
[FREQUENTLY ASK] FortiAnalyzer Interview Questions and Answers
Last updated on 26th Sep 2022, Blog, Interview Question
1.What square measures the basics of FortiAnalyzer?
Ans:
FortiAnalyzer may be a platform that integrates network work, analysis, and coverage into one system, delivering inflated information of security events throughout your network. FortiAnalyzer merchandise minimizes the trouble needed to scrutinize and maintain policies, furthermore establish attack patterns to assist America fine-tune structure policies. In short, FortiAnalyzer provides Centralized work, Analysis, and coverage on a Virtual Platform.
2.What square measures the options and advantages of FortiAnalyzer virtual appliances?
Ans:
Followings square measure the options and advantages provided by FortiAnalyzer virtual appliances:
- FortiAnalyzer virtual appliances offer over 550 reports and customizable charts that help to watch and maintain establish attack patterns, acceptable use policies, and demonstrate policy compliance.
- FortiAnalyzer’s network capability and utilization knowledge coverage permit economical management of the networks.
- The descendible design of FortiAnalyzer permits the devices to run in collector or analyser modes for optimized log process.
- Advanced inherent options inside FortiAnalyzer like event correlation, rhetorical analysis, and vulnerability assessment offer essential tools for in-depth protection of complicated networks.
- Secure knowledge aggregation from multiple FortiGate and FortiMail appliances provides compliance to the complete network.
3.How FortiAnalyzer enhances the visibility inside its Platforms?
Ans:
FortiAnalyzer provides its services like security event analysis, rhetorical analysis, reporting, content archiving, and data processing, malicious file quarantining, and vulnerability management to organizations of any size from a centralized location. Its capability of a centralized assortment of information, correlation, and analysis of the various written account and geographical security knowledge from Fortinet appliances & third-party devices delivers a simplified, consolidated read of organizations’ threat exposure.
4.How FortiAnalyzer manages info associated with Security Events?
Ans:
We can place time back in by putting in a FortiAnalyzer platform into the prevailing security infrastructure, making one read of the safety events, archived content, and vulnerability assessments. FortiAnalyzer platforms pull the complete variety of information from Fortinet solutions, together with traffic, event, virus, attack, content filtering, and email filtering. It removes the manual search of multiple log files once activity rhetorical analysis and network auditing. FortiAnalyzer platform’s centralized knowledge archiving, file quarantine, and vulnerability assessment scale back the time taken to manage the vary.
5.What issue depends on choosing between hardware and virtual appliances?
Ans:
Most organizations use the desired hardware IT infrastructure or virtual IT infrastructure nowadays, for several budget constraints. This creates a requirement for each hardware and virtual appliances inside a security strategy. FortiAnalyzer will be put in either hardware or virtual appliance to suit the surroundings, which incorporates a mixture of virtual and physical IT infrastructure. FortiAnalyzer has the ability to log events from FortiOS-based hardware appliances, virtual appliances, or a mix of each.
6.What square measures the advantages of Network Event Correlation benefits?
Ans:
The component called event correlation plays a key role in integrated management. Network Event Correlation permits the computer user to quickly establish and react to network security threats across the organization network.
7.What do the graphical outline reports show?
Ans:
Graphical outline reports offer elaborate events, activities, and trends occurring on FortiGate and third-party devices on the complete network.
8.How can we have the benefit of FortiAnalyzer’s performance to upmarket capacity?
Ans:
FortiAnalyzer family models support thousands of FortiGate and FortiClient agents, and may dynamically scale storage supported retention and compliance necessities.
9.What square measures the advantages of FortiAnalyzer Centralized work of Multiple Record Types?
Ans:
This record together with traffic activity, system events, viruses, attacks, internet filtering events, and electronic messaging activities and knowledge. System directors will scrutinize the complete network from one single location.
10.What square measures the advantages of FortiAnalyzer Seamless Integration with the Fortinet Products?
Ans:
The shut integration with Fortinet merchandise maximizes its performance and permits FortiAnalyzer resources for economical management from FortiGate or different FortiManager user interfaces.
11.What advantages if FortiAnalyzer is chosen as Standalone, Collector, or Analyzer mode?
Ans:
FortiAnalyzer will be put in as a personal unit, or optimized for specific operations. It depends on the situation and utility that’s needed. Any company doesn’t need all the options and advantages of FortiAnalyzer.
12.How can we have the benefit of FortiAnalyzer’s Versatile Management Solutions?
Ans:
Key parts of FortiAnalyzer’s management skillfulness are:
- Diversity of kind factors.
- Architectural flexibility.
- Highly customizable.
- Simple licensing.
13.How will FortiAnalyzer dissent from ancient methods?
Ans:
Threats square measure perpetually evolving inside networks, like structure growth or new regulations and business necessities. ancient strategies concentrate on recording and characteristic network threats through work, analysis, and coverage over time. FortiAnalyzer offers enterprise-class options to not solely establish these threats however conjointly provide flexibility to evolve beside the dynamical network. FortiAnalyzer will generate extremely tailor-made reports for structure necessities whereas aggregating logs in an exceedingly class-conscious, layer work topology.
14.What does one perceive by Content work & knowledge Mining?
Ans:
Log aggregation and archiving square measure are essential these days in characteristic security threats and managing network usage. In addition to in-depth analysis, time period work, and coverage, FortiAnalyzer facilitates elaborate content work of user activities and network traffic. Activities will be scrutinized in time period, archived, and later analyzed as per the necessity. Activities will be half-tracked user-wise, protocol, source, destination, etc., and also the actual content changed in an exceedingly session is accessible. Content work isn’t solely essential so as to implement regulatory mandates like HIPAA and SOX compliance however completely required to enforce acceptable use policies and shield necessary company assets and holding.
15.What is a Vulnerability Scanner?
Ans:
FortiAnalyzer’s integrated vulnerability scanner identifies vulnerabilities on a number server, like a mail server, FTP server, or the other operating system or Windows host, and produces vulnerability reports consequently showing the potential weaknesses to attacks that will exist for a specific device.
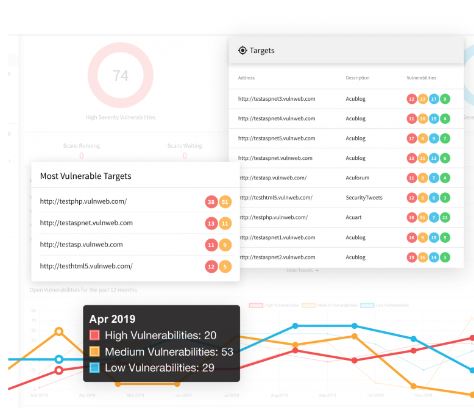
16.What Granular info can we get with the assistance of FortiAnalyzer?
Ans:
The FortiAnalyzer programme (UI) facilitates the system directors to dig deep into security log knowledge to supply the granular level of reportage necessary to know what’s happening on the whole network. Historical or period of time knowledge permits network directors to investigate log and content info, yet because of the traffic of the whole network.
17.What is Log Browser?
Ans:
Log Browser facilitates America to look at log files or messages from the registered devices. We are able to simply filter the log files and messages to dig down and find specific info.
18.What square measures the FortiAnalyzer’s Supporting Devices?
Ans:
- FortiGate Multi-Threat Security Systems.
- FortiMail Email Security Systems.
- FortiClient Mobile End-Point Security.
- FortiClient computer End-Point Security.
19.How will we have a tendency to edit FortiAnalyzer’s science Address?
Ans:
To edit the FortiAnalyzer VM science address we’d like to perform the subsequent steps:
- In the toolbar choose plus > Manage/View product, that opens the read product page.
- Select the FortiAnalyzer VM serial range and also the Product Details page opens.
- Select Edit to alter the outline, partner info, and science address of the particular FortiAnalyzer VM.
20.What does one mean by Thick Provision Lazy Zeroed?
Ans:
Thick provision lazy zeroed is the method of allocating area among the storage for a virtual machine (VM) disk that makes a virtual disk during a default thick format. The thick provision means that all the area selected for the virtual disk files is reserved for the Virtual Machine.
21.What is Thick Provisioning Eager Zeroed?
Ans:
Thick provisioning eager zeroed could be a VMware provisioning method that generates a virtual machine (VM) disk during a default thick format. Thick provision eager zeroed supports agglomeration options like VMware Fault Tolerance, an element of VMware vSphere that’s to supply high convenience (HA) for enterprise computer code applications.
22.What is Skinny Provisioning?
Ans:
Thin provisioning (TP) could be a method of increasing the potency with that the accessible area is employed in enclosure networks (SAN). skinny Provisioning functions by allocating disk cupboard space during a versatile manner among multiple users, supported the minimum area needed by every user at any given time.
23.What is ancient storage provisioning?
Ans:
Storage provisioning is the method of distribution storage, sometimes within the variety of server hard drive areas, so as to optimize the performance of an enclosure network (SAN). Historically, this has been done by the SAN administrator, and it is a tedious method.
24.What is fetching?
Ans:
We can fetch offline reports that square measure compressed logs from one FortiAnalyzer unit to a second FortiAnalyzer unit wherever the logs are mechanically indexed within the information to support knowledge analysis on the Log read, FortiView, and Reports tabs. The fetch feature in FortiAnalyzer permits system directors to investigate knowledge from compressed logs while not poignant the performance of the first FortiAnalyzer unit as a result of the method of attractive logs happening within the background.
25.How many Panes will FortiAnalyzer have and what square measures its functions?
Ans:
- Banner is on the highest of the page; which has the house button (Fortinet logo), tile menu, ADOM menu (when enabled), admin menu, notifications, and facilitate button.
- The tree menu is on the left aspect, which has the menus for the chosen pane. Not accessible in Device Managers.
- The Content pane consists of widgets, lists, configuration choices, or alternative info, reckoning on the pane, menu, or choices that are elite. Most management tasks are handled within the content pane.
- The toolbar is directly higher than the content pane; which has choices for managing content within the content pane, like produce New and Delete.
26.How will we have a tendency to add a static route?
Ans:
Adding a static route in FortiAnalyzer is straightforward by the subsequent steps:
- We need to travel to System Settings > Network.
- After that, we should always click the Routing Table button to feature an associate IPv4 static route or the IPv6 Routing Table button to feature an associate IPv6 static route.
- Then we should always click the produce New button. The product New Network Route pane is displayed.
- Lastly, we are able to assemble the settings, and click on alright to produce the new static route.
27.How will we modify body access?
Ans:
- To change body access we should always 1st head to System Settings > Network.
- By default, port1 settings are going to be displayed. we are able to assemble body access for a special interface.
- We should Click All Interfaces, and choose the interface from the list.
- We should set the sciencev4 IP Address/Netmask or the IPv6 Address.
- After that, we should always choose one or a lot of Body Access varieties for the interface, and set the default entrance and name System (DNS) servers followed by clicking on Apply.
28.How to assemble RAID?
Ans:
- To assemble the RAID level we should always head to System Settings > RAID Management.
- Then we should always click on modification beside RAID Level, that displays the RAID Settings window.
- We should choose a brand new raid level from the RAID Level list, and click on OK.
- The FortiAnalyzer unit can restart itself.
- The period to come up with the RAID array considerably depends on the chosen RAID level.
29.How will we have a tendency to replace exhausting Disks?
Ans:
Whenever a tough disk on a FortiAnalyzer unit fails, it’s to be replaced. FortiAnalyzer devices that support hardware RAID, the fixed disk is replaced whereas the FortiAnalyzer unit remains running, called hot-swapping. On FortiAnalyzer units with computer code RAID, the device ought to be close up before exchanging the fixed disk.
30.What is the distinction between a thick and eager zeroed thick virtual disk?
Ans:
Most folks are conversant in the distinction between a thin-provisioned virtual disk and a thick-provisioned virtual disk. A thick disk’s blocks are allotted in Virtual Machine once the disk is formed whereas a skinny disk’s blocks aren’t. The distinction in performance between a thick disk associated with an Eager Zeroed thick disk is extremely little, however some applications still need eager zeroed thick provisioned disks.
31.What does one fathom Fortinet’s FortiGate?
Ans:
It includes options like intrusion hindrance system (IPS), net filtering, secure sockets layer (SSL) scrutiny, and automatic threat protection. FortiGate is additionally equipped with computer science (AI), that helps in proactive threat detection.
32.What is Fortinet’s history?
Ans:
Fortinet was supported within the year 2000 by Ken Xie and archangel Xie (siblings). they need discharged their initial product, FortiGate, within the year 2002. Between the years 2000 and 2003, the corporate has raised $13 million in camera funding and $30 million in funding. Over the last decade, the corporation has non inheritable several security-related package vendors. Fortinet recently discharged associate AI-powered product, known as FortiAI in February 2020.
33.What does one fathom Fortinet as an associate organization?
Ans:
Fortinet is an associate yankee MNC having over 7000 workers with its headquarters at Sunnyvale, California. Fortinet provides security-driven networking solutions like firewalls, anti-spam, end security, spyware, anti-virus, etc. Fortinet additionally declared a technical certification program known as Network Security knowledgeable (NSE) to alter additional developers on cybersecurity.
34.What is the ancient Firewall?
Ans:
It either uses a homeless or stateful technique to attain this.
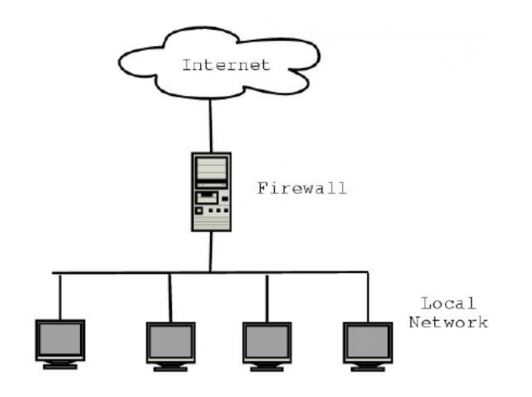
35.What is the Next-Generation Firewall?
Ans:
The Next-Generation Firewall (NGFW) acts as a deep-packet scrutiny firewall. It includes all the functionalities of a standard firewall. To boot, it provides application awareness, Integrated Intrusion Protection System (IPS), Secure Sockets Layer (SSL) scrutiny, and Shell (SSH) management.
36.Explain the variations between a Next-Generation Firewall and a standard Firewall?
Ans:
Following are the most variations between the standard firewall and Next-Generation firewall:
- The NGFW will realize the identity of a user, whereas the standard firewall can’t.
- A traditional firewall will solely track the traffic supported by two to four layers.
- A traditional firewall solely appears at the header, footer, source, and destination of the incoming packets. The NGFW will investigate the info of the incoming packet.
37.What is UTM?
Ans:
It provides a spread of security measures in a very single platform that may be employed by IT groups to deal with security challenges. It includes functionalities like anti-virus, content filtering, unapproved web site access, spyware, etc.
38.Explain concerning integrated threat management?
Ans:
Integrated threat management is an associate approach wont to face malware like alloyed threats, spam, etc. It protects from intrusion at each entryway and end levels. It permits simplified administration by protecting from all threats for each element in a very heterogeneous and integrated setting.
39.What is Security Fabric?
Ans:
It provides seamless protection through increasing attack surface, the richness of endpoints across multiple environments, etc. It will increase the speed of operation by linking completely different tools through one console and eliminates security gaps.
40.Name the various coding mechanisms offered in Fortigate Firewall?
Ans:
FortiGate uses AES and DES symmetric-key algorithms for encrypting and decrypting knowledge. a number of the algorithms supported by FortiGate are:
- des-md5
- des-sha1
- des-sha256
- des-sha384
- des-sha512
- aes128-md5
- aes128-sha1
41.What does one mean by ‘Aware’ in Fortinet Security fabric?
Ans:
Security material provides situational awareness to management and permits continuous improvement. it’ll establish awareness throughout the network, which suggests understanding threats. It focuses on understanding the flow info} or information across the network. It controls that packet gets to wherever and to whom.
42.Explain concerning ‘Actionable’ in Fortinet Security material?
Ans:
It’s a typical set of threat intelligence and centralized orchestration. Therefore it correlates world threat intelligence with native network knowledge and delivers unjust threat intelligence to each security device in your network.
43.Explain the ‘Scalable’ feature in Fortinet Fabric?
Ans:
Security ought to be provided end-to-end at a deep scrutiny level. Security Fabric’s package not solely scales at intervals the setting, however it additionally scales seamlessly trailing knowledge from IoT and endpoints. It protects the packet knowledge across distributed networks from IoT to the Cloud.
44. What’s the FortiGate firewall?
Ans:

45.What are open genus Apis in Fortinet Security Fabric?
Ans:
An organization might need multiple security devices that serve completely different functions. Security material provides open genus Apis that need to be wont to embody these devices from technology to associate integrated Fortinet security answers.
46.How is Fortinet’s Fabric-Ready Partner program completely different from the opposite partner programs?
Ans:
Fortinet Fabric-Ready partner program expands openness by providing integration through open genus Apis and a spread of scripts exploitation DevOps tools. material connectors permit integration with Amazon net Services (AWS), Microsoft Azure, Google Cloud Platform, VMWare NSX, etc. It permits automation of workflows, security policies, and application deployments.
47.What is a Fortinet Firewall?
Ans:
Fortinet firewalls are nothing , however purpose-made with security processors primarily wont to alter the industry’s best threat protection and performance for SSL-encrypted traffic in a corporation. This Fortinet Firewall primarily offers the subsequent usages like granular visibility of applications, user knowledge protection, and secured IoT devices. These sorts of appliance firewalls are designed to trace any reasonably to trace the problems.
48.What is SPU FortiGate?
Ans:
Most FortiGate models contain Security process Unit (SPU) Content Processors (CPs) that accelerate several common resource intensive security connected processes. Hertz works on the system level with tasks being offloaded to them as determined by the most central processing unit. … Newer FortiGate units embrace CP9 processors.
49.What area unit the points that ought to be thought-about whereas mounting a Fortinet firewall (Hardware) within the rack?
Ans:
Below area unit small print that justify a way to perform molding Fortinet firewalls:
- First set the area temperature -> this could be up to the vary of close temperature that is given by the first instrumentality manufacturer system management(OEM).
- Using a mechanism like reliable power attachment.
- Firewalls Adequate system flowing used for safe operations.
- Firewalls Adequate system precautions used for overcurrent management and provide wiring.
50.Why can we deploy a FortiMail unit in clear mode?
Ans:
If the FortiMail unit is working in clear mode, then the administrator doesn’t have to track DNS records for protected domain names.
51.What is the aim of a dataset question in FortiAnalyzer?
Ans:
FortiAnalyzer datasets area unit collections of log messages from monitored devices. Charts in FortiAnalyzer area unit generated supported the datasets. to form a chart, you’ll use the predefined datasets, otherwise you will produce your own custom datasets by querying the log messages within the SQL info on the FortiAnalyzer unit.
52.What profiles are often wont to shield against denial of service attacks?
Ans:
FGCP stands for FortiGate agglomeration Protocol. This can be one amongst the proprietaries and common high handiness solutions offered by Fortinet firewall. FortiGate High handiness answer chiefly contains 2 firewalls, that area unit used for configuring the high handiness operation.
53.What is the FGCP cluster?
Ans:
FGCP stands for FortiGate agglomeration Protocol. This can be one amongst the proprietaries and common high handiness solutions offered by Fortinet firewall. FortiGate High handiness answer chiefly contains 2 firewalls, that area unit used for configuring the high handiness operation.
54.What area unit the assorted steps that ought to be taken by any user before playing up-gradation of the compter code of the Fortinet security Firewall?
Ans:
The steps area unit as follows:
- Back up -> store the previous configuration.
- Back up the copy -> then the previous.
- Fortinet computer code is often dead. This can be one amongst the worst-case situations.
- Now the user has to browse the NOTE command that is free by the manufacturer. This could incorporate firewall mechanisms helpful data associated with debugging fixation, and take a look at the performance, etc.
- Finally upgrade the system.
55.What happens if the disk work is disabled within the FortiGate unit?
Ans:
If the disc work is disabled, then the logs are a unit written to nonvolatile storage. Constant rewrites to flash drives can scale back the life and potency of the memory.
56.How to perform disable activities concerning body access management from the internet?
Ans:
will disable the executive activity access from the skin world through user interface (user interface) AND user interface through CLI:
- Config system interface.
- Edit.
- Unset permit access.
- End.
57.Write the vital user interface command to disable or deactivate car USB installation?
Ans:
The following is that the vital user interface code piece to disable or deactivate USB installation:
- Config system auto-install.
- Set auto-install-config disable.
- Set auto-install-image-disable.
- End.
58.What is Ipsengine in FortiGate?
Ans:
The Fortigate IPS engine is the software system that applies IPS and application management scanning techniques to content passing through FortiOS. IPS engine updates embrace detection and performance enhancements and bug fixes.
59.How Fortinet provides support just in case of any problem or issue sweet-faced by any network administrator?
Ans:
Below square measure the vital choices out there to resolve any issue:
- Knowledge base system.
- Fortinet document library management.
- Training and Certification provided by communities.
- Fortinet Video library usage.
- Discussion forums maintenance.
- Technical Contact support convenience.
60.An e-mail message, received by the Fortigate unit is subject to the bounce verification, Anti Spam check, underneath tat circumstances?
Ans:
The cover MAIL FROM field contains a null reverse-path once a bounce verification secret is created and activated.
61.What is NP6Lite?
Ans:
NP6 supports offloading of most IPv4 and IPv6 traffic, IPsec VPN cryptography, CAPWAP traffic, and multicast traffic. The NP6Lite could be a part of the Fortinet SOC3 and is analogous to the NP6 however with a lower output and a few useful limitations (for example, the NP6Lite doesn’t offload CAPWAP traffic).
62.Which SMTP sessions square measure outlined As Incoming?
Ans:
SMTP sessions for the protected domain.
63.What are body domains?
Ans:
Administrative domains (ADOMs) alter the admin administrator to constrain the access privileges of different FortiAnalyzer unit directors to a set of devices within the device list. For Fortinet devices with virtual domains (VDOMs), ADOMs will prohibit access to solely information from a selected VDOM for a tool. enabling ADOMs alters the out their functions within the interface and interface. Access to the functions depends on whether or not you’re logged in because of the admin administrator. If you’re logged in because of the admin administrator, you’ll be able to access all ADOMs. If you’re not logged in because the admin administrator, the settings in your administrator account determines access to ADOMs.
64.How to add devices to victimize the wizard?
Ans:
To add devices victimization the wizard:
If victimization ADOMs, make sure that you’re within the correct ADOM. Go to Device Manager and click on Add Device. Configure the subsequent settings:
- IP Address : kind the information science address for the device.
- SN : kind the serial range for the device.
- Device Name: blood type name for the device.
- Device Model: choose the model of the device.
- Firmware Version: choose the code version of the device.
- Description :Type an outline of the device (optional).
- Click Next. The device is sent to the ADOM and, if productive, is prepared to start causation logs to the FortiAnalyzer unit.
- Click end to complete adding the device and shut the wizard.
65.How to Displaying historical average log rates?
Ans:
To show historical average logs rates:
- If victimization ADOMs, make sure that you’re within the correct ADOM.
- Go to Device Manager and click on the Devices Total tab within the fast standing bar.
- In the Average Log Rate (Logs/Sec) column, click the amount to show the graph.
- Hover the pointer over the graph to show additional details.
66.What is material View?
Ans:
The Fabric read module permits you to form material connectors and look at the list of endpoints. The material read tab is offered in version vi.0 ADOMs and later.
67.What are material Connectors?
Ans:
You can use FortiAnalyzer to form the subsequent sorts of material connectors:
- l ITSM.
- l Storage on page thirty three.
68.What is IDS in FortiGate?
Ans:
An intrusion detection system (IDS) is an associate degree application that monitors network traffic and searches for well-known threats and suspicious or malicious activity. The IDS sends alerts to that and security groups once it detects any security risks and threats.
69.WAN optimization is organized in active or passive mode, once can the remote peer settle for a trial to initiate a tunnel?
Ans:
The try is going to be accepted once there’s an identical WAN optimisation passive rule.
70.How will FortiMail Administrator Retrieve Email Account data from associate degree LDAP server rather than configuring his information manually on the unit?
Ans:
The assembly of the LDAP profile sections “User question options” and “Authentication” then associates the profile to the domain that is regionally organized.
71.When employing a sender name on a FortiMail unit, that action is taken against a supply information science address generating spam or invalid E-mail messages?
Ans:
- FortiMail Delays the e-mail messages from that supply information science address with a brief failure.
- FortiMail Rejects the e-mail messages from that supply information science address with a permanent failure.
- FortiMail Quarantines all the e-mail messages from that supply information science address.
72.What will the safety feature of Fortinet Security material profit us?
Ans:
global and native risk intelligence and alteration data is shared across individual products to decrease time to shield. Not solely will security have to be compelled to embrace powerful security tools for the varied places and functions within the network, however true visibility associate degreed management would like these distinct parts to figure along as an integrated security system.
73.What will we mean by unjust in Fortinet Security Fabric?
Ans:
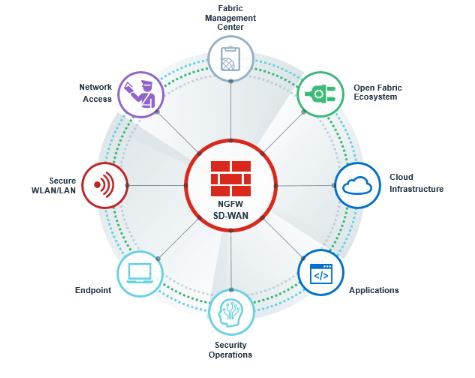
74.What will we perceive by the Open arthropod genus in Fortinet Security Fabric?
Ans:
Well-defined, open arthropod genus enables leading technology partners to become a part of the material. Of course, real security material lets North American nations maximize our existing investment in security technologies. That’s why Fortinet has developed a series of well-defined, open arthropod genus that enable technology partners to become a section of the Fortinet Security material. Combined, the Fortinet Security material is in a position to quickly adapt to the evolving spec in addition to the dynamic threat landscape.
75.Why is the plan of a security material thus vital to network security during this current environment?
Ans:
In this artistic movement era, corporations got to alter a growing list of problems that place unimaginable strain on their security capabilities, as well as the web of Things, virtualization.
76.What distinguishes Fortinet’s security cloth approach from alternative vendors’ associate attempt|tries} at an intgrated platform?
Ans:
Fortinet distinguishes itself from alternative vendors by design integrated starting with a unified software system, extremely optimized hardware and computer code process with unmatched zero-day discovery, and a detection approach that mixes activity detection, machine learning, and hardware virtualization.
77.How will Fortinet’s Security cloth profit Fortinet’s international partner network of distributors and answer providers?
Ans:
Because of its important and sophisticated character, security continues to be one in all the most important opportunities for the channel. Partners which will arrange, design, deploy Associate in Nursing optimize an integrated security system area unit finding a growing demand for his or her skills. By combining the standard security devices Associate in Nursing rising technologies along into an integrated security cloth, associates will facilitate their customers collect and answer intelligence that’s a lot of unjust, synchronize risk responses, and modify the creation, distribution, and orchestration of their security management and more investigation.
78.How is Fortinet’s Fabric-Ready Partner program totally different from the partner programs we tend to see alternative vendors promoting?
Ans:
Like several alternative partner programs, Fortinet’s Fabric-Ready Partner Program brings along best-in-class technology alliance partners. In contrast to alternative approaches, Fortinet’s approach truly permits the partners to deliver pre-integrated, end-to-end security offerings prepared for preparation in any organization.
79.An e-mail message, received by the FortiMail unit is subject to the bounce verification, Anti Spam check, below that circumstances?
Ans:
The envelope MAIL FROM field contains a null reverse-path once a Bounce Verification secret is created and activated.
80.Network Administrator of a FortiMail Unit in operation in server mode has been given the need to tack together disk qutas for all the users of a particular domain. however will the administrator bring home the bacon to this requirement?
Ans:
The network administrator must outline a disk quota price in an exceedingly resource profile.
81.Which operational mode permits the FortiMail unit to control as a full-featured email server instead of simply a mail relay agent?
Ans:
82.What is the one reason for deploying a FortiMail unit in clear mode?
if the network administrator deploys the FortiMail unit in clear mode then DNS records don’t essentially need to be changed.
Ans:
83.Which SMTP Sessions is outlined as incoming?
Ans:
84.Which back-end servers may be wont to offer recipient verification?
Ans:
LDAP servers, and SMTP servers.
85.A supervisor is bothered By the number Of space being employed To Store Quarantine Email Messages For Non-existen Accounts. that Techniques may be Used On A FortiMail Unit to Stop Email Messages From Being Unintegrated For Non-existent unts?
Ans:
Recipient Address Verification ought to be adopted to stop Email messages from being unintegrated for non-existent accounts.
86.In The native Storage Structure Of The Fortimail Unit, What Will The Non-volatile Storage Contain?
Ans:
The non-volatile storage Contain computer code Image in conjunction with System Configuration and Certificates.
87.What Is the tactic will The Fortigate Unit Use to see the provision Of an online Cache victimization net Cache ommunication Protocol (wccp)?
Ans:
The web cache sends an Associate in Nursing “I see you” message that is captured by the FortiGate unit.
88.What Is One Reason For Deploying A Fortimail Unit In Clear Mode?
Ans:
DNS records don’t essentially need to be changed. Configure the LDAP profile sections “User question options” and “Authentication” then associate the profile to the domain that’s regionally designed.
89.Which Operation Is Performed By the Cast Scientific Discipline Scanning Technique?
Ans:
DNS PTR record operation on the sender’s scientific discipline address then A record operation on the canonical hostname.
90.Which Operational Modes Support High Availability?
Ans:
- Transparent Mode.
- Gateway Mode.
- Server Mode.
91.Which History Log Field Indicates The Action Taken By The Fortimail Unit relating to a particular Email?
Ans:
Disposition.
92.Which High handiness Mode ought to Associate in Nursing Administrator prefer to offer enhanced process Capabilities?
Ans:
Config-Only.
93.Which Operational Mode permits The Fortimail Unit to control As A Full Featured Mail Server instead of simply A Mail Relay Agent?
Ans:
Server Mode.
Are you looking training with Right Jobs?
Contact Us- Hadoop Interview Questions and Answers
- Apache Spark Tutorial
- Hadoop Mapreduce tutorial
- Apache Storm Tutorial
- Apache Spark & Scala Tutorial
Related Articles
Popular Courses
- Hadoop Developer Training
11025 Learners - Apache Spark With Scala Training
12022 Learners - Apache Storm Training
11141 Learners
- What is Dimension Reduction? | Know the techniques
- Difference between Data Lake vs Data Warehouse: A Complete Guide For Beginners with Best Practices
- What is Dimension Reduction? | Know the techniques
- What does the Yield keyword do and How to use Yield in python ? [ OverView ]
- Agile Sprint Planning | Everything You Need to Know
