- How to learn Ethical Hacking?
- How to become a Ethical Hacker ? Know about the requirements to become one
- Introduction to Cyber Security | A Complete Guide
- Top Reasons to Learn Cyber Security | Everything You Need to Know to Become an Expert
- CyberSecurity Framework | How to Implement | A Definitive Guide with Best Practices [ OverView ]
- The Impact of AI and Machine Learning on Cybersecurity | Everything You Need to Know
- What is Certified Ethical Hacker (CEH) Certification and Why is it Important? [ OverView ]
- Benefits Of ECSA Certification | Everything You Need to Know | Expert’s Top Picks
- Top Most OSINT Tools – Open Source Intelligence | Expert’s Top Picks
- Cyber Security Salary in India : Everything You Need to Know
- What is Computer Security? Free Guide Tutorial & REAL-TIME Examples
- Ethical Hacker Salary and Job Description | Everything You Need to Know
- Hacking Tools and Software | All you need to know [ OverView ]
- What is DES? Free Guide Tutorial & REAL-TIME Examples
- How to Become an Ethical Hacker?
- Which are the Best Network Security Certifications?
- Cybersecurity Consultant Career Path
- The Most Effective Data Encryption Techniques
- Great CISSP Books and Study Guides for the CISSP Certification
- What Is Kerberos?
- Top CISSP Domains
- Cyber Security Career Path
- CISSP Certification Exam Guide 2020
- Top Cyber Security Trends for 2020
- CISSP Exam Online 2020
- Compare and Contrast Physical and Environmental Security Controls
- What is information security architect?
- Certified Information Systems Security Professional (CISSP) Certification
- Top Cyber Security Jobs
- What is CISA Certification?
- What is Threat Modeling?
- Certified Information Security Manager (CISM) Certification
- Information Security Management Principles
- Network Perimeter Security Design
- Things You Must Know About Cyber Security in the Cloud
- What is ECSA?
- Why is Cybersecurity Important?
- Tips to Clear Certified Ethical Hacker (CEH) Exam
- Average Annual Salary of a CISSP Certified Professional
- “How to Become a Cyber Security Engineer? “
- Who is an Ethical Hacker?
- What are the requirements to become Cissp certified?
- The Phases of Ethical Hacking
- What is Ethical Hacking?
- Top Ethical Hacking Certifications
- Hash in Python
- How to learn Ethical Hacking?
- How to become a Ethical Hacker ? Know about the requirements to become one
- Introduction to Cyber Security | A Complete Guide
- Top Reasons to Learn Cyber Security | Everything You Need to Know to Become an Expert
- CyberSecurity Framework | How to Implement | A Definitive Guide with Best Practices [ OverView ]
- The Impact of AI and Machine Learning on Cybersecurity | Everything You Need to Know
- What is Certified Ethical Hacker (CEH) Certification and Why is it Important? [ OverView ]
- Benefits Of ECSA Certification | Everything You Need to Know | Expert’s Top Picks
- Top Most OSINT Tools – Open Source Intelligence | Expert’s Top Picks
- Cyber Security Salary in India : Everything You Need to Know
- What is Computer Security? Free Guide Tutorial & REAL-TIME Examples
- Ethical Hacker Salary and Job Description | Everything You Need to Know
- Hacking Tools and Software | All you need to know [ OverView ]
- What is DES? Free Guide Tutorial & REAL-TIME Examples
- How to Become an Ethical Hacker?
- Which are the Best Network Security Certifications?
- Cybersecurity Consultant Career Path
- The Most Effective Data Encryption Techniques
- Great CISSP Books and Study Guides for the CISSP Certification
- What Is Kerberos?
- Top CISSP Domains
- Cyber Security Career Path
- CISSP Certification Exam Guide 2020
- Top Cyber Security Trends for 2020
- CISSP Exam Online 2020
- Compare and Contrast Physical and Environmental Security Controls
- What is information security architect?
- Certified Information Systems Security Professional (CISSP) Certification
- Top Cyber Security Jobs
- What is CISA Certification?
- What is Threat Modeling?
- Certified Information Security Manager (CISM) Certification
- Information Security Management Principles
- Network Perimeter Security Design
- Things You Must Know About Cyber Security in the Cloud
- What is ECSA?
- Why is Cybersecurity Important?
- Tips to Clear Certified Ethical Hacker (CEH) Exam
- Average Annual Salary of a CISSP Certified Professional
- “How to Become a Cyber Security Engineer? “
- Who is an Ethical Hacker?
- What are the requirements to become Cissp certified?
- The Phases of Ethical Hacking
- What is Ethical Hacking?
- Top Ethical Hacking Certifications
- Hash in Python

How to learn Ethical Hacking?
Last updated on 30th Jan 2023, Artciles, Blog, Cyber Security
- In this article you will learn:
- 1.Introduction.
- 2.What is Hacking?
- 3.What is Ethical hacking?
- 4.Types of Hacking.
- 5.Advantages of Hacking.
- 6.Disadvantages of Hacking.
- 7.Why learn Hacking Course?
- 8.Why Choose Ethical Hacking as a Career?
- 9.How to Fight Back with an Ethical Hacking.
- 10.Build Supplemental Cybersecurity Skills.
- 11.Conclusion.
Introduction:
Ethical Hacking provides a basic and advanced concepts of Ethical Hacking an Ethical Hacking tutorial is developed for a beginners and professionals.In a network hacking section learn how a networks work how to crack Wi-Fi keys and gain access a Wi-Fi networks. In Gaining access section will learn how to gain access to a servers and personal computers. In a post-exploitation section we will learn what can do with the access that gained So learn how to interact with a file system how to execute the system command how to open a webcam. In a website hacking section will learn how a website works and how to gather a comprehensive information about website. In the end will learn how to secure a system from the discussed attacks.
What is Hacking?
Gaining access to the system that you are not supposed to have access is considered as a hacking. For example login into an email account that is not supposed to have an access gaining access to a remote computer that are not supposed to have access reading information that are not supposed to able to read is be considered as hacking. There are a more number of ways to hack a systemIn 1960 the first known event of a hacking had taken place at MIT and at a same time the term Hacker was organized.
What is Ethical hacking?
- Ethical hacking is also known as a White hat Hacking or Penetration Testing. Ethical hacking involves the authorized attempt to gain unauthorized access to the computer system or data. Ethical hacking is used to increase a security of the systems and networks by fixing a vulnerability found while testing.
- Ethical hackers improve a security posture of an organization. Ethical hackers use same tools, tricks and techniques that malicious hackers used but with permission of the authorized person. The purpose of an ethical hacking is to improve a security and to defend the systems from attacks by malicious users.
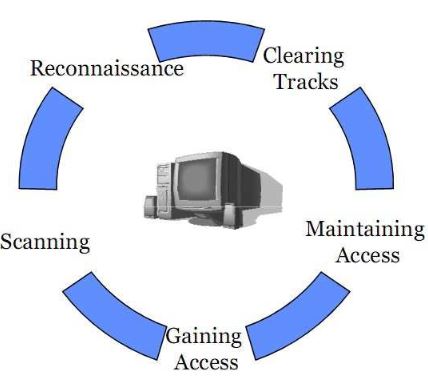
Types of Hacking:
Define a hacking into various categories based on what is being hacked. These are as below :
1. Network Hacking.
2. Website Hacking.
3. Computer Hacking.
4. Password Hacking.
5. Email Hacking.
1. Network Hacking: a Network hacking means gathering information about network with an intent to harm a network system and hamper its operations using a various tools are Telnet, NS lookup, Ping, Tracert etc.
2. Website hacking: Website hacking means taking an unauthorized access over a web server, database and make change in an information.
3. Computer hacking: Computer hacking means be unauthorized access to the Computer and steals an information from PC like Computer ID and password by applying a hacking methods.
4. Password hacking: Password hacking is a process of recovering secret passwords from data that has been already stored in a computer system.
5. Email hacking: Email hacking means unauthorized access on Email account and using it without owner’s permission.
Advantages of Hacking:
There are different advantages of hacking:
1. It is used to recover a lost of information especially when lost a password.
2. It is used to perform the penetration testing to increase security of a computer and network.
3. It is used to test how a good security is on a network.
Disadvantages of Hacking:
There are different disadvantages of hacking:
1. It can harm a privacy of someone.
2. Hacking is an illegal.
3. Criminal can use a hacking to their advantage.
4. A Hampering system operations.

Why Learn Hacking Course?
Information is one of more valuable assets of an organization. Keeping information secure can protect an organization’s image and save an organization a lot of money. More organizations and government agencies need ethical hackers to secure their resources and systems from cybercriminals. So there are vast opportunities and ethical hackers jobs around world. Learning ethical hacking will help to get a job as an ethical hacker or enhance a network and data security knowledge.
Why Choose Ethical Hacking as a Career?
Choosing ethical hacking as a career has more benefits, like the demand of an ethical hackers higher pay scale and higher ethical hacking salary problem-solving etc.
How to Fight Back with an Ethical Hacking:
- The core problem for the companies is that cybersecurity professionals don’t fundamentally think like a hackers and cybercriminals. To be successful they must understand what goes through a mind of a hacker what tools they use and how they are leverage their assets to penetrate networks and a steal data. That’s why ethical hacking is becoming one of the most prized skill sets in a cybersecurity arena.
- Certified Ethical Hackers (CEH) are trained to leverage a same techniques as hackers but without the danger of law enforcement knocking at their doors. CEH certification training is geared to help an IT professionals master the advanced concepts of a writing virus codes exploit writing reverse engineering, social engineering and also tactics hackers use to penetrate a corporate networks, firewalls, IDS wireless systems and IoT networks.
- Ethical or “white hat” hackers learn how to assess the potential vulnerabilities and utilize the latest hacking tools by a thinking like cybercriminals. They’re also in high demand. In fact CEH practitioners are more valuable to cybersecurity teams that they can earn as much as 44 percent higher salaries than non-certified counterparts.
Build Supplemental Cybersecurity Skills:
While ethical hacking training adds a tremendous value to cybersecurity teams more CEH certification holders got their start by earning other credentials to be establish themselves as viable IT security practitioners. The most famous and valuable skills and certifications include:
- Certified Information Systems Security Professional (CISSP)
- Certified Information Security Manager (CISM)
- Certified Information Systems Auditor (CISA)
- Certified Cloud Security Professional (CCSP)
Conclusion:
Ethical or “white hat” hackers learn how to assess the potential vulnerabilities and utilize a latest hacking tools by thinking like cybercriminals. They’re also in a high demand. In fact CEH practitioners are more valuable to cybersecurity teams that they can earn as much as a 44 percent higher salaries than a non-certified counterparts.