- How to learn Ethical Hacking?
- How to become a Ethical Hacker ? Know about the requirements to become one
- Introduction to Cyber Security | A Complete Guide
- Top Reasons to Learn Cyber Security | Everything You Need to Know to Become an Expert
- CyberSecurity Framework | How to Implement | A Definitive Guide with Best Practices [ OverView ]
- The Impact of AI and Machine Learning on Cybersecurity | Everything You Need to Know
- What is Certified Ethical Hacker (CEH) Certification and Why is it Important? [ OverView ]
- Benefits Of ECSA Certification | Everything You Need to Know | Expert’s Top Picks
- Top Most OSINT Tools – Open Source Intelligence | Expert’s Top Picks
- Cyber Security Salary in India : Everything You Need to Know
- What is Computer Security? Free Guide Tutorial & REAL-TIME Examples
- Ethical Hacker Salary and Job Description | Everything You Need to Know
- Hacking Tools and Software | All you need to know [ OverView ]
- What is DES? Free Guide Tutorial & REAL-TIME Examples
- How to Become an Ethical Hacker?
- Which are the Best Network Security Certifications?
- Cybersecurity Consultant Career Path
- The Most Effective Data Encryption Techniques
- Great CISSP Books and Study Guides for the CISSP Certification
- What Is Kerberos?
- Top CISSP Domains
- Cyber Security Career Path
- CISSP Certification Exam Guide 2020
- Top Cyber Security Trends for 2020
- CISSP Exam Online 2020
- Compare and Contrast Physical and Environmental Security Controls
- What is information security architect?
- Certified Information Systems Security Professional (CISSP) Certification
- Top Cyber Security Jobs
- What is CISA Certification?
- What is Threat Modeling?
- Certified Information Security Manager (CISM) Certification
- Information Security Management Principles
- Network Perimeter Security Design
- Things You Must Know About Cyber Security in the Cloud
- What is ECSA?
- Why is Cybersecurity Important?
- Tips to Clear Certified Ethical Hacker (CEH) Exam
- Average Annual Salary of a CISSP Certified Professional
- “How to Become a Cyber Security Engineer? “
- Who is an Ethical Hacker?
- What are the requirements to become Cissp certified?
- The Phases of Ethical Hacking
- What is Ethical Hacking?
- Top Ethical Hacking Certifications
- Hash in Python
- How to learn Ethical Hacking?
- How to become a Ethical Hacker ? Know about the requirements to become one
- Introduction to Cyber Security | A Complete Guide
- Top Reasons to Learn Cyber Security | Everything You Need to Know to Become an Expert
- CyberSecurity Framework | How to Implement | A Definitive Guide with Best Practices [ OverView ]
- The Impact of AI and Machine Learning on Cybersecurity | Everything You Need to Know
- What is Certified Ethical Hacker (CEH) Certification and Why is it Important? [ OverView ]
- Benefits Of ECSA Certification | Everything You Need to Know | Expert’s Top Picks
- Top Most OSINT Tools – Open Source Intelligence | Expert’s Top Picks
- Cyber Security Salary in India : Everything You Need to Know
- What is Computer Security? Free Guide Tutorial & REAL-TIME Examples
- Ethical Hacker Salary and Job Description | Everything You Need to Know
- Hacking Tools and Software | All you need to know [ OverView ]
- What is DES? Free Guide Tutorial & REAL-TIME Examples
- How to Become an Ethical Hacker?
- Which are the Best Network Security Certifications?
- Cybersecurity Consultant Career Path
- The Most Effective Data Encryption Techniques
- Great CISSP Books and Study Guides for the CISSP Certification
- What Is Kerberos?
- Top CISSP Domains
- Cyber Security Career Path
- CISSP Certification Exam Guide 2020
- Top Cyber Security Trends for 2020
- CISSP Exam Online 2020
- Compare and Contrast Physical and Environmental Security Controls
- What is information security architect?
- Certified Information Systems Security Professional (CISSP) Certification
- Top Cyber Security Jobs
- What is CISA Certification?
- What is Threat Modeling?
- Certified Information Security Manager (CISM) Certification
- Information Security Management Principles
- Network Perimeter Security Design
- Things You Must Know About Cyber Security in the Cloud
- What is ECSA?
- Why is Cybersecurity Important?
- Tips to Clear Certified Ethical Hacker (CEH) Exam
- Average Annual Salary of a CISSP Certified Professional
- “How to Become a Cyber Security Engineer? “
- Who is an Ethical Hacker?
- What are the requirements to become Cissp certified?
- The Phases of Ethical Hacking
- What is Ethical Hacking?
- Top Ethical Hacking Certifications
- Hash in Python

What is DES? Free Guide Tutorial & REAL-TIME Examples
Last updated on 27th Oct 2022, Artciles, Blog, Cyber Security
- In this article you will get
- 1.Introduction
- 2.Data Encryption Standard (DES)
- 3.What is the DES Algorithm in Cyber Security?
- 4.Modes of Operation of DES
- 5.DES Deployment and Testing
- 6.Implementations of the DES Algorithm
- 7.Benefits and Demerit points of the DES Algorithm
- 8.DES and Triple DES are still used in limited situations
- 9.Why is DES unsafe?
- 10.Conclusion
Introduction
We spend so much of our time online these days. Our society is increasingly reliant on an online presence, whether for storing personal information, finding entertainment, making purchases, or performing our jobs.
Because of our increased reliance on the internet, information security is more important than ever. The stakes are now too high. Users must have confidence that their sensitive data is kept confidential, unaltered, and easily accessible to authorized readers.
Although data encryption is only one tool in the cybersecurity arsenal, it is one of the oldest and most widely used. And because no discussion of data encryption is complete without mentioning DES, here we are.
Data Encryption Standard (DES)
The acronym DES stands for Data Encryption Standard. Certain machines can be used to crack the DES algorithm. The DES algorithm makes use of a 56-bit key. Using this key, the DES takes a block of 64-bit plain text as input and generates a block of 64-bit cypher text as output.
The DES process is comprised of several steps, each of which is referred to as a round. The number of rounds varies according to the size of the key used. For example, a 128-bit key requires 10 rounds, a 192-bit key requires 12 rounds, and so on.
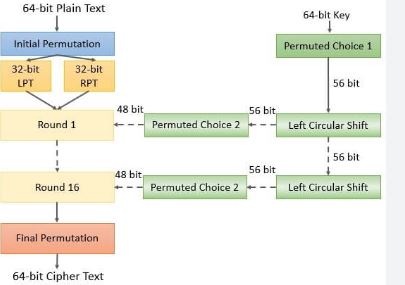
What is the DES Algorithm in Cyber Security?
The DES (Data Encryption Standard) algorithm is a symmetric-key block cypher developed by an IBM team in the early 1970s and adopted by the National Institute of Standards and Technology (NIST). The algorithm takes plain text in 64-bit blocks and converts it to ciphertext using 48-bit keys.
Because it is a symmetric-key algorithm, it uses the same key to encrypt and decrypt the data. If it were an asymmetrical algorithm, the encryption and decryption keys would be different.
Modes of Operation of DES
There are five distinct modes of operation available to DES experts.
Electronic Codebook (ECB) : Every 64-bit block is independently encrypted and decrypted.Each 64-bit block is dependent on the previous block and uses an Initialization Vector (IV).
Cipher Feedback (CFB) : The previous ciphertext becomes the input for the encryption algorithm, which generates pseudorandom output, which is then XORed with the plaintext to generate the next ciphertext unit.Similar to CFB, except that the input to the encryption algorithm is the output of the preceding DES.
Counter (CTR) : Each plaintext block is XOR’d with a counter that has been encrypted. The counter is then incremented after each block.
DES Deployment and Testing:Implementing DES necessitates a security provider. However, there are numerous providers from which to choose, and selecting one is the initial step in implementation. Your choice may depend on the programming language you’re utilising, such as Java, Python, C, or MATLAB.
After selecting a provider, you must decide whether to use the KeyGenerator to generate a random secret key or to generate a key yourself using plaintext or a byte array.
In addition, it is essential to test the encryption to ensure that it has been properly implemented. Using GitHub’s recurrence relation, you can find a testing procedure that will do the trick.
Now that we have a solid grasp on what DES is, let’s examine the benefits of DES learning.
Implementations of the DES Algorithm
Several applications of the DES Algorithm will be discussed in this section.
- It is employed in the generation of random numbers.
- It is used when only moderate encryption is required.
- It is utilised to create Triple DES, a new form of DES (using a 168-bit key formed using three keys).
Benefits and Demerit points of the DES Algorithm
The DES algorithm’s benefits are:
- The US government sets it as a standard.
- Hardware performs the function more quickly than software.
- Triple DES, with a 168-bit key, is extremely difficult to decipher.
The DES algorithm’s disadvantages:
- Algorithm with poor security.
- Attacks employing brute force pose a threat.
- Deep Crack is a DES-cracking machine that is commercially available.
Encryption Procedures:
There are multiple steps involved in the process of encrypting data. They’re:
- Permute the 64-bits in the plain text and divide them in half equally.
- Multiple operations will be carried out on these 32-bit data chunks.
- Use the XOR operation between the 48-bit compressed key and the expanded right plain text.
- The output is forwarded to the next step known as S-box substitution.
- Apply the XOR operation to the output and the left plain text, and then store the result in the right plain text.
- Store the initial left plain text in the initial right plain text.
- Both the LPT and RPT halves are passed on to the subsequent rounds for further operations.
- Change the data in the LPT and RPT at the conclusion of the previous round.
- pply the inverse permutation step in the final step to obtain the ciphertext.
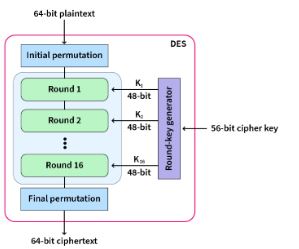
Decryption Procedure
The decryption of data involves the following steps:
- The order of the 16 48-bit keys is inverted such that key 16 becomes key 1, and so forth.
- The ciphertext is subjected to the encryption procedures.
Why Should One Learn DES If It Is Becoming Obsolete?
Even though DES is no longer the algorithm of choice for encrypting data, it is still worthwhile to learn. In cryptography, there will always be a place for the DES algorithm because it served as the foundation for subsequent encryption algorithms. If you are familiar with the history of data encryption, you will have an easier time grasping the fundamentals of contemporary encryption techniques.
Check out the video below, which explains encryption and decryption steps in detail, the future of the Data Encryption Standard in cryptography, and a real-world example that further illustrates the characteristics of DES encryption.
How is DES used currently?
The DES and 3DES rules and key lengths may still be used as deprecated standards. Users should be aware, though, that using the deprecated algorithm and key length poses a security risk, which gets more likely as time goes on.
DES is no longer secure for encrypting sensitive data. Before it was deprecated and then banned, the standard was needed for government financial transactions that used electronic funds transfers. It became the standard algorithm for encoding used in financial services and other industries.
DES and Triple DES are still used in limited situations:
In 2023, the Triple-DES office can modify its 3DES disallowed guidance. The rule and key length will then no longer be used for scientific discipline protection. training in scientific disciplines. DES and its variants are still employed in cryptography education today. The algorithms are well understood, and there is a large body of research on both the efficacy of DES and how to effectively attack it. The technology is still used to show how digital cryptography works and to do the following:
Even though it was no longer useful, the widespread use of information encoding helped people learn more about cryptography and make new encryption algorithms. Before DES, cryptography was a secretive art practiced only by military and government intelligence agencies.
Due to the open nature of DES, academics, mathematicians, and anyone interested in data security could study how the algorithm worked and attempt to break it. As with any popular and challenging puzzle, a craze or, in this case, an entire industry—was born.
Why is DES unsafe?
The DES encryption algorithm has been substantially replaced by the AES encryption algorithm.
The most fundamental method of attack for any cypher is brute force, which entails attempting each key until the correct one is discovered. The length of the key determines the number of possible keys and, by extension, the viability of this attack.
Effective DES key length of fifty-six bits would require a maximum of 256, or approximately seventy-two quadrillion, attempts to find the correct key. This may not be sufficient to protect information with DES against brute-force attacks utilising modern computers.
Few DES-encrypted messages could have been subjected to this intensive code-breaking effort before DES was completely replaced by AES. Prior to the adoption of DES as the industry standard, a number of security experts believed that the 56-bit key length was insufficient. There have been persistent rumours that interference from the National Security Agency has weakened the first rule.
Through the middle of the 1990s, DES remained a reliable and widely-used encoding algorithm. The subsequent year, roll in the hay reduced the secret writing time to twenty-two hours by utilising the power of thousands of networked computers.
As of this writing, the website promises, for a fee, to decrypt DES keys in approximately twenty-six hours. Crack. sh additionally provides free access to a rainbow table for proverbial plaintexts of 1122334455667788, from which a DES key can be generated in less than 25 seconds.
There are significantly more secure algorithms available, namely AES. Comparable to a cheap luggage lock, DES will keep the contents secure from honest people, but it will not prevent a determined thief.
Conclusion
The principles upon which the cryptanalysis of the Japanese and German cypher machines of World War II was based were not declassified and made public until the end of the twentieth century. The DES was a completely public cryptographic algorithm, which set it apart from other systems. Every aspect of its operations, sufficient for anyone desiring to program it on a microcomputer, was published and widely accessible via the Internet. Paradoxically, the best cryptographic system in the history of cryptology was also the least secure.