
The Most Effective Data Encryption Techniques
Last updated on 14th Oct 2020, Artciles, Blog
Encryption is a way of scrambling data so that only authorized parties can understand the information. In technical terms, it is the process of converting plaintext to ciphertext. In simpler terms, encryption takes readable data and alters it so that it appears random. Encryption requires the use of an encryption key: a set of mathematical values that both the sender and the recipient of an encrypted message know.
Although encrypted data appears random, encryption proceeds in a logical, predictable way, so that a party receiving the encrypted data and in possession of the key used to encrypt the data can decrypt the data, turning it back into plaintext. Truly secure encryption will be complex enough that a third party is highly unlikely to decrypt the ciphertext by brute force – in other words, by guessing.
Subscribe For Free Demo
Error: Contact form not found.
Data can be encrypted “at rest,” when it is stored, or “in transit,” while it is being transmitted somewhere else.
What is a key in cryptography?
A cryptographic key is a string of characters used within an encryption algorithm for altering data so that it appears random. Like a physical key, it locks (encrypts) data so that only someone with the right key can unlock (decrypt) it.
What are the different types of encryption?
The two main kinds of encryption are symmetric encryption and asymmetric encryption. Asymmetric encryption is also known as public key encryption.
In symmetric encryption, there is only one key, and all communicating parties use the same key for encryption and decryption. In asymmetric, or public key, encryption, there are two keys: one key is used for encryption, and a different key is used for decryption. Either key can be used for either action, but data encrypted with the first key can only be decrypted with the second key, and vice versa. One key is kept private, while one key is shared publicly, for anyone to use – hence the “public key” name. Asymmetric encryption is a foundational technology for SSL (TLS).
Why is data encryption necessary?
Privacy: Encryption ensures that no one can read communications or data at rest except the intended recipient or proper data owner. This prevents attackers, ad networks, Internet service providers, and in some cases governments from intercepting and reading sensitive data.
Security: Encryption helps data breaches, whether the data is in transit or at rest. If a corporate device is lost or stolen and its hard drive is properly encrypted, the data on that device will likely still be secure. Similarly, encrypted communications enable the communicating parties to exchange sensitive data without leaking the data. Encryption also helps prevent malicious behavior such as on-path attacks.
Authentication: Public key encryption, among other things, establishes that a website’s origin server owns the private key and therefore was legitimately issued an SSL certificate (see What is public key encryption? to learn more).
Regulations: For all these reasons, many industry and government regulations require companies that handle user data to keep that data encrypted. Examples of regulatory and compliance standards that require encryption include HIPAA, PCI-DSS, and the GDPR.
What is an encryption algorithm?
An encryption algorithm is the mathematical formula used to transform data into ciphertext. An algorithm will use the key in order to alter the data in a predictable way, so that even though the encrypted data will appear random, it can be turned back into plaintext by using the key again.
What are some common encryption algorithms?
Commonly used encryption algorithms include:
- Blowfish
- AES
- RC4, RC5, RC6
- DES
- Twofish
What is a brute force attack in encryption?
A brute force attack is when an attacker who does not know the key for decryption attempts to determine the key by making thousands or millions of guesses. Brute force attacks are much faster with modern computers, which is why encryption has to be extremely strong and complex. Most modern encryption methods, coupled with high-quality passwords, are resistant to brute force attacks, although they may be in the future as computers become more and more powerful. Weak passwords are still susceptible to this type of attack.
How is encryption used to keep Internet browsing secure?
Encryption is foundational for a variety of technologies, but it is especially important for keeping HTTP requests and responses secure, and for authenticating website origin servers. The protocol responsible for this is called HTTPS (Hypertext Transfer Protocol Secure). A website served over HTTPS instead of HTTP will have a URL that begins with https:// instead of http://.
HTTPS uses the encryption protocol called Transport Layer Security (TLS). In the past, an earlier encryption protocol called Secure Sockets Layer (SSL) was the standard, but TLS has replaced SSL. A website that implements HTTPS will have an SSL certificate installed on its origin server.To help keep the Internet more secure, Cloudflare offers free TLS/SSL encryption for any websites using Cloudflare services.
Different Types Of Encryption
As technology is advancing, modern encryption techniques have taken over the outdated ones. Hence, there are several different types of encryption software that have made our job easy. So for your ease, I have provided you with a list of best encryption types below.
Triple DES
Triple Data Encryption Algorithm or Triple-DES uses symmetric encryption. It is an advanced version of DES block cipher, which used to have a 56-bit key. However, and as the name suggests, TDES encrypts data using 56-bit key thrice, making it a 168-bit key. It works in three phases when encrypting the data:
- encrypt
- decrypt
- re-encrypt
Likewise, the decryption phases would be:
- decrypt
- encrypt
- decrypt again
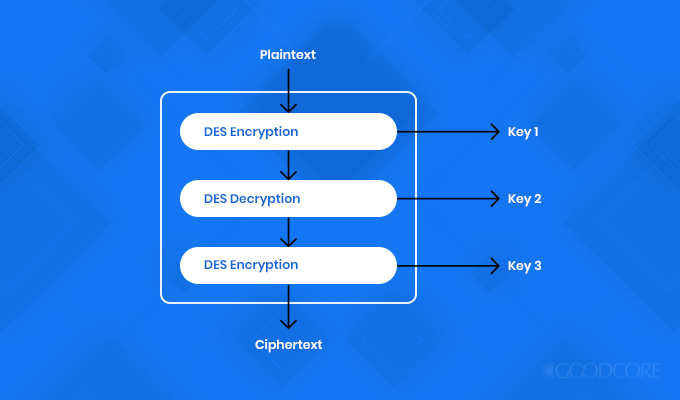
Triple DES encryption model
Since it encrypts thrice, therefore it is much slower as compared to other types of encryption. Not only that, but it also encrypts data in shorter block lengths, therefore it becomes fairly easy to decrypt the data during the entire encryption process. Hence, there is a higher risk of data theft. However, before other modified types of encryptions emerged, it was the most recommended and widely adopted algorithm.
Even though it is phasing out, many financial and business organisations still use this encryption type to protect their data.
AES
The Advanced Encryption Standard (AES) is also symmetric encryption based on the Rijndael algorithm. It uses block-cipher and encrypts one fixed-size block at a time. It works in 128-bit or 192-bit but can be extended up to the 256-bit key length. To encrypt every bit, there are different rounds. For instance, 128-bit will have 10 rounds, 192-bit will have 12 rounds and so on.
It is considered as one of the best encryption algorithms because it was developed by the US National Institute of Standards and Technology. It is also one of the secured types of encryptions as it works on a single private key.
RSA
Rivest–Shamir–Adleman (RSA) encryption is an asymmetric cipher that functions on two keys: a public key for encryption and a private key for decryption. Considered as the best encryption algorithm, it functions on 1024-bit and can extend up to 2048-bit key length. This means that the larger the key size, the slower the encryption process becomes.
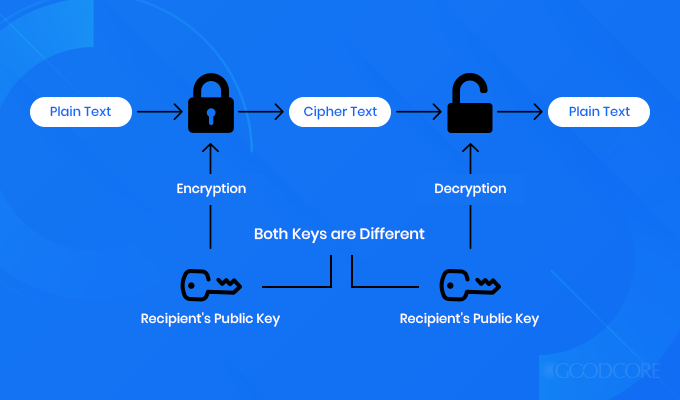
RSA encryption model
Due to a larger key size, it is known to be as one of the strongest encryption types. It is also considered as an encryption standard for data shared over the internet because it is the most secure encryption algorithm up till now. As compared to other types of encryption, RSA gives hackers quite a tough time because of the length of the keys it works with.
Blowfish
Another encryption algorithm designed to replace DES, Blowfish is a symmetric block cipher, which works on a variable key length from 32 bits to 448 bits. Since it is a block cipher, therefore it divides data or a message into fixed 64-bit blocks when encrypting and decrypting.
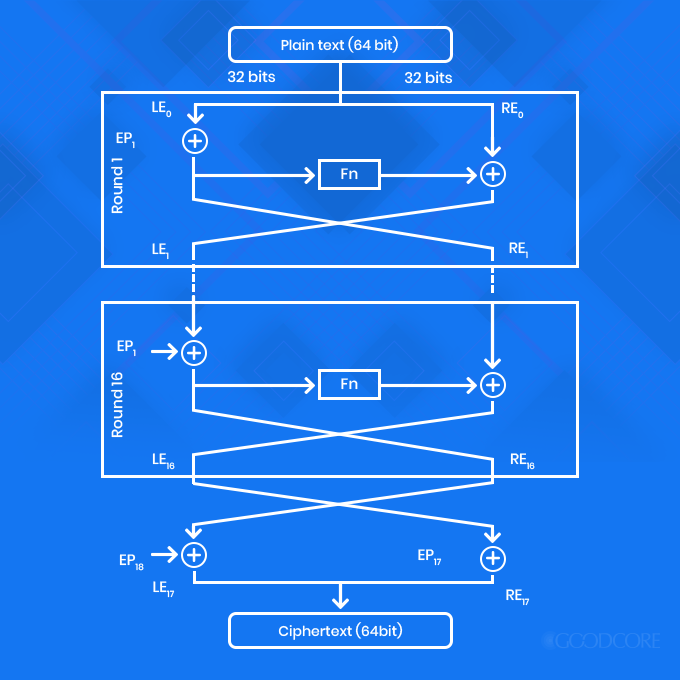
Blowfish encryption model
It was designed to function fast and is available as free public encryption software for any user. It is neither patented nor licensed. Being a public encryption platform, it has been tested multiple times for its speed, efficiency and security. Many organisations claim that no one has successfully hacked it. Hence, Blowfish has become a choice for vendors and e-commerce mainly helping them secure payments, passwords and other confidential information.
Twofish
Also a symmetric block cipher, Twofish is an advanced version of Blowfish encryption. It has a block size of 128-bits and can extend to the 256-bit key length. Like other symmetric ciphers, it also breaks data into fixed-length blocks. However, it functions in 16 rounds regardless of how large the data is. Amongst the various types of encryption, this one is flexible. It allows you to choose the encryption process to be quick while the key setup to be slow and vice versa.
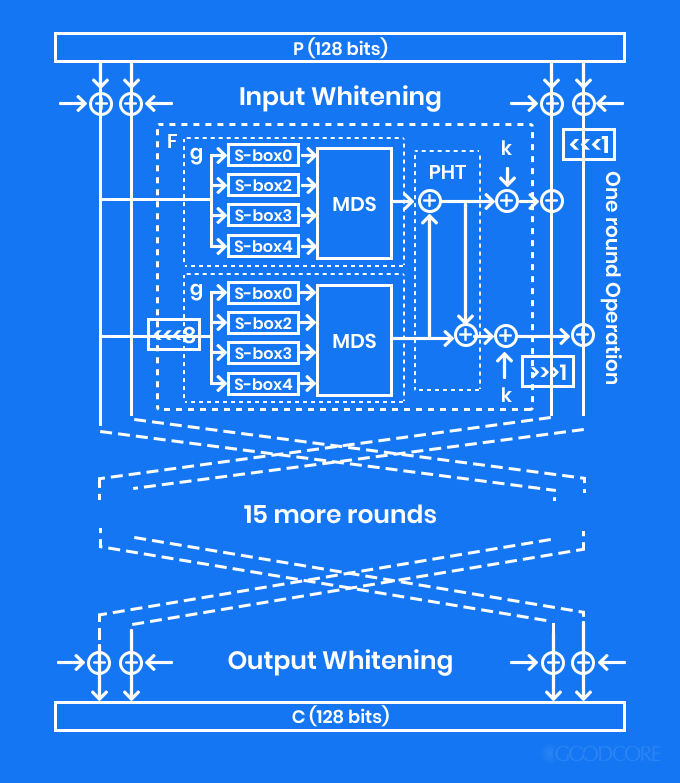
Twofish encryption model
Since this is license-free and considerable fast, you have full control over it as compared to other types of encryption. If AES would not have become the best encryption algorithm, Twofish would have been considered as one.
FPE
Format Preserving Encryption (FPE) is a fairly new encryption method. It encrypts your data in a similar format. For instance, if you have encrypted your password having 6 letters, 5 numbers and 4 special letters, then your output will be a different combination of a similar format.
In other words, if you use this encryption technique, it will preserve the format of your plain text that is after encryption the structure of your data will remain the same.
Encryption Applications
By this point, I am assuming you are well-aware of how to secure your data. But there is another factor that needs to be addressed, which is how to make sure that the message you send does not get altered or changed. For that, you need to know about the following encryption applications that will make sure of that.
Hashes
Once you have chosen your desired encryption type, you need to further make sure that your data is not altered and is authentic and verified. For that, you need to use hashes. They are a one-way function that takes a large set of data and convert them into a small standard size data. You create a unique fingerprint that is proof that your data has not been altered during different encryption levels. The outcome of hashing is called hash value or hash digest.
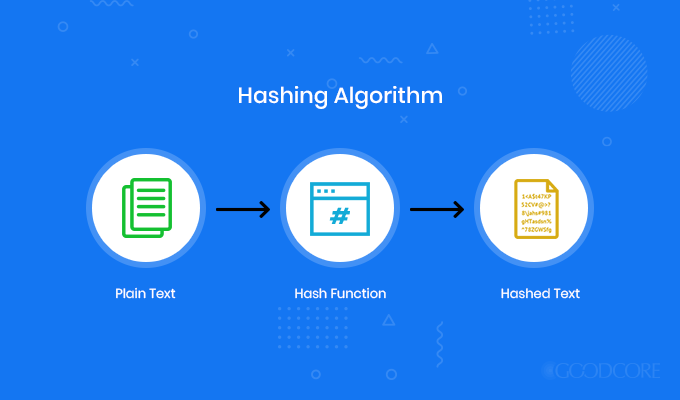
Hashing algorithm
If by any chance there is a doubt of data being changed or altered, you can always compare the original hash with that of the new one because two differently altered data cannot produce the same hashes.
If we look at the backend process, then hash functions when a user logins through their ID and password. The server searches for the associated hash value. The password which you entered is hashed with the same algorithm through which it was encrypted. If it matches with the already stored hash value then it is valid and authenticated.
Digital Certificates
Once you have identified that your encrypted information is not altered, it is also necessary to identify from which source your encrypted information is coming and who will decrypt it. This is where digital certificates come in, which are also known as identity certificates or public-key certificates.
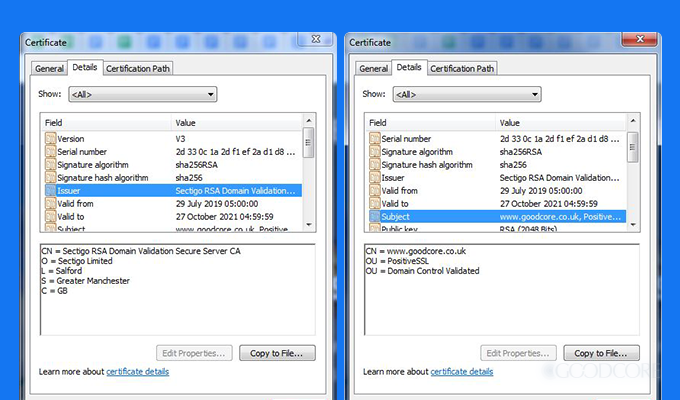
A screenshot of GoodCore’s digital certificate
They authenticate the details of the sender and receiver of the encrypted data over the internet using various types of encryption methods. Any certification authority will issue you your digital certificate. It will contain the following:
- Your name
- Certificate authority’s name
- Unique certificate serial number
- Its expiry date
- Unique private key
- Certificate authority’s digital signature
Once your digital certificate is issued, you can use it as a source of verification for your various online needs.
Encryption Protocols
In order to conduct private communication over a network, we need to make sure that our devices and our channels of communication are safe and secure. The ways in which we can achieve this are called encryption protocols.
Below, I have discussed a few encryption protocols that you must be well aware of.
IPsec
Internet Protocol Security (IPsec) is a framework for different types of encryption. It helps verify different packets, which are encrypted and decrypted using a public and a private key, within the protocol. For authentication, hash values are also added in those packets. If the sent packet is different from the received packet, then you can easily identify that there has been a change made during the process.
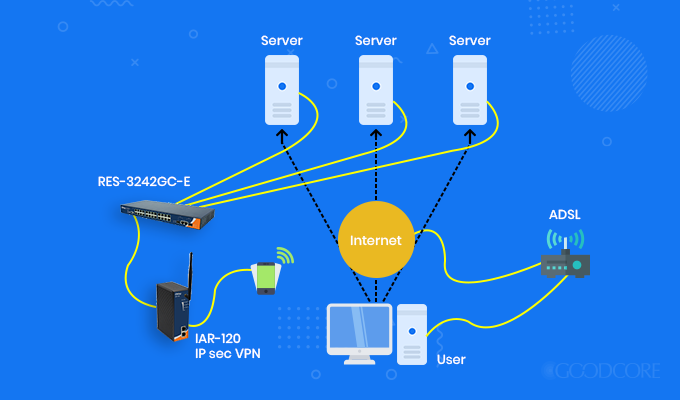
IPsec encryption protocol model
Also, you can run IPsec through two types of operations:
1. Tunnel mode: The entire packet, including the header, is encrypted and placed in another packet. It is then forwarded to a central VPN, where the endpoints decrypt them. After decryption, the packets are sent to the correct IP.
2. Transport mode: Only payloads of the packets are encrypted. The headers are sent as-is. This process requires less infrastructure and is easy to deploy.
PPTP
Point-to-Point Tunneling Protocol (PPTP) was developed by Microsoft and other tech companies as a framework for types of encryption. It makes sure that the communication between the VPN (Virtual Private Network) client and the VPN server is without any disturbance.
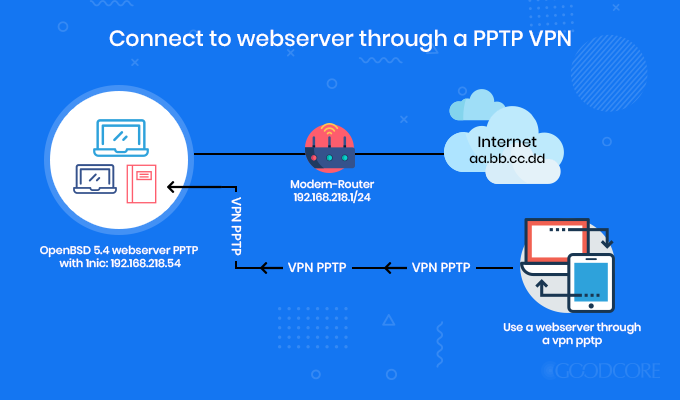
PPTP encryption protocol model
It encloses the data network and places inside the IP envelope which upon every encounter will be treated as an IP packet. This encryption protocol is quite out-dated now.
L2TP
Layer 2 Tunneling Protocol, endorsed by Microsoft and Cisco, is another framework for types of encryption which is used in hardware-based encryption devices. Unlike PPTP, it encloses the network data twice making the whole process slower.
Also, it works with IPsec to provide secure connection and encryption. It is built-in in all the operating systems and VPN-cable devices these days.
SSTP
Secure Socket Tunneling Protocol secures the connection between the VPN client and the VPN server.
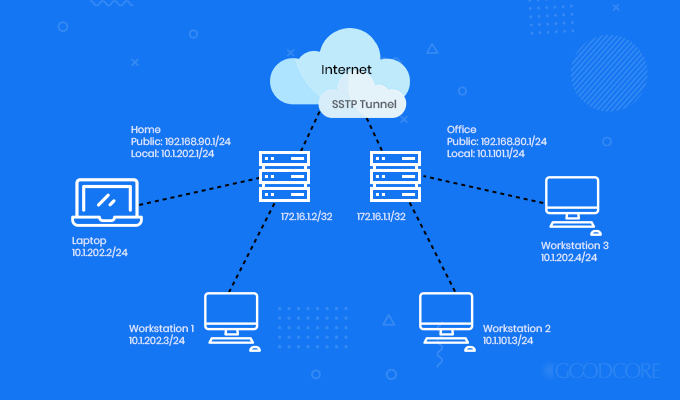
SSTP encryption protocol model
Hence, all the data and Point-to-Point Protocol (PPP) traffic through the SSL channel, which passes in between is encrypted. Therefore, it is highly secured as compared to PPTP.
SSL
Specifically designed to connect with a Web server, Secure Sockets Layer (SSL), now known as Transport Layer Security (TLS), provides data encryption, message integrity using certificates and authentication during encryption and decryption.
A screenshot of GoodCore’s SSL certificate
It guarantees that information is protected throughout the sharing process. It usually runs in the background.
HTTPS
Hypertext Transfer Protocol Secure (HTTPS) is HTTP combined with SSL. It is a secure version of HTTP, which you see in every website’s URL. HTTPS makes sure that your sensitive data from a web browser to a website is highly secured and encrypted to avoid online theft of information.
A screenshot of GoodCore’s web address
It works on asymmetric key encryption that is through private key, which is with the owner of the website, and a public key, which is available to everyone. So, the next time you use a website, check for an ‘s’ after HTTP, to make your online browsing and data sharing secured.
CONCLUSION:
This brings us to the end of our article.
Data security has become the focus of the whole internet world. It is really up to you to decide which encryption technique is better suited for you, along with the right combination of encryption application and protocols.
To recap this article, encryption is a secure way of sharing confidential data over the internet. There are various types of encryption but I have discussed six best encryption types with you, which are AES, Triple DES, FPE, RSA, Blowfish and Twofish. To authenticate and validate your information, you will need to have encryption protocols and applications in place.
I hope through this article, you are able to understand the science behind information security and are well aware of how it can be achieved by using the right types of encryption and protocols.
Are you looking training with Right Jobs?
Contact Us- Service Desk Analyst Interview Questions and Answers
- What is IT governance and its Significance?
- What are IT security policies?
- TOGAF 9.1 – Quick Start Guide for IT Enterprise Architect
- How to Build a Successful Career in IT Service Management?
Related Articles
Popular Courses
- Ethical Hacking Training
14025 Learners - Cyberark Training
15922 Learners - CCNA Training
13741 Learners
- What is Dimension Reduction? | Know the techniques
- Difference between Data Lake vs Data Warehouse: A Complete Guide For Beginners with Best Practices
- What is Dimension Reduction? | Know the techniques
- What does the Yield keyword do and How to use Yield in python ? [ OverView ]
- Agile Sprint Planning | Everything You Need to Know


