- An Overview of AWS Machine Learning Tutorial
- Mapplet In Informatica | Purpose and Implementation of Mapplets | Expert’s Top Picks | Free Guide Tutorial
- Spring Cloud Tutorial
- Azure IoT Hub Integration Tutorial | For Beginners Learn in 1 Day FREE
- Cloud Native Microservices Tutorial | A Comprehensive Guide
- Azure Stream Analytics | Learn in 1 Day FREE Tutorial
- Azure Data Warehouse | Learn in 1 Day FREE Tutorial
- AWS Lambda Tutorial | A Guide to Creating Your First Function
- Azure Logic Apps Tutorial – A beginners Guide & its Complete Overview
- Azure Service Bus Tutorial | Complete Overview – Just An Hour for FREE
- Introduction to Azure Service Fabric Tutorial | Learn from Scratch
- Amazon CloudWatch Tutorial | Ultimate Guide to Learn [BEST & NEW]
- AWS Data Pipeline Documentation Tutorial | For Beginners Learn in 1 Day FREE
- What is Azure App Service? | A Complete Guide for Beginners
- AWS Key Management Service | All You Need to Know
- Apigee Tutorial | A Comprehensive Guide for Beginners
- Kubernetes Tutorial | Step by Step Guide to Basic
- AWS SQS – Simple Queue Service Tutorial | Quickstart – MUST READ
- AWS Glue Tutorial
- MuleSoft
- Cloud Computing Tutorial
- AWS CloudFormation tutorial
- AWS Amazon S3 Bucket Tutorial
- Kubernetes Cheat Sheet Tutorial
- AWS IAM Tutorial
- Cloud Concepts And Models Tutorial
- Cloud Network Security Tutorial
- Azure Active Directory Tutorial
- NetApp Tutorial
- OpenStack tutorial
- AWS Cheat Sheet Tutorial
- Informatica Transformations Tutorial
- AWS vs AZURE Who is The Right Cloud Platform?
- How to Host your Static Website with AWS Tutorial
- VMware Tutorial
- Edge Computing Tutorial
- Cognitive Cloud Computing Tutorial
- Serverless Computing Tutorial
- Sharepoint Tutorial
- AWS Tutorial
- Microsoft Azure Tutorial
- IOT Tutorial
- An Overview of AWS Machine Learning Tutorial
- Mapplet In Informatica | Purpose and Implementation of Mapplets | Expert’s Top Picks | Free Guide Tutorial
- Spring Cloud Tutorial
- Azure IoT Hub Integration Tutorial | For Beginners Learn in 1 Day FREE
- Cloud Native Microservices Tutorial | A Comprehensive Guide
- Azure Stream Analytics | Learn in 1 Day FREE Tutorial
- Azure Data Warehouse | Learn in 1 Day FREE Tutorial
- AWS Lambda Tutorial | A Guide to Creating Your First Function
- Azure Logic Apps Tutorial – A beginners Guide & its Complete Overview
- Azure Service Bus Tutorial | Complete Overview – Just An Hour for FREE
- Introduction to Azure Service Fabric Tutorial | Learn from Scratch
- Amazon CloudWatch Tutorial | Ultimate Guide to Learn [BEST & NEW]
- AWS Data Pipeline Documentation Tutorial | For Beginners Learn in 1 Day FREE
- What is Azure App Service? | A Complete Guide for Beginners
- AWS Key Management Service | All You Need to Know
- Apigee Tutorial | A Comprehensive Guide for Beginners
- Kubernetes Tutorial | Step by Step Guide to Basic
- AWS SQS – Simple Queue Service Tutorial | Quickstart – MUST READ
- AWS Glue Tutorial
- MuleSoft
- Cloud Computing Tutorial
- AWS CloudFormation tutorial
- AWS Amazon S3 Bucket Tutorial
- Kubernetes Cheat Sheet Tutorial
- AWS IAM Tutorial
- Cloud Concepts And Models Tutorial
- Cloud Network Security Tutorial
- Azure Active Directory Tutorial
- NetApp Tutorial
- OpenStack tutorial
- AWS Cheat Sheet Tutorial
- Informatica Transformations Tutorial
- AWS vs AZURE Who is The Right Cloud Platform?
- How to Host your Static Website with AWS Tutorial
- VMware Tutorial
- Edge Computing Tutorial
- Cognitive Cloud Computing Tutorial
- Serverless Computing Tutorial
- Sharepoint Tutorial
- AWS Tutorial
- Microsoft Azure Tutorial
- IOT Tutorial

Cloud Network Security Tutorial
Last updated on 29th Sep 2020, Blog, Cloud Computing, Tutorials
When the Internet came into existence, it created a massive revolution. These days it is very famous and useful for satisfying people with various services related to various fields and people are dependent on the internet for various services. It also gave rise to cloud computing which provided a centralized platform for storing and accessing data but it has many security issues.
What is Cloud Computing?
- It’s internet computing
- Computations are done through the Internet
- No worry about any maintenance or management of actual resources
Shared computing resources 4 So, Cloud Computing is:Cloud computing is a model for enabling convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service
Threats to Cloud Computing
1.Abuse and Nefarious Use of Cloud Computing
2.Insecure Application Programming Interfaces
3.Malicious Insiders
4.Shared Technology Vulnerabilities
5.Data Loss/Leakage
6.Account, Service, and Traffic Hijacking
7.Unknown Risk ProfileFrom Cloud Security Alliance, 2010
Subscribe For Free Demo
Error: Contact form not found.
Abuse and Nefarious Use
- Password and key cracking
- DDOS
- Launching dynamic attack points
- Hosting malicious data
- Botnet command and control
- Building rainbow tables
- CAPTCHA solving
- Exploits exist already
Insecure Interfaces and APIs
- Could expose more functionality than intended
- Policy could be circumvented
- Credentials may need to be passed –is the interface secure
Malicious Insiders
- Particularly poignant for cloud computing
- Little risk of detection
- System administrator qualifications and vetting process for cloud services provider may be different than that of the data owner
Shared Technology Issues
- 1. Underlying architecture (CPU cache, GPU, etc.) not intended to offer strong isolation properties
- 2. Virtualization hypervisor used to mediate access between guest OS and physical resources
- 3. Exploits exist (Blue Pill, Red Pill)
- 4. Data Loss or Leakage
- 5. Data is outside the owner’s control
- 6. Data can be deleted or decoupled (lost)
- 7. Encryption keys can be lost
- 8. Unauthorized parties may gain access
- 9. Caused by Insufficient authentication, authorization, and access controls
- 10. Persistence and remanence
- 11. Poor disposal procedures
- 12. Poor data center reliability
- 13. Account or Service Hijacking
- 14. Exploits phishing attacks, fraud, or software vulnerabilities
- 15. Credential reuse
- 16. Unknown Risk Profile
How well is the cloud being maintained?
- Many companies are unwilling to release details
- Is the infrastructure up to date Patches
Firmware
Does the combination of different service providers create previously unseen vulnerabilities
Introduction of cloud computing
Cloud computing is the concept that data can be stored in a centralized space, in the cloud, and accessed anytime from anywhere through thin clients. This has many advantages, including data ubiquity and flexibility of access. In many ways, it also enhances security. However, since cloud computing puts data outside of the control of the data owner, it introduces security issues too.
Cloud computing security concerns with all the conditions of making cloud computing secure. Many of these aspects are not unique to the cloud setting: data can be attacked irrespective of where it is stored. Therefore, cloud computing security encompasses all the topics of computing security, including the design of security architectures, minimal attack surfaces & protection from viruses. But there are some aspects of cloud computing security that appear to be specific to it.
Cloud computing providers give common business applications which can be accessed from servers through the internet .
- The cloud is typically a shared resource, and other sharers may be attackers.
- Cloud based data is usually intentionally widely accessible by APIs across public networks.
- Data in the cloud is vulnerable to being lost.
Cloud Security
- Security in cloud computing is an important concern.
- Data in the cloud is necessary to be stored in encrypted form. It restricts the client from accessing the shared data directly. For this purpose proxy and brokerage services are necessary to employ.
- Encryption helps to protect transferred data as well as the data stored in the cloud. Encryption also helps to protect data from any unauthorized access, but it does not prevent data loss.
Planning of security
In security planning, before deploying a particular resource to cloud there is a need to analyze different aspects of the resources which are as follow:
- Select a resource which requires you to move to the cloud and examine its sensitivity risk.
- The cloud service models i.e IaaS, PaaS and SaaS are necessary to be considered for security at different levels of services.
- The cloud types, i.e public, private, community, hybrid also need to be considered.
- The risk in a cloud deployment generally depends on the types of cloud and service models.
Security Boundaries
- A specific service model defines the boundary among the responsibilities of customer and service provider.
- The boundaries between each service model are defined by Cloud Security Alliance (CSA) stack model.
Following diagram shows the cloud security alliance (CSA) stack model.
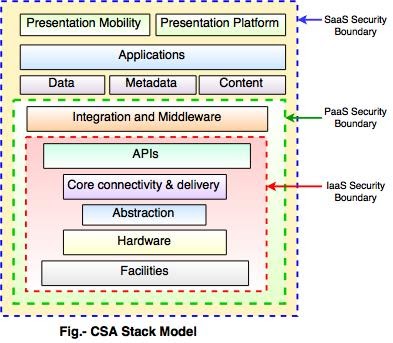
Key things in above model:
- 1. IaaS is the basic level of service. PaaS and SaaS are the next levels of services.
- 2. IaaS gives the infrastructure, PaaS gives a platform development environment and SaaS gives operating environment.
- 3. IaaS has the minimum level of integrated functionalities and integrated security while the SaaS has the highest.
- 4. The security boundaries are described in this model. At the security boundary, cloud service provider responsibilities end and the customer’s responsibilities start.
- 5. The security mechanism below the security boundary is necessary to construct into the system and should be maintained by the customer.
Data security in cloud
Data security in the cloud is an important concern because all the data is transferred using the Internet.
Following are the mechanisms for data protection.
I) Access Control
ii) Auditing
iii) Authentication
iv) Authorization
Isolated Access to Data
- 1. Data stored in the cloud can be retrieved from anywhere, hence it should have a mechanism to isolate data and protect it from clients direct access.
- 2. To isolate storage in the cloud, Brokered Cloud Storage Access is an approach.
Following two services are generated in this approach:
- 1. A broker with complete access to storage, but no access to clients.
- 2. A proxy with no access to storage, but access to client and broker both.
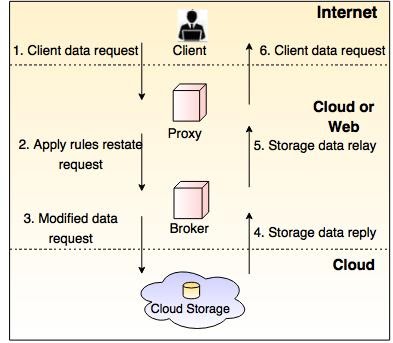
Working of Brokered Cloud Access System
Following are the steps to access the data:
- The client data request goes to the external service interface of the proxy.
- The proxy forwards the request to the broker.
- The broker requests the data from a cloud storage system.
- The cloud storage system returns the data to the broker.
- In the next step, the broker returns the data to the proxy.
- The last proxy sends the data to the client.
Ways to secure cloud storage
A good path to security in a cloud configuration can be very challenging. This is complicated by the different types of cloud we use – public or hybrid – and the class of data and computing we assign to those cloud segments. Generally, one can create a comprehensive and compliant cloud security solution, but a nuanced approach to different use cases is almost required.
Let’s first disclose a few myths. The cloud is a very safe place for data, despite FUD from those who might want you to stay in-house. The large cloud providers (CSPs) maintain a tight ship, simply because they would lose customers otherwise.
At the same time, CSP-encrypted storage is also not safe. If the CSP uses drive-based encryption, don’t consider it secure. Security researchers in 2015 revealed flaws in a hard drive product line that rendered the automatic encryption useless. This is lazy man’s encryption! Do it right and encrypt on the server with your own key set.
Part of the data security rule is that data must maintain its integrity even under attack by external sources. It isn’t sufficient to have one copy of data; just think what would happen if all the four copies of a set of files in your S4 pool are all updated by virus(malware). If you don’t provide a protection mechanism for this, you are likely going to lose it!
There are various ways of protecting the data.
A.Encryption
The first challenge in protecting data stored in the cloud is preventing a hacker who has gotten inside your firewalls from reading, editing or deleting files.
The hacker should not be able to access the files from the cloud and use it for illegal purposes. To protect the data in the cloud from unauthorized access, we use encryption. The obvious answer is encryption.
The safest way to encrypt the data is to encrypt key data in the server at the source and manage the keys yourself. It might be argued that data in transit isn’t so vulnerable for attack, but we are entering a generation of SDN with network virtualization, making in-transit protection a must. This requires a lot of discipline, but that’s essential for a rugged system.
B.Take Responsibility For Security
The general conception today is that the large public clouds storage services are the safe places to work. Cross-tenancy attacks have been nullified by some of the CPU hardware changes and improvements in the code.
Having said that, any installation is vulnerable to the same sort of attacks as any set up, including human error, viruses, other malware, password guessing. The public and private cloud installations typically have a much bigger attack area than a dedicated server deployment. Assuming the CSP is responsible for security is plain wrong. Just as in any data centre, you must pay deep attention to security services and shrink the attack surface down to the size.
But the main problem is the volatility of deployments in the cloud. Instances come and go. Tracking this requires an automated security monitor platform, it is a kind of software that identifies attempted unauthorized cross-tenant access and detects unusual access patterns.
Private cloud: Private cloud can be owned and managed by the private or the third-party organization and exist at on-premises or off-premises. It is more expensive when compared to public cloud service.
C.Data Protection
Even encrypted data is under the risk of deletion or damage. Failed hardware, virus programs (malware) or bad software are all the main contributors to this risk. While not just a security issue, there are some common fixes for this issue.
The backup copies of data also need to be secured by replication or coding across geographically-dispersed zones in the cloud platform. Physical security for power grid systems is not as good as for the public cloud data centres, which are also at risk of acts of God.
One solution is to keep the data away from reach. Backups or frequent snapshots are a good way of minimizing the amount of exposed data. The first method makes an offline copy, while screenshots keep all the data and add only new versions when a change takes place. In both cases, only a very small amount of data is exposed enhancing data security.
Organizations always have a risk of not following the government policies as would be explained further while the cloud vendors who expose sensitive information risk the legal liabilities. Virtual co-tenancy of sensitive and non-sensitive data on the same host platform also carries its own possible risks .
D. Data Management
Many clouds and data centres suffer from weak data management. There are partial data sets scattered all over the storage pool which gives rise to poor data management and this data is also not secure. Collecting trash data is a huge and difficult task, complicated by versioning of files and a lack of naming discipline that leads to many files with similar names.
These are all security risks possible. The possibility of a critical file getting into a low-security area cannot be ignored. The answer is to first keep an eye on the data proliferation process using a deduplication process, which was intended to save storage space but security might be a much more important application, and removing extra copies from storage would reduce the problem.
The issue of data access is mainly related to security policies provided to the users while accessing the data. In a typical scenario, a small organization can use a cloud provided by some other service provider for carrying out its own business processes. This organization will have its own security policies based on which each employee can have access to a particular set of data. The security policies may entitle some considerations wherein some of the employees are not given access to certain amount of data which is called data abstraction. These security policies must be followed by the cloud to avoid intrusion of data by unauthorized users.
Deduplication would not get rid of files in wrong places. This requires a metadata driven approach that puts a life expectancy and location as well, copying and other controls on data. These tools are just entering the storage market.
E.Protecting APIs and Images
When Operating Systems or app code images on cloud nodes get out of synchronization, we can get boundary errors that mess up the data. Files get left behind the surface, edits on the data hit the wrong data. In the worst case, the data and code are incompatible and data corruption occurs.
This can happen through careless upgrades made in the code, where some nodes are left over using older code revisions during operations. It is possible for viruses to exploit the lack of synchronization. The solution is to use available software for automated updating of code images across all nodes so that each and every code is updated, with auditing to check that the update is properly executed and running.
F.Secure Access
If you want secure operations on your database, do not trust the people! A notable portion of major data losses have an insider person involved, but that’s not the only issue with the people. The most common password in the world is 123456 and hackers will always try this combination. Assume passwords are always compromised. Use multi-factor authentication; it’s a bit slower, but much safer. Use a combination of numbers, characters and special characters to make a strong password that is very hard to be identified by a hacker.
The other part of the people issue is admin error. There is a risk of finger trouble, especially with the CLI-based software, where a simple transpose by a tired admin might delete all your database and the records. Consider this and limit who can do certain tasks limiting the access to certain areas only. Limit access, too, so that admins cannot enter systems they do not have knowledge of.
Much of the data which is stored today is linked to mobile devices. Some data can be linked down by two-factor authentication service, but the risk of a mobile user accessing data in unauthorized places and stealing files is a crucial risk
IMPORTANCE OF CLOUD SECURITY
With the help of cloud storage service, the data is backed up to the cloud platform rather than stored on-site or nearby locations. Some businesses are still backing up to tapes, secondary storage devices, or storing their data backups on-site or at a nearby off-site location. If there is a local disaster in that place, then this could result in both backups being lost easily. Cloud security prevents this issue, as the data is stored in remote locations, protecting the business data from the threat of data loss and data is always secure.
- Cloud security is very crucial for both business and personal users. Everyone using the cloud wants to know that their information is safe and secure and businesses have legal obligations and rules to keep client data secure, with certain sectors having stricter rules about data storage.
- Security is a very crucial element of a cloud service platform and one should always check that the service provider can provide the correct levels of security for your industry or not.
- Using cloud antivirus software and backups can be an integral part of a security plan. Threats come from internal and external sources. External threats include hacking whereas internal threats include disgruntled staff members and error created by humans. It is important to cover every eventuality in your security plan, so that you can protect your business from these major security threats. Many businesses have not prepared or tested to ensure they are safe from potential security breaches, whether these come from internal or external sources.
