
CISSP – Asset Security Tutorial
Last updated on 12th Oct 2020, Blog, Tutorials
An asset is a resource with economic value that an individual, corporation, or country owns or controls with the expectation that it will provide a future benefit. Assets are reported on a company’s balance sheet and are bought or created to increase a firm’s value or benefit the firm’s operations. An asset can be thought of as something that, in the future, can generate cash flow, reduce expenses, or improve sales, regardless of whether it’s manufacturing equipment or a patent.
Importance of Asset Security
Recently, a hacker broke into one of the Nutri Worldwide servers taking advantage of an application vulnerability. The server had various types of information at different levels of criticality.
The information on the server was secured with appropriate security controls. Although the hacker was able to gain access only to the information with a lower level of protection, the breach had a huge impact on the organization. It was later found that there was a flaw in the classification process, leaving even sensitive information with very little protection.
Types of Assets
Current Assets
- Current assets are short-term economic resources that are expected to be converted into cash within one year. Current assets include cash and cash equivalents, accounts receivable, inventory, and various prepaid expenses.
- While cash is easy to value, accountants periodically reassess the recoverability of inventory and accounts receivable. If there is evidence that accounts receivable might be uncollectible, it’ll become impaired. Or if inventory becomes obsolete, companies may write off these assets.
Subscribe For Free Demo
Error: Contact form not found.
Fixed Assets
- Fixed assets are long-term resources, such as plants, equipment, and buildings. An adjustment for the aging of fixed assets is made based on periodic charges called depreciation, which may or may not reflect the loss of earning powers for a fixed asset.
- Generally accepted accounting principles (GAAP) allow depreciation under two broad methods. The straight-line method assumes that a fixed asset loses its value in proportion to its useful life, while the accelerated method assumes that the asset loses its value faster in its first years of use.
Financial Assets
- Financial assets represent investments in the assets and securities of other institutions. Financial assets include stocks, sovereign and corporate bonds, preferred equity, and other hybrid securities. Financial assets are valued depending on how the investment is categorized and the motive behind it.
Intangible Assets
- Intangible assets are economic resources that have no physical presence. They include patents, trademarks, copyrights, and goodwill. Accounting for intangible assets differs depending on the type of asset, and they can be either amortized or tested for impairment each year.
Asset in security
In information security, computer security and network security, an asset is any data, device, or other component of the environment that supports information-related activities.
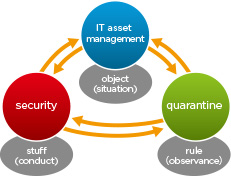
Asset categories
In order to discover all information assets, it is useful to use categories for different types of assets. The categories can be used as a checklist, to make sure one has thought of all aspects. We use ‘PEES DOT’ as a simple categorisation, both for risks and assets (see our risk assessment approach). The category descriptions are:
- People: Information accessible to one person or linked to unique role
- Equipment: Information inside or generated on/by specific devices
- Environment: Information linked to factors outside the company, e.g. city, region
- Software: Information stored by single IT systems
- Data: Structured information not linked to one software system. Includes user generated content
- Organisation: Any information about the organisation, e.g. org structure, processes
- Third parties: Information from or managed by specific suppliers, customers or partners
If you involve people from all departments, and you ask them to think about all the PEES DOT aspects, you should get a complete overview of all assets. There are probably some assets that fit into multiple categories (e.g. database for specific software). This is not a problem, just pick a category that fits well. PEES DOT is not mandatory but a useful tool for discovery.
Basic Security Principles
- Confidentiality, integrity, and availability (CIA) define the basic building blocks of any good security program when defining the goals for network, asset, information, and/or information system security and are commonly referred to collectively as the CIA triad.
Data Security
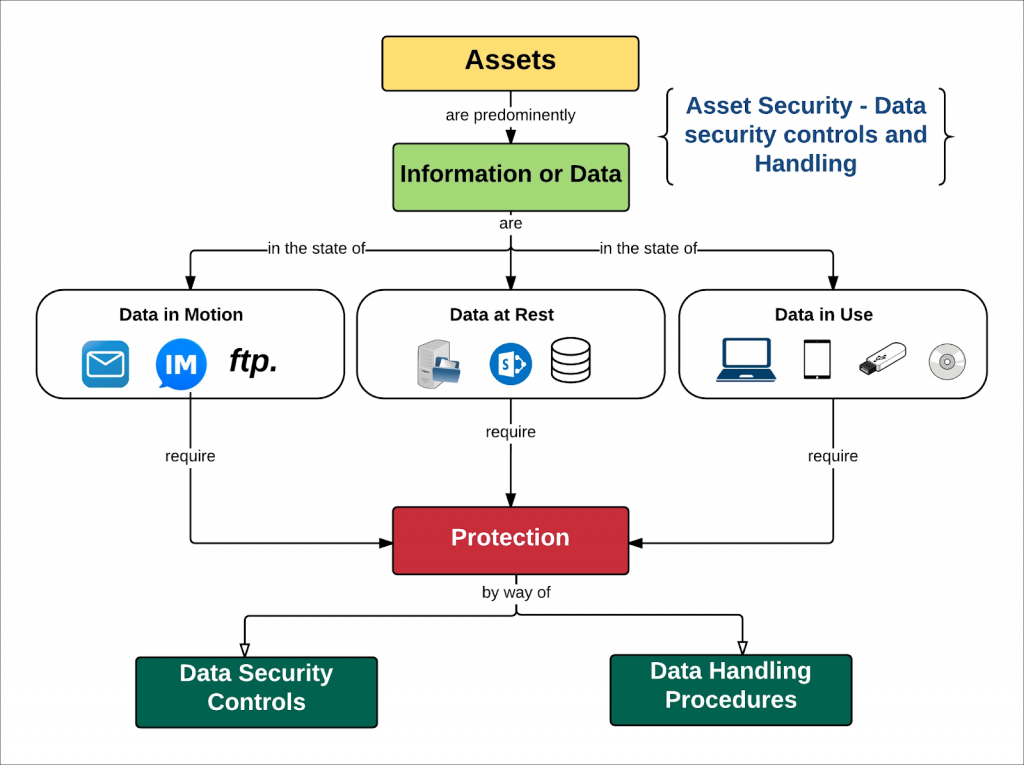
- Data security means protecting data, from harmful entities and unauthorized users. Database security involves safeguarding the confidentiality, integrity, and availability of data.
- Addressing security concerns require systems, policies, and processes to protect a database from unintended activities Security must be implemented using the Defense in Depth or layered approach. Several controls can be used such as data encryption, backups, incidence response, disaster recovery, clustering, and others.
- The security controls implemented must be regularly tested to check for effectiveness. Weaknesses or gaps identified have to be mitigated. A security practitioner can also apply risk management principles to maintain acceptable levels of risk.
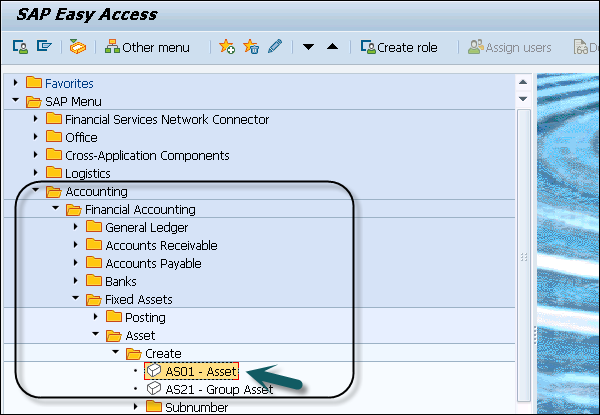
Create Asset
Step 1 − To create a new asset, navigate to Accounting → Financial Accounting → Fixed Assets → Asset → Create → Asset or use Transaction code AS01.
Step 2 − In the next window, enter Asset class and Company Code. Press ENTER key to confirm the details.
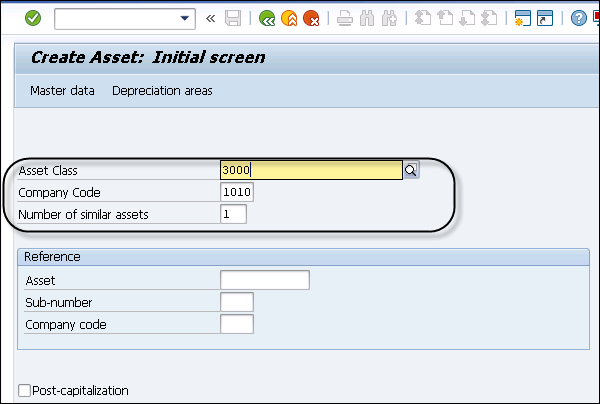
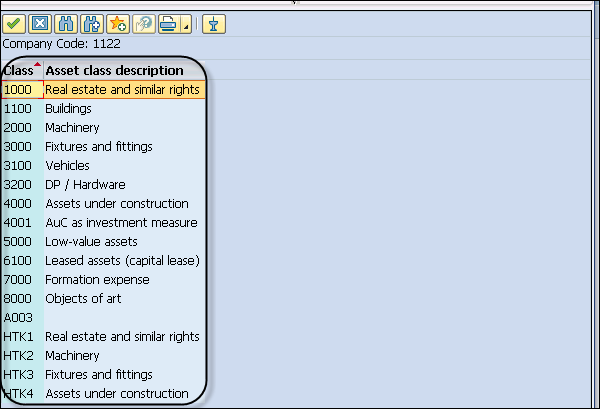
Step 3 − You can select from different Asset class types as per Company Code value.
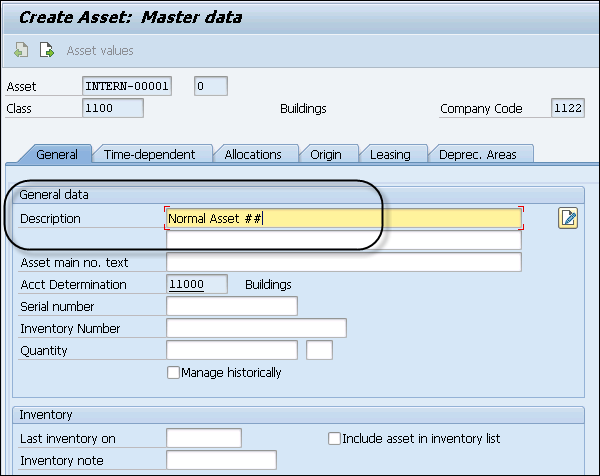
Step 4 − In the General tab, you have to enter the Description of the asset and navigate to the Time Dependent tab and enter the Cost Center details.
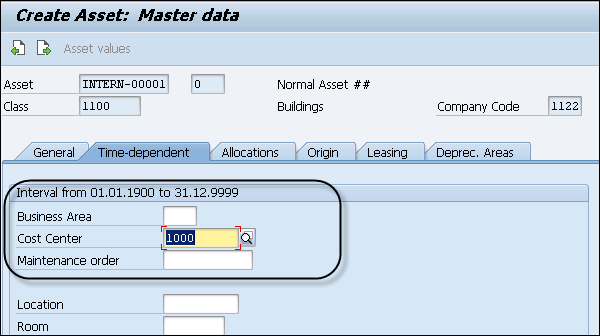
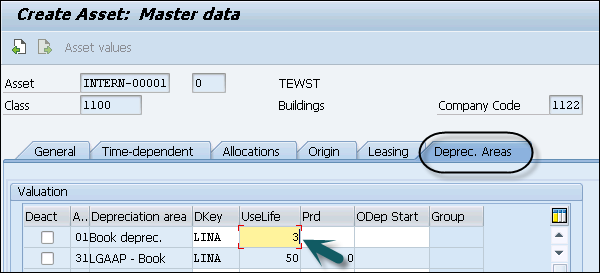
Step 5 − Next is to Navigate to Click the Deprec. Select the Areas tab and enter the value of UseLife box.
Step 6 − Click the Save button to save the entry and you will get a confirmation that asset XXXXXXX is created in the system.

Asset scrapping
- In SAP Asset Accounting, it is required to remove an asset partially or completely from an asset portfolio. This is called asset retirement or asset scrapping.
There are following types of retirement −
When you sell an asset, it results in revenue being earned. The sale is posted with a customer.
When an asset is sold, it results in revenue being earned. This is posted against the clearing account.
You scrap an asset with no revenue earned.
When an asset is sold to an affiliated company.
Step 1 − To perform a partial scrapping in Asset Accounting, navigate to Accounting → Financial Accounting → Fixed Assets → Posting → Retirement → Asset Retirement by Scrapping.
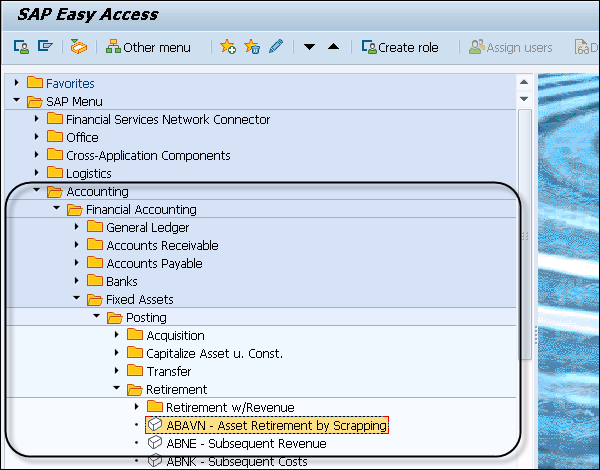
Step 2 − Enter the Company Code and click the Continue button. You can also start the transaction ABAVN – Asset Retirement by Scrapping, double-click it.
Enter GAAP in the Accounting Principle box (U1).
Enter today’s date +1 month in the Document Date box.
Enter today’s date +1 month in the Posting Date box.
Enter today’s date +1 month in the Asset Value Date box.
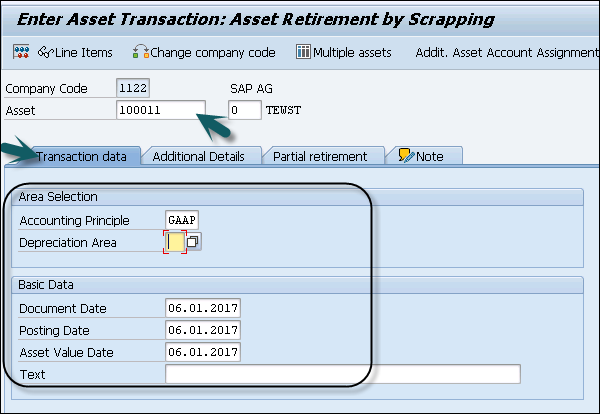
Step 3 − Click the Partial retirement tab to select it. In the next window, enter Amount Posted and From curr.-yr aquis.. checkbox and click the Simulate button.
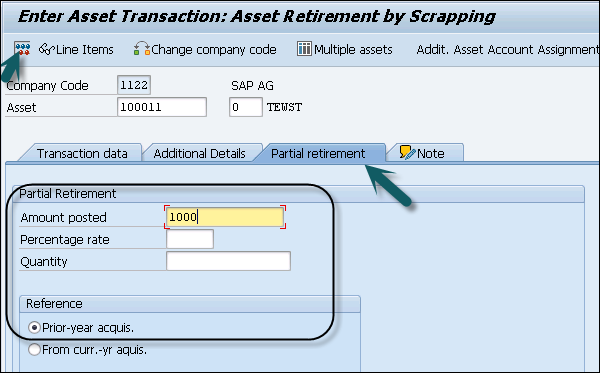
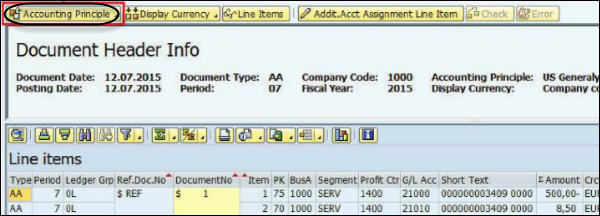
When you use scrapping, it decreases APC value by the amount entered minus depreciation calculated. In this, Only GAAP is selectable as the document is only posted to the OL ledger and the other ledgers get no update.
Step 4 − To post, click the Save button.

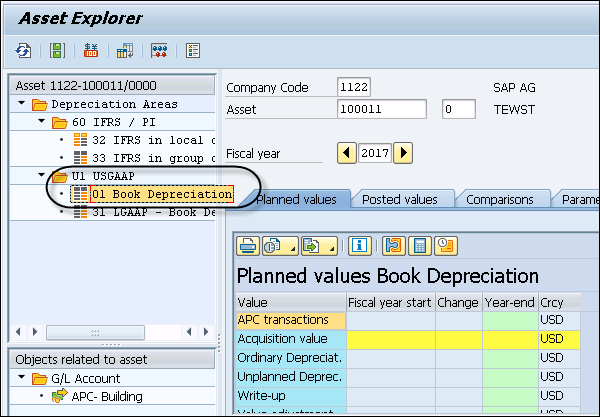
Step 5 − To view the result, start the Transaction AW01N – Asset Explorer by double clicking it.
Benefits:
- Good Business Practice. Asset management results in better decisions. Aligning management of infrastructure with strategic policies and direction will support the long-term success of the utility’s mission, goals and objectives.
- Improved Regulatory Compliance. For wastewater utilities in particular, the proposed CMOM regulations will require improved asset management. Part of asset management involves the implementation of better O&M practices, which can significantly improve compliance.
- Improved Reliability. More structured day-to-day attention to system assets and their condition means that unexpected failures are less likely, thus minimizing emergency repairs, costly lawsuits and customer relations problems. Assessing the risk implications of asset failure helps focus resources on critical priorities and reduces overall risk to the utility.
- Long Term System Integrity. The concept of “sustainable infrastructure” is gaining increased visibility, probably due to the problems in many American cities and towns where sufficient reinvestment in infrastructure has not been made. By relating costs to asset conditions and conducting long term planning for each asset, policy makers get the facts they need to help sustain the infrastructure.
- Cost Savings. There is evidence that asset management systems that maintain infrastructure in a sound and reliable condition and are based on minimizing life cycle costs, can significantly reduce operating and maintenance cost, as well as long-term capital expenses. A life cycle approach means that the utility always gets the most assets for its money.
- Eligibility for Federal Funding. The apparent need for increased infrastructure spending coupled with concerns over the quality of infrastructure management prevalent in the industry have led to a range of provisions in proposed funding legislation that include requirements for “asset management plans.”
Conclusion:
- Recently, a hacker broke into one of the Nutri Worldwide servers taking advantage of an application vulnerability. The server had various types of information at different levels of criticality.
- The information on the server was secured with appropriate security controls. Although the hacker was able to gain access only to the information with a lower level of protection, the breach had a huge impact on the organization. It was later found that there was a flaw in the classification process, leaving even sensitive information with very little protection.
Are you looking training with Right Jobs?
Contact Us- Information Security Management Tutorial
- Security Implications Tutorial
- SAP Security Interview Questions and Answers
- Information Security Management Principles
- Certified Information Security Manager (CISM) Certification
Related Articles
Popular Courses
- Itil Certification Training
11025 Learners - Ethical Hacking Training
12022 Learners - Hardware and Networking Training
11141 Learners
- What is Dimension Reduction? | Know the techniques
- Difference between Data Lake vs Data Warehouse: A Complete Guide For Beginners with Best Practices
- What is Dimension Reduction? | Know the techniques
- What does the Yield keyword do and How to use Yield in python ? [ OverView ]
- Agile Sprint Planning | Everything You Need to Know

