
IT Threats And Attacks Tutorial
Last updated on 10th Oct 2020, Blog, Tutorials
In Information Security threats can be many like Software attacks, theft of intellectual property, identity theft, theft of equipment or information, sabotage, and information extortion.
What is a Security Threat?
Security Threat is defined as a risk that which can potentially harm computer systems and organization. The cause could be physical such as someone stealing a computer that contains vital data. The cause could also be non-physical such as a virus attack. In these tutorial series, we will define a threat as a potential attack from a hacker that can allow them to gain unauthorized access to a computer system.

Subscribe For Free Demo
Error: Contact form not found.
What are Physical Threats?
A physical threat is a potential cause of an incident that may result in loss or physical damage to the computer systems.
The following list classifies the physical threats into three (3) main categories;
- 1. Internal: The threats include fire, unstable power supply, humidity in the rooms housing the hardware, etc.
- 2. External: These threats include Lightning, floods, earthquakes, etc.
- 3. Human: These threats include theft, vandalism of the infrastructure and/or hardware, disruption, accidental or intentional errors.
To protect computer systems from the above mentioned physical threats, an organization must have physical security control measures.
The following list shows some of the possible measures that can be taken:
- Internal: Fire threats could be prevented by the use of automatic fire detectors and extinguishers that do not use water to put out a fire. The unstable power supply can be prevented by the use of voltage controllers. An air conditioner can be used to control the humidity in the computer room.
- External: Lightning protection systems can be used to protect computer systems against such attacks. Lightning protection systems are not 100% perfect, but to a certain extent, they reduce the chances of Lightning causing damage. Housing computer systems in high lands are one of the possible ways of protecting systems against floods.
- Humans: Threats such as theft can be prevented by use of locked doors and restricted access to computer rooms.
What are Non-physical threats?
A non-physical threat is a potential cause of an incident that may result in;
- Loss or corruption of system data
- Disrupt business operations that rely on computer systems
- Loss of sensitive information
- Illegal monitoring of activities on computer systems
- Cyber Security Breaches
- Others
The non-physical threats are also known as logical threats. The following list is the common types of non-physical threats;
- 1. Virus
- 2. Trojans
- 3. Worms
- 4. Spyware
- 5. Key loggers
- 6. Adware
- 7. Denial of Service Attacks
- 8. Distributed Denial of Service Attacks
- 9. Unauthorized access to computer systems resources such as data
- 10. Phishing
- 11. Other Computer Security Risks
To protect computer systems from the above-mentioned threats, an organization must have logical security measures in place. The following list shows some of the possible measures that can be taken to protect cyber security threats
To protect against viruses, Trojans, worms, etc. an organization can use anti-virus software. In additional to the anti-virus software, an organization can also have control measures on the usage of external storage devices and visiting the website that is most likely to download unauthorized programs onto the user’s computer.
Unauthorized access to computer system resources can be prevented by the use of authentication methods. The authentication methods can be, in the form of user ids and strong passwords, smart cards or biometric, etc.
Intrusion-detection/prevention systems can be used to protect against denial of service attacks. There are other measures too that can be put in place to avoid denial of service attacks.
Vulnerabilities
A vulnerability is an inherent weakness in the design, configuration, implementation, or management of a network or system that renders it susceptible to a threat. Vulnerabilities are what make networks susceptible to information loss and downtime. Every network and system has some kind of vulnerability.
Threat
The threat is a possible security condition/violation to exploit the vulnerability of a system/asset. A threat can arise from any condition for example, accident, fire incident, environmental like natural disaster, human negligence. The following are various types of threats.
- Interruption
- Interception
- Fabrication
- Modification
Attack
The attack is an intended unauthorized action on a system/asset. An attack always has a motivation to misuse system and generally wait for an opportunity to occur.
The following are some of the important differences between Threat and Attack.
| Key | Threat | Attack |
|---|---|---|
| Intentional | Threats can be intentional like human negligence/failure or unintentional like natural disaster. | The attack is a deliberate action. An attacker have a motive and plan the attack accordingly. |
| Malicious | The threat may or may not malicious. | The attack is always malicious. |
| Definition | The threat by definition is a condition/circumstance which can cause damage to the system/asset. | Attack by definition, is an intended action to cause damage to system/asset. |
| Chance for Damage | Chance to damage or information alteration varies from low to very high. | The chance to damage or information alternation is very high. |
| Detection | A threat is difficult to detect. | An attack is comparatively easy to detect. |
| Prevention | A threat can be prevented by controlling the vulnerabilities. | An attack cannot be prevented by merely controlling the vulnerabilities. Other measures like backup, detect and act etc are required to handle a cyber-attack. |
Types of Cyber Attacks
A cyber-attack is an exploitation of computer systems and networks. It uses malicious code to alter computer code, logic or data and lead to cybercrimes, such as information and identity theft.
We are living in a digital era. Now a day, most of the people use computer and internet. Due to the dependency on digital things, the illegal computer activity is growing and changing like any type of crime.
Cyber-attacks can be classified into the following categories:
Web-based attacks
These are the attacks which occur on a website or web applications. Some of the important web-based attacks are as follows-
1. Injection attacks
It is the attack in which some data will be injected into a web application to manipulate the application and fetch the required information.
Example- SQL Injection, code Injection, log Injection, XML Injection etc.
2. DNS Spoofing
DNS Spoofing is a type of computer security hacking. Whereby a data is introduced into a DNS resolver’s cache causing the name server to return an incorrect IP address, diverting traffic to the attacker?s computer or any other computer. The DNS spoofing attacks can go on for a long period of time without being detected and can cause serious security issues.
3. Session Hijacking
It is a security attack on a user session over a protected network. Web applications create cookies to store the state and user sessions. By stealing the cookies, an attacker can have access to all of the user data.
4. Phishing
Phishing is a type of attack which attempts to steal sensitive information like user login credentials and credit card number. It occurs when an attacker is masquerading as a trustworthy entity in electronic communication.
5. Brute force
It is a type of attack which uses a trial and error method. This attack generates a large number of guesses and validates them to obtain actual data like user password and personal identification number. This attack may be used by criminals to crack encrypted data, or by security, analysts to test an organization’s network security.
6. Denial of Service
It is an attack which meant to make a server or network resource unavailable to the users. It accomplishes this by flooding the target with traffic or sending it information that triggers a crash. It uses the single system and single internet connection to attack a server. It can be classified into the following-
Volume-based attacks- Its goal is to saturate the bandwidth of the attacked site, and is measured in bit per second.
Protocol attacks- It consumes actual server resources, and is measured in a packet.
Application layer attacks- Its goal is to crash the web server and is measured in request per second.
7. Dictionary attacks
This type of attack stored the list of a commonly used password and validated them to get original password.
8. URL Interpretation
It is a type of attack where we can change the certain parts of a URL, and one can make a web server to deliver web pages for which he is not authorized to browse.
9. File Inclusion attacks
It is a type of attack that allows an attacker to access unauthorized or essential files which is available on the web server or to execute malicious files on the web server by making use of the include functionality.
10. Man in the middle attacks
It is a type of attack that allows an attacker to intercepts the connection between client and server and acts as a bridge between them. Due to this, an attacker will be able to read, insert and modify the data in the intercepted connection.
System-based attacks
These are the attacks which are intended to compromise a computer or a computer network. Some of the important system-based attacks are as follows-
1. Virus
It is a type of malicious software program that spread throughout the computer files without the knowledge of a user. It is a self-replicating malicious computer program that replicates by inserting copies of itself into other computer programs when executed. It can also execute instructions that cause harm to the system.
2. Worm
It is a type of malware whose primary function is to replicate itself to spread to uninfected computers. It works same as the computer virus. Worms often originate from email attachments that appear to be from trusted senders.
3. Trojan horse
It is a malicious program that occurs unexpected changes to computer setting and unusual activity, even when the computer should be idle. It misleads the user of its true intent. It appears to be a normal application but when opened/executed some malicious code will run in the background.
4. Backdoors
It is a method that bypasses the normal authentication process. A developer may create a backdoor so that an application or operating system can be accessed for troubleshooting or other purposes.
5. Bots
A bot (short for “robot”) is an automated process that interacts with other network services. Some bots program run automatically, while others only execute commands when they receive specific input. Common examples of bots program are the crawler, chatroom bots, and malicious bots.
Types of Cyber Attackers
In computer and computer networks, an attacker is the individual or organization who performs the malicious activities to destroy, expose, alter, disable, steal or gain unauthorized access to or make unauthorized use of an asset.
As the Internet access becomes more pervasive across the world, and each of us spends more time on the web, there is also an attacker grows as well. Attackers use every tools and techniques they would try and attack us to get unauthorized access.
There are four types of attackers which are described below-
Cyber Criminals
Cybercriminals are individual or group of people who use technology to commit cybercrime with the intention of stealing sensitive company information or personal data and generating profits. In today’s, they are the most prominent and most active type of attacker.
Cybercriminals use computers in three broad ways to do cybercrimes-
- 1. Select computer as their target– In this, they attack other people’s computers to do cybercrime, such as spreading viruses, data theft, identity theft, etc.
- 2. Uses the computer as their weapon– In this, they use the computer to do conventional crime such as spam, fraud, illegal gambling, etc.
- 3. Uses the computer as their accessory– In this, they use the computer to steal data illegally.
Hacktivists
Hacktivists are individuals or groups of hackers who carry out malicious activity to promote a political agenda, religious belief, or social ideology. According to Dan Lohrmann, chief security officer for Security Mentor, a national security training firm that works with states said “Hacktivism is a digital disobedience. It’s hacking for a cause.” Hacktivists are not like cybercriminals who hack computer networks to steal data for the cash. They are individuals or groups of hackers who work together and see themselves as fighting injustice.
State-sponsored Attacker
State-sponsored attackers have particular objectives aligned with either the political, commercial or military interests of their country of origin. These type of attackers are not in a hurry. The government organizations have highly skilled hackers and specialize in detecting vulnerabilities and exploiting these before the holes are patched. It is very challenging to defeat these attackers due to the vast resources at their disposal.
Insider Threats
The insider threat is a threat to an organization’s security or data that comes from within. These type of threats are usually occurred from employees or former employees, but may also arise from third parties, including contractors, temporary workers, employees or customers.
Insider threats can be categorized below-
Malicious
Malicious threats are attempts by an insider to access and potentially harm an organization’s data, systems or IT infrastructure. These insider threats are often attributed to dissatisfied employees or ex-employees who believe that the organization was doing something wrong with them in some way, and they feel justified in seeking revenge.
Insiders may also become threats when they are disguised by malicious outsiders, either through financial incentives or extortion.
Accidental
Accidental threats are threats which are accidently done by insider employees. In this type of threats, an employee might accidentally delete an important file or inadvertently share confidential data with a business partner going beyond company?s policy or legal requirements.
Negligent
These are the threats in which employees try to avoid the policies of an organization put in place to protect endpoints and valuable data. For example, if the organization have strict policies for external file sharing, employees might try to share work on public cloud applications so that they can work at home. There is nothing wrong with these acts, but they can open up to dangerous threats nonetheless.
Cyber Security Principles
The UK internet industry and Government recognized the need to develop a series of Guiding Principles for improving the online security of the ISPs’ customers and limit the rise in cyber-attacks. Cybersecurity for these purposes encompasses the protection of essential information, processes, and systems, connected or stored online, with a broad view across the people, technical, and physical domains.
These Principles recognize that the ISPs (and other service providers), internet users, and UK Government all have a role in minimizing and mitigating the cyber threats inherent in using the internet.
These Guiding Principles have been developed to respond to this challenge by providing a consistent approach to help, inform, educate, and protect ISPs’ (Internet Service Provider’s) customers from online crimes. These Guiding Principles are aspirational, developed and delivered as a partnership between Government and ISPs. They recognize that ISPs have different sets of customers, offer different levels of support and services to protect those customers from cyber threats.
Some of the essential cybersecurity principles are described below-
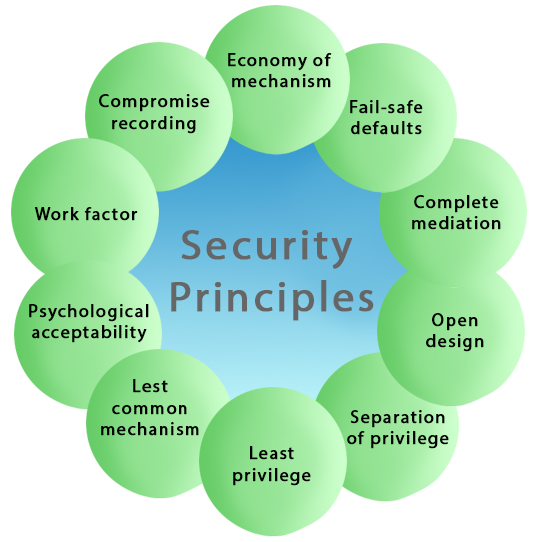
- Economy of mechanism
- Fail-safe defaults
- Least Privilege
- Open Design
- Complete mediation
- Separation of Privilege
- Least Common Mechanism
- Psychological acceptability
- Work Factor
- Compromise Recording
1. Economy of mechanism
This principle states that Security mechanisms should be as simple and small as possible. The Economy of mechanism principle simplifies the design and implementation of security mechanisms. If the design and implementation are simple and small, fewer possibilities exist for errors. The checking and testing process is less complicated so that fewer components need to be tested.
Interfaces between security modules are the suspect area which should be as simple as possible. Because Interface modules often make implicit assumptions about input or output parameters or the current system state. If the any of these assumptions are wrong, the module’s actions may produce unexpected results. Simple security framework facilitates its understanding by developers and users and enables the efficient development and verification of enforcement methods for it.
2. Fail-safe defaults
The Fail-safe defaults principle states that the default configuration of a system should have a conservative protection scheme. This principle also restricts how privileges are initialized when a subject or object is created. Whenever access, privileges/rights, or some security-related attribute is not explicitly granted, it should not be grant access to that object.
Example: If we will add a new user to an operating system, the default group of the user should have fewer access rights to files and services.
3. Least Privilege
This principle states that a user should only have those privileges that need to complete his task. Its primary function is to control the assignment of rights granted to the user, not the identity of the user. This means that if the boss demands root access to a UNIX system that you administer, he/she should not be given that right unless he/she has a task that requires such level of access. If possible, the elevated rights of a user identity should be removed as soon as those rights are no longer needed.
4. Open Design
This principle states that the security of a mechanism should not depend on the secrecy of its design or implementation. It suggests that complexity does not add security. This principle is the opposite of the approach known as “security through obscurity.” This principle not only applies to information such as passwords or cryptographic systems but also to other computer security related operations.
Example: DVD player & Content Scrambling System (CSS) protection. The CSS is a cryptographic algorithm that protects the DVD movie disks from unauthorized copying.
5. Complete mediation
The principle of complete mediation restricts the caching of information, which often leads to simpler implementations of mechanisms. The idea of this principle is that access to every object must be checked for compliance with a protection scheme to ensure that they are allowed. As a consequence, there should be wary of performance improvement techniques which save the details of previous authorization checks, since the permissions can change over time.
Whenever someone tries to access an object, the system should authenticate the access rights associated with that subject. The subject’s access rights are verified once at the initial access, and for subsequent accesses, the system assumes that the same access rights should be accepted for that subject and object. The operating system should mediate all and every access to an object.
Example: An online banking website should require users to sign-in again after a certain period like we can say, twenty minutes has elapsed.
6. Separation of Privilege
This principle states that a system should grant access permission based on more than one condition being satisfied. This principle may also be restrictive because it limits access to system entities. Thus before privilege is granted more than two verification should be performed.
Example: To su (change) to root, two conditions must be met-
- 1. The user must know the root password.
- 2. The user must be in the right group (wheel).
7. Least Common Mechanism
This principle states that in systems with multiple users, the mechanisms allowing resources shared by more than one user should be minimized as much as possible. This principle may also be restrictive because it limits the sharing of resources.
Example: If there is a need to be accessed a file or application by more than one user, then these users should use separate channels to access these resources, which helps to prevent from unforeseen consequences that could cause security problems.
8. Psychological acceptability
This principle states that a security mechanism should not make the resource more complicated to access if the security mechanisms were not present. The psychological acceptability principle recognizes the human element in computer security. If security-related software or computer systems are too complicated to configure, maintain, or operate, the user will not employ the necessary security mechanisms. For example, if a password is matched during a password change process, the password changing program should state why it was denied rather than giving a cryptic error message. At the same time, applications should not impart unnecessary information that may lead to a compromise in security.
Example: When we enter a wrong password, the system should only tell us that the user id or password was incorrect. It should not tell us that only the password was wrong as this gives the attacker information.
9. Work Factor
This principle states that the cost of circumventing a security mechanism should be compared with the resources of a potential attacker when designing a security scheme. In some cases, the cost of circumventing (“known as work factor”) can be easily calculated. In other words, the work factor is a common cryptographic measure which is used to determine the strength of a given cipher. It does not map directly to cybersecurity, but the overall concept does apply.
Example: Suppose the number of experiments needed to try all possible four character passwords is 244 = 331776. If the potential attacker must try each experimental password at a terminal, one might consider a four-character password to be satisfactory. On the other hand, if the potential attacker could use an astronomical computer capable of trying a million passwords per second, a four-letter password would be a minor barrier for a potential intruder.
10. Compromise Recording
The Compromise Recording principle states that sometimes it is more desirable to record the details of intrusion that to adopt a more sophisticated measure to prevent it.
Example: The servers in an office network may keep logs for all accesses to files, all emails sent and received, and all browsing sessions on the web. Another example is that Internet-connected surveillance cameras are a typical example of a compromise recording system that can be placed to protect a building.
Importance of Threat Intelligence
Raw data from the existing threats are gathered from multiple sources by the threat intelligence. The automated security control solutions use the information present in the intel feeds and management reports produced by analyzing and filtering the gathered data. This security aims to inform the organization of advanced continuous threats, zero-day threats, and exploit risks and provide protection against such threats.
The following objectives can be achieved by implementing the threat intelligence:
- Staying up to date with daily emerging threats, methods, weaknesses, targets, etc. that are huge in volumes.
- Make us more proactive against the threats that are about to happen in the future.
- Informing the users, stakeholders, and leaders about the latest threats and the effects they could have on their businesses.
How Threat Intelligence Works?
Threat intelligence is the output product of a cycle of data collection, processing, and analysis that consists of six parts. An intelligence program becomes effective when it is iterative in nature becoming more refined in each iteration. The threat intelligence can be produced effectively if the use cases are identified and the objectives are defined.
The steps to maximize the value of threat intelligence are:
1. Planning and Direction
Asking the right question is the first step to produce valuable threat intelligence. The questions must be focused on a single fact or single event or single activity and such questions add to the value of threat intelligence. Open and broad questions must be avoided. The intelligence objectives must be based on factors like how close they are to the core values of the organization, what is the impact of the resulting decision, is the decision time-sensitive. It is also important to understand who is benefitting from the output product.
2. Collection
The new requirements that are set up in the first stage must be fulfilled in this step by gathering the raw data. The data can be collected from a variety of sources. Network event logs and responses of the past incident’s records are the internal sources of data. Open web, dark web, etc. are the external sources of data. Threat data can be IOC’s list like malicious IP addresses, domains, etc. but there can also be personal identity information of customers, text from sources of news or social media that are vulnerable.
3. Processing
The data after it has been collected must be sorted, organized with tags of metadata and redundant information or false positives and negatives must be filtered out. The data collected by the organizations are too huge to be processed by humans, hence data collection and processing must be automated.
4. Analysis
The processed data must make sense and that is taken care of in this step. The aim of the analysis is to find out the possible security issues and let the teams know to fulfill the requirements of intelligence. Based on the audience, threat intelligence can be of many forms, but the basic idea is to make the audience understand by converting the data into a proper format.
5. Dissemination
The distribution of the output product to its consumers is done by this step. Right people at the right time must be available for the threat intelligence to be in action. There must be a tracking of threat intelligence so that there is a continuation from one cycle of intelligence to another cycle of intelligence and learning is maintained. The intelligence cycle is tracked using security systems and they are integrated with ticketing systems. Multiple people from different teams accept, write up, and review the tickets whenever a request for new intelligence comes up.
6. Feedback
When the intelligence cycle becomes a full circle going back to the initial planning phase is the final step in the intelligence cycle. When the output product is ready, the person who requested the product reviews it and check if there are answers to all the questions asked. This makes for the objectives of the next threat intelligence cycle.
Benefits
- 1. The threats faced by the organization can be determined immediately.
- 2. Decision making by addressing the vulnerabilities and the order in which the vulnerabilities must be addressed can be determined by the information gained using threat intelligence.
- 3. Emerging threats information can be accessed.
- 4. The activities of cyber-criminals can be tracked using threat intelligence.
- 5. If the organization or a brand is mentioned in social media can be monitored.
- 6. The online channels of communication are monitored for proofs of activities of cybercrime.
- 7. Checking the strength of the internet in the organization to determine if it’s vulnerable.
- 8. Security breaches can be identified and prevented by using threat intelligence.
- 9. Fraud and theft can be prevented and minimized by incident monitoring.
- 10. Threat management provides the information required for risk management of the organization.
Drawbacks
- The defenders are unable to act on security incidents with the highest priority because of signal to noise problems.
- False threat reports are being filed by the attackers to mislead the intelligence systems.
- Most of the data gathered by security peoples are duplicate in nature thereby wasting time and effort.
- Security systems must match the attack speeds.
- Data can be turned into intelligence if and only if there is the identification of patterns.
Conclusion
Modern security teams are driven by threat intelligence because it gives in-depth knowledge about threats thereby protecting the organization from all kinds of attacks. The value of threat intelligence is recognized by the organizations and studies show that organizations investing in intelligence are increasing day by day.
Summary
- A threat is any activity that can lead to data loss/corruption through to disruption of normal business operations.
- There are physical and non-physical threats
- Physical threats cause damage to computer systems hardware and infrastructure. Examples include theft, vandalism through to natural disasters.
- Non-physical threats target the software and data on the computer systems.
Are you looking training with Right Jobs?
Contact Us- Information Security Management Tutorial
- Security Implications Tutorial
- The Top In-demand cloud skills for 2020
- “Microsoft Dynamics 365 Tutorial “
- Top IT Security Jobs
Related Articles
Popular Courses
- Cyber Security Training
11025 Learners - Ethical Hacking Training
12022 Learners - Hardware And Networking Training
11141 Learners
- What is Dimension Reduction? | Know the techniques
- Difference between Data Lake vs Data Warehouse: A Complete Guide For Beginners with Best Practices
- What is Dimension Reduction? | Know the techniques
- What does the Yield keyword do and How to use Yield in python ? [ OverView ]
- Agile Sprint Planning | Everything You Need to Know
