
WebGoat Tutorial
Last updated on 29th Sep 2020, Blog, Tutorials
WebGoat is a deliberately insecure J2EE web application designed to teach web application security lessons. In each lesson, users must demonstrate their understanding of a security issue by exploiting a real vulnerability in the WebGoat application. For example, in one of the lessons the user must use SQL injection to steal fake credit card numbers. The application is a realistic teaching environment, providing users with hints and code to further explain the lesson.
Why the name ‘WebGoat‘?
Developers should not feel bad about not knowing security. Even the best programmers make security errors. What they need is a scapegoat, right? Just blame it on the ‘Goat!
Runtime environment for OWASP WebGoat
The following picture shows the ideal local setup for running WebGoat and following the lessons. It also shows WebWolf and how OWASP Zap can be used between the browser and OWASP WebGoat.
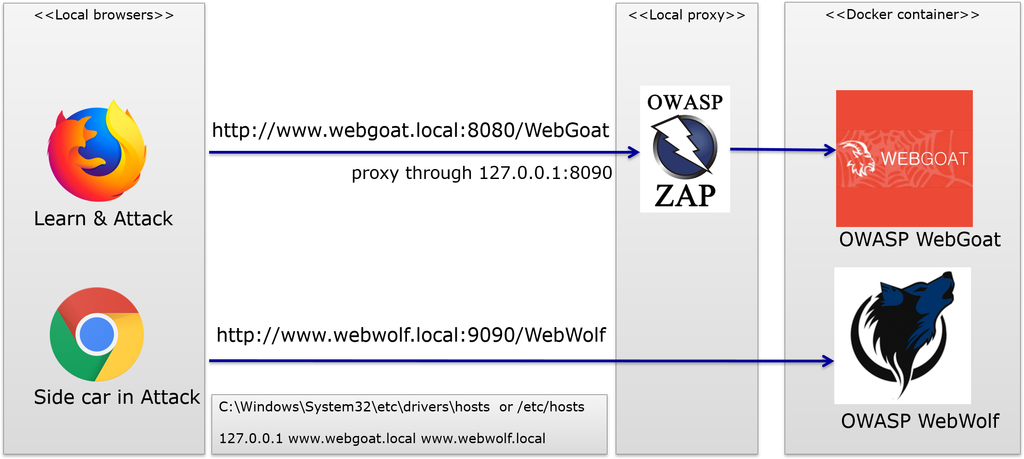
Releases
WebGoat consists of two applications that work together. One is called WebGoat and one is called WebWolf. WebWolf depends on WebGoat and requires that WebGoat is started first.
Subscribe For Free Demo
Error: Contact form not found.
Both WebGoat and WebWolf are runnable jar files. Make sure the following ports are available: 80, 8080, 9090, 9001 when running locally.
There are several options to run WebGoat (and WebWolf):
Fork/Clone the repository, checkout the develop branch, build the artifacts using Java 11 and Maven 3.6+, and run the archives.
- mvn clean install
- java -jar webgoat-server/target/webgoat-server-v8.0.0-SNAPSHOT.jar
- #then in another shell
- java -jar webwolf/target/webwolf-v8.0.0-SNAPSHOT.jar
- Download the released and build jar files and run using Java 11
- Standalone WebGoat 8.0
- Use the all-in-one docker container which contains a reverse proxy and both WebGoat and WebWolf which start in the correct order
- Docker WebGoat 8.0
- docker run -d -p 80:8888 -p 8080:8080 -p 9090:9090 -e TZ=Europe/Amsterdam webgoat/goatandwolf:latest
As you’re getting a handle on the type of testing and skills that are required to do this sort of work, it’s helpful to have a place where you can do some playing. And not only do some playing but maybe learn some things along the way. WebGoat is a pretty good project that’s maintained by The Open Web Application Security Project or OWASP.
Now WebGoat, as you can see here, it’s a deliberately insecure J2EE web application. That’s Java for an enterprise. And they’ve built this web application. So that you can do some practicing with the different types of attacks and it will walk you through how you would perform the attack and lead you along the path of doing the exploration and the testing and the playing that you need in order to build up your skills in these particular areas.
So, you can see that we’ve got some hints and we can look at parameters and cookies and look at the source code. So, they do a pretty good job of leading you through these lessons, and that’s really how it’s sort of structured.
Now, if you want to get a copy of WebGoat, you would go to the site with OWASP. And sometimes it’s a little hard to dig around through all of the links that they’ve got, in this case, we just go to downloads, and it’s going to take me to the OWASP download page. And then I’ve got to find OWASP web goat which is over here. And it leads me back there. And they said it could be a little difficult to find where it’s downloaded.
In this case, I had to scroll down through the page and find the download link there, even though there was a download on the left-hand side. The organization of the site can be challenging.
So, here’s where we are with the downloads. And what I want to do is just download, in this case, it runs on Win32 or I could get the war file, and that should run on most Operating systems that have Java. So I could run the war file on Linux for example or under Mac OX, so this is where I would go get WebGoat and WebGoat as I said is pretty good for.
Having a place to play around with a safe sandbox, where you can learn some of these techniques in more detail. Practice them, hands-on and get some experience doing that.
Practicing Web Application Attacks
It’s helpful to have a place where you can practice web application attacks. WebGoat happens to be one of them. There are several places where you can get damaged sites that you can use. So, Foundstone, for example, used to have several Microsoft based websites. And I believe they still do.
One of them was called Hacme Bank as an example. Here’s one though called Damn Vulnerable Web Application and you could download this, install it onto a web server.
And then once you log in It gives you some places where you can perform some attacks. Now, there are instructions here, and it tells you how it works and how you would go about installing it.
And there’s a video on YouTube for how you would go about installing it. So Once you’ve got it installed, you can go about doing things like these particular types of attacks like there’s a force attack as an example and command execution. The sequel injection attacks and we’ve got cross-age scripting so there lots of different things that you can do with.
The Damn Vulnerable Web Application in addition to the WebGoat that we have briefly looked at as well. So just some different sandboxes that you can use to practice and enhance your skills to test web applications. This happens to be a pretty good one. The one advantage to WebGoat over this I would say would be that WebGoat will lead you through or will provide hints.
Now, there are more info links here if you want to go read up on how these things work. But they give you an overview of The vulnerability rather than leading you through actually how to exploit it within this particular site; we’re just something WebGo will do. It will lead you through how you would exploit a particular vulnerability within that application framework.
But, here’s another application that you can use in order to practice your skills. It’s DVWA, and you can download it. It’s a pretty good framework for doing practicing attacks against web applications.
Basics of Webgoat
At this point, we’ve got WebGo downloaded, and I’ve unzipped it here, and I’m going to get it started up. So, I’m in the WebGo directory and let’s take a look at what’s here. First of all, there is a Java directory and Tomcat directory because ultimately WebGo is A Java-based application, and it runs inside a Java application server, which is Tom Cat here. I’ve got a pair batch file.
The first will start Webgoat on port 80, and the second will start Webgoat on port 8080. Now I’ve also got a shell script here. Which is going to give me the ability to start it on port 80 or port 8080. So what I want to do here is I want to run webgoat, and I’m going to start 8080 because I want to run it on port 8080. It’s a Ports that doesn’t require administrative privileges. So you can see the server startup here, and we’ve got it all running now.
Now I can go to port 8080 and what I want to do is go to /WebGoat/attack. And it’s going to ask me to log in, and you may have noticed when we stated up the server, it gave a username and password, and that’s guest, guest. So, I’m going to use that to log in.
Now, I’m actually inside of Web Goat, and I can start it up, and that’s going to bring me to the user interface. That we use to work with WebGoat. So on the left-hand side, we’ve got all of the different attack vectors we can use. We’ve got some functionality on the top here where we’ve got hints, and we can take a look at parameters and cookies. And there’s a lesson plan. We can also take a look at the Java.
For a particular page. So, right here is the Java that we’ve got. I’m going to shut FireBug off because I don’t need that thing there. And we can take a look at all of the Java that is implemented inside of this page. So, we’ve got a lot of tools that are going to give us the ability to work through a lot of these lessons and get a better handle on. How each of these work. And as I said we could get hints as we go along. And that will give us some guidance if we’re a little stuck on maybe how to proceed forward.
Now the tools that we’ve downloaded so far for example Temperdata are going to be helpful as we work through some of these things. You may also find it useful to have a proxy like Burp Suite or the Zed Attack Proxy or something like that so you can intercept requests and do some manipulation with them.
So, that’s how we get WebGoat started. That’s all of the different ways that we can interface with it, and we’ll take a look at actually working through some of the lessons coming up.
Working Through Lessons
So we’ve got WebGoat up and running, and we looked through how we would get it started up under Windows or a UNIX-like operating system. And I’ve logged in at this point; now I’m inside the WebGoat interface. And you’ll see on the left-hand side here all of the different Lessons that available within WebGoat, and you’ll get a little check mark when you complete them. So the introduction is just a set of static pages that give you some idea of how WebGoat works, and some tools that you may be able to use.
So, the very first one is just HTTP basics, and you’ll see we can take a look at hints, and it says, type in your name and press go, and I’ve got some parameters there, which I can Toggle on and off based on clicking the show Parum button up top. I can also do show Cookies, where we’ve got the session ID, and what I can do at this point is just type my name in. And press go. And I’ve completed the lesson because what the lesson was looking for here was just, let’s get familiar with the interface. So we wanted to take a look at hints and parameters and cookies.
Now I can move on to something like HTTP splitting. So the very first thing That we want to do is be able to split an HTTP response and get some different interaction with the server based on that. And you can see we get a little bit of hint here; you can use the carriage return and line feed. And if you want, we could do some more hints. And you can keep plugging through hints. You never actually get to the point where you get the actual answer in the hints, and sometimes the hints aren’t even really that useful to get you to the full final stage. But they’re a good starting point. Now we can take a look at access control flaws.
There are some labs here where we’ve got multiple stages; we’ve got Remote Admin Access, AJAX Security, Authentication Flaws like Password Strength here, for example. And this one is going to send us to another page so that we can test password strength. And then all you’ve gotta do is plug the answer in. So, I can also do some attacks against basic authentication, and this is getting us used to HTTP, so it’s going to ask for the name of the authentication header.
And again, here’s where something like Hack bar as an example would be useful because we can do some encoding with it. We’re going to get a header here. It’s going to be encoded. We need to decode it, so the hack bar is really good for that. So cross-site scripting, you can see stored cross-site scripting. We could do something here. And it looks like the login field is potentially vulnerable to some stored cross-site scripting. And that something that you need to work through and figure out how you’d exploit that vulnerability.
So you can see there is a lot of Different lessons in WebGoat and again you can do hands in, it gives you ways of looking at parameters and cookies without actually using something like tempered data or the Zed attack proxy or burps weed or something like that which would also give you the ability To look at parameters and cookies and session IDs and so on.
So again, web goat’s good for just getting some practice and seeing how all of these different vulnerabilities work on a system that is designed to have these vulnerabilities be able to be exploited.
And, it’s something where you can do it ethically without going against somebody’s server and potentially causing some disruption to a real site and cause some downtime for a real business and its users.
Installing Java
WebGoat requires installation of the Java Runtime Environment (JRE). If you already have Java installed, it is worth updating to the latest version to avoid any possible issues.
First, update the package index:
- sudo apt-get update
Then install the JRE by running this command:
- sudo apt-get install default-jre
To check the Java version after installing the package:
- java -version
Installing WebGoat
Download and install the latest version of WebGoat Server to a suitable location, such as your Downloads folder.
All releases can be found here: https://github.com/WebGoat/WebGoat/releases
The latest version (at the time of writing) is: webgoat-server-8.0.0.M23.jar
- wget
- https://github.com/WebGoat/WebGoat/releases/download/v8.0.0.M23/webgoat-server-8.0.0.M23.jar
To start the WebGoat Server:
- java -jar webgoat-server-8.0.0.M23.jar
Note: if using Java 9 or higher you might need to start WebGoat as follows (update version number as required):
- java –add-modules java.xml.bind -jar webgoat-server-8.0.0.M23.jar
You will see the following message when WebGoat has started successfully:
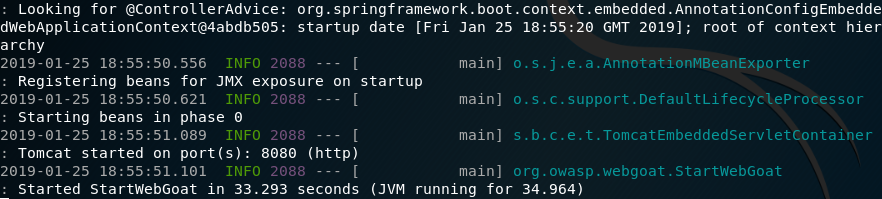
Note: if you wish to run WebGoat on an alternate port and address, you can do so with the following options:
- java -jar webgoat-server-8.0.0.M23.jar [–server.port=8080] [–server.address=localhost]
Accessing the WebGoat Interface
To access the WebGoat interface, open your browser and navigate to:
You will then be presented with the WebGoat login screen:
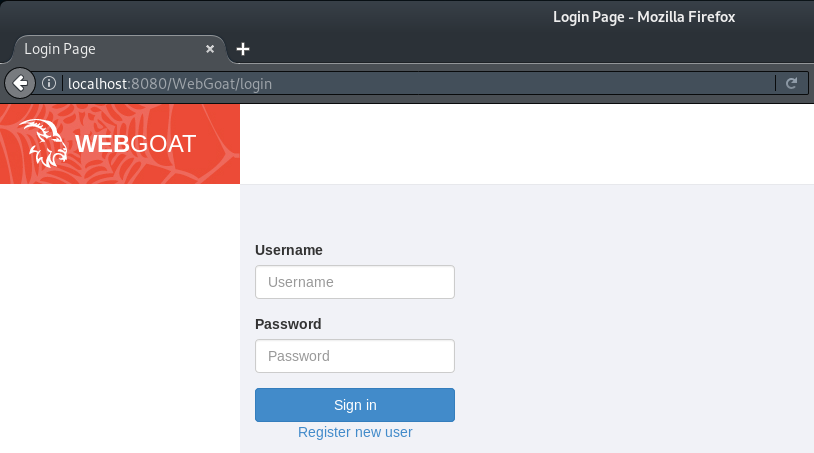
To access the lessons and challenges you will need to select ‘Register new user‘ and create a login.
Note the terms of use when creating a new user:
While running this program your machine will be extremely vulnerable to attack. You should disconnect from the Internet while using this program. WebGoat’s default configuration binds to localhost to minimize the exposure.
This program is for educational purposes only. If you attempt these techniques without authorization, you are very likely to get caught. If you are caught engaging in unauthorized hacking, most companies will fire you. Claiming that you were doing security research will not work as that is the first thing that all hackers claim.
Once you are logged in, then it’s time to get started:
Conclusion:
Learning the basic techniques necessary to secure web applications is absolutely essential for professional web developers. The OWASP project and especially the WebGoat are great resources for doing exactly that. Especially in the field of web security, learning how to hack can be greatly beneficial for anyone aspiring to improve their skills in web security.
But you don’t have to take my word for it, Michael Coates, Chief Information Security Officer at Twitter, in his great talk Applications Through an Attacker’s Lens at InfoQ, mentioned WebGoat and OWASP’s Security Shepherd as some of the best ways to learn how to hack in a safe environment.
So if you’re interested in improving your web security skills, I encourage you to start out by hacking the WebGoat! ~:)
Are you looking training with Right Jobs?
Contact Us- How to Install Git on Windows Tutorial
- GIT Interview Questions and Answers
- Git Architecture Tutorial
- what is Git Push Command?
- GitHub Interview Questions and Answers
Related Articles
Popular Courses
- Web Designing Training
11025 Learners - Angular Training
12022 Learners - JQuery Certification Training
11141 Learners
- What is Dimension Reduction? | Know the techniques
- Difference between Data Lake vs Data Warehouse: A Complete Guide For Beginners with Best Practices
- What is Dimension Reduction? | Know the techniques
- What does the Yield keyword do and How to use Yield in python ? [ OverView ]
- Agile Sprint Planning | Everything You Need to Know

