
Splunk Enterprise Security Tutorial | Get all the Reviews, Ratings, and Features
Last updated on 10th Aug 2022, Blog, Tutorials
Introdution:
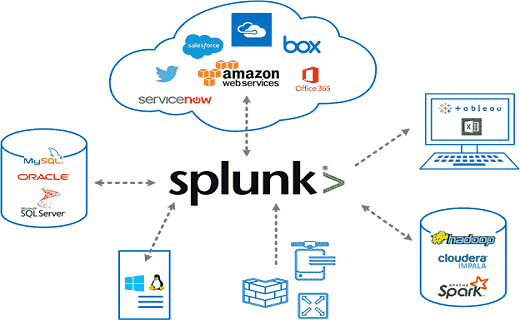
Splunk may be a software package package that allows one to watch, search, visualize, and collectively to analysis machine-generated info (best example unit of measurement application logs, info from websites, information logs for a start) to big-data using a web vogue interface. it’s advanced software package package that indexes and searches log files hold on on a system or selection, aboard to that, it is a scalable and potent software package package. Splunk bridges the gaps that one straightforward log management software package package or a security knowledge product or one event management product can manage all by themselves.Splunk Es can assist you accomplish continuous looking, support your security operations center (SOC), implement incident response, or inform stakeholders regarding business risks. you will run the solution in varied environments, like public and private clouds, on-premises infrastructure, and hybrid deployments.
Advantages:
1. Amount of your time Monitoring:Splunk Es provides terribly clear image of your Organization’s security posture and it makes it terribly straightforward to customize views for higher accessibility. you will even drill down these views to identify the raw event with an excellent deal of ease. Provides ways in which and means to key security indicators and collectively provides access to static and dynamic thresholds
2.Rate and act:Splunk Es provides a granular scan on the protection aspects of your info, that in turn can increase the speed at that the issues are detected. Once this will be achieved, we have a tendency to ar ready to painstakingly examine optimizing the incident responses with alerts, centralized logs or pre-defined reports and correlations.
3. Quicker investigations:Splunk Es provides you with ways in which and means to conduct ad-hoc searches and collectively permits you to examine static or dynamic correlations among the tactic of characteristic any malicious activities against your Organization.
4.Handle construction or multistep investigations:With the provided security, we have a tendency to ar ready to conduct organized checks on but the attack your own Organization. supported this, we have a tendency to ar ready to trace out the specified dynamic activities and collectively fill the associated risks which is able to cause any of the advanced threats. Applying the kill-chain methodology to analysis and establish the attack lifecycle.
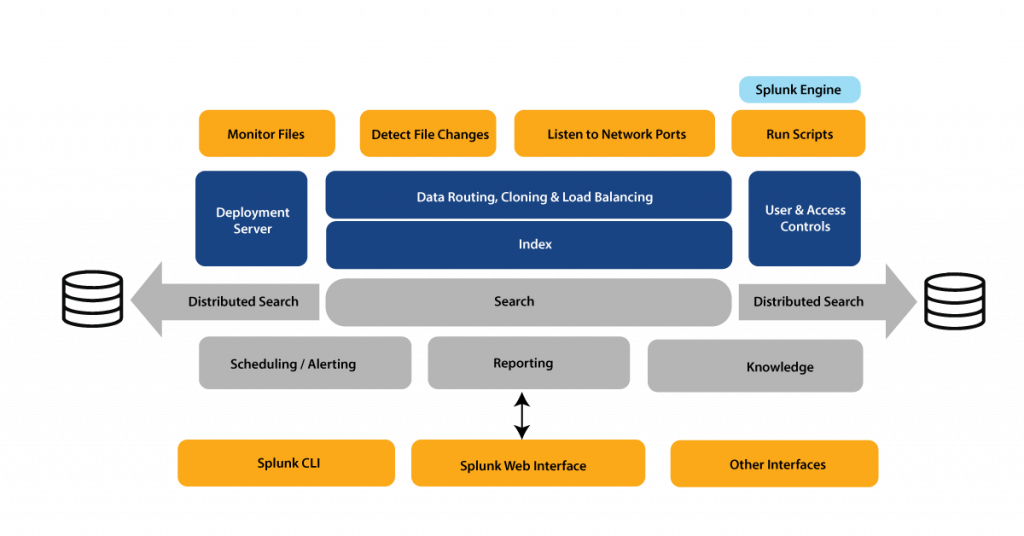
Architecture:
By using data forwarding scripts, you might in fact gather information from a variety of tcp ports.
- You may monitor the files as they come in and spot changes.
- The forwarder may intelligently route, clone, and conduct load balancing on data before it reaches the indexer. While load balancing makes sure that data can be passed to another instance hosting the indexer even if one instance fails, cloning makes several copies of an event at the data source.
- As indicated before, the deployment server is in charge of overseeing every aspect of the deployment, including configurations and policies.
- When this data is received, an indexer stores it. Permissions can be established at each data store to limit what each user sees, accesses, and uses after the indexer has been separated into logical data stores.
- After the data has been entered, you can search the index data and distribute searches to other search peers. The combined results will then be sent back to the search head.
- In addition, you may plan searches and create alerts that are activated when particular criteria match saved searches.
- Users could build reports and use saved searches to evaluate data using Visual representation dashboards.
- Knowledge objects may eventually be utilised to improve existing unstructured data.
- Search heads and knowledge items can be accessed either the Splunk Web Interface or the Splunk CLI. A REST API connection is used for this communication.
Uses of Spunk
Security looking:
Splunk ceaselessly monitors all network resources and activity 24/7 therefore on notice abnormal behavior before it poses a major threat to the organization. practice the information Splunk provides, security teams can get associate degree exhaustive, data-driven scan into the performance, health, and vulnerabilities of the network at any given time. Malicious or speculative activity detected by Splunk automatically alerts the suitable parties with complete discourse knowledge particularization the threat.
- Machine-driven event alerts.
- Machine-driven event log assortment for all devices, applications, and user activity.
- Data-rich, graphical user dashboards.
- Pre-defined and customizable correlation parameters.
- Gather necessary info to require care of audit readiness.
Advanced Threat Detection:
Intelligent looking of infrastructure, applications, users, and various network resources across environments permits Splunk to catch and contextualize active threats or abnormal behavior as they occur in amount of your time. Splunk cross-correlates event logs to unearth indicators of compromise or malicious relationships therefore security teams can straightaway move with potential threats before any important injury are caused to the network.
- End-to-end network visibility and analytics.
- Intelligent threat classification.
- Event log correlation across devices and environments.
- Kill chain methodology to identify advanced threats.
- User behavior analytics (UBA) to note activity and mathematics anomalies.
User Behavior Analytics:
Leveraging machine learning algorithms, Splunk proactively baselines network behavior still as correlates user behavior across info sources and environments to catch hard to note security threats. Deviations from regular network activity automatically alerts the chosen security teams so as that they’ll quickly mitigate the threats and/or conduct multi-step rhetorical investigations as necessary.
- Machine-driven early breach detection.
- Machine-driven continuous threat looking.
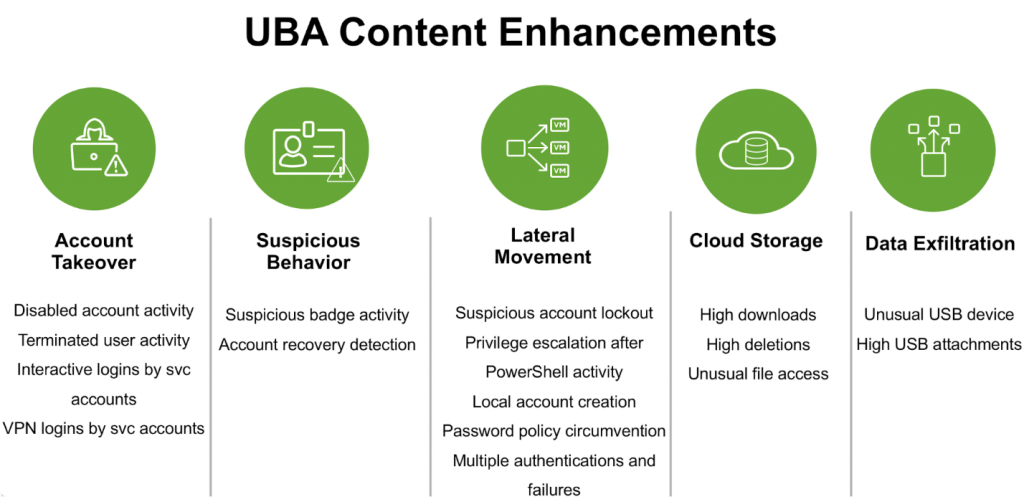
- sight compromised accounts, executive threats, lateral movement, etc.
- Event log correlation across multiple info sources.
- User risk analysis.
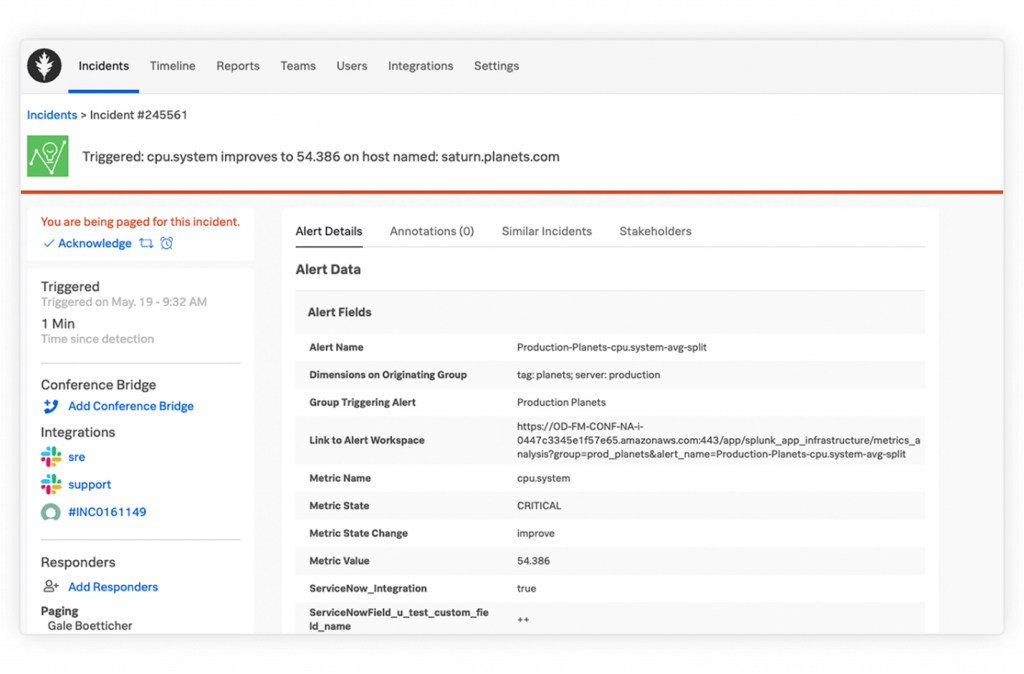
Incident Response:
Once a threat is detected, security teams can quickly respond with a stronger degree of confidence than with heritage SIEM technology. Splunk’s adaptative Response Framework contextualizes event info across environments and automates response workflows therefore analysts can merely make certain, prioritize, and engage the threats with the relevant knowledge they need.
- Event alerts with threat prioritization.
- Mechanically pull relevant threat knowledge across devices and environments.
- Response advancement automation.
- Data-rich dashboards and graphical displays.
Splunk monitors and logs large info sets of security knowledge gleaned from a ramification of network sources day by day. Security teams can use this well-spring of knowledge to conduct thorough rhetorical investigations into the origins of a breach or validate rising threats to comprehend deeper insight into the performance of their security efforts (and produce enhancements accordingly).
- Alert sorting to identify high-priority incidents automatically
- Knowledge searchable across devices, users, applications, time frames, etc.
- Customizable visualizations and reports
- Ability to style event and activity sequences.
Difference Between Tableau and Splunk:
Ranking:According to EDUCBA, a corporate bridge consultant, Tableau is the best analytical tool, with Splunk coming in second.
Role: While Splunk’s major function is to gather and index machine-generated information, Tableau’s primary function is to visualise and communicate information for quick decisions.
Data Source: In Tableau, data models in an upfront schema can be used to synthesise information. The uniformity of information also calls for an extraction procedure.
Using the Splunk search box, information may be extracted. The uniformity of information does not necessitate the use of a relational database on the backend.Price:Tableau’s price starts at $70 per month, whereas Splunk’s pricing begins at $675 per month.
Created for:While Splunk is a system monitoring tool created for developers, Tableau is a visualisation tool created for analysts, business decision-makers, and data scientists.
Supported platforms:Tableau runs on Windows, Mac, Linux, Android, iPhone/iPad, and Web-based platforms. Splunk is accessible on every platform, with the exception of Linux and web-based platforms, just as Tableau.
Services provided:Tableau provides services like data management, analytics, and visualisation, whereas Splunk provides services like security and compliance, IT operations, adoption, and cloud.
The Breadth of Splunk’s Coverage
The Internet of Things (IoT) is unquestionably the future of our generation, and handling the various types of data together is not a simple task. The simplicity of installation and the breadth of its use in big data analytics are largely responsible for Splunk’s meteoric rise to prominence. The software’s potential applications are expanding at a breakneck pace in tandem with the expansion of the capabilities of the information technology industry as a whole. Splunk is without a doubt the most effective product on the market for managing machine data, which is a requirement for every information technology organisation, regardless of size.Splunk has emerged as a frontrunner among the major competitors in the technology sector as a result of its extensive and flexible machine learning capabilities. It does not stop there; rather, it continually adds new features to its infrastructure in order to make it more user-friendly.
Disadvantages of Splunk:
- When dealing with enormous data quantities, pricing can become more expensive.
- Search engine optimization might be seen of as more of an art than a purely scientific endeavour.
- When contrasted to tableau, dashboard has a somewhat harsh tone.
- It is persistently working to find open source alternatives to it and replace it.
Are you looking training with Right Jobs?
Contact Us- Splunk Eval Commands With Examples | Free Guide Tutorial [ OverView ]
- Dedup : Splunk Documentation | Step-By-Step Process | Expert’s Top Picks
- What is Splunk Rex : Step-By-Step Process with REAL-TIME Examples
- What is Splunk Logging ? | The Ultimate Guide with Expert’s Top Picks
- How to create a Splunk Dashboard | A Complete Guide For Beginners [ OverView ]
Related Articles
Popular Courses
- VM Ware Training
11025 Learners - Microsoft Dynamics Training
12022 Learners - Siebel Training
11141 Learners
- What is Dimension Reduction? | Know the techniques
- Difference between Data Lake vs Data Warehouse: A Complete Guide For Beginners with Best Practices
- What is Dimension Reduction? | Know the techniques
- What does the Yield keyword do and How to use Yield in python ? [ OverView ]
- Agile Sprint Planning | Everything You Need to Know
