- Robotic Process Automation with Python Tutorial | Learn to Write Python Script Command in RPA
- Kofax Tutorial: Getting Started | A Complete guide for beginners
- UFT Tutorial | Learn Unified Functional Testing – Best Guide
- Pega Tutorial : Learn the In-Built Features
- Automation Anywhere Tutorial | What is, RPA & Types of Bots
- SaltStack Tutorial
- Ansible Basic Cheat Sheet Tutorial
- RPA blue prism tutorial
- RPA Developer Tutorial
- UIPath Tutorial
- Appttus Tutorial
- Appium Tutorial
- Chef Tutorial
- Ansible Tutorial
- PowerShell Tutorial
- Blue Prism Tutorial
- Selenium Tutorial
- RPA Tutorial
- Robotic Process Automation with Python Tutorial | Learn to Write Python Script Command in RPA
- Kofax Tutorial: Getting Started | A Complete guide for beginners
- UFT Tutorial | Learn Unified Functional Testing – Best Guide
- Pega Tutorial : Learn the In-Built Features
- Automation Anywhere Tutorial | What is, RPA & Types of Bots
- SaltStack Tutorial
- Ansible Basic Cheat Sheet Tutorial
- RPA blue prism tutorial
- RPA Developer Tutorial
- UIPath Tutorial
- Appttus Tutorial
- Appium Tutorial
- Chef Tutorial
- Ansible Tutorial
- PowerShell Tutorial
- Blue Prism Tutorial
- Selenium Tutorial
- RPA Tutorial

Ansible Tutorial
Last updated on 25th Sep 2020, Automation, Blog, Tutorials
Ansible is an open-source IT engine that automates application deployment, cloud provisioning, intra service orchestration, and other IT tools.
Ansible Overview
Ansible is easy to deploy because it does not use any agents or custom security infrastructure on the client-side, and by pushing modules to the clients. These modules are executed locally on the client-side, and the output is pushed back to the Ansible server.
It can easily connect to clients using SSH-Keys, simplifying though the whole process. Client details, such as hostnames or IP addresses and SSH ports, are stored in the files, which are called inventory files. If you created an inventory file and populated it, then Ansible can use it.
Ansible uses the playbook to describe automation jobs, and playbook, which uses simple language, i.e., YAML. YAML is a human-readable data serialization language & commonly used for configuration files, but it can be used in many applications where data is being stored.
A significant advantage is that even the IT infrastructure support guys can read and understand the playbook and debug if needed.
Ansible is designed for multi-tier deployment. Ansible does not manage one system at a time, and it models IT infrastructure by describing all of your systems are interrelated. Ansible is entirely agentless, which means Ansible works by connecting your nodes through SSH (by default). Ansible gives the option to you if you want another method for the connection like Kerberos.
Ansible pushes small programs after connecting to your nodes which are known as “Ansible Modules”. Ansible runs that module on your nodes and removes them when finished. Ansible manages the inventory in simple text files (These are the host’s files).
Ansible uses the host file where one can group the hosts and can control the actions on a specific group in the playbooks.
Ansible History
Here are some essential points from the history of Ansible, such as:
- Michael DeHaan developed Ansible, and the Ansible project began in February 2012.
- The creator of Cobbler and Func is also the controller of the Fedora Unified network.
- RedHat acquired the Ansible tool in 2015.
- Ansible is included as part of the Fedora distribution of Linux.
- Ansible is also available for RedHat Enterprise Linux, Debian, CentOS, Oracle Linux, and Scientific Linux via Extra Packages for Enterprise Linux (EPEL) and Ubuntu as well as for other operating systems.
Why use Ansible?
Here are some important pros/benefits of using Ansible
- One of the most significant advantages of Ansible is that it is free to use by everyone.
- It does not need any special system administrator skills to install and use Ansible, and the official documentation is very comprehensive.
- Its modularity regarding plugins, modules, inventories, and playbooks make Ansible the perfect companion to orchestrate large environments.
- Ansible is very lightweight and consistent, and no constraints regarding the operating system or underlying hardware are present.
- It is also very secure due to its agentless capabilities and due to the use of OpenSSH security features.
- Another advantage that encourages the adoption of Ansible is its smooth learning curve determined by the comprehensive documentation and easy to learn structure and configuration.
Important terms used in Ansible
1.Ansible server
The machine where Ansible is installed and from which all tasks and playbooks will be ran
2.Module
Basically, a module is a command or set of similar commands meant to be executed on the client-side
3.Task
A task is a section that consists of a single procedure to be completed
4.Role
A way of organizing tasks and related files to be later called in a playbook
5.Fact
Information fetched from the client system from the global variables with the gather-facts operation
6.Inventory
File containing data about the ansible client servers. Defined in later examples as hosts file
7.Play
Execution of a playbook
8.Handler
Task which is called only if a notifier is present
9.Notifier
Section attributed to a task which calls a handler if the output is changed
10.Tag
Name set to a task which can be used later on to issue just that specific task or group of tasks.
Ansible Installation in Linux
When you have compared and weighed your options and decided to go for Ansible. Then installed it on your system. Let’s go step by step of the installation in different Linux distributions, such as:
Subscribe For Free Demo
Error: Contact form not found.
Install Ansible on RedHat/Centos systems
Step 1: Install the EPEL repo
[root@ansible-server ~]# sudo yum install epel-release
Step 2: Install the Ansible package.
[root@ansible-server ~]# sudo yum install -y ansible
Install Ansible on Debian/Ubuntu systems
Step 1: First perform an update to the packages
$ sudo apt update
Step 2: Then install the software properties common package.
$ sudo apt install software-properties-common
Step 3: And install the Ansible personal package archive.
$ sudo apt-add-repository ppa:ansible/ansible
Step 4: Install the Ansible.
$ sudo apt update
$ sudo apt install ansible
Install Ansible using pip
The pip command is a tool for installing and managing python packages.
Step 1: This given method works on the Linux and UNIX like systems.
$ sudo pip install ansible
Install the latest version of Ansible
Using Portage (Gentoo)
$ emerge -av app-admin/ansible
To install the latest version, you need to unmask the Ansible package prior to emerging:
$ echo ‘app-admin/ansible’ >> /etc/portage/package.accept_keywords
Using pkg (FreeBSD)
Ansible works with both python 2 and 3 versions, FreeBSD has different packages for each python version. To install you can use:
$ sudo pkg install py27-ansible
Or
$ sudo pkg install py36-ansible
You can also to install from ports:
$ sudo make -C /usr/ports/sysutils/ansible install
Using OpenCSW (Solaris)
The Ansible is available for Solaris as SysV package from openCSW:
- # pkgadd -d http://get.opencsw.org/now
- # /opt/csw/bin/pkgutil -i ansible
Using Pacman (Arch Linux)
Ansible is available in the community repository:
$ pacman -S ansible
Using sbopkg (Slackware Linux)
Ansible build script is available in the SlackBuilds.org repository. Also can be built and installed using sbopkg.
Step 1: Create a queue with Ansible and all dependencies.
# sqg -p ansible
Step 2: Build and install packages from the created queue file.
# sbopkg -k -i ansible
Using swupd (Clear Linux)
Step 1: Ansible and its dependencies are available as part of the sysadmin host management bundle.
$ sudo swupd bundle-add sysadmin-hostmgmt
Step 2: And update of the software will be managed by the swupd tool.
$ sudo swupd update
Installing
By using yum
On Fedora:
$ sudo dnf install python-argcomplete
On RHEL and CentOS:
$ sudo yum install epel-release
$ sudo yum install python-argcomplete
By using apt
$ sudo apt install python-argcomplete
By using pip
$ pip install argcomplete
Ansible Workflow
As we discussed above, when services increase, sysadmins will provision more servers to do configuration management. They need not do it manually anymore but install Ansible on the master node where they need to write the code into the Ansible playbook to describe the setup, installation process, and the configuration required for these servers.
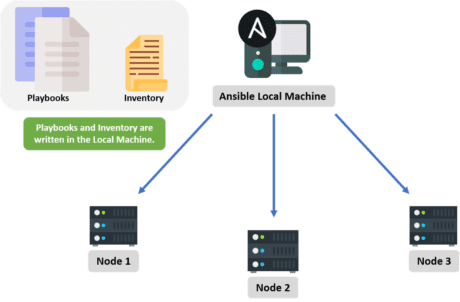
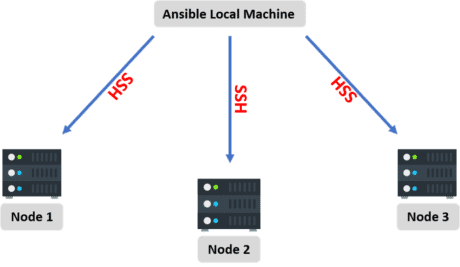
The local machine connects to these servers (nodes) through an inventory using secured SSH connections.
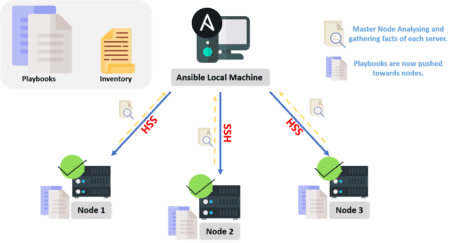
Once these nodes are connected to the master server, then the node servers are analyzed and the playbook codes are pushed toward each of the servers so that these playbooks can configure the servers remotely, which leads to a consistent environment.
Ansible Architecture
From the diagram below it is clear that Ansible Orchestration Engine interacts with a user who is writing the Ansible playbook to execute Ansible Orchestration Engine, along with interacting with the services of public/private cloud and configuration management databases.
Modules
Ansible connects the nodes and pushes out small ‘Ansible Modules.’ Modules are executed by Ansible and then get removed when finished. These modules can reside on any machine; no servers or daemons or databases are required here. We can work with the text editor of our choice or a terminal and a version control system to keep track of the changes made in our content.
Plugins
A plugin is a piece of code that expands the core functionality of Ansible. There are plenty of handy plugins, and we can write our own plugins as well.
Inventory
We already discussed this in the Ansible Terminologies section. An inventory is a list of hosts/nodes, having IP addresses, servers, databases, etc., which need to be managed.
Playbooks
As discussed earlier, we write our code in a playbook. It is simple and written in the YAML format and basically describes tasks that are supposed to be executed through Ansible. We can launch tasks synchronously or asynchronously with playbooks.
APIs
Ansible APIs work as transport for cloud services, either public or private.
Hosts
Hosts are basically the node systems in the Ansible architecture getting automated by Ansible only. They can be any type of machine such as Windows, Red Hat, Linux, etc.
Networking
We can use Ansible to automate different networks. It uses the easy, simple, yet powerful, agentless automation framework for IT operations and development. It uses a type of data model (playbook or role), which is separated from the Ansible Automation Engine that spans across different network hardware quite easily.
CMDB
CMDB is a type of repository that acts as a data warehouse for the IT installations.
Cloud
A network of remote servers on which we can store, manage, and process our data. These servers are hosted on the Internet. For storing the data remotely rather than on local servers, we would just launch our resources and instances on the cloud and connect them to our servers, and we would have the wisdom of operating our task remotely.
Operations by Ansible
So far, we have figured out how reliable and efficient Ansible is. Now, we will learn about the type of operations Ansible can perform.
Configuration Management
Ansible provides stability in the performance of our product by recording and updating stats in detail. This describes all information about the hardware and software of an enterprise/organization, such as versions and updates applied to the installed software packages, along with the locations and network addresses of hardware devices.
Resource/Server Provisioning

Either we are booting/starting servers/virtual machines or creating cloud instances from various templates, Ansible is always there to help us with the smooth running of the process. Ansible makes sure to provide the required packages installed on our application.
Application Deployment

With Ansible, we can define our application and manage its deployment. Instead of performing the deployment steps one by one, we just need to install Ansible on our machine and it will do the same tasks for us, even in a lesser time. Provided those tasks are listed in our Ansible playbook, Ansible executes them in order.
Security and Compliance

With Ansible, we can easily configure our security details. We do it once in a control machine and the same security details will be spread across all the other nodes.
Orchestration

We can also perform the orchestration of our application using Ansible. Ansible provides orchestration by aligning the business requests with the application, data, and infrastructure. It creates an application-aligned infrastructure that can be scaled up or down based on the needs.
Ansible Playbooks
Playbooks are the files where the Ansible code is written. Playbooks are written in YAML format. YAML means “Yet Another Markup Language,” so there is not much syntax needed. Playbooks are one of the core features of Ansible and tell Ansible what to execute, and it is used in complex scenarios. They offer increased flexibility.
Playbooks contain the steps which the user wants to execute on a particular machine. And playbooks are run sequentially. Playbooks are the building blocks for all the use cases of Ansible.Ansible playbooks tend to be more configuration languages than a programming language.
Through a playbook, you can designate specific roles to some of the hosts and other roles to other hosts. By doing this, you can orchestrate multiple servers in very different scenarios, all in one playbook.
Playbook Structure
Each playbook is a collection of one or more plays. Playbooks are structured by using Plays. There can be more than one play inside a playbook.
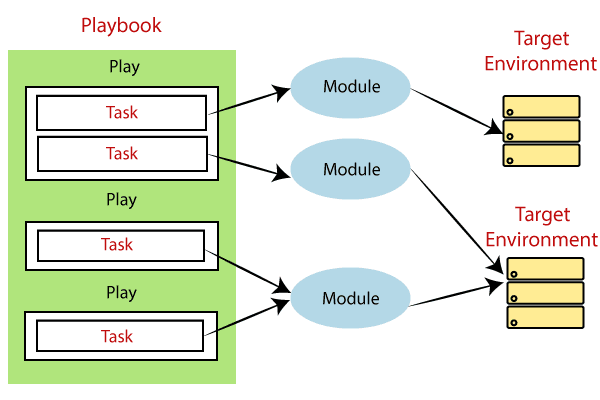
The function of the play is to map a set of instructions which is defined against a particular host.There are different YAML editors, but prefer to use a simple editor such as notepad++. First, open the notepad++ and copy-paste the below YAML and change the language to YAML (Language → YAML).
A YAML starts with — (3 hyphens) always.
Create a Playbook
Let’s start by writing an example YAML file. First, we must define a task. These are the interface to ansible modules for roles and playbooks.
One playbook with one play, containing multiple tasks looks like the below example.
- name: install and configure DB
- hosts: testServer
- become: yes
- vars:
- oracle_db_port_value : 1521
- tasks:
- -name: Install the Oracle DB
- yum: <code to install the DB>
- -name: Ensure the installed service is enabled and running
- service:
- name: <your service name>
Above is a basic syntax of a playbook. Save it in a file as test.yml. A YAML syntax needs to follow the correct indentation.
YAML Tags
Here are some YAML tags are given below, such as:
| Tags | Explanation |
|---|---|
| Name | It specifies the name of the Ansible Playbooks. |
| Hosts | It specifies the lists of the hosts against which you want to run the task. And the host’s Tag is mandatory. It tells Ansible that on which hosts to run the listed tasks. These tasks can be run on the same machine or the remote machine. One can run the tasks on the multiple machines, and the host’s tag can have a group of the host’s entries as well. |
| Vars | Vars tag defines the variables which you can use in your playbook. Its usage is similar to the variables in any programming language. |
| Tasks | Tasks are the lists of the actions which need to perform in the playbooks. All the playbooks should contain the tasks to be executed. A task field includes the name of the task. It is not mandatory but useful for debugging the playbook. Internally each task links to a piece of code called a module. A module should be executed, and arguments that are required for the module you want to run. |
Ansible Modules
Ansible modules are discrete units of code which can be used from the command line or in a playbook task.The modules are also referred to as task plugins or library plugins in Ansible.
Ansible ships with several modules that are called module libraries, which can be executed directly or from remote hosts through the playbook.Users can also write their modules. These modules can control like services, system resources, files, or packages, etc. and handle executing system commands.
Let’s see how to execute three different modules from the command line.
- 1. ansible webservers -m service -a “name=httpd state=started”
- 2. ansible webservers -m ping
- 3. ansible webservers -m command -a “/sbin/reboot -t now”
Each module supports taking arguments. Mainly all modules take key=value arguments, space delimited.Some module takes no arguments, and the shell/command modules take the string of the command which you want to execute.
From playbook, Ansible modules execute in a very similar way, such as:
– name: reboot the servers
command: /sbin/reboot -t now
Here is another way to pass arguments to a module that is using YAML syntax, and it is also called complex args.
– name: restart webserver
service:
name: httpd
state: restarted
Technically, all modules return JSON format data, though command line or playbooks, you don’t need to know much about that. If you’re writing your module, it means you do not have to write modules in any particular language which you get to choose.
Modules should be idempotent and avoid making any changes if they detect that the current state matches the desired final state. When using Ansible playbooks, these modules can trigger “change events” in the form of notifying “handlers” to run additional tasks.
Documentation for each module can be accessed from the command line with the Ansible-doc tool:
ansible-doc yum
Benefits of Using Ansible
- Agentless: As long as a connection can be SSHed and it has Python, it can be configured with Ansible; no agent/software or additional firewall ports are required to install on our client or host systems for automation. Also, we don’t have to worry about setting up and managing the infrastructure.
- Simple: As we’ve seen, Ansible uses a very simple syntax written in YAML known as playbooks—YAML (Yet Another Markup Language) is a human-readable data serialization language. We don’t need special coding skills to code and understand playbooks. It is very easy to install and execute tasks in order.
- Modular: Ansible is modular as we require only one program per script. This way, we can spread our programs across different servers.
- Efficient: Not requiring any extra software on our servers means that there is more space for our resources.
- Powerful and flexible: Having powerful features gives us the capability to model even complex IT workflows in less time, along with managing infrastructure, networks, operating systems, and services that are already in use.
Conclusion
Server systems are the backbones and foundation of applications. They too need to be version controlled, tested, and automated as we do with the applications. Nowadays, configuration management is nothing new; tools to perform configuration management have been around for quite some time now. Puppet, Chef, etc. are some of the names that pop up in our minds when we talk about configuration management.
Ansible is somewhat similar to these tools and yet it seems that more companies are interested in Ansible these days. The reason behind this fact is thoroughly elucidated in this tutorial, along with almost all the other must-know concepts on Ansible.
