- How to learn Ethical Hacking?
- How to become a Ethical Hacker ? Know about the requirements to become one
- Introduction to Cyber Security | A Complete Guide
- Top Reasons to Learn Cyber Security | Everything You Need to Know to Become an Expert
- CyberSecurity Framework | How to Implement | A Definitive Guide with Best Practices [ OverView ]
- The Impact of AI and Machine Learning on Cybersecurity | Everything You Need to Know
- What is Certified Ethical Hacker (CEH) Certification and Why is it Important? [ OverView ]
- Benefits Of ECSA Certification | Everything You Need to Know | Expert’s Top Picks
- Top Most OSINT Tools – Open Source Intelligence | Expert’s Top Picks
- Cyber Security Salary in India : Everything You Need to Know
- What is Computer Security? Free Guide Tutorial & REAL-TIME Examples
- Ethical Hacker Salary and Job Description | Everything You Need to Know
- Hacking Tools and Software | All you need to know [ OverView ]
- What is DES? Free Guide Tutorial & REAL-TIME Examples
- How to Become an Ethical Hacker?
- Which are the Best Network Security Certifications?
- Cybersecurity Consultant Career Path
- The Most Effective Data Encryption Techniques
- Great CISSP Books and Study Guides for the CISSP Certification
- What Is Kerberos?
- Top CISSP Domains
- Cyber Security Career Path
- CISSP Certification Exam Guide 2020
- Top Cyber Security Trends for 2020
- CISSP Exam Online 2020
- Compare and Contrast Physical and Environmental Security Controls
- What is information security architect?
- Certified Information Systems Security Professional (CISSP) Certification
- Top Cyber Security Jobs
- What is CISA Certification?
- What is Threat Modeling?
- Certified Information Security Manager (CISM) Certification
- Information Security Management Principles
- Network Perimeter Security Design
- Things You Must Know About Cyber Security in the Cloud
- What is ECSA?
- Why is Cybersecurity Important?
- Tips to Clear Certified Ethical Hacker (CEH) Exam
- Average Annual Salary of a CISSP Certified Professional
- “How to Become a Cyber Security Engineer? “
- Who is an Ethical Hacker?
- What are the requirements to become Cissp certified?
- The Phases of Ethical Hacking
- What is Ethical Hacking?
- Top Ethical Hacking Certifications
- Hash in Python
- How to learn Ethical Hacking?
- How to become a Ethical Hacker ? Know about the requirements to become one
- Introduction to Cyber Security | A Complete Guide
- Top Reasons to Learn Cyber Security | Everything You Need to Know to Become an Expert
- CyberSecurity Framework | How to Implement | A Definitive Guide with Best Practices [ OverView ]
- The Impact of AI and Machine Learning on Cybersecurity | Everything You Need to Know
- What is Certified Ethical Hacker (CEH) Certification and Why is it Important? [ OverView ]
- Benefits Of ECSA Certification | Everything You Need to Know | Expert’s Top Picks
- Top Most OSINT Tools – Open Source Intelligence | Expert’s Top Picks
- Cyber Security Salary in India : Everything You Need to Know
- What is Computer Security? Free Guide Tutorial & REAL-TIME Examples
- Ethical Hacker Salary and Job Description | Everything You Need to Know
- Hacking Tools and Software | All you need to know [ OverView ]
- What is DES? Free Guide Tutorial & REAL-TIME Examples
- How to Become an Ethical Hacker?
- Which are the Best Network Security Certifications?
- Cybersecurity Consultant Career Path
- The Most Effective Data Encryption Techniques
- Great CISSP Books and Study Guides for the CISSP Certification
- What Is Kerberos?
- Top CISSP Domains
- Cyber Security Career Path
- CISSP Certification Exam Guide 2020
- Top Cyber Security Trends for 2020
- CISSP Exam Online 2020
- Compare and Contrast Physical and Environmental Security Controls
- What is information security architect?
- Certified Information Systems Security Professional (CISSP) Certification
- Top Cyber Security Jobs
- What is CISA Certification?
- What is Threat Modeling?
- Certified Information Security Manager (CISM) Certification
- Information Security Management Principles
- Network Perimeter Security Design
- Things You Must Know About Cyber Security in the Cloud
- What is ECSA?
- Why is Cybersecurity Important?
- Tips to Clear Certified Ethical Hacker (CEH) Exam
- Average Annual Salary of a CISSP Certified Professional
- “How to Become a Cyber Security Engineer? “
- Who is an Ethical Hacker?
- What are the requirements to become Cissp certified?
- The Phases of Ethical Hacking
- What is Ethical Hacking?
- Top Ethical Hacking Certifications
- Hash in Python

Ethical Hacker Salary and Job Description | Everything You Need to Know
Last updated on 27th Oct 2022, Artciles, Blog, Cyber Security
- In this article you will get
- 1.Introduction of moral Hacker earnings and Job Description
- 2.Skills of moral Hacker
- 3.Features of moral Hacker
- 4.Types of moral Hackers
- 5.Structure of moral hacker process
- 6.Why is moral hacking is extremely important?
- 7.Benefits of moral Hacker
- 8.Conclusion
Introduction of moral Hacker earnings and job description
A moral criminal evaluates the organization’s use of digital security to spot its weaknesses and propose development consequently. they’re professionals WHO will access networks to notice security risks. Black hat hackers use this threat to interrupt the organization’s cybersecurity system. Therefore, honest hackers typically check the company’s network plans to spot area units that are in danger and repair them. They conjointly train organization workers on best practices and standards.
By hijacking a computer virus, the hacker should fits the subsequent rules:
- Written permission to scan the network and commit to determine potential security risks.
- While participating in dishonorable or connected activities, a hacker ought to respect the privacy of the individual or the corporate.
- After finishing his task, the villain shouldn’t leave something open for somebody else to use later.
- Before hacking, a hacker ought to inform software package developers or software package developers that they’re conscious of any security risks to their software package or hardware.
- In this case, the new moral Hacker will expect to receive Rs four.8 hundred thousand each year. However, candidates with teaching qualifications and work expertise area unit up to Rs thirty hundred thousand each year.
- Committing criminal acts involves repetition of the ways and actions of vicious attackers. This observation helps to spot security risks that may be addressed before a malicious aggressor gets an opportunity to use them.
Skills of moral Hacker
Good gang skills and also the role of white hats hacks:
Simply put, the work of a well-behaved criminal is to approach AN organization as if it were an online criminal, repeat a vicious criminal on the work then stop following the attack. Instead, they’ll report any danger or concern and get counter-measures to strengthen the system’s defenses.
A well-behaved criminal might use one or a lot of of those ways to urge into the system or notice danger:
- Port scanners like Nmap or Nessus are accustomed to scan organizational systems and notice open holes. The risks for every port are often assessed and remedial measures taken.
- It checks the installation of safety features and makes sure they’re not exploited.
- Engaging in social engineering concepts like container diving — virtually looking for trash cans to seek out passwords, charts, sticky notes, or the rest that has valuable info that may be accustomed turn out AN attack.
- Using alternative social engineering techniques like shrugging your shoulders to achieve access to special info or enjoying a kindness card tricks staff into yielding their passwords.
- Make efforts to avoid IDS (Intrusion Detection Systems), IPS (Access management Programs), honey pots, and firewalls.
- Networks that smell, skip and break wireless encoding, and hijack internet servers and internet applications.
- Investigating problems associated with mobile laptop stealing and worker fraud.
- Ethical hacker criminals are wrongfully needed to report any issues they encounter throughout their work, as this can be legitimate info (in theory, at least) that would be used for bootleg functions.
Features of moral hacker
- They have smart morals. Moral hackers typically gain access to hints.
- They are patient and protracted. felony within the system doesn’t simply happen.
- They are sort of a hacker.
- Focus on the main points.
- They love the challenge.
- They ne’er stop reading.
A person with a code of ethics is predicted to be adept in managing info, network, and applications and has wonderful soft skills as they have to speak about security problems across the organization. additionally to those common skills, the moral criminal conjointly understands the subsequent skills well:
- Smell of network traffic
- Set up numerous network attacks
- Use the danger of overflow baths
- SQL injection
- Guess and watchword
- Session hijacking and spoofing
- DNS spoofing
Apart from this, the ethical hacker ought to be artistic as a result of black hat hackers forever coming up with clever ways in which to use the system and it’s the work of the hacker of the character to predict and s
Types of moral Hackers
It is no secret that any system, process, website, device, etc are often hacked. To know however felony will occur and the way it is often harmful, honest hearted hackers have to be compelled to know they feel as malicious hackers and grasp the tools and techniques they will use.
Types of Hackers:
The hackers area unit of various sorts and area unit named supported their intent to hack. Overall, there are 2 major hackers – White-Hat hacker and Black-Hat hacker. The names are a unit derived from the traditional pasta Westerns, where the great man wears a white hat and also the evil one wears a black hat.
Job profile for moral hackers
After getting the much-needed CEH v10, an ethical criminal might attempt the subsequent roles:
- Information Security Analyst
- Security Analyst
- Certified moral Hacker (CEH)
- Ethical Hacker
- Information Security Manager
- Login Checker
How its works?
- Moral criminals use their data to safeguard and improve organizational technology. they supply essential services to those organizations by considering the risks that will result in security breaches. A moral hacker criminal reports AN known threat to an organization.
- Here are some samples of real-life recruits from real hackers WHO represent the traditional activities they will be performing arts in their roles.
- Manage work methods and work collaboratively with numerous groups to enhance web site style and usefulness.
- Hire a hacker to hack facebook accounts.
- Hack, grade, & stack brick.
- Include cheap promoting methods like Adwords and SEO to form cash.
- Perform daily information queries, produce comments on the location victimization SQL.
- I worked ethically with the Kali UNIX system and learned regarding physical security and cyber security.
- Established on-line consulting services.
- Use mobile-first interface styles victimization HTML5 levels.
- Update the list of accessible properties with info and photos.
- Support multiple departments within the development of computer network sites and applications.
Structure of moral hacker process
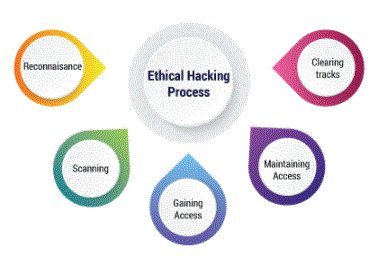
What it takes to become associate degree moral hacker?
If you’re a former “bad hacker” World Health Organization set to wear your black and white hat, then you’re in all probability acquainted with mercantilism. However, you must even be aware that activity cheating skills (such as immoral cheating skills) square measure perpetually ever-changing. Nearly as good guys square measure continually attempting to stay up with the most recent trends, it’s necessary to stay on your edge by keeping your ear down.
As with any profession, love of business is one amongst the keys to success. This, combined with sturdy network information and coming up with, can facilitate the skilled to stand out within the field of fine-tuning. Knowing the way to suppose sort of a black hat shooter is key to developing a person’s moral cheating skills, however you furthermore may ought to have a transparent plan of your final goal of up the protection of your leader (or client).
Like alternative laptop and network security roles, cybercriminals square measure in high demand, and this demand solely grows because the intensity and value of cyber attacks still rise. As you would possibly expect, organizations that square measure in dire want of competent and licensed moral hackers square measure willing to pay a premium. Within the U.S., the common annual remuneration for a resourceful legal criminal is $ ninety,000, however salaries typically go on top of $ a hundred and twenty,000 for knowledgeable professionals.
Why is moral Hacking is extremely important?
The main advantage of moral larceny is to safeguard the info from the larceny and misuse of malicious attackers, further as: To notice danger from the attacker’s POV in order that weak points square measure corrected. employing a secure network that stops security breaches.
Their square measure has such a lot of compelling reasons to think about ethical fraud, and a few of them could surprise you! For instance, did you recognize that there live} additional cyberattacks happening now than ever before within the history of the universe? The most recent measure of this can be somewhere between one attack each eleven to fourteen seconds.
This means that corporations, no matter their size or power or profit, square measure continually in danger of losing their valuable knowledge, further as any business secrets they will be keeping reachable. gratuitous to mention, this interprets to a really specific concern once it involves assessing on-line safety issues, further as being in danger of threats, notwithstanding what a part of the spectrum is hospitable block.
And there’s a really sensible reason behind the enlarged responsibility currently that must be borne by moral hackers. trust it – knowledge, while not a doubt, is one amongst the foremost necessary things a corporation will turn out, acquire, or exchange these days. Therefore, it will have a right away impact on the company’s line, to not mention the highest one.
Ethical criminals square measure thus abundant required lately, not solely as a result of they’ll shield the info required by corporations on a usual, however conjointly as a result of they’ll give valuable concepts on the way to create existing security systems higher and additional economical in terms of observance. against malicious attacks and malware.
If you’re keen on work after you feel the pressure to try to do it daily, then ethical cheating is the right call for your career. If you have got already accepted that during all|one amongst|one in every one of} the most effective ways in which to be recognized is to place yourself in a position to die or to die, then ethical ethics could be excellent for you! Keep reading to seek out what reasonable jobs you expect within the superb field of moral fraud.
Trends for moral hacker:
Growing at the best rate altogether in alternative IT areas, cybersecurity security has emerged as a platform for the best growth of 2017, and presumably throughout the last decade. Throughout the five years between 2012 and 2017, the list of cybersecurity activities enlarged by seventy fifth in keeping with a survey by the Bureau of Labour Statistics. This has semiconductor diodes to several vacant posts such as a lot of jobs square measure well paid.
Benefits of moral hacker
1.Suppose sort of a criminal:
To be ready to perceive the hacker world you have got to be ready to suppose like him. As a result, most people don’t consider them as hijackers. It provides the hijackers a plus. The common person doesn’t grasp what technologies or strategies criminals use to take advantage of the systems they manage. After you take a licensed moral hacker course, you may learn the techniques utilized in excavation and testing entries. you may receive sensible coaching in thinking and acting sort of a criminal. A location the same as the criminal space has been started, thus you’ll be able to see for yourself and mimic the kinds of things you’ll encounter.
2. Shield systems from attack:
As a CEH, you may have complete management over your organization’s systems so you’ll effectively shield them from cyber attacks. there’s a large quantity of information out there on-line for cyber criminals to use. With evidenced crime coaching you may have the hacking skills required to urge into all the weaknesses in your organization’s programs to find out a way to shield that information. Knowing the weaknesses in your system can permit you to double your security perimeter. Doable attacks and intrusion on your organization will cause the loss of necessary information, usually mastercard breaches that build waves within the news, which may have extensive consequences and injure the name of the organization.
3. The hacking business is booming:
Aside from the actual fact that hackers build plenty of cash by stealing, those on the hacking facet of moral hacking are facing a boom. The requirement to coach certified moral hackers has fully grown exponentially because of the requirement for quite five hundred,000 security professionals. With such a lot of organizations under fire, the demand for cash has gone so much on the far side that. Though moral hijackers square measure heavily used by IT companies, different industries like aviation, monetary establishments, and hotels additionally use CEHs. The kinds of profitable jobs out there embody network security managers, security managers and net security managers.
4. Acquire skilled recognition:
This capability alone has emerged mutually of the foremost necessary in protecting the info infrastructure of associate organizations. In addition to the monetary compensation related to such a certificate, you’re additionally recognized as an associate skilled in your field. The CEH certificate is internationally recognized because it is the most vital certification we are able to have within the field of knowledge security. Displaying this certificate can open several closed doors that some fully fledged however not however certified have found not possible to open. consistent with the international organization Council, this certificate could be a complete industry-wide theft course, containing twenty current security bases.
5. Gain info:
Learning all that you simply ought to realize theft, whereas it should be a sensitive subject, also can be fun. Not solely does one increase awareness, however you furthermore might shield your on-line presence by making certain that it’s not compromised. One amongst the most effective points to review so as to become a criminal is to reveal yourself to the globe of the dark net. having the ability to sift through and navigate through the deep black waters of the black net can expose you to the onslaught of pre-existing attacks.
Conclusion
Being a licensed moral Hacker will be useful for pretty much any info security or skilled career. Not solely can you find out about the innovative and profitable business, however you may even be well rewarded for your skills.The availability of jobs during this sector guarantees that you simply can ne’er run out of cash once it involves financial gain. Otherwise you may be recognized as an associate skilled within the field, which may produce additional jobs and increase your possibilities of earning cash.
