
Must-Know [LATEST] SonicWall Interview Questions and Answers
Last updated on 26th Sep 2022, Blog, Interview Question
1.What Is A Dingle Sonicwall?
Ans:
Dell SonicWall may be a firewall resolution that not solely detects security breaches however prevents them with SonicWall next-generation firewalls that are recently awarded for its network security solutions. dingle SonicWall blocks ransomware, encrypted threats, and phishing attacks, not solely on wired but additionally on wireless and mobile networks.
2.Why will we want A Firewall?
Ans:
Internet association makes North American nations exposed to hackers UN agencies access our money and private data. Firewall works as a barrier between our network and also the net. Once we are connected to the net and are perpetually causating and receiving data and may be simply hacked. SonicWALL is our 1st line of defense against security threats and management information over the net.
3.What Is A Sonicwall Vpn?
Ans:
SonicWALL VPN specifies whether or not the VPN association is being employed to supply remote access or to attach 2 SonicWALL devices (Office Gateway). It additionally specifies the SonicWALL’s information science address or name & provides an association name and to click Next.
4.Describe Sonicwall Tz one hundred And Its Function?
Ans:
The SonicWALL TZ one hundred is associate economical business workhorse. This is often a router that boasts of widespread cryptography capabilities, VPN and security compatibility that provides ex gratia Unified Threat Management (UTM) subscription services. it’s appropriate remote and branch offices that have got to be firmly connected to main headquarters’ offices. The network security appliance is additionally an impressive firewall possibility for little business organizations that need network security, remote property practicality, and inexpensive reading.
5.How Sonicwall Helps Network Administrators?
Ans:
SonicWALL is understood for its Standout options. Network directors with one installation of SonicWALL acquire data on each website} to site hardware and cross-platform code based mostly VPN practicality, firewalled cases, DHCP services, comprehensive routing capabilities, VOIP support, security supports at zonal and branch offices, work and reportage practicality, perimeter protection and subscription services, load equalization capability, hardware failover capability, associate integrated network switch with ex gratia wireless property.
6.What Are The Compatibility Options Of Sonicwall?
Ans:
SonicWALL TZ one hundred is understood for its compatibility. Many VPN cryptography and validation technologies are supported, as well as DES, 3DES, AES, MD5, and SHA-1. Key exchange technologies that are supported embody the President of the United States, manual key, X.509 certificates and L2TP over IPSec. international VPN shopper platforms that are supported embody Windows 2000, XP, view and Windows seven, whereas the SSL VPN platforms that are supported embody Mac OS X and multiple Linux distributions. RIP and static routes that are supported on the TZ one hundred platform are XAUTH/RADIUS, Active Directory, SSO, LDAP and Novell information validation.
7.Can Sonicwall Be Managed Centrally?
Ans:
TZ one hundred series devices are equipped by SonicWALL’s international Management System (GMS). This distinctive feature facilitates centralized management of various SonicWALL devices, thereby lowering reading and maintenance prices for larger organizations because of its GMS’ capability and remotely manages configurations, incorporating policies and reportage as well as oversight of period of time performance.
8.What are The advanced problems with Sonicwall?
Ans:
SonicWALL router configuration and readying is extremely advanced and wishes to be extremely trained and skilled for its installation. Its technology provides unimaginable and complicated practicality for its firewall capabilities. For organizations that require help, Remote Startup and Configuration Service for the TZ Series is offered from a large variety of vendors.
9.What Is Sonicwall Mobile Connect?
Ans:
SonicWall Mobile Connect may be a free app that wants a co-occurring user license on one amongst the SonicWALL router solutions to operate properly. SonicWall secures Mobile Access in one hundred Series / SRA appliances running seven.5 or higher.
10.What Is Netextender Dell?
Ans:
NetExtender empowers dingle SonicWALL with Secured Remote Access (SRA) 4600 and 1600, adding facilities like seamless and secure access to any resource on the company network, as well as servers or custom applications. it’s not a fat shopper. NetExtender is an SSL VPN shopper for securing Windows, Mac, or Linux North American nations which might be downloaded simply and permits us to run any application firmly on the company’s network. It uses Point-to-Point Protocol (PPP).
11.How will Sonicwall Firewall Be designed Step By Step?
Ans:
We need to form associate access rule:
- Firstly we want to go browsing to the SonicWALL firewall device.
- Then we should always click the Firewall button.
- Then we should always click the Matrix or change posture boxes and read the vogue radio button.
- Followed by clicking the acceptable Zone (such as WAN to LAN).
- Lastly we want to click the Add button that seems at an all-time low of the menu.
12.How will we have a tendency to Access The Sonicwall Management Interface?
Ans:
We need to run the Setup Tool to find the SonicWALL’s information science address. Then we should always try and ping the Sonicwall LAN interface information science and also the upstream device’s information science. We will use the Sonic OS command Interface (CLI) guide higher called the console port and use acceptable commands to reset the settings.
13.How To Produce A Nat Policy?
Ans:
The Network Address Translation (NAT) engine in SonicWALL permits users to outline granular NAT policies for his or her incoming and outgoing traffic. By default, the SonicWALL security device contains a preconfigured NAT policy to permit all computers connected to the computer network to perform several to at least one NAT. It permits victimisation of the information processing address of the WAN interface, and a policy to not perform NAT once traffic across different interfaces.
14.Can we have a tendency to tack together numerous Nat Policies Concurrently?
Ans:
A NAT policy provides North American countries the ability to regulate Network Address Translation supported mixtures of supply information processing address, Destination information processing address and Destination Services. Policy-based NAT permits North American countries to activate differing types of NAT at an equivalent time.
15.How will we have a tendency to tack together Nat Policies?
Ans:
To tack together a Many-to-One NAT policy that enables all computers on the X1 interface to initiate traffic victimization the SonicWALL security appliance’s WAN information processing address,we need to perform the subsequent steps:
- Navigate to Network > NAT Policies page and click on Add. Then the Add NAT Policy window is displayed.
- For Original supply, choose the choice Any.
- For Translated supply, we’d like to pick WAN Interface information processing.
- For Original Destination, we’d like to pick Any.
- For the Translated Destinations, we’d like to pick the Original.
- For Original Service, we’d like to pick Any.
- For Translated Service, we’d like to pick Original.
- For arriving Interface, we’d like to pick X1.
- For departing Interface, we’d like to pick X1.
- In the comments, we’d like to enter a brief description.
- Followed by clicking on the altar NAT Policy checkbox.
- We need to go away and produce a reflexive policy ungoverned.
- Finally Click Add.
16.What Is The Difference Between Entryway And Firewall at Intervals A Network?
Ans:
Network gateways connect 2 networks along whereas a firewall acts as a defense to the pc against unauthorized incoming or outgoing access. Firewalls will be put in at intervals on a network as hardware devices or software package programs.
17.What Is The Difference Between Ips And Firewall?
Ans:
The main performance of a firewall is to manage traffic and ensure an outdoor network. A firewall cannot notice an associate attack within which the information is deviating from its regular pattern, whereas IPS will simply notice and reset that reference to its constitutional anomaly detection.
18.What does one Mean By A clear Firewall?
Ans:
A clear firewall is believed to be as Layer a pair of in any network. putting in a replacement firewall into a network will be an advanced method because of numerous problems for e.g. information processing address reconfiguration, constellation changes, current firewall etc. Since the firewall isn’t a routed hop, we will simply introduce a clear firewall to associate the existing network.
19.What does one Mean By Packet Filtering?
Ans:
Packet filtering is the method of permitting or blocking information processing packets supporting its supply and destination addresses, ports, or protocols. The packet filter examines the header of every knowledge packet supporting a selected set of rules. on its basis, it decides to dam it or enable crossing. Packet filtering is additionally half to safeguard an area network from unwanted access.
20.Define Stateful Inspection?
Ans:
Stateful review is additionally referred to as dynamic packet filtering that could be a firewall technology that supervises the state of active connections and analyzes this data to see that network packets are allowed through the firewall. Stateful review analyzes packets at intervals in the appliance layer.
21.What Is the general public Key Encryption?
Ans:
Public key encoding could be a methodology that’s used for encoding and decoding. During this system, a public secret’s accustomed to write messages and solely the corresponding non-public key will decipher them. For causing an associated encrypted message, the sender needs to understand the recipient’s public key too.
22.What Is Authorization?
Ans:
Authorization could be a methodology of security accustomed to confirm user or shopper privileges and access levels that are associated with network resources, together with firewalls, routers, switches and different security application options. Authorization is generally followed once authentication method and through authorization. It’s a system that checks associate attested user’s access rules and either grants or blocks the resource access.
23.What Is Stateful Failover?
Ans:
Each time a session is generated for a flow of traffic on the first node, it’s synced to the secondary node too. Once the first node fails, sessions still pass traffic through the second node while not having to restore the link.
24.What Is Vpn And Describe Ipsec Vpn?
Ans:
Virtual non-public Network (VPN) generates a secure network affiliation over any public network like the web. Information processing sec VPN means that VPN over information processing Security permits 2 or a lot of users to speak firmly by authenticating and encrypting every IP packet at intervals during a communication session.
25.What Is Web Site To Web Site And Remote Access Vpn?
Ans:
A site-to-site VPN permits offices in multiple locations to ascertain secure connections with one another over a public network like the web. Site-to-site VPN is in contrast to different remote-access VPN because it removes the necessity for every pc to run VPN shopper software package as if it’s on a far off access VPN.
26.How does one Check The Standing Of The Tunnel’s part one & 2?
Ans:
Following commands ar accustomed check the standing of tunnel phases:
If we’ve got tons of tunnels and also the output is incredibly confusing, then we will use a ‘show crypto IPsec Sturmabteilung peer twelve.12.12.12’ command.
27.What Is Ssl Vpn? however Is It totally different From Ipsec Vpn?
Ans:
SSL VPN facilitates remote access property from any web enabled location with no special shopper from the remote web site. We’d like an internet browser and its native SSL encoding.
28.What Is Gre And Why Is It Required?
Ans:
Generic Routing Encapsulation (GRE) may be a protocol that encapsulates packets so as to route different protocols over IP networks.GRE places a wrapper around a packet throughout transmission of the info. once receiving, GRE removes the wrapper and allows the initial packet for process by the receiving stack.Following square measure the benefits of GRE tunnels:
- The tunnels connect discontinuous sub-networks.
- It permits VPNs across wide space networks (WANs).
- The tunnels offer workarounds for networks with restricted hops.
29.At that Levels Firewalls Works? outline Firewall Generations And Their Roles.?
Ans:
- Firewalls typically work layer three, 4 & 7. 1st generation firewalls provide packet filtering and operate at layer three (Network Layer).
- Second generation firewalls will operate up to the Transport layer (layer 4) Associate in Nursing record all property passing through it and decides whether or not a packet is that the begin of a brand new association or a locality of an existing association, or with none a part of the association.Second generation firewalls square measure essentially used for Stateful examination.
- Third generation firewalls will operate at layer seven. The key advantage of this application layer filtering is that it will “understand” certain applications and protocols (such as File Transfer Protocol (FTP), name System (DNS), or machine-readable text Transfer Protocol (HTTP)) on its own.
30.What Is Dos Attack? However, will it’s Prevented?
Ans:
DoS (Denial of Service) attack is created by causing a flood of knowledge or requests to a target system leading to either consume or crash of the target system’s resources. The offender usually uses IP spoofing to hide his identity once launching a DoS attack.
31.What Is Associate in Nursing Object Server?
Ans:
With Associate in Nursing object server, the Client/Server application is written as a collection of human action objects. consumer objects communicate with server objects victimization Associate in Nursing Object Request Broker (ORB). The consumer invokes a technique on an overseas object. The ORB locates the Associate in Nursing instance of that object server category, invokes the requested technique and returns the results to the consumer object. Server objects should offer support for concurrency and sharing. The ORB brings it all at once.
32.What Is Mail Gateway?
Ans:
It is a system that performs a protocol translation between totally different pieces of email delivery protocols.
33.What Is Rip (routing data Protocol)?
Ans:
It is an easy protocol accustomed to exchanging data between the routers.
34.What Is Nvt (network Virtual Terminal)?
Ans:
It is a collection of rules that process a really straightforward virtual terminal interaction. The NVT is employed within the beginning of a Telnet session.
35.What Is the Supply Route?
Ans:
It is a sequence of IP addresses distinguishing the route a datagram should follow. A supply route might optionally be enclosed in the Associate in Nursing IP datagram header.
36.What Is Bgp (border entranceway Protocol)?
Ans:
It is a protocol used to advertise the set of networks that may be reached within the Associate in Nursing autonomous system. BGP allows this data to be shared with the autonomous system. This can be newer than EGP (Exterior entranceway Protocol).
37.What Is the Gateway-to-gateway Protocol?
Ans:
It is a protocol erstwhile accustomed to exchange routing data between web core routers.
38.What Is A Dealing Server?
Ans:
With a dealing server, the consumer invokes remote procedures that reside on the server with the Associate in Nursing SQL information engine. These remote procedures on the server execute a gaggle of SQL statements. One message (a request and an accompanying response) is sent and received over the network. Every one of the SQL statements executes successfully or fails.
39.What Is An Information Server?
Ans:
With an information server, the consumer passes SQL requests as messages to the information server. The results of every SQL command square measure came over the network. The server uses its own process power realize|to seek out|to search out} the request knowledge rather than passing all the records back to the consumer so obtaining it finds its own knowledge. The results are a lot of economical use of distributed process power. It’s additionally referred to as SQL engine.
40.What square measures the foremost Typical useful Units Of The Client/server Applications?
Ans:
- User interface.
- Business Logic and
- Shared knowledge.
41.What square measure Triggers And Rules?
Ans:
Triggers square measure special user outlined actions typically within the sort of hold on procedures, that square measure mechanically invoked by the server supported knowledge connected events. It will perform complicated actions and may use the complete power of procedural languages. A rule may be a special sort of trigger that’s accustomed to performing straightforward checks on knowledge.
42.What Is Meant By Transparency?
Ans:
Transparency extremely suggests that concealment of the network and its servers from the users and even the applying programmers.
43.What square measure Tp-lite And Tp-heavy Monitors?
Ans:
TP-Lite is just the combination of TP Monitor functions within the information engines. TP-Heavy square measures TP Monitors that support the Client/Server design and permit computers to initiate some terribly complicated multi server dealing from the desktop.
44.What square measures the 2 kinds of Oltp?
Ans:
TP lite, supported hold on procedures. TP heavy, supported the TP monitors.
45.What Is an Online Server?
Ans:
This new model of Client/Server consists of skinny, portable, “universal” purchasers that refer to superfat servers. within the simplest kind, an online server returns documents once purchasers raise them by name. The purchasers Associate in Nursing server communicate victimization an RPC-like protocol referred to as protocol.
46.What are Super Servers?
Ans:
These are fully-loaded machines which have multiprocessors, high-speed disk arrays for interview I/O and fault tolerant options.
47.What Is A Tp Monitor?
Ans:
There is no usually accepted definition for a TP monitor. consistent with Jeri Edwards’ a TP Monitor is “an OS for dealings processing”.
48.Tp Monitor will chiefly 2 Things extraordinarily Well. they’re method Management And dealings Management.?
Ans:
They were originally introduced to run categories of applications that might service tons of and generally thousands of shoppers. TP Monitors give Associate in Nursing OS – on top of existing OS – that connects in real time these thousands of humans with a pool of shared server processes.
49.What Is Meant By Asymmetrical Protocols?
Ans:
There is a many-to-one relationship between shoppers and servers. shoppers continually initiate the dialog by requesting a service. Servers are passively waiting for requests from shoppers.
50.What Is The Difference Between Trigger And Rule?
Ans:
The triggers are referred to as implicitly by info generated events, whereas hold on procedures are referred to as expressly by shopper applications.
51.What are referred to as Transactions?
Ans:
The classified SQL statements are referred to as Transactions (or) A dealings could be an assortment of actions embused with ACID properties.
52.What does one mean by stateful inspection?
Ans:
Stateful review is additionally referred to as a dynamic packet filter. This is often a firewall era accustomed to supervising active connections and analyzes the network statistics to spot that networking packets are going to be allowed through the firewall. This stateful review additionally analyzes the info packets at intervals in the utility layer.
53.Explain The Building Blocks Of Client/server?
Ans:
- The shopper aspect building block runs the shopper aspect of the application.
- The server aspect building block runs the server aspect of the application.
54.The Middleware Building Block Runs On Each Shopper Associate in Nursing Server Sides Of An Application. It’s Broken Into 3 Categories?
Ans:
- Transport stack.
- Network OS.
- Service-specific middleware.
55.What Is Structured Question Language (sql)?
Ans:
SQL could be a powerful set-oriented language that was developed by IBM analysis for the databases that adhere to the relative model. It consists of a brief list of powerful, nonetheless extremely versatile, commands which will be accustomed to manipulate info collected in tables. Through SQL, we are able to manipulate and manage sets of records at a time.
56.What Is a Remote Procedure Decision (rpc)?
Ans:
RPC hides the intricacies of the network by exploiting the normal procedure decision mechanism acquainted to each software engineer. A shopper method calls an operation on an overseas server and suspends itself till it gets back the results. Parameters are passed like in any standard procedure. The RPC, like a standard procedure, is synchronous. The method that problems the decision waits till it gets the results.Under the covers, the RPC run-time computer code collects values for the parameters, forms a message, and sends it to the remote server. The server receives the request, takes away the parameters, calls the procedures, and sends the reply back to the shopper. It’s a telephone-like trope.
57.What are the best parts Of Transaction-based Systems?
Ans:
Resource Manager dealings Manager and computer programme.
58.What are The 3 varieties of Sql info Server Architecture?
Ans:
Process-per-client design. (Example: Oracle vi, Informix ) Multithreaded design. (Example: Sybase, SQL server) Hybrid design.
59.What Is Message familiarized Middleware (mom)?
Ans:
MOM permits general purpose messages to be changed in an exceedingly Client/Server system exploitation message queues. Applications communicate over networks by merely swinging messages within the queues and obtaining messages from queues. It usually provides a really straightforward high level API to its services.MOM’s electronic messaging and queuing enable shoppers and servers to speak across a network while not being joined by a non-public, dedicated, logical association. The shoppers and server will run at completely different times. it’s a post-office like trope.
60.What Is Meant By Middleware?
Ans:
Middleware could be a distributed computer code required to support interaction between shoppers and servers. In short, it’s the computer code that’s within the middle of the Client/Server systems and it acts as a bridge between the shoppers and servers. It starts with the API assaulting the shopper aspect that’s accustomed to invoke a service and it covers the transmission of the request over the network and also the ensuing response.
61.What are The Functions Of the Everyday Saver Program?
Ans:
It waits for client-initiated requests. Executes several requests at a constant time. Take care of influential person shoppers 1st. Initiates and runs background task activity. Keep running. mature larger and quicker.
62.What Is Meant By Symmetric Data Processing (smp)?
Ans:
It treats all processors as equal. Any processor will do the work of the other processor. Applications are divided into threads which will run at the same time on any accessible processor. Any processor within the pool will run the OS kernel and execute user-written threads.
63.What are General Middleware?
Ans:
It includes the communication stacks, distributed directories, authentication services, network time, RPC, Queuing services beside the network OS extensions like the distributed file and print services.
64.What Is Meant By uneven data processing (amp)?
Ans:
Only 1 selected processor, the master, controls (in a tightly coupled arrangement) slave processors dedicated to specific functions.
65.What Is Oltp?
Ans:
In the dealings server, the shopper part sometimes includes GUI and also the server parts sometimes consists of SQL transactions against the info. These applications are referred to as OLTP (Online dealings Processing) OLTP Applications usually, Receive a hard and fast set of inputs from remote shoppers. Perform multiple pre-compiled SQL comments against an area info. Commit the work and come back with a hard and fast set of results.
66.What Is Meant By 3-tier Architecture?
Ans:
In 3-tier Client/Server systems, the appliance logic (or process) lives within the middle tier and it’s separated from the information and also the program. In theory, the 3-tier Client/Server systems area unit additional ascendable, strong and versatile.Example: TP monitor, Web.
67.What Is Meant By 2-tier Architecture?
Ans:
In 2-tier Client/Server systems, the appliance logic is either buried within the program on the consumer or inside the information on the server.Example: File servers and information servers with hold on procedures.
68.What Is Load Balancing?
Ans:
If the amount of incoming purchasers requests exceeds the amount of processes during a server category, the TP Monitor might dynamically begin new ones and this is often referred to as Load leveling.
69.What area unit referred to as Fat purchasers And Fat Servers?
Ans:
If the majority of the appliance runs on the consumer facet, then it’s Fat purchasers. It’s used for call support and private software package.If the majority of the appliance runs on the Server facet, then it’s Fat servers. It tries to attenuate network interchanges by making additional abstract levels of services.
70. Describe Horizontal Scaling And Vertical Scaling?
Ans:
Horizontal scaling means that adding or removing consumer workstations with solely a small performance impact. Vertical scaling means migrating to a bigger and quicker server machine or multi servers.
71.What Is a Software Server?
Ans:
Groupware addresses the management of semi-structured info like text, image, mail, bulletin boards and also the flow of labor. These Client/Server systems have folks in direct contact with others.
72.What area unit the 2 Broad categories Of Middleware?
Ans:
General middleware Service-specific middleware.
73.What Is A File Server?
Ans:
File servers are a unit helpful for sharing files across a network. With a digital computer, the consumer passes requests for file records over the network to the digital computer.
74.What Is Client/server?
Ans:
Clients and Servers are separate logical entities that job along over a network to accomplish a task. several systems with terribly completely different architectures that area units connected along are referred to as Client/Server.
75.What area unit The Services Provided By The operational System?
Ans:
Extended services:These area unit add-on standard software package elements that are bedded on high of base service.
76.What Is Acid Property?
Ans:
ACID may be a term coined by St. Andrew Reuter in 1983, that stands for Atomicity, Consistence, Isolation and sturdiness.
77.What area units hold on Procedures?
Ans:
A hold on procedure is known as an assortment of SQL statements and procedural logic that’s compiled, verified and held on during server information. it’s generally treated like several different information objects. hold on procedures settle for input parameters so one procedure is used over the network by multiple purchasers exploiting completely different input files. one remote message triggers the execution of a group of hold on SQL statements. The results may be a reduction of network traffic and higher performance.
78.What Is a Wide-mouth Frog?
Ans:
Wide-mouth frog is the simplest legendary key distribution center (KDC) authentication protocol.
79.What Is Passive Topology?
Ans:
When the computers on the network merely listen and receive the signal, they’re cited as passive as a result of they don’t amplify the signal in any means.Example for passive topology – linear bus.
80.What Is Region?
Ans:
When stratified routing is employed, the routers are divided into what we tend to decide regions, with every router knowing all the small print concerning a way to route packets to destinations inside its own region, however knowing nothing concerning the interior structure of different regions.
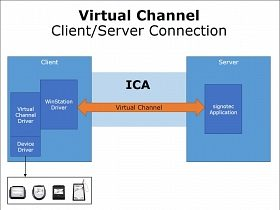
81.What Is Virtual Channel?
Ans:
Virtual channel is generally an affiliation from one supply to at least one destination, though multicast connections are permissible. The opposite name for a virtual channel is virtual circuit.
82.Difference Between The Communication And Transmission?
Ans:
Transmission may be a physical movement of data and concern problems like bit polarity, synchronization, clock etc.Communication means that that means full exchange of data between 2 communication media.
83.What Is The Difference Between Tftp And Ftp Application Layer Protocols?
Ans:
The Trivial File Transfer Protocol (TFTP) permits an area host to get files from an overseas host however it doesn’t offer dependability or security. It uses the elemental packet delivery services offered by UDP.The File Transfer Protocol (FTP) is the commonplace mechanism provided by protocol / information science for repeating a file from one host to another. It uses the services offered by protocol and is reliable and secure. It establishes 2 connections (virtual circuits) between the hosts, one for information transfer and another for management info.
84.What area unit the benefits and drawbacks Of The 3 kinds of Routing Tables?
Ans:
The 3 kinds of routing tables are unit mounted, dynamic, and glued central. The mounted table should be manually changed when there’s an amendment. A dynamic table changes its info supported network traffic, reducing the number of manual maintenance. A hard and fast central table lets a manager modify only 1 table, which is then browsed by different devices. The mounted central table reduces the requirement to update every machine’s table, like the mounted table. Typically a dynamic table causes the fewest issues for a network administrator, though the table’s contents will be amended while not the administrator being awake to the amendment.
85.What Is Beaconing?
Ans:
The process that enables a network to self-repair networks issues. The stations on the network give notice to the opposite stations on the ring once they aren’t receiving the transmissions. Beaconing is employed in Token ring and FDDI networks.
86.What will The Mount Protocol Do ?
Ans:
The Mount protocol returns a file handle and also the name of the filing system during which a requested file resides. The message is distributed to the shopper from the server once reception of a client’s request.
87.What square measure Digrams And Trigrams?
Ans:
The most common 2 letter mixtures square measure known as diagrams. e.g. th, in, er, re and an.The most common 3 letter mixtures square measure known as trigrams. e.g. the, ing, and, and ion.
88.What Is The Howdy Protocol Used For?
Ans:
The howdy protocol uses time rather than distance to work out best routing. it’s another to the Routing data Protocol.
89.What Is The Minimum And Most Length Of The Header Within The Protocol Phase And Science Datagram?
Ans:
The header ought to have a minimum length of twenty bytes and might have a most length of sixty bytes.
90.What does one Mean By “triple X” In Networks?
Ans:
The performance of PAD (Packet assembly program Disassembler) is delineated in a document referred to as X.3. The quality protocol has been outlined between the terminal and also the PAD, called X.28; another normal protocol exists between the PAD and also the network, called X.29. Together, these 3 recommendations square measure typically known as “triple X”.
91.What Is Attenuation?
Ans:
The degeneration of a symbol over distance on a network cable is termed attenuation.
92.What Is the Protocol Knowledge Unit?
Ans:
The knowledge unit within the LLC level is termed the protocol data unit (PDU). The PDU contains 4 fields: a destination service access purpose (DSAP), a supply service access purpose (SSAP), an effect field Associate in Nursing, a data field. DSAP, SSAP square measure addresses employed by the LLC to spot the protocol stacks on the receiving and causing machines that square measure generating and victimizing the information. The management field specifies whether or not the PDU frame may be a data frame (I – frame) or a superordinate frame (S – frame) or an uncounted frame (U – frame).
93.What is the distinction Between creative person And Rarp?
Ans:
The address resolution protocol (ARP) is employed to associate the thirty two bit science address with the forty eight bit physical address, employed by a bunch or a router to seek out the physical address of another host on its network by causing a creative person question packet that has the science address of the receiver. The reverse address resolution protocol (RARP) permits a bunch to find its web address once it is aware of its physical address.
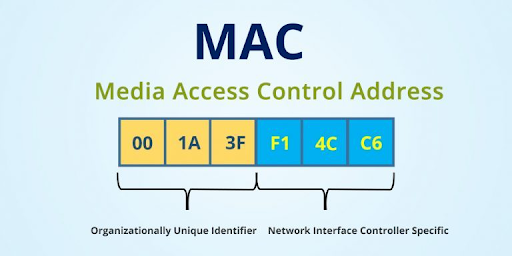
94.What is the Mackintosh Address?
Ans:
The address for a tool because it is known at the Media Access management (MAC) layer within the spec. The mackintosh address is sometimes kept in fixed storage on the network adapter card and is exclusive.
95.What Is emulation, during which Layer It Comes?
Ans:
Telnet is additionally known as emulation. It belongs to the application layer.
96.What square measures Major kinds of Networks And Explain?
Ans:
Server-based network, Peer-to-peer network.Peer-to-peer network, computers will act as each server sharing resources and as purchasers victimizing the resources.Server-based networks offer centralized management of network resources and think about server computers to supply security and network administration.
97.What Is Sap?
Ans:
Series of interface points that permit alternative computers to speak with the opposite layers of network protocol stack.
98.What Is Multicast Routing?
Ans:
Sending a message to a bunch is termed multicasting, and its routing rule is termed multicast routing.
99.What Is The Difference Between Routable And Non- Routable Protocols?
Ans:
Routable protocols will work with a router and might be wont to build massive networks. Non-Routable protocols square measure designed to figure on little, native networks and can’t be used with a router.
100.What Is Rex?
Ans:
Request to Exit (REX): A symbol that informs the controller that somebody has requested to exit from a secure space.
Are you looking training with Right Jobs?
Contact Us- Hadoop Interview Questions and Answers
- Apache Spark Tutorial
- Hadoop Mapreduce tutorial
- Apache Storm Tutorial
- Apache Spark & Scala Tutorial
Related Articles
Popular Courses
- Hadoop Developer Training
11025 Learners - Apache Spark With Scala Training
12022 Learners - Apache Storm Training
11141 Learners
- What is Dimension Reduction? | Know the techniques
- Difference between Data Lake vs Data Warehouse: A Complete Guide For Beginners with Best Practices
- What is Dimension Reduction? | Know the techniques
- What does the Yield keyword do and How to use Yield in python ? [ OverView ]
- Agile Sprint Planning | Everything You Need to Know
