Everything You Need to Know | Expert’s Top Picks
- Top Most OSINT Tools – Open Source Intelligence | Expert’s Top Picks
- Cyber Security Salary in India : Everything You Need to Know
- What is Computer Security? Free Guide Tutorial & REAL-TIME Examples
- Ethical Hacker Salary and Job Description | Everything You Need to Know
- Hacking Tools and Software | All you need to know [ OverView ]
- What is DES? Free Guide Tutorial & REAL-TIME Examples
- How to Become an Ethical Hacker?
- Which are the Best Network Security Certifications?
- Cybersecurity Consultant Career Path
- The Most Effective Data Encryption Techniques
- Great CISSP Books and Study Guides for the CISSP Certification
- What Is Kerberos?
- Top CISSP Domains
- Cyber Security Career Path
- CISSP Certification Exam Guide 2020
- Top Cyber Security Trends for 2020
- CISSP Exam Online 2020
- Compare and Contrast Physical and Environmental Security Controls
- What is information security architect?
- Certified Information Systems Security Professional (CISSP) Certification
- Top Cyber Security Jobs
- What is CISA Certification?
- What is Threat Modeling?
- Certified Information Security Manager (CISM) Certification
- Information Security Management Principles
- Network Perimeter Security Design
- Things You Must Know About Cyber Security in the Cloud
- What is ECSA?
- Why is Cybersecurity Important?
- Tips to Clear Certified Ethical Hacker (CEH) Exam
- Average Annual Salary of a CISSP Certified Professional
- “How to Become a Cyber Security Engineer? “
- Who is an Ethical Hacker?
- What are the requirements to become Cissp certified?
- The Phases of Ethical Hacking
- What is Ethical Hacking?
- Top Ethical Hacking Certifications
- Hash in Python

What is Computer Security? Free Guide Tutorial & REAL-TIME Examples
Last updated on 28th Oct 2022, Artciles, Blog, Cyber Security
- In this article you will get
- 1.Introduction to laptop Security
- 2.Computer Security is concentrated on 3 key areas
- 3.Features of laptop Security
- 4.The different kinds of cybersecurity
- 5.Working principle of pc Security
- 6.Why is pc security important?
- 7.Benefits of pc security
- 8.Conclusion
Introduction to laptop Security
Computer Security is essentially the protection of laptop systems and information from injury, stealing and unauthorized use. It’s a technique to forestall and spot unauthorized use of your computer system. Their square measure varied styles of laptop security that square measure wide used to defend necessary structure information. Laptop security, jointly known as cybersecurity, security of laptop systems and information on injury, stealing and unauthorized use. Laptop systems square measure typically defended by equivalent ways used to shield totally different necessary or sensitive objects — that’s, serial numbers, doors and locks, and alarms.
The elements of a computing system that has to be protected are:
- Computer hardware, virtual part of laptop, like system memory and drive.
- Firmware, a computer code that’s for good put in within the device’s fastened memory and is mostly invisible to the user.
- Software, a program that gives services, like software package, application program, net browser for the user.
Computer Security is concentrated on 3 key areas
- Confidentiality to make sure that data is barely offered to the supposed audience.
- Integrity protects data from being compromised by unauthorized parties.
- Availability protects the data from being processed by unauthorized teams.
- In easy language, laptop Security ensures that laptop data and elements square measure are usable however still secure from folks or computer code that ought to not be accessed or changed.
Features of laptop Security
Many companies run their businesses on-line. Even the epidemic has brought a fresh approach of performing from home practice the online and varied on-line applications. All of these activities manufacture opportunities for cyber criminals to interrupt the system. Therefore, every sure-handed organization has to be compelled to prepare the information to grasp the key aspects of cybersecurity. I don’t know how? IU International University of Applied Sciences offers a degree to spice up your sure-handed skills – the Masters of Science program in Cyber Security is one of the courses you have to be compelled to favor to resolve cybersecurity problems as AN skilled. A good set of cybersecurity choices establishes the first line of defense against attacks and lawlessness. Here could also be a listing to stay in mind.
1.Installation of external threats:
According to the PurpleSec 2021 report, twenty seventh of cyber attacks and incidents come from outside sources. External threats look like phishing scams, Denial of Services, malicious web applications, malicious email attachments, etc. Therefore, security applications connected to the business system ought to monitor these external threats. M.Sc. Cyber Security at IU International University of Applied Sciences can give essential guidance in addressing external threats.
2.Protect yourself from internal threats:
Although many on-line threats come from external sources, from time to time, degree staff at intervals the organization can still be a threat. in line with the twenty Cybersecurity executive director Threat Report twenty, sixty eight p.c of organizations feel vulnerable by internal attacks. In many cases, internal threats occur as a result of staff errors, misconduct, or poor staff alternatives, or unhealthy players. However, a reliable security system and a team of extraordinarily qualified on-line security consultants can minimize these threats from the organization. If you want to become a cybersecurity knowledgeable, choosing a Masters of Science in cybersecurity will assist you understand security principles against internal threats.
3.Compliance with safety rules:
Information security may be a crucial business for every company, be it health or cash. each organization includes a completely totally different set of standards, processes, rules, {and information|and information|and data} sharing and knowledge assortment. Compliance with the principles jointly includes rules, details, and tips for business processes. Cybersecurity officers ought to vogue security compliance in line with trade and placement wants to forestall company data from getting in the wrong hands. MS Cyber Security at IU International University of Applied Sciences guides you in preparing to suit business safety rules.
4.Cloud-based security services:
Cloud-based security services square measure the backbone of assorted security systems. it’s many analytical tools and threatening skills. These services embrace storage areas for security and focus machine learning models to spice up scanning for across-the-board functions. Masters in Cyber Security focuses on cloud-based expertise to master such skills.
5.Threat detection, prevention, and response:
According to a study written in CISO magazine, thirty 5 p.c of CISO consultants evoke a comprehensive security strategy which can stop most (95 out of 100) attacks. In addition, they need the bowl to trace degreed issue associate degree automatic warning of AN attack that might not be stopped. MS Cyber Security or M.Sc. Cyber Security seekers receive work to trace down suspicious activities and complete them. They use tools like hardware and coding system firewall, network analysts, SSL / TLS hosting servers, and totally different applications to search out and stop breaches.
6.Integrated Solutions:
Cybersecurity resolutions have to be compelled to jointly supply a complete resolution to forestall the system (business / individual) from varied threats. For this reason, security consultants have to be compelled to have skills and where to use anti-spam, anti-virus, anti-malware, content filters, wireless security, etc. Such complete protection will stop the system from attackers whereas guaranteeing the confidentiality and security of data and business. actions.
7.Acceptable Protection Statistics:
Every trade uses one factor productive with smart statistics – therefore the protection trade. It’s easy to purpose the finger at insensitive and inevitable threats. A good security analysis jointly helps to observe the danger and respond quickly to matters before it happens.
The different kinds of cybersecurity
Application security:Application security is the implementation of various protections among business code and services to protect against a variety of varied threats. This sort of cybersecurity desires the design of secure applications to attenuate unauthorized access and modification.
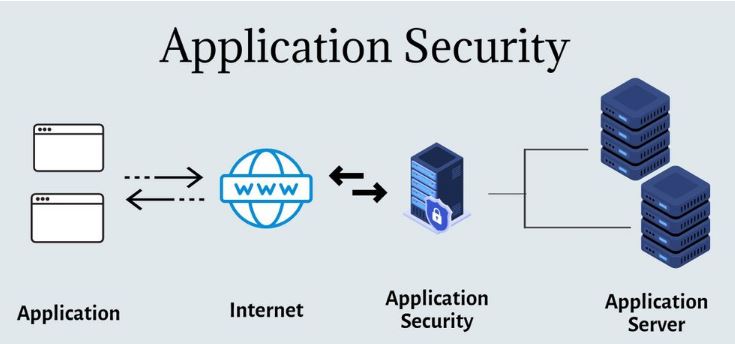
Network Security:Network security focuses on protecting business from external and internal threats through hardware and code programs specifically designed to protect the business network and infrastructure from misuse, disruption, and unauthorized access.
Mobile Security:Businesses that use mobile devices, like mobile phones, laptops, and tablets, have to use cellular security measures to protect the info remaining from those devices from a range of threats.
Cloud Security:Most cloud applications — AWS, Google, Microsoft, etc. — use cloud security to protect users from varied threats.
Examples for pc Security:
Computer Security risks will be caused by malware, that is, malicious computer code, which might infiltrate your pc, corrupt your files, steal your information, or permit the wrongdoer to access your system while not your data or authorization. samples of malware programs embody viruses, worms, ransomware, spyware, and Trojan horses.
Examples of pc Security embody Antivirus programs and Antispyware, Firewall that blocks unauthorized access to the network and VPNs (Visible non-public Networks) used for secure remote access.
Working principle of pc Security
Cybersecurity is also a sophisticated technology tool that uses many tools. It starts with protective rings designed into computer-enabled chips. Basic hardware rules enforce sophisticated security policies. Security in addition depends on but the package is utilized and used. Hackers try to exploit errors inside the protection system to avoid or get into the goals of their access to essential services. This chapter describes a variety of the elemental tools and principles used in secure computer systems.
Cybersecurity is meant to produce multiple layers of protection across all computers, networks, and applications used by businesses. Therefore, in a kind of a combined defense against potential cyber attacks, it’s necessary that business, employees, processes, and technologies are a unit designed to work on seamlessly. Effective Cybersecurity systems are aiming to be able to observe, investigate, and resolve potential vulnerabilities and vulnerabilities inside the system before they’ll be exploited by a cyber criminal or malicious package.
Why is pc security important?
Computer Security may be a method to stop and notice unauthorized use of your pc. Preventive measures assist you stop unauthorized users (hackers) from accessing any part of your ADP system. they sometimes need to require management of your pc so they’ll use it to attack alternative pc systems. During this digital age, we all need to keep our computers and private info secure which is why pc Security is important to stay our personal info secure. It’s additionally necessary to take care of the protection of our pc and its overall health by preventing viruses and malware that will have an effect on system performance.
Computer Security threats:
Computer Security threats unit of measurement threats which will disrupt the standard operation of your laptop computer. Throughout this modern age, cyberbullying threats still grow as a result of the planet becoming digital. the foremost dangerous forms of laptop computer security are:
Virus:A bug may be a bug that’s downloaded to a user’s laptop computer whereas not the user’s information. It replicates and infects files and programs on the user’s laptop computer. The main goal of the virus is to verify that the victim’s laptop computer will ne’er work properly. pc Worm. a PC worm may be a code program that will copy itself from one laptop computer to a special, whereas not human interaction. The potential danger here is that it’ll damage your computer’s disc space as a result of the worm replicating with high volume and high speed.
The crime of stealing sensitive information:Pretending to be Associate in Nursing associate honest person or a business person, fraudsters try and steal sensitive financial or personal information via fallacious email or instant messages. The crime of stealing sensitive information is sadly very easy to use.
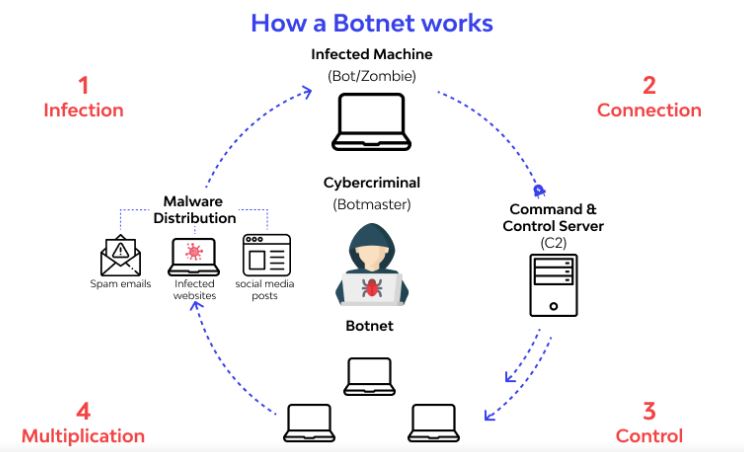
Botnet:A botnet may be associated with an assortment of computers connected to the world wide web that are compromised by a criminal using a bug. Each laptop computer is known as a ‘zombie computer’. The results of this threat to the victim’s laptop computer, which might be used for malicious activity and large-scale attacks like DDoS.
Rootkit:A rootkit may be a bug designed to grant a fairly continuous access to a laptop computer whereas concealment its existence. Once the rootkit is placed in, the rootkit controllers are able to manufacture files remotely and modify system settings on the host machine.
Keylogger:Also noted as keystroke loggers, keyloggers can track the user’s period of time activity on his or her laptop computer.Keylogger is in addition a very powerful threat to steal people’s login information like username and identification. These areas all tell the chance of the foremost common security threats you’ll encounter. Apart from this, there are unit others like spyware, wabbits, scareware, bluesnarfing and much more. fortunately, there unit of measurement ways in which to protect ourselves from these attacks.
Benefits of pc security
Protection of your business : On-line security solutions offer digital protection to your business which can make sure that your workers don’t seem to be exposed to potential threats like Adware and Ransomware.
High productivity : Viruses will impede computers to crawl, and create work not possible. Effective net security eliminates this chance, maximizing the impact of your business.
Promotes shopper confidence : If you’ll be able to prove that your business is with success protected against all styles of crime, you’ll be able to promote confidence in your.
Protecting your customers :Guaranteeing that your business is protected against on-line threats also will facilitate guarding0.27 your customers. The United Nations agency is also in danger of being hacked on-line by a representative.
Stopping your web site from happening : If you’re the business that owns your web site, net infringement is ruinous. If your system becomes infected, your web site is also forced to finish off which suggests you’ll lose cash because of loss of sales.
Conclusion
According to IT specialists, cybersecurity options guarantee complete security of necessary business assets, actions, and data. Medium and huge organizations want all seven purposeful safety features to totally shield themselves by adding some attributes. People who can elect the M.Sc. Cyber Security or on-line masters at Cyber Security can encounter these several cybersecurity options.